
HOME | SEARCH | CONTACT | PDF FILES | WHAT'S NEW
TABLE OF CONTENTS | PREVIOUS TOPIC | NEXT TOPIC | INDEX

|
BEA eLink TCP for CICS 3.1 Information Center | |
|
HOME | SEARCH | CONTACT | PDF FILES | WHAT'S NEW |
||
|
TABLE OF CONTENTS | PREVIOUS TOPIC | NEXT TOPIC | INDEX |
||
The eLink TCP product supports a security feature that allows a requester from BEA TUXEDO services to pass a USERID requirement through the CICS server interfaces for verification through a third-party security package. The following topics explain the how to set up security:
The following sections describe the process flow for security verification of a service request.
Figure 3-1 depicts the process flow for security verifications from eLink for Mainframe TCP for CICS on UNIX to a mainframe.
Service Request Processing with Security
Security Checking from UNIX to Mainframe
Figure 3-1 Security Checking for UNIX to Mainframe Transactions
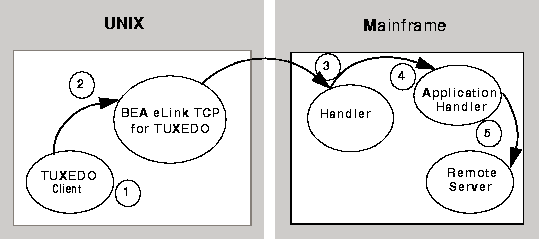
tpinit(), the
user's TUXEDO identity is validated against the tpusr file.
With each request, the eLink TCP for TUXEDO gateway passes the user's TUXEDO identity to the remote eLink TCP for CICS gateway (to the Handler).
Note:
To pass authority checking, the user's TUXEDO identity must match the mainframe userid exactly.
Figure 3-2 depicts the process flow for security verifications from a mainframe to eLink for Mainframe TCP for CICS on UNIX.
Figure 3-2 Security Checking for Mainframe to UNIX Transactions
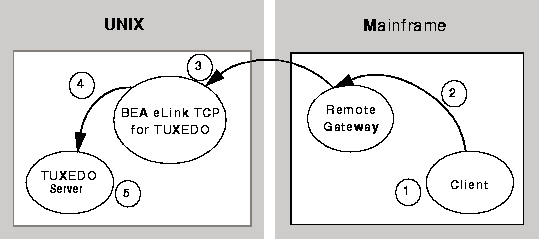
Note:
To pass authority checking, the user's TUXEDO identity must match the mainframe userid exactly.
The eLink TCP for CICS product supports enhanced security. This interface allows a requester from BEA TUXEDO services to pass a USERID through the CICS server interface for authorization through your security package. For field definitions, refer to the "Configuring and Administering BEA eLink TCP for CICS."
Complete the following tasks to enable the security feature for each connection.
When SECURITY=Y, eLink TCP for CICS verifies the ACCOUNT and PASSWORD values from the User Connection Account match the RMTACCT and PASSWORD values in the eLink TCP for TUXEDO GWICONFIG file *FOREIGN section. If these values do not match and SECURITY=Y, a security error occurs.
If SECURITY=N, the gateway allows a connection without any verification.
Complete the following tasks to enable the security feature for each inbound service.
Complete the following tasks to enable the security feature for each outbound connection.
Verify that the parameter values for ACCOUNT and PASSWORD in the Requester screen match the RMTACCT and PASSWORD values in the *FOREIGN section of the eLink TCP for TUXEDO GWICONFIG file.
When SECURITY=Y, the requester program sends the ACCOUNT and PASSWORD to the remote UNIX system on connection initiation. When SECURITY=N, the gateway attempts to make a connection without any verification.
Complete the following tasks to enable the security feature for each outbound connection.
Verify that the parameter values for ACCOUNT and PASSWORD in the Requester screen match the ACCOUNT and PASSWORD values in the User Connection Account screen.
When SECURITY=Y, the requester program sends the ACCOUNT and PASSWORD to the remote CICS system on connection initiation. When SECURITY=N, the gateway attempts to make a connection without any verification.
Complete the following tasks to enable the security feature for each outbound connection.
Verify that the parameter values for ACCOUNT and PASSWORD in the Requester screen match the ACCOUNT and PASSWORD values in the GATEWAY TYPE=REMOTE statement.
When SECURITY=Y, the requester program sends the ACCOUNT and PASSWORD to the remote IMS system on connection initiation. When SECURITY=N, the gateway attempts to make a connection without any verification.
Complete the following tasks to enable the security feature for each outbound service.