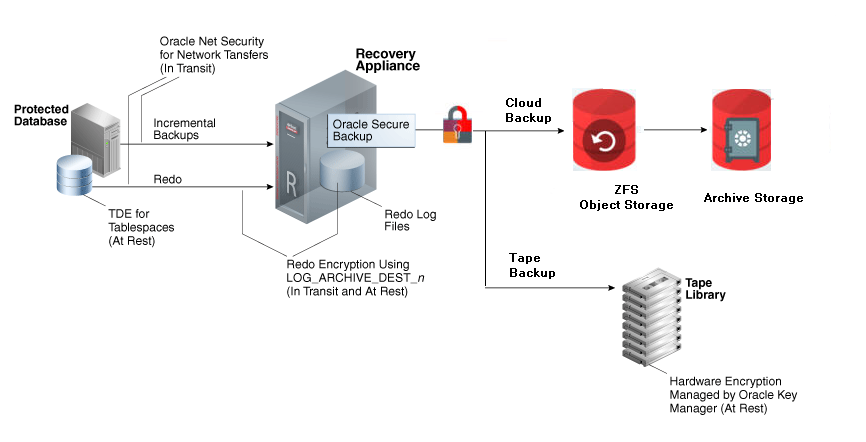
Data Encryption Techniques
Various encryption options are available for backups and redo sent to the Recovery Appliance, as shown in Figure 2-9. The Recovery Appliance does not provide server-side encryption, which means that the appliance does not itself encrypt and decrypt data.
The following types of encryption are supported:
Transparent Data Encryption (TDE) on Production Database Tablespaces
Oracle recommends that you enable TDE on tablespaces in the database, and then take incremental backups as usual. TDE requires the Advanced Security Option. The benefits of TDE are as follows:
-
TDE is transparent to applications.
-
Backups of encrypted tablespaces, and redo describing changes to these tablespaces, are encrypted. The TDE-encrypted data blocks are secured on the protected database, Recovery Appliance storage, tape devices, and replicated appliances, and also when transferred through any network connections.
-
TDE on the source database reduces overhead on downstream servers.
-
TDE supports space-efficient encrypted backups by allowing the data file blocks to be decrypted before they are compressed and then re-encrypted.
-
This technique supports an incremental-forever strategy and virtual full backups.
Note:
Space-efficient encrypted backups are enabled by specifying RA_FORMAT=TRUE in RMAN channel allocation commands with the Recovery Appliance and using SET or CONFIGURE ENCRYPTION command. See "Archival and Encrypted Backups" for more information
The following table shows the support for incremental forever when RMAN encryption and/or RMAN compression are used for the protected database backups:
Table 2-4 Support for Incremental Forever with RMAN Encryption and RMAN Compression
| Data in the Database | No RMAN Encryption and No RMAN Compression | RMAN Encryption | RMAN Compression | RMAN Encryption and RMAN Compression |
|---|---|---|---|---|
| Not Encrypted | Yes; RMAN incremental backups. | No; incremental forever requires RA_FORMAT=TRUE in channel allocation and SET ENCRYPTION ON.
|
Yes; specify RA_FORMAT=TRUE in channel allocation.
|
Yes; specify RA_FORMAT=TRUE in channel allocation and SET ENCRYPTION ON.
|
| TDE Tablespace Encryption | Yes; RMAN incremental backups. | Yes; specify RA_FORMAT=TRUE in channel allocation. TDE backups are always compressed and encrypted.
|
Yes; specify RA_FORMAT=TRUE in channel allocation. TDE backups are always compressed and encrypted.
|
Yes; specify RA_FORMAT=TRUE in channel allocation and SET ENCRYPTION ON.
|
See Also:
-
Oracle Database Advanced Security Guide to learn about TDE
-
Oracle Database Backup and Recovery User’s Guide to learn about configuring backup encryption
-
Oracle Database Backup and Recovery User’s Guide to learn about making compressed backups
Redo Encryption Using LOG_ARCHIVE_DEST_n
When enabled, the ENCRYPTION attribute of LOG_ARCHIVE_DEST_n encrypts redo both at rest on the Recovery Appliance and during the network transfer to the appliance. The basic process is as follows:
-
The protected database encrypts the redo in memory, using the private key contained in the Oracle Wallet on the protected database.
-
The protected database transfers the redo to the Recovery Appliance over the network.
Note:
If Oracle Net security is also enabled, then the redo is double encrypted during network transfer.
-
The Recovery Appliance writes the encrypted redo to archived redo log files, which exist in encrypted form only on the Recovery Appliance.
In a recovery scenario, RMAN restores and decrypts the encrypted redo log files on the protected database, using the encryption key stored in the Oracle wallet on the protected database host (not on the Recovery Appliance). RMAN never applies encrypted redo log files during media recovery.
See Also:
-
My Oracle Support Note Doc ID KB439308 for versions of Oracle AI Database that support encrypted redo
-
Oracle Data Guard Concepts and Administration to learn about redo encryption using
LOG_ARCHIVE_DEST_n
Tape Drive-Based Hardware Encryption
The Recovery Appliance supports tape drive-based hardware encryption. In this case, the tape drive encrypts the data, not the software.
Note:
Oracle Secure Backup can encrypt backup pieces before Recovery Appliance copies them to tape. However, Oracle does not recommend software-based encryption because of its possible negative effect on performance.
For key management, Oracle recommends Oracle Key Manager, which centrally authorizes, secures, and manages all encryption keys. Oracle Key Manager does not consume CPU on the Recovery Appliance when encrypting and decrypting data.
See Also:
Oracle Secure Backup Administrator's Guide to learn about hardware encryption