3 Implementing EPAP Security
This chapter explains security related configuration settings that may be applied to the EPAP.
3.1 User and Group Administration
The EPAP user interface (UI) comes pre-defined with UI users to provide a seamless transition to the GUI. For instance, there is a pre-defined user that is used to access the User Administration menu, as shown in Table 3-1.
Table 3-1 EPAP UI Logins
| Login Name | Access Granted |
|---|---|
| epapmaint | Maintenance menu and all submenus |
| epapdatabase | Database menu and all submenus |
| epapdebug | Debug menu and all submenus |
| epapplatform | Platform menu and all submenus |
| uiadmin | User Administration menu |
| epapall | All of the above menus |
| epapconfig | Configuration menu and all submenus (text-based UI) |
The User Administration menu is used to set up and perform administrative functions for users and groups, and also to terminate active sessions and modify system defaults.
Establishing Groups and Group Privileges
Each user is assigned to a group, and permissions to a set of functions are assigned to the group. The permissions determine the functions and restrictions for the users belonging to the group. EPAP users can fall into one of the following default groups:
- maint
- database
- platform
- debug
- pdba
- admin
- readonly
The readonly group is the default group for new users. The readonly group contains only actions that view status and information.
The menu allows administrator access to group functions to add, modify, delete, and retrieve a group. For more information, see Groups under User Administration Menu in Administration Guide.
Creating Users and Assigning to Groups
Each user that is allowed access to the user interface is assigned a unique username. This username and associated password must be provided during login.
Prior to adding a user, determine which group the user should be assigned based on their operational role. The group assignment determines the functions that a user can access.
After determining the proper group for a user, use the menu to add the user.
The menu can also be used to modify, delete, and retrieve user accounts, and to reset passwords. For more information, see Users under User Administration Menu in Administration Guide.
3.2 User Authentication
Users are authenticated using login credentials. Each user that is allowed access to the UI is assigned a unique username. This username and associated password must be provided during login.
Password Restrictions
Before beginning to use EPAP for provisioning, the EPAP software must be configured and initialized. During configuration, default password restrictions such as password aging and minimum password size can be changed via the menu. For more information, see Security under EPAP Configuration Menu in Administration Guide.
The UI addresses security concerns with various restrictions and controls. In many cases, the frequency or severity of these checks is configurable by the administrator at both a user-specific and system-wide level. For information about modifying system-wide defaults, see Modify Defaults under User Administration Menu in Administration Guide. For information about user-specific settings, see Users under User Administration Menu in Administration Guide.
For information about topics such as password complexity, password aging, and password reuse, see Change Password under EPAP Graphical User Interface Menus in Administration Guide.
Changing Default Passwords for EPAP Administrative Account
As a security measure, passwords for the EPAP UI login names, the OS root, and the OS admusr must be changed from their default values to user-defined values. For more information, see Secure Turnover to Customer.
Changing User Passwords
The Change Password screen of the EPAP GUI main menu provides all EPAP users with the capability to change their password. To change the password, the current password must be entered, then the new password is entered. The new password is confirmed by retyping the new password and clicking the Set Password button.
Password Change for System Users
The epapdev and appuser users can use the passwd command provided by the operating system. If changing a password using the passwd command, then the Linux PAM credit rules are used.
The system user epapconfig uses the option provided in the EPAP Configuration Menu. Linux PAM rules are not applicable while changing the password for the epapconfig user. Only the configured minimum password length applies.
Note:
If the password for the appuser or epapconfig user is changed by the root user, the appuser or epapconfig user will be prompted to change the password again.3.3 Modifying System Defaults
The screen enables the administrator to manage system defaults. Use this screen to control settings such as maximum failed login attempts before disabling a user account, maximum account inactivity, maximum password age, and minimum password length. For more information, see Modify Defaults under User Administration Menu in Administration Guide.
3.4 SNMP Configuration
EPAP can use the industry-standard Simple Network Management Protocol (SNMP) interface to send alarms as trap messages to an OCEEMS. EPAP sends SNMPv2c only, SNMPv3 only, or both SNMPv2c and SNMPv3 traps to the OCEEMS if the configurable parameter SNMP Alarm Feed is set to ON. EPAP also supports GET and SET of the resyncVar MIB element.
The active EPAP server provides a single interface to SNMP data for the EPAP pair. For network configurations using the Stand-Alone PDBI feature, the PDBI provides its own SNMP interface directly with SNMP managers. The application sends SNMP traps to SNMP managers that are registered to receive traps.
Community Names / Strings
The default community names configured for Read and Write in the snmpd.conf file are epapRdSnmp and epapWrSnmp. You should change the default community names to prevent unauthorized access. Always use different names for the Read community and Write community.
For more information about configuring community names, see Configure SNMP Agent Community in Administration Guide.
3.5 Authorized IP Addresses
The menu enables you to add, remove, and list authorized IP addresses (IPv4 and/or IPv6), and to change the IP address authorization status. The IP addresses are authorized for both GUI and server access. For more information, see EPAP Security Enhancements, and Authorized IPs under User Administration Menu, in Administration Guide.
The PDBA maintains a list of IP addresses that are allowed to connect through the PDBI. Any connect request coming from an IP address that is not in the list is rejected. Each IP address in the list has either READ or READ/WRITE permission. The menu enables you to add, modify, remove, and list the IP addresses authorized to connect to the PDBA through the PDB. For more information, see Authorized IP List under PDBA Menu in Administration Guide.
3.6 Installing an SSL Certificate For a Provisionable Interface With Customized Parameters
Perform the following steps to install a certificate with customized parameters:
- Log in to EPAP A as admusr.
- Execute the following commands to determine the IP configuration for
which the certificate files were
generated.
[admusr@mps-A ~]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server.crt [admusr@mps-A ~]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server_dual.crtSample output for the above commands:
[admusr@mps-A ~]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server.crt /usr/TKLC/plat/etc/ssl/server.crt: CN = 10.250.51.149 error 18 at 0 depth lookup:self signed certificate OKThe EPAP network configuration can be IPv4, IPv6, or dual stack (both IPv4 and IPv6), and you need to determine which certificate file corresponds to which network configuration:
- Both certificate files have the same IP address (either IPv4 or IPv6)
- The server.crt file has the certificate for IPv4 and the server_dual.crt file has the certificate for IPv6
- The server.crt file has the certificate for IPv6 and the server_dual.crt file has the certificate for IPv4
- Sign the certificate files on the EPAP A server according to the
determined network configuration information:
- If both certificate files have been generated for the same IP
address (either IPv4 or IPv6), sign both certificate files with that IP
address by using the following
commands:
[admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server.key -out /usr/TKLC/plat/etc/ssl/server.crt [admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_dual.key -out /usr/TKLC/plat/etc/ssl/server_dual.crt - If the server.crt file has the certificate for EPAP IPv4 and
the server_dual.crt file has the certificate for EPAP IPv6, sign the
certificate files by using the following commands:
[admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IPv4 IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server.key -out /usr/TKLC/plat/etc/ssl/server.crt [admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IPv6 IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_dual.key -out /usr/TKLC/plat/etc/ssl/server_dual.crt - If the server.crt file has the certificate for EPAP IPv6 and
the server_dual.crt file has the certificate for EPAP IPv4, sign the
certificate files by using the following commands:
[admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IPv6 IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server.key -out /usr/TKLC/plat/etc/ssl/server.crt [admusr@mps-A ~]$ sudo /usr/bin/openssl req –x509 -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A GUI IPv4 IP address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_dual.key -out /usr/TKLC/plat/etc/ssl/server_dual.crt
- If both certificate files have been generated for the same IP
address (either IPv4 or IPv6), sign both certificate files with that IP
address by using the following
commands:
- Sign the certificate files on the EPAP B server in the same way.
- Restart the httpd service on both the EPAP A and B servers by using
the following
commands:
[admusr@mps-A ~]$ sudo systemctl restart httpd [admusr@mps-B ~]$ sudo systemctl restart httpd - Open the EPAP A and B GUIs using https and install the SSL
certificates.
- For IPv4, use the following
commands:
https://<EPAP A GUI IPv4 IP> https://<EPAP B GUI IPv4 IP> - For IPv6, use the following
commands:
https://[<EPAP A GUI IPv6 IP>] https://[<EPAP B GUI IPv6 IP>]
- For IPv4, use the following
commands:
- Verify that the certificates installed successfully and the EPAP A and B GUIs opened successfully.
- If the EPAP GUI does not open, on the EPAP A and B servers, follow
these steps to reconfigure the IP addresses on EPAP through the epapconfig menu.
This will re-install the SSL certificates with the default parameters.
- Check the value of EPAP_IP_VERSION, and then access the
EPAP Configuration
Menu:
[admusr@mps-A ~]$ uiEdit | grep -i EPAP_IP_VERSION "EPAP_IP_VERSION" is set to "IPv4v6" [admusr@mps-A ~]$ sudo su – epapconfig - Enter choice 2 to access
the Configure Network Interfaces
Menu:
/-------EPAP Configuration Menu--------\ /----------------------------------------\ | 1 | Display Configuration | |----|-----------------------------------| | 2 | Configure Network Interfaces Menu | |----|-----------------------------------| | 3 | Set Time Zone | |----|-----------------------------------| | 4 | Exchange Secure Shell Keys | |----|-----------------------------------| | 5 | Change Password | |----|-----------------------------------| | 6 | Platform Menu | |----|-----------------------------------| | 7 | Configure NTP Server | |----|-----------------------------------| | 8 | PDB Configuration Menu | |----|-----------------------------------| | 9 | Security | |----|-----------------------------------| | 10 | SNMP Configuration | |----|-----------------------------------| | 11 | Configure Alarm Feed | |----|-----------------------------------| | 12 | Configure Query Server | |----|-----------------------------------| | 13 | Configure Query Server Alarm Feed | |----|-----------------------------------| | 14 | Configure SNMP Agent Community | |----|-----------------------------------| | 15 | Mate Disaster Recovery | |----|-----------------------------------| | e | Exit | \----------------------------------------/ Enter Choice: 2 - Enter choice 1 to Configure
Provisioning Network:
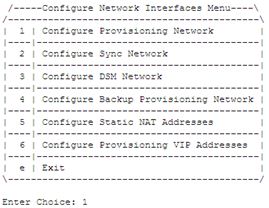
- On the Configure Provisioning Network
Menu, choose option 1 if the EPAP_IP_VERSION is IPv4, option
2 if the EPAP_IP_VERSION is IPv6, or options 1 and 2 in succession if the
EPAP_IP_VERSION is IPv4v6.
- Enter 1 for IPv4 Configuration:
-
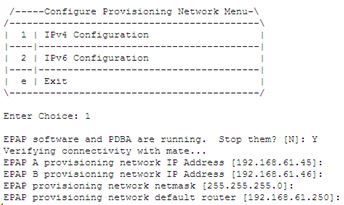
- Press Enter to reconfigure the network with the same configuration.
- Enter 2 for IPv6
Configuration:
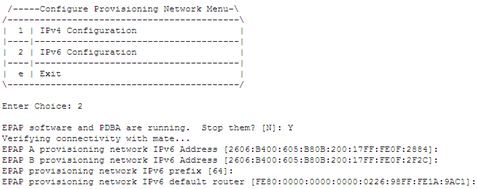
- Press Enter to reconfigure the network with the same configuration.
- If you need assistance, contact unresolvable-reference.html#GUID-06251C83-E21A-4DB7-B8DE-227FC0FCE6E1.
- Check the value of EPAP_IP_VERSION, and then access the
EPAP Configuration
Menu:
- Copy the key and cert files for the tpdProvd process running on
the 20000
port.
cp /usr/TKLC/plat/etc/ssl/server.key /usr/TKLC/plat/etc/ssl/server.pem cp /usr/TKLC/plat/etc/ssl/server.crt /usr/TKLC/plat/etc/ssl/server.cert - Restart the tpdProvd process by
killing the existing process and letting it
restart.
ps -eaf | grep tpdProvdOutput: tpdProvd 13468 1 0 03:42 ? 00:00:04 /usr/TKLC/plat/bin/tpdProvd kill -9 <pid> Example: kill -9 13468 Run ps again to check process is restarted ps -eaf | grep tpdProvd Output: tpdProvd 9090 1 3 04:09 ? 00:00:00 /usr/TKLC/plat/bin/tpdProvd - Repeat steps 9 and 10 on EPAP B.
3.7 Installing an SSL Certificate For a Provisionable Interface From a Trusted Certificate Authority
Perform the following steps to install an SSL certificate from a trusted Certificate Authority (CA):
- Log in as the admusr user on both the EPAP A and B servers, create a
new certificate directory (
/var/TKLC/epap/free/certificate), provide permissions to the new directory, and change to the new directory:[admusr@mps-A ~]$ pwd /home/admusr [admusr@mps-A ~]$ sudo mkdir /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ sudo chmod 777 /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ cd /var/TKLC/epap/free/certificate - On EPAP A, execute the following commands to determine the IP
configuration for which the certificate files were
generated.
[admusr@mps-A certificate]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server.crt [admusr@mps-A certificate]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server_dual.crtSample output of the above commands:
[admusr@mps-A certificate]$ sudo openssl verify /usr/TKLC/plat/etc/ssl/server.crt /usr/TKLC/plat/etc/ssl/server.crt: CN = 10.250.51.149 error 18 at 0 depth lookup:self signed certificate OKThe EPAP network configuration can be IPv4, IPv6, or dual stack (both IPv4 and IPv6), and you need to determine which certificate file corresponds to which network configuration:
- Both certificate files have the same IP address (either IPv4 or IPv6)
- The server.crt file has the certificate for IPv4 and the server_dual.crt file has the certificate for IPv6
- The server.crt file has the certificate for IPv6 and the server_dual.crt file has the certificate for IPv4
- Based on the determined network configuration information, generate
certificate signing request (CSR) and private key files for the EPAP A server by
using the appropriate commands from within the
certificatedirectory.Note:
The -subj option in the following commands has example fields, which must be replaced with your organization-specific domain information. The /C field is for your country, /ST is for state, /L is for location, /O is for organization, /OU is for organizational unit, and /CN is the common name field, which is the IP address or fully-qualified domain name that you want to use with your certificate.- If both certificate files have been generated for the same IP
address (either IPv4 or IPv6), enter the following
commands:
[admusr@mps-A certificate]$ sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server.key –out server.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com" [admusr@mps-A certificate]$ sudo /usr/bin/openssl req -newkey rsa:2048 -nodes –keyout server_dual.key –out server_dual.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com" - If the server.crt file has the certificate for EPAP IPv4 and
the server_dual.crt file has the certificate for EPAP IPv6, enter the
following commands:
[admusr@mps-A certificate]$ sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server.key –out server.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IPv4 IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com" [admusr@mps-A certificate]$ sudo /usr/bin/openssl req -newkey rsa:2048 -nodes –keyout server_dual.key –out server_dual.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IPv6 IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com" - If the server.crt file has the certificate for EPAP IPv6 and
the server_dual.crt file has the certificate for EPAP IPv4, enter the
following commands:
[admusr@mps-A certificate]$ sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server.key –out server.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IPv6 IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com" [admusr@mps-A certificate]$ sudo /usr/bin/openssl req -newkey rsa:2048 -nodes –keyout server_dual.key –out server_dual.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP GUI IPv4 IP address, e.g, 1.1.1.1>/emailAddress=xxx@yyy.com"
These commands generate the following files on the EPAP A server:
[admusr@mps-A certificate]$ ls -lrt -rw-r--r-- 1 root root 1679 May 21 11:08 server.key -rw-r--r-- 1 root root 968 May 21 11:08 server.csr -rw-r--r-- 1 root root 1675 May 21 11:09 server_dual.key -rw-r--r-- 1 root root 968 May 21 11:09 server_dual.csr - If both certificate files have been generated for the same IP
address (either IPv4 or IPv6), enter the following
commands:
- Generate certificate signing request (CSR) and private key files for
the EPAP B server in the same way (steps 2 - 3), using the files serverB.csr and
serverB_dual.csr for EPAP B.
The following files will be generated on the EPAP B server:
[admusr@mps-B certificate]$ ls -lrt -rw-r----- 1 root root 1679 May 21 11:02 server.key -rw-r----- 1 root root 968 May 21 11:02 serverB.csr -rw-r----- 1 root root 1679 May 21 11:02 server_dual.key -rw-r----- 1 root root 968 May 21 11:02 serverB_dual.csr - Send the generated CSR files (server.csr, server_dual.csr, serverB.csr, and serverB_dual.csr) to the CA. The CA will provide signed certificate (server.crt, server_dual.crt, serverB.crt, and serverB_dual.crt) files in return.
- Copy the appropriate files to the appropriate
ssldirectory, and rename (in the B server only) as needed:- On the EPAP A server, copy the four files generated through
the openssl commands (server.key, server_dual.key, server.csr,
server_dual.csr) and the two files provided by the CA for the EPAP A server
(server.crt and server_dual.crt) to the
/usr/TKLC/plat/etc/ssldirectory. - On the EPAP B server, copy the four files generated through
the openssl commands (server.key, server_dual.key, serverB.csr,
serverB_dual.csr) and the two files provided by the CA for the EPAP B server
(serverB.crt and serverB_dual.crt) to the
/usr/TKLC/plat/etc/ssldirectory. - After copying serverB.crt and serverB_dual.crt to the
/usr/TKLC/plat/etc/ssldirectory on the EPAP B server, rename them to server.crt and server_dual.crt respectively.
- On the EPAP A server, copy the four files generated through
the openssl commands (server.key, server_dual.key, server.csr,
server_dual.csr) and the two files provided by the CA for the EPAP A server
(server.crt and server_dual.crt) to the
- Restart the httpd service on both the EPAP A and B servers by using
the following
commands:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Open the EPAP A and B GUIs using https and install the SSL
certificates.
- For IPv4, use the following
commands:
https://<EPAP A GUI IPv4 IP> https://<EPAP B GUI IPv4 IP> - For IPv6, use the following
commands:
https://[<EPAP A GUI IPv6 IP>] https://[<EPAP B GUI IPv6 IP>]
- For IPv4, use the following
commands:
- Verify that the EPAP A and B GUIs opened successfully with the installed certificate.
- If the EPAP GUI does not open, follow these steps on the EPAP A and B
servers:
- Open the
/etc/httpd/conf.d/ssl.conffile:[admusr@mps-A certificate]$ sudo vi /etc/httpd/conf.d/ssl.conf - Edit
/etc/httpd/conf.d/ssl.confand un-comment the appropriate code:- If the CA provides ca.crt (CA intermediate
certificate), change
from:
to:#SSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crtSSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crt - If the CA provides CA certificate(s), change
from:
to:#SSLCACertificatePath /etc/httpd/conf/ca-cert #SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crtSSLCACertificatePath /etc/httpd/conf/ca-cert SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crt
- If the CA provides ca.crt (CA intermediate
certificate), change
from:
- Make sure that these files (CA certs) are copied to the right
path on both servers, as mentioned in
/etc/httpd/conf.d/ssl.conf. - Restart the httpd service using the following command on both
servers:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Verify that the EPAP A and B GUIs open successfully.
- Open the
- Copy the key and cert files for the tpdProvd process running on the 20000
port.
cp /usr/TKLC/plat/etc/ssl/server.key /usr/TKLC/plat/etc/ssl/server.pem cp /usr/TKLC/plat/etc/ssl/server.crt /usr/TKLC/plat/etc/ssl/server.cert - Restart the tpdProvd process by
killing the existing process and letting it
restart.
ps -eaf | grep tpdProvdOutput: tpdProvd 13468 1 0 03:42 ? 00:00:04 /usr/TKLC/plat/bin/tpdProvd kill -9 <pid> Example: kill -9 13468 Run ps again to check process is restarted ps -eaf | grep tpdProvd Output: tpdProvd 9090 1 3 04:09 ? 00:00:00 /usr/TKLC/plat/bin/tpdProvd - Repeat steps 11 and 12 on EPAP B.
3.8 Installing an SSL Certificate For a Backup Provisionable Interface With Customized Parameters
Perform the following steps to install an SSL certificate for a backup prov interface with customized parameters:
- Log in to EPAP A as admusr.
- Switch to the root user as "su -".
- Change the directory to
/usr/TKLC/plat/etc/ssl/. - Execute the following command to list the files in the directory
/usr/TKLC/plat/etc/ssl/.Sample output for the previous command:
[admusr@mps-A ssl]$ ls -ltrh server_bkprov* -rw-r----- 1 root epap 1.7K May 23 06:33 server_bkprov_v4.key -rw-r----- 1 root epap 1.1K May 23 06:33 server_bkprov_v4.crtThe EPAP network configuration can be IPv4, IPv6, or dual stack (both IPv4 and IPv6), and you need to determine which certificate file corresponds to which network configuration:
- Both certificate files are present in the
/usr/TKLC/plat/etc/ssl/directory - The server_bkprov_v4.crt certificate file is present in the
/usr/TKLC/plat/etc/ssl/directory - The server_bkprov_v6.crt certificate file is present in the
/usr/TKLC/plat/etc/ssl/directory
- Both certificate files are present in the
- Exit from the root user:
[admusr@mps-A ssl]$ exit logout - Sign the certificate files on the EPAP A server according to the determined certificate file information:
- If both certificate files have been generated for the same IP address (either IPv4 or IPv6), sign both certificate files with that IP address by using the following commands:
sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A Backup Prov IPv4 address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_bkprov_v4.key -out /usr/TKLC/plat/etc/ssl/server_bkprov_v4.crt sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A Backup Prov IPv6 address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_bkprov_v6.key -out /usr/TKLC/plat/etc/ssl/server_bkprov_v6.crt - If the server_bkprov_v4.crt file is generated because the bakcup prov is configured for EPAP IPv4, sign the certificate files by using the following command:
sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A Backup Prov IPv4 address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_bkprov_v4.key -out /usr/TKLC/plat/etc/ssl/server_bkprov_v4.crt - If the server_bkprov_v6.crt file is generated because the bakcup prov is configured for EPAP IPv6, sign the certificate files by using the following command:
sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A Backup Prov IPv6 address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_bkprov_v6.key -out /usr/TKLC/plat/etc/ssl/server_bkprov_v6.crt
- If both certificate files have been generated for the same IP address (either IPv4 or IPv6), sign both certificate files with that IP address by using the following commands:
- Sign the certificate files on the EPAP B server in the same way.
- Restart the httpd service on both the EPAP A and B servers by using the following
commands:
[admusr@mps-A ~]$ sudo systemctl restart httpd [admusr@mps-B ~]$ sudo systemctl restart httpd - Open the EPAP A and B GUIs using https and install the SSL certificates.
- For IPv4, use the following commands:
https://<EPAP A GUI IPv4 IP> https://<EPAP B GUI IPv4 IP> - For IPv6, use the following commands:
https://[<EPAP A GUI IPv6 IP>] https://[<EPAP B GUI IPv6 IP>]
- For IPv4, use the following commands:
- Verify that the certificates installed successfully and the EPAP A and B GUIs opened successfully.
- If the EPAP GUI does not open, on the EPAP A and B servers, follow these steps to reconfigure the IP addresses on EPAP through the epapconfig menu. This will re-install the SSL certificates with the default parameters.
- Check the value of EPAP_IP_VERSION, and then access the EPAP Configuration Menu:
[admusr@mps-A ~]$ uiEdit | grep -i "EPAP_A_BACKUP_PROV_NETWORK_IP_ADDRESS" "EPAP_A_BACKUP_PROV_NETWORK_IP_ADDRESS" is set to "10.75.136.41" [admusr@mps-A ~]$ uiEdit | grep -i "EPAP_B_BACKUP_PROV_NETWORK_IP_ADDRESS_V6" "EPAP_B_BACKUP_PROV_NETWORK_IP_ADDRESS_V6" is set to " 2606:b400:605:b912:200:17ff:fe0e:bf88" [admusr@mps-A ~]$ sudo su – epapconfig - Enter choice 2 to access the Configure Network Interfaces Menu:
/-------EPAP Configuration Menu--------\ /----------------------------------------\ | 1 | Display Configuration | |----|-----------------------------------| | 2 | Configure Network Interfaces Menu | |----|-----------------------------------| | 3 | Set Time Zone | |----|-----------------------------------| | 4 | Exchange Secure Shell Keys | |----|-----------------------------------| | 5 | Change Password | |----|-----------------------------------| | 6 | Platform Menu | |----|-----------------------------------| | 7 | Configure NTP Server | |----|-----------------------------------| | 8 | PDB Configuration Menu | |----|-----------------------------------| | 9 | Security | |----|-----------------------------------| | 10 | SNMP Configuration | |----|-----------------------------------| | 11 | Configure Alarm Feed | |----|-----------------------------------| | 12 | Configure Query Server | |----|-----------------------------------| | 13 | Configure Query Server Alarm Feed | |----|-----------------------------------| | 14 | Configure SNMP Agent Community | |----|-----------------------------------| | 15 | Mate Disaster Recovery | |----|-----------------------------------| | e | Exit | \----------------------------------------/ Enter Choice: 2 - Enter choice 1 to Configure Provisioning Network:

- On the Configure Provisioning Network Menu, choose option 1 if the EPAP_IP_VERSION is IPv4, option 2 if the EPAP_IP_VERSION is IPv6, or options 1 and 2 in succession if the EPAP_IP_VERSION is IPv4v6.
- Enter 1 for IPv4 Configuration:
-
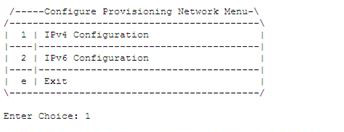
EPAP software and PDBA are running. Stop them? [N]: Y Verifying connectivity with mate... EPAP A backup provisioning network IP Address [10.75.136.41]: EPAP B backup provisioning network IP Address [10.75.136.42]: EPAP backup provisioning network netmask [255.255.255.0]: EPAP backup provisioning network default router [10.75.136.1]: - Press Enter to reconfigure the network with the same configuration.
- If you need assistance, contact unresolvable-reference.html#GUID-06251C83-E21A-4DB7-B8DE-227FC0FCE6E1.
- Check the value of EPAP_IP_VERSION, and then access the EPAP Configuration Menu:
3.9 Installing an SSL Certificate For a Backup Provisionable Interface From a Trusted Certificate Authority
Perform the following steps to install an SSL certificate for a backup prov interface from a trusted Certificate Authority (CA):
- Log in as the admusr user on both the EPAP A and B servers, create a new certificate directory (
/var/TKLC/epap/free/), provide permissions to the new directory, and change to the new directory:[admusr@mps-A ~]$ pwd /home/admusr [admusr@mps-A ~]$ sudo mkdir /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ sudo chmod 777 /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ cd /var/TKLC/epap/free/certificate - Switch to the root user as "su -".
- Change the directory to
/usr/TKLC/plat/etc/ssl/. - Execute the following command to list the files in the directory
/usr/TKLC/plat/etc/ssl/.Sample output for the previous command:
[admusr@mps-A ssl]$ ls -ltrh server_bkprov* -rw-r----- 1 root epap 1.7K May 23 06:33 server_bkprov_v4.key -rw-r----- 1 root epap 1.1K May 23 06:33 server_bkprov_v4.crt - The EPAP Backup prov network configuration can be IPv4, IPv6, or dual stack (both IPv4 and IPv6), and you need to determine which certificate file corresponds to which network configuration:
- Both certificate files are present in the
/usr/TKLC/plat/etc/ssl/directory - The server_bkprov_v4.crt certificate file is present in the
/usr/TKLC/plat/etc/ssl/directory - The server_bkprov_v6.crt certificate file is present in the
/usr/TKLC/plat/etc/ssl/directory
- Both certificate files are present in the
- Exit from the root user:
[admusr@mps-A ssl]$ exit logout - Based on the determined network configuration information, generate certificate signing request (CSR) and private key files for the EPAP A server by using the appropriate commands from within the
certificatedirectory.Note:
The -subj option in the following commands has example fields, which must be replaced with your organization-specific domain information. The /C field is for your country, /ST is for state, /L is for location, /O is for organization, /OU is for organizational unit, and /CN is the common name field, which is the IP address or fully-qualified domain name that you want to use with your certificate.- If both certificate files have been generated for the same IP address (either IPv4 or IPv6), enter the following commands:
sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server_bkprov_v4.key –out server_bkprov_v4.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP Backup Prov IPv4 address>/emailAddress=xxx@yyy.com" sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server_bkprov_v6.key –out server_bkprov_v6.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP Backup Prov IPv6 address>/emailAddress=xxx@yyy.com" - If the server_bkprov_v4.crt file is generated because the bakcup prov is configured for EPAP IPv4, sign the certificate files by using the following command:
sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server_bkprov_v4.key –out server_bkprov_v4.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP Backup Prov IPv4 address>/emailAddress=xxx@yyy.com" - If the server_bkprov_v6.crt file is generated because the bakcup prov is configured for EPAP IPv6, sign the certificate files by using the following command:
sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server_bkprov_v6.key –out server_bkprov_v6.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP Backup Prov IPv6 address>/emailAddress=xxx@yyy.com"
These commands generate the following files on the EPAP A server:
[admusr@mps-A certificate]$ ls –lrt -rw-r----- 1 root root 1679 May 21 11:08 server_bkprov_v4.key -rw-r----- 1 root root 968 May 21 11:08 server_bkprov_v4.csr -rw-r----- 1 root root 1675 May 21 11:09 server_bkprov_v6.key -rw-r----- 1 root root 968 May 21 11:09 server_bkprov_v6.csr - If both certificate files have been generated for the same IP address (either IPv4 or IPv6), enter the following commands:
- Generate certificate signing request (CSR) and private key files for the EPAP B server in the same way (steps 1- 7), using the files serverB_bkprov_v4.csrandserverB_bkprov_v6.csr for EPAP B.
The following files will be generated on the EPAP B server:
[admusr@mps-B certificate]$ ls –lrt -rw-r----- 1 root root 1679 May 21 11:02 server_bkprov_v4.key -rw-r----- 1 root root 968 May 21 11:02 serverB_bkprov_v4.csr -rw-r----- 1 root root 1679 May 21 11:02 server_bkprov_v6.key -rw-r----- 1 root root 968 May 21 11:02 serverB_bkprov_v6.csr - Send the generated CSR files (server_bkprov_v4.csr,server_bkprov_v6.csr,serverB_bkprov_v4.csrandserverB_bkprov_v6.csr ) to the CA. The CA will provide signed certificate files ( server_bkprov_v4.crt , server_bkprov_v6.crt, serverB_bkprov_v4.crt, serverB_bkprov_v6.crt) in return.
- Copy the appropriate files to the appropriate
ssldirectory, and rename as needed:- On the EPAP A server, copy the four files generated through the openssl commands ( server_bkprov_v4.key, server_bkprov_v6.key, server_bkprov_v4.csr, server_bkprov_v6.csr) and the two files provided by the CA for the EPAP A server ( server_bkprov_v4.crt and server_bkprov_v6.crt) to the
/usr/TKLC/plat/etc/ssldirectory. - On the EPAP B server, copy the four files generated through the openssl commands ( server_bkprov_v4.key, server_bkprov_v6.key, serverB_bkprov_v4.csr, serverB_bkprov_v6.csr) and the two files provided by the CA for the EPAP B server ( serverB_bkprov_v4.crt and serverB_bkprov_v6.crt) to the
/usr/TKLC/plat/etc/ssldirectory. - After copying serverB_bkprov_v4.crt and serverB_bkprov_v6.crt to the
/usr/TKLC/plat/etc/ssldirectory on the EPAP B server, rename them to server_bkprov_v4.crt and server_bkprov_v6.crt, respectively.
- On the EPAP A server, copy the four files generated through the openssl commands ( server_bkprov_v4.key, server_bkprov_v6.key, server_bkprov_v4.csr, server_bkprov_v6.csr) and the two files provided by the CA for the EPAP A server ( server_bkprov_v4.crt and server_bkprov_v6.crt) to the
- Restart the httpd service on both the EPAP A and B servers by using the following
commands:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Open the EPAP A and B GUIs using https and install the SSL certificates.
- For IPv4, use the following commands:
https://<EPAP A GUI IPv4 IP> https://<EPAP B GUI IPv4 IP> - For IPv6, use the following commands:
https://[<EPAP A GUI IPv6 IP>] https://[<EPAP B GUI IPv6 IP>]
- For IPv4, use the following commands:
- Verify that the EPAP A and B GUIs opened successfully with the installed certificate.
- If the EPAP GUI does not open, follow these steps on the EPAP A and B servers:
- Open the
/etc/httpd/conf.d/ssl.conffile:[admusr@mps-A certificate]$ sudo vi /etc/httpd/conf.d/ssl.conf - Edit
/etc/httpd/conf.d/ssl.confand un-comment the appropriate code:- If the CA provides ca.crt (CA intermediate certificate), change from:
to:#SSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crtSSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crt - If the CA provides CA certificate(s), change from:
to:#SSLCACertificatePath /etc/httpd/conf/ca-cert #SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crtSSLCACertificatePath /etc/httpd/conf/ca-cert SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crt
- If the CA provides ca.crt (CA intermediate certificate), change from:
- Make sure that these files (CA certs) are copied to the right path on both servers, as mentioned in
/etc/httpd/conf.d/ssl.conf. - Restart the httpd service using the following command on both
servers:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Verify that the EPAP A and B GUIs open successfully.
- Open the
3.10 Installing an SSL Certificate For a VIP With Customized Parameters
Perform the following steps to install an SSL certificate for a Virtual IP (VIP) with customized parameters:
- When the EPAP is configured in IPv4 configuration, log in to EPAP A as admusr.
- Switch to the root user as "su -".
- Change the directory to
/usr/TKLC/plat/etc/ssl/. - Execute the following command to list the files in the directory
/usr/TKLC/plat/etc/ssl/.Sample output for the previous command:
[admusr@mps-A ssl]$ ls -ltrh server_vip_v* -rw-r----- 1 root epap 1.7K May 25 03:34 server_vip_v4.key -rw-r----- 1 root epap 1.1K May 25 03:34 server_vip_v4.crt - Exit from the root user:
[admusr@mps-A ssl]$ exit logoutThe certificate file server_vip_v4.crt is present in the directory
/usr/TKLC/plat/etc/ssl/. Continue with the next step to sign the certificate after exiting from the root user. - Sign the certificate files on the EPAP A server according to the determined network configuration information:
The certificate file server_vip_v4.crt is generated, as the VIP is configured in IPv4 configuration. Sign the certificate file using the following command:
sudo /usr/bin/openssl req –x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire> –subj "/CN=<EPAP A VIP IPv4 address >" -newkey rsa:<RSA Key Management> -keyout /usr/TKLC/plat/etc/ssl/server_vip_v4.key -out /usr/TKLC/plat/etc/ssl/server_vip_v4.crt - Sign the certificate files on the EPAP B server in the same way.
- Restart the httpd service on both the EPAP A and B servers by using the following
commands:
[admusr@mps-A ~]$ sudo systemctl restart httpd [admusr@mps-B ~]$ sudo systemctl restart httpd - Open the GUI using VIP IPv4 IP using https and install the SSL certificate using the following command:
https://<EPAP A VIP IPv4 IP> - Verify that the certificate installed successfully and the GUI opened successfully.
- If the EPAP GUI does not open on the EPAP A server, follow these steps to reconfigure the VIP IP addresses on EPAP through the epapconfig menu. This will re-install the SSL certificates with the default parameters:
[admusr@mps-A ~]$ sudo su – epapconfig- Enter choice 2 to access the Configure Network Interfaces Menu:
/-------EPAP Configuration Menu--------\ /----------------------------------------\ | 1 | Display Configuration | |----|-----------------------------------| | 2 | Configure Network Interfaces Menu | |----|-----------------------------------| | 3 | Set Time Zone | |----|-----------------------------------| | 4 | Exchange Secure Shell Keys | |----|-----------------------------------| | 5 | Change Password | |----|-----------------------------------| | 6 | Platform Menu | |----|-----------------------------------| | 7 | Configure NTP Server | |----|-----------------------------------| | 8 | PDB Configuration Menu | |----|-----------------------------------| | 9 | Security | |----|-----------------------------------| | 10 | SNMP Configuration | |----|-----------------------------------| | 11 | Configure Alarm Feed | |----|-----------------------------------| | 12 | Configure Query Server | |----|-----------------------------------| | 13 | Configure Query Server Alarm Feed | |----|-----------------------------------| | 14 | Configure SNMP Agent Community | |----|-----------------------------------| | 15 | Mate Disaster Recovery | |----|-----------------------------------| | e | Exit | \----------------------------------------/ Enter Choice: 2 - Enter choice 6 to Configure Provisioning VIP Addresses:
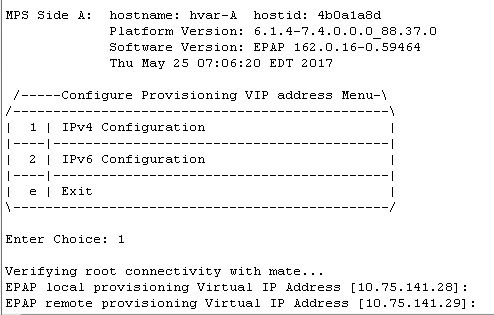
- Press Enter to reconfigure the network with the same configuration.
- If you need assistance, contact unresolvable-reference.html#GUID-06251C83-E21A-4DB7-B8DE-227FC0FCE6E1.
- Enter choice 2 to access the Configure Network Interfaces Menu:
3.11 Installing an SSL Certificate For a VIP From a Trusted Certificate Authority
Perform the following steps to install an SSL certificate for a Virtual IP (VIP) from a trusted Certificate Authority (CA):
- Log in as the admusr user on both the EPAP A and B servers, create a new certificate directory (
/var/TKLC/epap/free/), provide permissions to the new directory, and change to the new directory:[admusr@mps-A ~]$ pwd /home/admusr [admusr@mps-A ~]$ sudo mkdir /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ sudo chmod 777 /var/TKLC/epap/free/certificate [admusr@mps-A ~]$ cd /var/TKLC/epap/free/certificate - When the EPAP is configured in IPv4 configuration, log in to EPAP A as admusr.
- Switch to the root user as "su -".
- Change the directory to
/usr/TKLC/plat/etc/ssl/. - Execute the following command to list the files in the directory
/usr/TKLC/plat/etc/ssl/.Sample output for the previous command:
[admusr@mps-A ssl]$ ls -ltrh server_vip_v* -rw-r----- 1 root epap 1.7K May 25 03:34 server_vip_v4.key -rw-r----- 1 root epap 1.1K May 25 03:34 server_vip_v4.crt - Exit from the root user:
[admusr@mps-A ssl]$ exit logoutThe certificate file server_vip_v4.crt is present in the directory
/usr/TKLC/plat/etc/ssl/. Continue with the next step to sign the certificate after exiting from the root user. - Generate certificate signing request (CSR) and private key files for EPAP A server using the following commands from within the certificate directory.
The certificate file server_vip_v4.crt is generated since the VIP is configured in IPv4 configuration. Enter the following commands on EPAP A server:
sudo /usr/bin/openssl req -x509 -sha<SHA Hash> -nodes -days <No of days to certify the certificate for, after which the certificate shall expire > -newkey rsa:2048 -nodes –keyout server_vip_v4.key –out server_vip_v4.csr -subj "/C=US/ST=New York/L=Brooklyn/O=Example Brooklyn Company/OU=Example Org Unit/CN=<EPAP VIP IPv4 address>/emailAddress=xxx@yyy.com"Note:
The -subj option in the following commands has example fields, which must be replaced with your organization-specific domain information. The /C field is for your country, /ST is for state, /L is for location, /O is for organization, /OU is for organizational unit, and /CN is the common name field, which is the IP address or fully-qualified domain name that you want to use with your certificate.These commands generate the following files on the EPAP A server:
[admusr@mps-A certificate]$ ls –lrt -rw-r----- 1 root root 1679 May 21 11:08 server_vip_v4.key -rw-r----- 1 root root 968 May 21 11:08 server_vip_v4.csr - Generate certificate signing request (CSR) and private key files for EPAP B server by executing steps 1 to 7. Sign the certificate files on the EPAP B server in the same way. Use the files serverB_vip_v4.csr and serverB_vip_v6.csr for EPAP B.
These commands generate the following files on the EPAP B server:
[admusr@mps-B certificate]$ ls –lrt -rw-r--r-- 1 root root 1679 May 21 11:02 server_vip_v4.key -rw-r--r-- 1 root root 968 May 21 11:02 serverB_vip_v4.csr - Send the generated CSR files (server_vip_v4.csr, serverB_vip_v4.csr) to the CA. The CA will provide signed certificate files (server_vip_v4.crt, serverB_vip_v4.crt) in return.
- Copy the appropriate files to the appropriate ssl directory, and rename as needed:
- On the EPAP A server, copy the two files generated through the openssl commands (server_vip_v4.key,server_vip_v4.csr) and the file provided by the CA (server_vip_v4.crt) to the
/usr/TKLC/plat/etc/ssldirectory. - On the EPAP B server, copy the two files generated through the openssl command ( server_vip_v4.key , serverB_vip_v4.csr ) and the file provided by the CA for the EPAP B server ( serverB_vip_v4.crt ) to the
/usr/TKLC/plat/etc/ssldirectory.
- On the EPAP A server, copy the two files generated through the openssl commands (server_vip_v4.key,server_vip_v4.csr) and the file provided by the CA (server_vip_v4.crt) to the
- After copying server B_vip_v4.crt to the
/usr/TKLC/plat/etc/ssldirectory on the EPAP B server, rename them to server _vip_v4.crt. - Restart the httpd service on both the EPAP A and B servers by using the following
commands:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Open the GUI using VIP IPv4 IP using https and install the SSL certificate using the following command:
https://<EPAP A VIP IPv4 IP> - Verify that the certificate installed successfully and the GUI opened successfully.
- If the EPAP GUI does not open, follow these steps on the EPAP A and B servers:
- Open the
/etc/httpd/conf.d/ssl.conffile:[admusr@mps-A certificate]$ sudo vi /etc/httpd/conf.d/ssl.conf - Edit
/etc/httpd/conf.d/ssl.confand un-comment the appropriate code:- If the CA provides ca.crt (CA intermediate certificate), change from:
to:#SSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crtSSLCertificateChainFile /etc/httpd/conf/ssllcrt/ca.crt - If the CA provides CA certificate(s), change from:
to:#SSLCACertificatePath /etc/httpd/conf/ca-cert #SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crtSSLCACertificatePath /etc/httpd/conf/ca-cert SSLCACertificateFile /usr/share/ssl/certs/ca-bundle.crt
- If the CA provides ca.crt (CA intermediate certificate), change from:
- Make sure that these files (CA certs) are copied to the right path on both servers, as mentioned in
/etc/httpd/conf.d/ssl.conf. - Restart the httpd service using the following command on both
servers:
[admusr@mps-A certificate]$ sudo systemctl restart httpd [admusr@mps-B certificate]$ sudo systemctl restart httpd - Verify that the EPAP A and B GUIs open successfully.
- Open the