The Recovery Appliance Environment
At minimum, the Recovery Appliance environment consists of one Recovery Appliance and one protected database. More typical is the sample environment shown in Figure 2-1.
Figure 2-1 Sample Recovery Appliance Environment
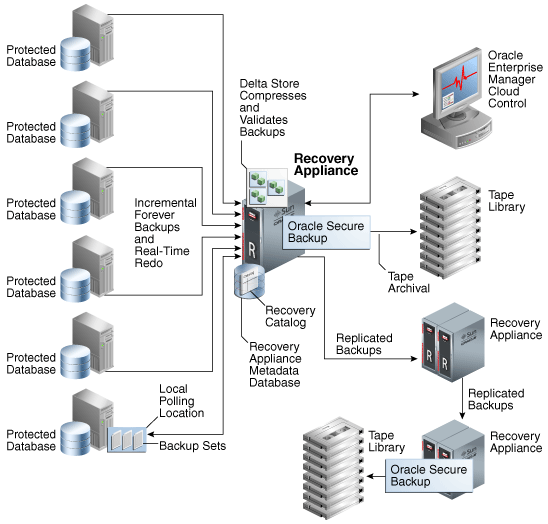
Description of "Figure 2-1 Sample Recovery Appliance Environment"
This section contains the following topics:
Main Components of the Recovery Appliance Environment
Figure 2-1 shows an example of a typical Recovery Appliance environment, which contains the following components:
-
Multiple protected databases
Each protected database sends backups and real-time redo to the Recovery Appliance. Protected databases can run on different releases of Oracle Database.
-
Recovery Appliance
Figure 2-1 shows a central Recovery Appliance, which receives incremental backups and real-time redo from the protected databases. The Recovery Appliance contains the Recovery Appliance metadata database. This database includes the following components:
-
The RMAN recovery catalog, which is subdivided into multiple virtual recovery catalogs.
-
One or more storage locations. Recovery Appliance storage contains the delta store, which includes multiple delta pools.
Figure 2-1 also shows the central Recovery Appliance replicating backups to a second Recovery Appliance, which in turn forwards these backups to a third Recovery Appliance.
-
-
Oracle Enterprise Manager Cloud Control (Cloud Control)
Figure 2-1 shows Cloud Control running on a separate server in the environment. Administrators can use Cloud Control to manage all Recovery Appliances, protected databases, and tape devices in the Recovery Appliance environment.
-
DBMS_RAPL/SQL packageThis is the command-line interface to Recovery Appliance. This package, which is stored in the Recovery Appliance metadata database, provides the underlying functionality for Cloud Control.
-
Oracle Secure Backup
Figure 2-1 shows the Recovery Appliance using Oracle Secure Backup to archive backups to a tape library. The diagram also shows a downstream Recovery Appliance archiving backups to a separate tape library.
User Accounts in the Recovery Appliance Environment
The central components of a Recovery Appliance environment are the protected databases, Recovery Appliance, and Cloud Control. Table 2-1 summarizes the most important user accounts in the environment.
Table 2-1 User Accounts in the Recovery Appliance Environment
| Component | Account Type | User Name | Description |
|---|---|---|---|
|
Cloud Control |
Cloud Control super-user |
|
This application account exists by default. Its purpose is to administer Cloud Control itself, and is not directly related to managing a Recovery Appliance or protected databases. |
|
Cloud Control |
Cloud Control administrator |
User-Specified |
A Cloud Control user account that has been granted the roles and privileges needed to manage a specific protected database or a specific Recovery Appliance. Multiple Cloud Control administrative accounts may exist, depending on your business requirements. |
|
Recovery Appliance |
Recovery Appliance metadata database super-user |
|
|
|
Recovery Appliance |
|
This database account owns the Recovery Appliance schema, which includes the RMAN recovery catalog and the |
|
|
Recovery Appliance |
User-Specified |
This account has authority to send and receive backups for databases registered with the Recovery Appliance, and to manipulate recovery catalog metadata for these databases. This is also the account to use to send redo data from a protected database to the Recovery Appliance. Unlike Typically, a Recovery Appliance metadata database contains multiple Recovery Appliance user accounts. These accounts are created when configuring access for protected databases (see Configuring Recovery Appliance for Protected Database Access). Every Recovery Appliance user account owns a virtual private catalog. The catalog owner can access and modify only those rows in the recovery catalog that pertain to the databases to which it has been granted access. The catalog user name for this is referenced in an RMAN |
|
|
Protected Database |
Protected database backup administrator |
User account with |
This account has the privileges to back up, restore, and recover a protected database. This is the database user name that is referenced in an RMAN |
Figure 2-2 depicts the relationship between RASYS and two Recovery Appliance user accounts. In this example, each Recovery Appliance user account owns a separate virtual private catalog. Note that RASYS, as owner of the Recovery Appliance schema, is also the owner of the RMAN recovery catalog.
Figure 2-2 RASYS and Recovery Appliance User Accounts
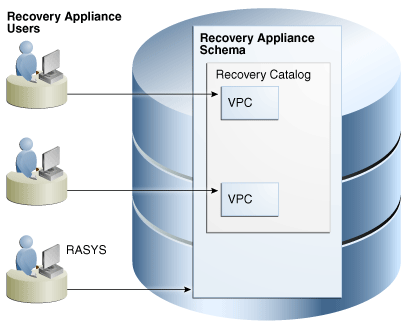
Description of "Figure 2-2 RASYS and Recovery Appliance User Accounts"
See Also:
Oracle Database Security Guide to learn how to create database user accounts
Lifecycle of a Backup: Scenario
This section describes the lifecycle of a backup as it flows through the Recovery Appliance environment depicted in Figure 2-1. In this sample scenario, each protected database has already seeded Recovery Appliance with the required initial level 0 incremental backup. The basic data flow is as follows:
-
A protected database, or a standby database protecting this database, sends a level 1 incremental backup to the Recovery Appliance.
Recovery Appliance distinguishes itself from other backup solutions because only one level 0 backup is ever required for each data file. Level 1 incremental backups are most efficient because data blocks are only backed up when they change.
Oracle recommends making cumulative level 1 incremental backups (see Oracle Database Backup and Recovery Reference). Each cumulative level 1 backup uses the most recent virtual level 0 backup as its baseline. Typically, this virtual level 0 backup corresponds to the most recent level 1 backup.
Note:
If a level 1 cumulative backup cannot be incorporated into the Recovery Appliance (for example, because of a storage corruption), then the next level 1 backup has the same virtual level 0 backup baseline, enabling the Recovery Appliance to seamlessly incorporate the new level 1 incremental backup. Thus, cumulative backups almost never have greater overhead than differential backups.
-
The Recovery Appliance receives the incremental backup.
The received backup is available for immediate retrieval, but the Recovery Appliance has not yet indexed it, so the corresponding virtual full backup are not available. If a protected database requires this backup for recovery before the Recovery Appliance can index it, then RMAN automatically restores the previous virtual full backup and applies this incremental backup to it.
-
The Recovery Appliance processes the incremental backup.
The following operations occur asynchronously:
-
The Recovery Appliance performs backup ingest. The Recovery Appliance processes the backup as follows:
-
Scans the backup that was sent by a protected database
-
Breaks it into smaller groups of blocks, assigning the blocks from each data file to a separate delta pool
-
Writes the groups into the appropriate storage location according to the protection policy for the database
-
Deletes the original backup set after the virtual backup set has been created
Note:
The Recovery Appliance may not delete the original backup at precisely the same time that the virtual backup is created. Thus, it is possible for both the original and virtual backups to coexist briefly in the recovery catalog as two separate copies.
During backup ingest, the Recovery Appliance also indexes the backup, which involves storing information about the contents and physical location of each data block in the metadata database. Because the Recovery Appliance contains the recovery catalog for the protected database, the newly indexed virtual full backups are now available for use by RMAN, if needed for recovery.
-
-
If Recovery Appliance replication is configured, then the Recovery Appliance forwards the backup to a downstream Recovery Appliance.
Many different replication configurations are possible. Figure 2-1 shows a one-to-one configuration in which the central Recovery Appliance, acting as the upstream Recovery Appliance (backup sender), forwards its backups to a separate Recovery Appliance, acting as the downstream Recovery Appliance (backup receiver). Figure 2-1 shows cascaded replication, in which the downstream Recovery Appliance forwards its backups to a third Recovery Appliance.
-
If automated copy-to-tape policies are enabled, then the Recovery Appliance archives the backup to tape.
In Figure 2-1, the central Recovery Appliance uses Oracle Secure Backup software to communicate with a tape device. Also, the Recovery Appliance furthest downstream in the replication scheme archives its backups to tape. This technique has the following benefits:
-
To create redundancy, identical backups reside on two separate tape devices. In Figure 2-1, the primary Recovery Appliance archives to tape, as does the Recovery Appliance that is furthest downstream.
-
A downstream Recovery Appliance can back up to tape, thus offloading tape archival processing from the upstream Recovery Appliance.
-
-
The Recovery Appliance periodically verifies that backups and redo are valid.
The Recovery Appliance automatically validates backups on disk, and during inbound and outbound replication. The Recovery Appliance automatically performs crosschecks of tape backups. Just as with data file backups, the Recovery Appliance validates the integrity of redo log blocks during every operation, including receiving redo from protected databases and storing it in compressed archived log backup sets. No manually run RMAN
VALIDATEcommands are required. -
The Recovery Appliance performs automated delta pool space management.
This phase involves deleting obsolete and expired backups, both on disk and tape, and optimizing the delta pools.
-
See Also:
-
Oracle Database Backup and Recovery User's Guide to learn how to make incremental backups