Enabling and Configuring Proxy Users
Oracle Database supports proxy user authentication, which allows a client user to connect to the database through an application server, as a proxy user.
The users connecting through a Forms application as proxy users must also be defined in authentication server and Oracle Internet Directory. Oracle Forms authenticates the user via authentication server (using authentication server with Forms is a requirement when using a proxy user). Oracle Forms then connects to the database as the proxy user with a username and password that is in the RAD for the Oracle Internet Directory entry for the application user.
This section contains the following:
Proxy User Overview
Many large applications, including Oracle's own E-Business Suite, use a single username for all connections. This makes it possible to manage users in a way that often suits large companies better but it creates a problem with auditing. All inserts, updates and removals of records appear, from the database's perspective, to have been done by a single user. To restore auditing, the application developers must write and implement customized auditing code in the database that requires a user name to be passed to the database from the application. This step not only takes development time, but also duplicates functionality that is already implemented in the Oracle Database.The second issue is security. If that single user access is ever compromised, the compromised user will have access to the entire application schema.To address these two issues, Oracle Database supports proxy user authentication, which allows a client user to connect to the database through an application server, as a proxy user.
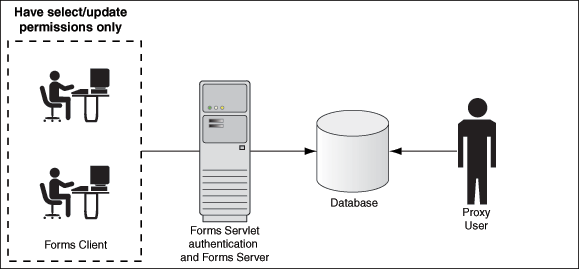
The following figure describes the authentication of a Forms proxy user.
-
Oracle Forms authenticates the user through Oracle Internet Directory or LDAP, as shown in the center of the image.
-
Forms then connects as the proxy user with or without a password, passing in the real username from the Oracle Internet Directory repository.
-
Typically, the proxy user is configured with least set of privileges. In the following procedure, the proxy user has "connect" and "create session" privileges.
-
The database accepts the
createsession action for the proxy user and uses the real username in audits and access control. -
The Oracle Internet Directory user cannot connect to the database independently without configuration of the proxy user account.
-
The proxy user account isolates the client from direct SQL*Plus connections.
Enabling Proxy User Connections When Enabling SSO with Oracle Internet Directory
To use a proxy support in Forms, you first need to create a proxy user.
In this example, the proxy user is called midtier:
It is also possible to set up the database users in Oracle Internet Directory with the help of the database functionality called Enterprise User Security. If you choose this method, the proxy user is the only user defined in the database and the additional benefit of easy administration is gained, see Configuring Directory Server Chaining in Administering Oracle Internet Directory.
The application user's password is not presented to the database; only the user name and the proxy user's user name and password. Forms, with the help of OCI calls, issues the equivalent of:
SQL> connect midtier[appuser]/midtierPW@databaseTnsName
For example, suppose your application always connects to the database using midtier. This midtier now informs the database that the actual user is appuser. Without using proxy users, the SQL command select USER from DUAL would return midtier, but, using proxy users, this query returns appuser. This essentially tells the database to trust that the user is authenticated elsewhere and to let the user connect without a password and to grant the connect role.
Note:
-
In the Step 3 of the above procedure, the database users are typically configured to have a subset of permissions granted to a schema. For example, appuser is granted
CREATEpermissions to the schemaapp_schemawith the SQL command:SQL> GRANT CREATE ON SCHEMA app_schema TO appuser
Thus, the appuser is restricted to perform only a set of actions in proxy user mode.
-
When the database user (for example, appuser) is connected in proxy mode, user actions of the database users are audited rather than that of the proxy user.
Enabling SSO for Proxy Users
Create a configuration section in formweb.cfg for single sign-on (for example, ssoapp) and set SSOProxyConnect to yes and ssoMode to true or webgate.
The username and password that is used for the proxy connection is defined in the RAD entry for the user that is logging on. If ssoProxyConnect=yes, the connect string equivalent issued by Forms is in effect:
SQL> connect RADUsername[appuserName]/RADPassword@databaseTnsName
Accessing the Forms Application
After enabling proxy user connections and single sign-on, perform the following steps to access the forms applications:
- Run the forms application with the URL
https://<host name>:<https port>/forms/frmservlet?config=ssoappwheressoappis the name of the configuration section with single sign-on (ssoMode) is enabled. - Use the single sign-on user name and password to log in.
appuser and password is appuserPW.