6 Integrating Audit with Oracle Platform Security Services (OPSS)
Note:
Before setting up single point security, ensure that you are familiar with the Tuxedo security architecture and requirements. You may also want to coordinate this effort with your OPSS Administrator.6.1 Overview
Oracle Tuxedo can integrate with Oracle Platform Security Services (OPSS) audit component. This integration assures you taking all advantages that OPSS has for audit analysis and reporting.
This feature provides you:
- Rich Data for Business Intelligence Analysis
Integrated with OPSS audit component, Oracle Tuxedo can generate rich data centrally stored in an audit sotre. You can then continue to use diverse BI tools (such as OPSS) to view and analyze the data using Oracle Business Intelligence Publisher and the like.
- Customized Audit Strategies/Policies
This feature enables you to generate data for specific events by defining these events on a static XML file (
component_events.xml), which makes it very convenient for you to change audit strategies/policies without affecting the application. - Easy Approach to Use
OPSS provides an abstraction layer in the form of standards-based application programming interfaces (APIs) that insulate you from security and identity management implementation details. With the integration with OPSS audit component, Oracle Tuxedo can directly use these OPSS APIs for auditing; you do not need to write a single line of audit-related code, or change any of your existing code.
6.2 Components and Deployment
6.2.1 Audit Flow
This figure illustrates you an Oracle Tuxedo event flow with OPSS audit framework when an event (such as tpcall) occurs.
Figure 6-1 Oracle Tuxedo Audit Flow with OPSS
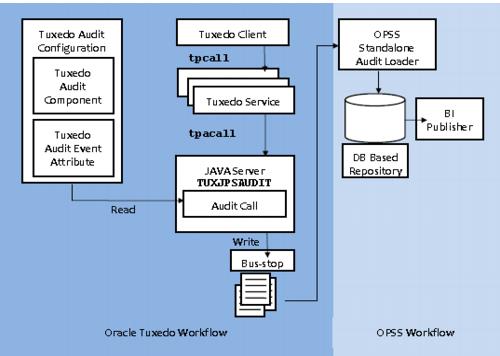
- Oracle Tuxedo Part
- This part requires you to configure Oracle Tuxedo as Configurations instructs. On this figure, an Oracle Tuxedo client invokes an Oracle Tuxedo service. This service then sends a request (also known as "an event") to Oracle Tuxedo Java Server, which has already configured OPSS audit module (
.TUXJPSAUDIT). This module then invokes OPSS audit APIs, which check if this event should be audited. If it should be, this module audits it to a local file in an intermediate location (known as the "bus-stop"), creating the audit event structure and collecting event information such as status, initiator, resource, and ECID. - OPSS Part
- This part requires you to configure OPSS standalone Audit Loader. Once OPSS APIs audit an event to the bus-stop, OPSS Audit Loader collects the audit records throughout all components running in the instance. If a database is configured for an audit store, the OPSS Audit Loader pulls the event from bus-stop and moves its data to audit store.
Parent topic: Components and Deployment
6.3 Configurations
Do the following to configure Oracle Tuxedo for this feature:
6.3.1 Register OPSS Audit Plug-In to Oracle Tuxedo Registry
Oracle Tuxedo registry is a disk-based repository for storing information related to plug-in modules. Initially, this registry holds registration information about the default security plug-ins; now that you want to use this feature, you must configure this registry for the OPSS plug-in before installing it.
-
Register OPSS Audit Plug-In to Oracle Tuxedo Registry
If you do not want to use this feature any more, you can
- Unregister OPSS Audit Plug-In from Oracle Tuxedo Registry
- Register OPSS Audit Plug-In to Oracle Tuxedo Registry
- Unregister OPSS Audit Plug-In from Oracle Tuxedo Registry
Parent topic: Configurations
6.3.1.1 Register OPSS Audit Plug-In to Oracle Tuxedo Registry
You must use epifreg tool to register OPSS plug-ins
for Oracle Tuxedo registry. Registering OPSS plug-in will replace
the default Oracle Tuxedo audit implement from ULOG to OPSS
audit.
The following listing describes an example.
Listing Example for Registering OPSS Audit Plug-In to Oracle Tuxedo Registry
epifregedt -s -k "SYSTEM/impl/bea/native/audfan" -a InterceptionSeq=bea/native/audopssepifreg -r -p bea/native/audopss -i engine/security/auditing -v 1.0 -f libtux.so -e _ep_dl_audopssUse the following shell script tools located at
$TUXDIR/bin for registering OPSS audit plug-in to
Oracle Tuxedo registry:
-
opssreg.batCommand of registering OPSS Audit Plug-In for Oracle Tuxedo on windows platforms.
-
opssreg.shCommand of registering OPSS Audit Plug-In for Oracle Tuxedo on UNIX platforms.
Parent topic: Register OPSS Audit Plug-In to Oracle Tuxedo Registry
6.3.1.2 Unregister OPSS Audit Plug-In from Oracle Tuxedo Registry
You should use epifunregtool to unregister OPSS plug-in from Oracle Tuxedo
registry. Unregistering OPSS plug-in will restore the default Oracle Tuxedo audit implement
back to ULOG.
The following listing describes an example.
Listing Example for Unregistering OPSS Audit Plug-In from Oracle Tuxedo Registry
epifunreg -p bea/native/audopssUse the following shell script tools located at .$TUXDIR/bin for
unregistering OPSS audit plug-in from Oracle Tuxedo registry:
-
opssunreg.batCommand of unregistering OPSS Plug-In for Oracle Tuxedo on windows platforms.
-
opssunreg.shCommand of unregistering OPSS Plug-In for Oracle Tuxedo on UNIX platforms.
Parent topic: Register OPSS Audit Plug-In to Oracle Tuxedo Registry
6.3.2 Configure Oracle Tuxedo Auditing Framework
This feature requires you to create Oracle Tuxedo Auditing framework.
- Add OPSS Audit to Oracle Tuxedo Plug-In Framework
Follow Oracle Tuxedo Auditing configuration rules to add OPSS audit to Tuxedo Plug-in framework. See Auditing for more information.
- Configure Security Options in
UBBCONFIGIn
UBBCONFIGRESOURCESsection, setSECURITYoption toACLorMANDATORY_ACL.
Parent topic: Configurations
6.3.3 Configure Oracle Tuxedo OPSS Audit Module
This feature requires to configure Oracle Tuxedo OPSS Audit Module.
Parent topic: Configurations
6.3.3.1 Configure Oracle Tuxedo Java Server (TMJAVASVR)
Oracle Tuxedo OPSS Audit Module runs in Oracle Tuxedo Java server (TMJAVASVR), so TMJAVASVR must be configured in your UBBCONFIG. TMJAVASVR handles the entire audit request, advertising audit module .TUXJPSAUDIT, which acts as a bridge between Oracle Tuxedo system with OPSS audit and Oracle Tuxedo application services. The following listing describes an example for configuring TMJAVASVR in UBBCONFIG SERVERS section.
TMJAVASVR can
- Read configuration file
tpopss_audit.xml. - Advertise audit module
.TUXJPSAUDIT, which is implemented with Java code according totpopss_audit.xml. - Launch JVM.
- Forward an audit request to .TUXJPSAUDIT.
- Get and execute the results from this .TUXJPSAUDIT.
Listing TMJAVASVR Configuration Example
*SERVERS
TMJAVASVR
SRVGRP=TJSVRGRP SRVID=3
CLOPT="-- -c/home/oracle/app/javaserver/tpopss_audit.xml"
MINDISPATCHTHREADS=2 MAXDISPATCHTHREADS=3Parent topic: Configure Oracle Tuxedo OPSS Audit Module
6.3.3.2 Configure Oracle Tuxedo OPSS Audit Module
Now that you have configured TMJAVASVR, you can
configure Oracle Tuxedo OPSS Audit Module in Oracle Tuxedo Java
Server Configuration File called tpospss_audit.xml,
which you can find in
${TUXDIR}/udataobj/tuxj/opss.
Two packages that Oracle Tuxedo Java Server uses for this feature are com.oracle.tuxedo.tjopss_12.2.2.0.jar (Oracle Tuxedo ships it and it is located in ${TUXDIR}/udataobj/tuxj/opss) and opss-manifest.jar (OPSS ships it and it is located in the path where -Dcommon.components.home specifies. For example, if you specify -Dcommon.components.home=/testarea/tuxuser/opss_standalone/, this opss-manifest.jar is located in /testarea/tuxuser/opss_standalone/modules/oracle.jps_12.1.2/opss-manifest.jar).
The listing for an example, where the following attributes are specified.
6.3.3.2.1 java-config
Declare the following jvm-options attributes, and ensure that every path you set is an absolute path.
- Required
jvm-optionsare-
-Doracle.security.jps.configThis declares the absolute path of OPSS configuration file
jps-config.xml. -
-Djava.security.policyThis declares the absolute path of
java.policy. -
-Doracle.tuxedo.opss.event.config.dirThis declares the absolute path of
component_events.xml. -
-Doracle.tuxedo.audit.typeThis declares the component type of
TMJAVASVR.TUXJPSAUDIT, determining which component table stores the record to the bus-stop. -
-Doracle.tuxedo.audit.categoryThis declares the component event category of
TMJAVASVR.TUXJPSAUDIT. -
-Dcommon.components.homeThis declares the absolute path of OPSS component home directory.
-
- Optional
jvm-optionsare-
-Djps.auth.debug -
-Djps.auth.debug.verbose
If these two jvm-options are set to true, JPS debug/trace functions are open.
-
Parent topic: Configure Oracle Tuxedo OPSS Audit Module
6.3.3.2.2 classpath-config
Declare the following classpath attributes, and make sure every path you set
is an absolute path.
-
com.oracle.tuxedo.tjopss_12.2.2.0.jarOracle Tuxedo ships
com.oracle.tuxedo.tjopss_12.2.2.0.jarto integrate OPSS Audit module. This library is located at$TUXDIR/udataobj/tuxj/opss.You should declare this path in
<classpath-config>classpathattribute intpopss_audit.xml. -
opss-manifest.jarOracle OPSS module ships
opss-manifest.jar.You should declare this path in
<classpath-config>classpathattribute intpopss_audit.xml.
Listing Example for tpopss_audit.xml
<?xml version="1.0" encoding="UTF-8"?>
<TJSconfig version="2.0">
<!--
do not forget modify $TUXDIR $COMMON_COMPONENTS_HOME $APPDIR to absolute path
-->
<java-config>
<jvm-options>-Dtuxedo.tjatmi.strictly_check=yes</jvm-options>
<jvm-options>-Doracle.security.jps.config=${TUXDIR}/udataobj/tuxj/opss/jps
-config.xml</jvm-options>
<jvm-options>-Djava.security.policy=${TUXDIR}/udataobj/tuxj/opss/java.poli
cy</jvm-options>
<jvm-options>-Doracle.tuxedo.opss.event.config.dir=${TUXDIR}/udataobj/tuxj
/opss/</jvm-options>
<jvm-options>-Doracle.tuxedo.audit.type=tuxedo_opss_template</jvm-options>
<jvm-options>-Doracle.tuxedo.audit.category=TUXEDOOPSSAUDIT</jvm-options>
<jvm-options>-Dcommon.components.home=${COMMON_COMPONENTS_HOME}</jvm-options>
<jvm-options>-Djps.auth.debug=true</jvm-options>
<jvm-options>-Djps.auth.debug.verbose=true</jvm-options>
</java-config>
<classpath-config>
<classpath>${TUXDIR}/udataobj/tuxj/opss/com.oracle.tuxedo.tjopss_13.1.1.0.
jar</classpath>
<classpath>${COMMON_COMPONENTS_HOME}/modules/oracle.jps_12.1.2/opss-manifest.jar</classpath>
</classpath-config>
<tux-server-config>
<server-class name="TuxAuditServer"/>
</tux-server-config>
</TJSconfig>Parent topic: Configure Oracle Tuxedo OPSS Audit Module
6.3.4 Configure OPSS Configuration Files
This feature requires you to configure the following OPSS
configuration files. All of them are located at
$TUXDIR/udataobj/tuxj/opss.
- jps-config.xml
- java.policy
- component_events.xml (static) and audit-store.xml (dynamic)
- system-jazn-data.xml
Parent topic: Configurations
6.3.4.1 jps-config.xml
Oracle Tuxedo integrates with the Oracle Fusion Middleware Audit Framework through jps-config.xml runtime configuration file, which contains the initial filter settings for using OPSS Audit Plug-In. You should declare its absolute path in tpopss_audit.xml configuration file (jvm-options: -Doracle.security.jps.config). See Configure Oracle Tuxedo OPSS Audit Module for more information.
See the following listing describes for an example, where jps-config.xml declares serviceInstance audit, whose provider is audit.provider and location is ./audit-store.xml.
Listing jps-config.xml Example
<?xml version="1.0" encoding="UTF-8" standalone="yes"?>
<jpsConfig xmlns="http://xmlns.oracle.com/oracleas/schema/11/jps-config-11_1.xsd"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" schema-major-version="11" schema-minor-version="1"
xsi:schemaLocation="http://xmlns.oracle.com/oracleas/schema/11/jps-config-11_1.xsd jps-config-11_1.xsd">
<property name="oracle.security.jps.jaas.mode" value="off"/>
<property name="oracle.security.jps.enterprise.user.class"
value="weblogic.security.principal.WLSUserImpl"/>
<property name="oracle.security.jps.enterprise.role.class"
value="weblogic.security.principal.WLSGroupImpl"/>
<propertySets>
<propertySet name="saml.trusted.issuers.1">
<property name="name" value="www.oracle.com"/>
</propertySet>
<propertySet name="trust.provider.embedded">
<property name="trust.provider.className"
value="oracle.security.jps.internal.trust.provider.embedded.EmbeddedProviderImpl"/>
<property name="trust.clockSkew" value="60"/>
<property name="trust.token.validityPeriod" value="1800"/>
<property name="trust.token.includeCertificate" value="false"/>
</propertySet>
</propertySets>
<serviceProviders>
<serviceProvider type="POLICY_STORE" name="policystore.xml.provider"
class="oracle.security.jps.internal.policystore.xml.XmlPolicyStoreProvider">
<description>XML-based PolicyStore Provider</description>
</serviceProvider>
<serviceProvider type="AUDIT" name="audit.provider"
class="oracle.security.jps.internal.audit.AuditProvider">
<description>Audit Service</description>
</serviceProvider>
</serviceProviders>
<serviceInstances>
<serviceInstance name="policystore.xml"
provider="policystore.xml.provider" location="./system-jazn-data.xml">
<description>File Based Policy Store Service
Instance</description>
</serviceInstance>
<serviceInstance name="audit" provider="audit.provider" location="./audit-store.xml">
<description>Audit Service</description>
<property name="audit.filterPreset" value="None"/>
<property name="audit.maxDirSize" value="0"/>
<property name="audit.maxFileSize" value="104857600"/>
<property name="audit.timezone" value="utc"/>
<property name="audit.loader.interval" value="15"/>
<property name="audit.loader.repositoryType" value="File"/>
<property name="auditstore.type" value="file"/>
<property name="audit.db.principal.map"
value="AuditDbPrincipalMap"/>
<property name="audit.db.principal.key"
value="AuditDbPrincipalKey"/>
</serviceInstance>
</serviceInstances>
<jpsContexts default="default">
<jpsContext name="default">
<serviceInstanceRef ref="policystore.xml"/>
<serviceInstanceRef ref="audit"/>
</jpsContext>
</jpsContexts>
</jpsConfig>Parent topic: Configure OPSS Configuration Files
6.3.4.2 java.policy
java.policy is the system policy file to grant system-wide code permissions; this policy is represented by a Policy object for Java programming language application environment (specifying which permissions are available for code from various sources, and executing as various principals). For this feature in particular, you should use this file to grant audit store access permissions to all domains invoke OPSS Audit APIs. You must declare its absolute path in tpopss_audit.xml configuration file (jvm-options: -D Djava.security.policy). See Configure Oracle Tuxedo OPSS Audit Module for more information. See the following listing for an example, where the following two grants are specifically added for this feature.
- This is to grant permissions to
file:${common.components.home}/modules/oracle.jps_12.1.2/*, whereopss-manifest.jaris located.grant codeBase "file:${common.components.home}/modules/oracle.jps_12.1.2/*" { permission java.security.AllPermission; }; - This is to grant permissions to
file:${oracle.deployed.app.dir}/*, where required configuration files (tpopss_audit.xml,jps-config.xml,component_events.xml,audit-store.xml,java.policy, andsystem-jazn-data.xml) are located.grant codeBase "file:${oracle.deployed.app.dir}/*" { permission java.security.AllPermission; };
// Standard extensions get all permissions by default
grant codeBase "file:${{java.ext.dirs}}/*" {
permission java.security.AllPermission;
};
// default permissions granted to all domains
grant {
// Allows any thread to stop itself using the java.lang.Thread.stop()
// method that takes no argument.
// Note that this permission is granted by default only to remain
// backwards compatible.
// It is strongly recommended that you either remove this permission
// from this policy file or further restrict it to code sources
// that you specify, because Thread.stop() is potentially unsafe.
// See "http://java.sun.com/notes" for more information.
permission java.lang.RuntimePermission "stopThread";
// allows anyone to listen on un-privileged ports permission
java.net.SocketPermission "localhost:1024-", "listen";
// "standard" properies that can be read by anyone
permission java.util.PropertyPermission "java.version", "read";
permission java.util.PropertyPermission "java.vendor", "read";
permission java.util.PropertyPermission "java.vendor.url", "read";
permission java.util.PropertyPermission "java.class.version", "read";
permission java.util.PropertyPermission "os.name", "read";
permission java.util.PropertyPermission "os.version", "read";
permission java.util.PropertyPermission "os.arch", "read";
permission java.util.PropertyPermission "file.separator", "read";
permission java.util.PropertyPermission "path.separator", "read";
permission java.util.PropertyPermission "line.separator", "read";
permission java.util.PropertyPermission "java.specification.version", "read";
permission java.util.PropertyPermission "java.specification.vendor", "read";
permission java.util.PropertyPermission "java.specification.name", "read";
permission java.util.PropertyPermission "java.vm.specification.version", "read";
permission java.util.PropertyPermission "java.vm.specification.vendor", "read";
permission java.util.PropertyPermission "java.vm.specification.name", "read";
permission java.util.PropertyPermission "java.vm.version", "read";
permission java.util.PropertyPermission "java.vm.vendor", "read";
permission java.util.PropertyPermission "java.vm.name", "read";
};
grant codeBase
"file:${common.components.home}/modules/oracle.jps_12.1.2/*"
permission java.security.AllPermission;
{;
grant codeBase "file:${common.components.home}/modules/oracle.iau_12.1.2/*" {
permission java.security.AllPermission;
};
grant codeBase "file:${classpath}/*" {
permission java.security.AllPermission;
};
grant codeBase "file:${oracle.deployed.app.dir}/*" {
permission java.security.AllPermission;
};
grant codeBase "file:${TUXDIR}/udataobj/tuxj/opss/*" {
permissionjava.security.AllPermission;
};
grant codeBase "file:${TUXDIR}/udataobj/tuxj/*" {
permission java.security.AllPermission; };Parent topic: Configure OPSS Configuration Files
6.3.4.3 component_events.xml (static) and audit-store.xml (dynamic)
component_events.xml is a static file that defines
all the audit events that are generated by the OPSS Audit Plug-In;
audit-store.xml is the dynamic file that defines all
the audit events that are mapped from the static file
component_events.xml.
After tmboot for Oracle Tuxedo audit module
.TUXJPSAUDIT, audit policy for a specific component is
stored in audit-store.xml. .TUXJPSAUDIT
automatically registers the event component, and maps it from
component_events.xml to audit-store.xml;
after automatically un-registering the event component,
.TUXJPSAUDIT drops it from
audit-store.xml.
Note:
As Oracle Tuxedo depends on OPSS stand-alone component,audit-store.xml is actually the file that is mainly used for this feature. Nevertheless, you are still required to use the static file component_events.xml to adjust your audit policy and specify component_events.xml in your CLASSPATH. See Change Audit Policy for more information.
You must declare the absolute path for component_events.xml in tpopss_audit.xml configuration file (jvm-options: -Doracle.tuxedo.opss.event.config.dir). See Configure Oracle Tuxedo OPSS Audit Module for more information.
In component_events.xml configuration file, you
must set:
-
componentTypeAudit-Aware Components, referring to components that are integrated with the Oracle Fusion Middleware Audit Framework so that audit policies can be configured and events can be audited for these components. You should also set
componentTypeintpopss_audit.xml(jvm-options:-Doracle.tuxedo.audit.type). -
categoryAn audit event category contains related events in a functional area. Attributes are categorized into base. You should also set
categoryintpopss_audit.xml(jvm-options:-Doracle.tuxedo.audit.category).See the following listing for an example, where
-
componentTypeis set totuxedo_opss_template(the same as "<jvm-options>-Doracle.tuxedo.audit.type=tuxedo_opss_template</jvm-options>"). -
categoryis set toTUXEDOOPSSAUDIT(the same as "<jvm-options>-Doracle.tuxedo.audit.category=TUXEDOOPSSAUDIT</jvm-options>").
Listing component_events.xml Example
<?xml version="1.0" encoding="UTF-8"?><AuditConfig
xmlns="http://xmlns.oracle.com/ias/audit/audit-2.0.xsd">
<AuditComponent minor="0" major="1" componentType="tuxedo_opss_template">
<Attributes version="1.0" ns="tuxedo_opss_template">
<Attribute order="1" displayName="visitor ID" required="true" searchable="true" maxLength="255" type="string" name="visitorid">
<HelpText>Visitor ID</HelpText>
</Attribute>
<Attribute order="2" displayName="Start Time" required="true" searchable="true" maxLength="2048" type="dateTime"name="starttime"> <HelpText>The time a visitor enters.</HelpText> </Attribute> <Attribute order="3"
displayName="End Time" required="true" searchable="true"
maxLength="2048" type="dateTime" name="endtime">
<HelpText>the time a visitor exists.</HelpText>
</Attribute><Attribute order="4" displayName="Service
Charge" required="true" searchable="true" maxLength="2048"
type="float" name="fee"> <HelpText>the dollar amount a
visitor pays.</HelpText> </Attribute><Attribute
order="5" displayName="Service Item" required="true"
searchable="true" maxLength="2048" type="float" name="item">
<HelpText>the name of an item a visitor
borrows.</HelpText>
</Attribute></Attributes><Events>
<Category displayName="TUXEDOOPSSAUDIT" name="TUXEDOOPSSAUDIT">
<Attributes>
<Attribute version="1.1" ns="common" name="EventType">
<HelpText>The type of the audit event. Use wlst listAuditEvents to list out all the events.</HelpText>
</Attribute>
<Attribute version="1.0" ns="tuxedo_opss_template" name="visitorid">
<HelpText>Visitor ID</HelpText>
</Attribute>
<Attribute version="1.0" ns="tuxedo_opss_template"
name="starttime"> <HelpText> The time a visitor centers.</HelpText>
</Attribute>
<Attribute version="1.0" ns="tuxedo_opss_template" name="endtime">
<HelpText>the time a visitor exists.</HelpText>
</Attribute>
</Attributes>
<HelpText>TUXEDOOPSSAUDIT category</HelpText> <Event displayName="SERVICECALL" name="SERVICECALL">
<HelpText>A service call enters the facility.</HelpText>
</Event>
<Event displayName="ENQUEUE" name="ENQUEUE">
<HelpText>A enqueue enters the facility.</HelpText>
</Event> <Event displayName="DEQUEUE" name="DEQUEUE">
<HelpText>A dequeue enters the facility.</HelpText>
</Event> <Event displayName="POST" name="POST">
<HelpText>A post call enters the facility.</HelpText>
</Event> <Event displayName="CONNECT" name="CONNECT">
<HelpText>A connect enters the facility.</HelpText>
</Event>
<Event displayName="IMPERSONATE" name="IMPERSONATE">
<HelpText>A impersonate enters the facility.</HelpText>
</Event>
<Event displayName="LOGON" name="LOGON">
<HelpText>A logon enters the facility.</HelpText>
</Event>
<Event displayName="LOGOFF" name="LOGOFF">
<HelpText>A logoff enters the facility.</HelpText>
</Event>
<Event displayName="DECRYPT" name="DECRYPT">
<HelpText>A decrypt enters the facility.</HelpText>
</Event>
<Event displayName="SERVICESIGNATURE" name="SERVICESIGNATURE">
<HelpText>A service signature enters the facility.</HelpText>
</Event>
<Event displayName="SERVICEENCRYPTION" name="SERVICEENCRYPTION">
<HelpText>A service encryption enters the facility.</HelpText>
</Event>
<Event displayName="QUEUESIGNATURE" name="QUEUESIGNATURE">
<HelpText>A queue signature enters the facility.</HelpText>
</Event>
<Event displayName="EVENTSIGNATURE" name="EVENTSIGNATURE">
<HelpText>A event signature enters the facility.</HelpText>
</Event>
<Event displayName="EVENTENCRYPTION" name="EVENTENCRYPTION">
<HelpText>A event encryption enters the facility.</HelpText>
</Event>
<Event displayName="SIGNATURE" name="SIGNATURE">
<HelpText>A signature enters the facility.</HelpText>
</Event>
<Event displayName="QUEUEENCRYPTION" name="QUEUEENCRYPTION">
<HelpText>A queue encryption enters the facility.</HelpText>
</Event>
<Event displayName="UNKNOWN" name="UNKNOWN"> <HelpText>A unknown enters the facility.</HelpText>
</Event>
</Category> </Events> <FilterPresetDefinitions>
<FilterPresetDefinition helpText="" displayName="Low"
name="Low"> <FilterCategory enabled="partial"
name="TUXEDOOPSSAUDIT">SERVICECALL,ENQUEUE,DEQUEUE,POST,CONNECT,IMPERSONATE,LOGON,LOGOFF,DECRYPT,SERVICESIGNATURE,SERVICEENCRYPTION,QUEUESIGNATURE,QUEUEENCRYPTION,EVENTSIGNATURE,EVENTENCRYPTION,SIGNATURE,UNKNOWN</FilterCategory>
</FilterPresetDefinition> <FilterPresetDefinition
helpText="" displayName="Medium" name="Medium">
<FilterCategory enabled="partial"
name="TUXEDOOPSSAUDIT">SERVICECALL,ENQUEUE,DEQUEUE,POST,CONNECT,IMPERSONATE,LOGON,LOGOFF,DECRYPT,SERVICESIGNATURE,SERVICEENCRYPTION,QUEUESIGNATURE,QUEUEENCRYPTION,EVENTSIGNATURE,EVENTENCRYPTION,SIGNATURE,UNKNOWN</FilterCategory>
</FilterPresetDefinition> </FilterPresetDefinitions>
<Policy filterPreset="Custom">
<CustomFilters>
<FilterCategory enabled="partial"
name="TUXEDOOPSSAUDIT">SERVICECALL,ENQUEUE,DEQUEUE,POST,CONNECT,IMPERSONATE,LOGON,LOGOFF,DECRYPT,SERVICESIGNATURE,SERVICEENCRYPTION,QUEUESIGNATURE,QUEUEENCRYPTION,EVENTSIGNATURE,EVENTENCRYPTION,SIGNATURE,UNKNOWN</FilterCategory>
</CustomFilters>
</Policy>
<AttributesMapping version="1.0" tableName="IAU_CUSTOM" ns="tuxedo_opss_template">
<AttributeColumn datatype="string" column="IAU_STRING_001" attribute="visitorid"/>
<AttributeColumn datatype="dateTime" column="IAU_DATETIME_001" attribute="starttime"/>
<AttributeColumn datatype="dateTime" column="IAU_DATETIME_002" attribute="endtime"/>
<AttributeColumn datatype="float" column="IAU_FLOAT_001" attribute="fee"/>
<AttributeColumn datatype="float" column="IAU_FLOAT_002" attribute="item"/>
</AttributesMapping>
</AuditComponent>
</AuditConfig>Parent topic: Configure OPSS Configuration Files
6.3.4.4 system-jazn-data.xml
system-jazn-data.xml is an OPSS configuration file.
Oracle Tuxdo provides this file by default in
$TUXDIR/udataobj/tuxj/opss, and uses it for this
feature. You should keep this file as it is and should not change
or remove it. See Oracle Fusion Middleware Security Guide for
more information about this file.
Parent topic: Configure OPSS Configuration Files
6.3.5 Configure OPSS Audit Bus-Stop
This feature requires you to configure OPSS audit bus-stop.
OPSS audit bus-stop files are named audit_<rotation_index>.log. You can use underscore ("_") as a separator (current file should not have _<rotation_index>).
The location of audit bus-stop files is currently not
configurable. Oracle Tuxedo OPSS audit bus-stop file locates at the
parent directory of jps-config.xml. For example,
<parent directory of
jps-config.xml>/logs/auditLogs/<componentType>See the following listing for an example.
Listing OPSS Audit Bus-Stop File Example
#Fields:Date Time Initiator EventType EventStatus MessageText AuditUser ApplicationName AuditService:TransactionId ContextFields
DomainName ECID EventCategory FailureCode HomeInstance HostId HostNwaddr MajorVersion MinorVersion RID RemoteIP Resource Roles
SessionId Target TargetComponentType TenantId ThreadId TransactionId UserSession:AuthenticationMethod UserTenantId
tuxedo_opss_template:endtime tuxedo_opss_template:fee tuxedo_opss_template:item tuxedo_opss_template:starttime
tuxedo_opss_template:visitorid
#Remark Values:ComponentType="tuxedo_opss_template" ReleaseVersion="MAIN"
2015-05-12 06:27:39.259 - "SERVICECALL" true "WARN: TUXEDO AUDIT: who = U1, operation_name = SERVICECALL, operation_target = TOUPPER, status = operation success" - - - - - "0000Kp6nelk8TsS_MDS4ye1LKPpR000002,0"
"TUXEDOOPSSAUDIT" - - "wyhbj" "10.182.54.145" "1" "0" - - - - - - - - "12" - - - 2015-05-12 06:27:38.794 - - 2015-05-12 06:27:38.794 "U1"Parent topic: Configurations
6.4 Administration
6.4.1 Change Audit Policy
You can add/remove/change events in the static configuration file component_events.xml to change audit policy at any time. Your audit policy change is effective right after you restart Oracle Tuxedo (after tmboot, .TUXJPSAUDIT automatically update the audit policy in the corresponding dynamic audit-store.xml).
See component_events.xml (static) and audit-store.xml (dynamic) for more information.
Parent topic: Administration