7 Configuring and Managing the Administrative Domain
This chapter explains the basic steps involved in setting up an Oracle Secure Backup administrative domain after initial installation of the product on all of your hosts. Some steps, such as "Adding a Host to the Administrative Domain", are also useful when managing an existing administrative domain.
This chapter contains the following sections:
Overview of Configuring the Administrative Domain
The administrative domain consists of a set of hosts and backup containers that are managed as a single unit by Oracle Secure Backup. The administrative domain enables you to manage backup and restore operations among diverse hosts, devices, and databases.
After you install the Oracle Secure Backup software on all the hosts, except NDMP hosts and NAS filers, in the administrative domain, you must configure the administrative domain. Configuring the administrative domain sets up the environment that is required to create and manage backups.
The instructions in this chapter describe how to configure the administrative domain with host and backup container information using the Web tool. It is assumed that you have installed the Oracle Secure Backup software on each host in the domain, as described in Installing Oracle Secure Backup on Linux or UNIX or Installing Oracle Secure Backup on Windows.
See Also:
Oracle Secure Backup Reference for information about the obtool commands used to configure the administrative domain
The administrative domain is set up using a default security configuration that should be adequate for most users. Further configuration of users, user classes, security options, and the Oracle Secure Backup media management layer for use with Recovery Manager (RMAN) in backing up Oracle databases might be required in some cases.
See Also:
Oracle Secure Backup Administrator's Guide for information about additional security configuration
Network Load Balancing in Oracle Secure Backup
Network load balancing ensures that multiple network connections on a client are utilized optimally and no single connection carries the data load of all the concurrent backup and restore jobs. The transfer load of multiple backup and restore jobs is distributed across the network connections available on the client and media server. Load balancing is available starting with Oracle Secure Backup 10.4 and is supported for both file-system and Oracle Database backup and restore operations. Load balancing is turned off by default.
Note:
Load balancing is not supported for NDMP clients.
Oracle Secure Backup sets up a data connection between the client and the media server over which the data transfer occurs. If a host contains more than one network interface of a particular type, Oracle Secure Backup uses all the available interfaces of that type for the data connections between the client and the media server. The type of network interface can be IPv4, IPv6, or RDS/RDMA (Reliable Datagram Socket over Remote Direct Memory Access) over Infiniband. Load balancing requires connectivity between the client and the media server on all the interfaces of the selected connection type.
Oracle Secure Backup selects a connection type only if both the client and the media server support that connection type. Therefore, if both the client and the media server support RDS/RDMA over Infiniband and the IPv6 connection types, then Oracle Secure Backup selects RDS/RDMA over Infiniband as the connection type.
If a Preferred Network Interface (PNI) is configured, then load balancing is disabled on the media server and PNI takes precedence. Load balancing will still be performed on the client.
Order of Precedence for Network Connection Types
When multiple network connections are available between a client and media server, Oracle Secure Backup decides which connection type to use based on the following order of precedence:
-
RDS/RDMA over Infiniband
-
IPv6
-
IPv4 (includes TCP/IP over Infiniband)
Steps to Configure the Administrative Domain
-
Configure all the hosts in your administrative domain. Hosts include the administrative server, media servers, and clients.
While configuring a host, specify the role that is assigned to the host in the administrative domain.
See Also:
"Steps to Configure Hosts in the Administrative Domain" for information about configuring hosts
-
Add the tape devices in your network to the administrative domain. Tape devices include tape libraries and tape devices.
You can automatically discover tape devices that are attached to media servers in the administrative domain or manually configure each tape device.
See Also:
-
"Overview of Automatic Device Discovery" for information about discovering tape devices
-
"Adding Tape Devices to an Administrative Domain" for information about adding tape devices
-
-
Verify the configuration of tape devices that were added to the administrative domain.
See Also:
"Verifying and Configuring Added Tape Devices" for information about verifying tape devices
-
Configure disk pools in your administrative domain.
See Also:
"Configuring Disk Pools" for information about configuring disk pools
The initial configuration of your administrative domain is complete.
Network communication among hosts in the administrative domain is configured with the default security configuration described in "Default Security Configuration".
Note:
You must still identify files to be backed up in a dataset, configure at least one backup schedule, and set up users, classes, and security policies. These tasks are described in the Oracle Secure Backup Administrator's Guide.
Configuring the Administrative Domain with Hosts
After you install Oracle Secure Backup on all hosts in your administrative domain, you must configure the domain with hosts. You can add hosts to your administrative domain either during the initial administrative domain configuration or when you subsequently define new hosts in your domain.
After the initial configuration, you can manage your hosts and perform tasks such as editing host properties, updating hosts, and removing hosts from the administrative domain.
This section contains these topics:
About Administrative Domain Host Configuration
The host configuration process makes the administrative server aware of a media server or client to be included in the administrative domain. You must perform this process for every host in the administrative domain, including each host running Oracle Secure Backup natively and each network-attached storage device managed by Network Data Management Protocol (NDMP).
For any host to be added to the administrative domain, you must provide the following attributes:
-
Host name
-
IP address
-
Assigned roles: client, media server or both
-
Whether the host is in service or not in service at the moment
After adding a host to the administrative domain, Oracle recommends that you ping the host to confirm that it can be accessed by the administrative server.
See Also:
For hosts that use NDMP access mode, such as network-attached storage devices, you must configure the following additional attributes:
-
NDMP authorization type
-
NDMP password
-
TCP port number for use with NDMP
See Also:
Oracle Secure Backup Reference for a complete account of host attributes
Steps to Configure Hosts in the Administrative Domain
After you install the Oracle Secure Backup software on hosts, use the steps in this section to configure the administrative domain with hosts.
To configure your hosts in the administrative domain:
-
Open the Oracle Secure Backup Web tool running on the administrative server and log in as the
adminuser.See Also:
"Starting a Web Tool Session" for information about accessing the Web tool
-
For each host in your administrative domain that must be set up for the role of media server, perform the following steps:
-
Add the host to the administrative domain by selecting the media server role for the host as described in "Adding a Host to the Administrative Domain".
Note:
If the administrative server is also assigned the media server role, then it is part of the administrative domain. See "Adding the Media Server Role to an Administrative Server" for information about assigning the media server role to the administrative server.
-
Configure the administrative domain to include each tape device attached to this host as described in "Adding Tape Devices to an Administrative Domain" describes this task.
-
Configure the administrative domain to include disk pools as described in "Configuring Disk Pools".
-
-
(Optional) For certain NDMP hosts, you may need to define backup and restore environment variables before the host can function with Oracle Secure Backup.
See Also:
"Adding Backup and Restore Environment Variables to an NDMP Host" for information about defining backup and restore environment variables for NDMP hosts
-
(Optional) For hosts that have multiple physical data paths with the administrative server or media server, you can define a Preferred Network Interface (PNI) that will be used while exchanging backup or restore data with another host.
See Also:
"Configuring Preferred Network Interfaces (PNI)" for information about defining a PNI for your host
-
For each host that is to be set up only for the client role, add the host to the administrative domain by selecting the client role as described in "Adding a Host to the Administrative Domain".
-
Verify that all the hosts that you added to your administrative domain are accessible using the IP address that was configured for the host.
See Also:
"Pinging Hosts in the Administrative Domain" for information about pinging hosts
After you complete the initial configuration of the hosts, you can manage hosts by performing tasks such as editing host properties, updating hosts, and removing hosts from the administrative domain as described in "Managing Hosts in the Administrative Domain".
Adding a Host to the Administrative Domain
You can add a host (media server or client) to the administrative domain either at the time of initial domain configuration or subsequently, when you want to configure additional hosts in your administrative domain.
To add a host to an administrative domain:
Adding the Media Server Role to an Administrative Server
If you choose both the administrative server and media server roles when installing Oracle Secure Backup on a host, then that host is automatically part of the administrative domain. But it is not recognized as a media server until that role is explicitly granted to it using the chhost command in obtool or the Oracle Secure Backup Web tool.
See Also:
Oracle Secure Backup Reference for complete syntax and semantics for the chhost command
To add the media server role to an administrative server using the Oracle Secure Backup Web tool:
Configuring Preferred Network Interfaces (PNI)
This section contains the following topics:
Note:
PNI configuration settings for a host are applicable only to Oracle Secure Backup services. These settings have no impact on the network selection or usage of other applications running on the same host.
About PNI
PNI (Preferred Network Interface) enables you to configure the network or interface that must be used for communication between two hosts in the administrative domain.
Multiple physical data paths can exist between a client, which contains primary storage to be backed up or restored, a media server, which controls at least one secondary storage device that writes and reads the backup media, and the administrative server. For example, a host might have multiple network interfaces connected to the network containing the hosts in the administrative domain. Typically, clients transfer huge amounts of backup data over the network. Therefore, specifying the network/interface over which data must be sent prevents performance issues that may be caused when production networks are used for backup data.
For each host, you can configure PNI to instruct Oracle Secure Backup services to use a specific network or interface for sending backup data or for requesting a remote Oracle Secure Backup service to send inbound data. PNI applies to both control connections and data connections. Data connections are used to transfer backup data. Backup data is large in size and consumes considerable network bandwidth. Control connections are used to manage the administrative domain. The messages sent over control connections are small and consume minimal bandwidth.
See Also:
Network Load Balancing in Oracle Secure Backup for information about network load balancing and PNI
About PNI for Inbound Connections
Configuring a PNI for inbound connections specifies the interface that will be used when a remote host (media server or client) establishes a connection with the host.
About PNI for Outbound Connections
Configuring a PNI for outbound connections from a host specifies the network and interface that must be used when this host connects to a remote host (media server or client). The configured PNI is used for both data and control connections.
-
Single interface only
Limits the outgoing backup and control data transfer to the interface specified in the configured PNI. The interface must exist in the remote host to which a connection is being established. You can configure one network/interface for each address family (one for IPv4 and another for IPv6). You must not use the single interface for RDS connections. When you chose this type of connection, you cannot configure other networks as PNI for outbound connections for this host.
-
One or more specified networks
Uses the specified network when connecting to a remote host. You can specify one or more networks. Optionally, a bind address for each outgoing network can be specified. If no bind address is specified, then the operating system decides which address to bind to. When multiple networks are specified, a connection is attempted based on the order of remote host IP names specified.
If the specified networks are not available, then you can configure Oracle Secure Backup to use any available network and interface to connect to a remote host. The following IP values are used to configure any network as PNI:
0.0.0.0/0: any IPv4 network
0::0/0: any IPv6 network
0/0: any of IPv4 or IPv6 network
PNI and Network Connection Types
A host can have different types of networks. Oracle Secure Backup supports IPv4 and IPv6 for control connections and IPv4, IPv6, RDS/RDMA over Infiniband for data connections. When multiple network connections exist between a client and the media server, Oracle Secure Backup uses the following criteria to determine which connection type is used:
-
If a PNI is configured, the network interface specified in the PNI is used to transfer backup and restore data between the client and media server. The connection type chosen is the same as the connection type of the network interface specified in PNI.
-
If a PNI is not configured, Oracle Secure Backup selects the connection type as follows:
-
For control connections, the order of precedence is based on the ordering of IP addresses in the host object. Each client has a host object. The host object contains the list of IP addresses that can be used to access that host.
-
For data connections, the default connection used depends on the type of connection. The order of precedence is described in "Order of Precedence for Network Connection Types".
For a particular connection type to be used, both the client and media server must support that connection type.
-
Configuring PNI for Inbound Connections
When you configure a PNI for inbound connections for a host, remote hosts specified in inbound PNI use the interface specified in PNI to send data to the host.
To configure a PNI for inbound connections:
Configuring PNI for Outbound Connections
When multiple network paths exist between hosts in the administrative domain, you can configure a PNI to define the network/interface that must be used when creating connections from this host to another remote host.
To configure a PNI for outbound connections from a host:
Pinging Hosts in the Administrative Domain
You can use the Oracle Secure Backup ping operation to determine whether a host responds to requests from Oracle Secure Backup on each of its configured IP addresses.
Pinging a host attempts to establish a TCP connection to the host on each of the IP addresses you have configured for it. For hosts running Oracle Secure Backup, the connection occurs on TCP port 400. For hosts that use the NDMP access mode, connections occur through the configured NDMP TCP port, usually 10000.
Oracle Secure Backup reports the status of each connection attempt and immediately closes each connection that has been established successfully.
To ping a host in the administrative domain:
Enable tcpkeepalive on local host
Enable tcpkeepalive in the local policy to prevent idle
Oracle Secure Backup network connections from being terminated by a proxy or firewall due to
inactivity.
You can set the
local policy for tcpkeepalive and configure the control connections
to remain open so that the backup operations, for both file system and Recovery Manager (RMAN), complete successfully.
About tcpkeeplive
Oracle Secure Backup provides a local policy for
tcpkeepalive.
The
tcpkeepalive policy helps maintain idle TCP connections by
periodically exchanging packets between hosts in the Oracle Secure Backup domain that
have the local policy enabled. By default, Oracle Secure Backup has the
tcpkeepalive policy disabled.
However, you can change the local policy and enable tcpkeepalive
from the obtool interface. Since tcpkeepalive is set on the local
host, you must enable it individually on all media servers and administrative servers in
the administrative domain.
To enable the tcpkeepalive policy:
-
Run the
obtoolcommands fortcpkeepaliveon the local host. -
Configure the system parameters depending on your operating system.
The Web tool does not support changing or viewing the local policies.
See Also:
Configuring Firewalls for Oracle Secure Backup on Windows for information about the role of Windows firewall on network connections.
Steps to enable tcpkeepalive
Log in to the obtool command-line interface and enable
tcpkeepalive in the local policy.
To enable tcpkeepalive:
The system parameters to set the timers associated with tcpkeepalive
vary for each operating system. After a restart, the system parameters may reset to
their default values.
Tip:
Consult with your system administrators or network administrators to define the system parameters and control the behavior of the connection timeouts.
Overview of Automatic Device Discovery
Oracle Secure Backup allows you to discover and configure libraries and tape drives that are attached to media servers in the administrative domain.
If you choose not to discover devices automatically, then you can manually configure attached tape devices as described in "Adding Tape Devices to an Administrative Domain".
About Automatic Device Discovery
You can automatically discover and then configure libraries and tape drives that are attached to media servers in the administrative domain. This includes NDMP servers and media servers that have Oracle Secure Backup software installed. Automated device discovery makes the process of configuring attached libraries and drives automatic so that you can quickly add attached tape drives to the administrative domain. Its options allow you to configure all attached libraries and drives, or devices attached to specific hosts.
In addition to the initial configuration, automatic device discovery can also detect changes in the configuration of libraries and tape drives. When automatic device discovery is performed for a media server that has existing tape devices configured, devices that have already been configured in Oracle Secure Backup will not be reconfigured. This information can be used to update the configuration information of existing tape devices. By default, Oracle Secure Backup discovers Solaris, Linux, and AIX attached libraries and tape devices that have their attachments located in the /dev directory.
Note:
It is recommended that you use the automatic device discovery feature to rediscover devices only when the existing devices in the current domain are not in use.
Tape Device Configuration Changes Oracle Secure Backup Detects
During automatic device discovery, the following media changers and tape drives can be detected:
-
Media changers and tape drives that were not previously part of the current administrative domain.
For each such device discovered, Oracle Secure Backup can create a device with an internally-assigned name and then configure its device attachment.
-
Previously configured libraries and/or tape devices that have new attachments.
In this case, Oracle Secure Backup can add new attachments to an existing device configuration.
Libraries and tape devices are detected by Oracle Secure Backup by reading the serial number reported for the device by the media server's operating system. Devices having multiple attachments are detected based on their having the same serial number reported by multiple media servers. Oracle Secure Backup will configure devices based on the serial number associated with its attachments rather than any logical name assigned by the operating system.
-
Previously configured devices which have lost an attachment
Oracle Secure Backup displays information about the lost device attachment.
About Persistent Binding for SCSI Tape Devices
Oracle Secure Backup uses device file names, such as /dev/sg3, to refer to the actual physical tape devices. These device file names are specified during device configuration as part of the attach point specification. Hardware configuration changes or a system reboot may sometimes cause an existing device file name to point to a different tape device instead of the originally-configured tape device. To ensure that SCSI tape device configuration remains constant across hardware configuration changes and system reboots, the system administrator can use persistent binding to set up the tape devices. When persistent binding is used, the operating system uses symbolic links to manage the mapping of device files to the configured SCSI tape devices. Therefore, Oracle Secure Backup device files will always map to the correct tape devices. Tape devices that use persistent binding can also be automatically discovered and configured as described in "Overview of Automatic Device Discovery".
Note:
Persistent binding is supported only for the Linux 64-bit platform.
By default, Oracle Secure Backup discovers Solaris, Linux, and AIX attached libraries and tape drives that have their attachments located in the /dev directory. However, when persistent binding is used, the tape device files may be located in a different directory. You can specify the directory from which SCSI persistent devices must be discovered by using the OB_DEVICE_SEARCH_PATH environment variable.
See Also:
discoverdev in the Oracle Secure Backup Reference for information about the OB_DEVICE_SEARCH_PATH environment variable
Steps to Discover and Configure Tape Devices in the Administrative Domain
Depending on the requirement, you can either discover tape devices attached to media servers in the administrative domain or you can also configure the discovered devices.
See Also:
discovereddevicestate policy in the Oracle Secure Backup Reference for more information on the policy setting for managing the availability of discovered tape devices
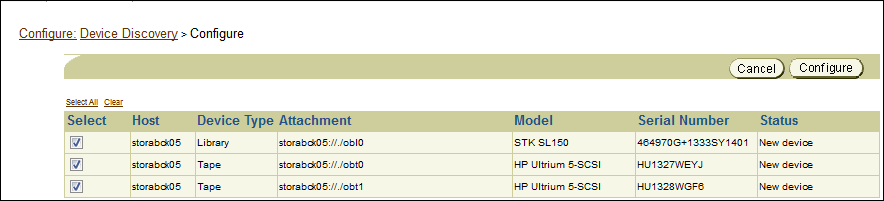
To automatically discover and configure tape devices:
Adding Tape Devices to an Administrative Domain
This section explains how to configure tape drives and tape libraries for use with Oracle Secure Backup. During initial configuration of the administration domain, you must add all tape devices in your environment to the domain. Subsequently, when you add new devices to your domain, you must configure the new tape devices using the steps described in this section.
This section contains the following topics:
About Tape Device Names
A tape device can be assigned a logical name by the host operating system (such as nrst0a), but it also can have a worldwide name, such as nr.WWN[2:000:0090a5:0003f7]L1.a. On some platforms, such as a Fibre Channel tape drive or tape library connected to a Network Appliance filer, the logical name might vary at each operating system restart. Oracle Secure Backup supports such tape devices, but they must be referred to by their worldwide name, which does not change across operating system restarts.
Any substring of the raw device name for the attachment that is the string $WWN is replaced with the value of the WWN each time the tape device is opened. For example a usable raw device name for a Storage Area Network (SAN) Network Appliance filer is nr.$WWN.a, specifying a no-rewind, best-compression tape device having the World Wide Name found in the device object.
The WWN is usually automatically discovered by the device discovery function in Oracle Secure Backup. However, you can enter it manually if necessary.
About Manually Configuring Tape Drives and Libraries
For both tape drives and tape libraries, you can configure the following attributes:
-
The name of the tape device
-
The attachment, which is the description of a physical or logical connection of a tape device to a host
-
Whether the tape device is in service
For tape drives, you can configure the following additional attributes:
-
The tape library in which the tape drive is housed, if the tape drive is not standalone
-
A storage element range that the tape device can use, if the tape drive is in a tape library
Note:
Oracle Secure Backup identifies each tape drive within a tape library by its data transfer element (DTE) number. You must assign each tape device a DTE number if it is installed within a tape library. DTEs are numbered 1 through n. See the description of the --dte option to the mkdev command in Oracle Secure Backup Reference for more details on data transfer element numbers.
For tape libraries, you can configure the following additional attributes:
-
Whether automatic cleaning is enabled
-
The duration of a cleaning interval
-
Whether a barcode reader is present
See Also:
Oracle Secure Backup Reference for a complete account of tape device attributes.
Methods of Configuring Tape Devices
You can configure a tape drive or tape library for use with Oracle Secure Backup using one of the following methods:
-
Automatic discovery
Oracle Secure Backup can automatically discover and configure each secondary storage device connected to media servers.
See Also:
-
Manually
A tape device connected to a media server on which Oracle Secure Backup is installed must be added to the administrative domain manually.
See Also:
Note:
You must add the media server role to a host before adding any tape devices whose attachment point references that host. Oracle Secure Backup does not do this automatically.
Steps to Configure Tape Devices in the Administrative Domain
This section provides an overview of the steps used to configure tape devices, with each step containing links to the sections that describe how to perform each device configuration task.
To configure your administrative domain to include tape devices:
-
Perform one of the following steps to add tape devices to the administrative domain:
-
Manually configure tape libraries and tape devices.
-
Configure tape libraries locally attached to your media servers as described in "Manually Configuring Tape Libraries".
-
Configure tape drives locally attached to your media servers as described in "Configuring Tape Drives"
-
Create an attachment between the tape device to the host to which the tape device is connected as described in "Adding Tape Device Attachments".
A tape device can have more than one attachment.
If your tape library is shared by multiple hosts in the administrative domain, see "Configuring Multihosted Device Objects" for details about handling shared devices.
-
-
Use automatic device discovery to add every tape device attached to hosts as described in "Overview of Automatic Device Discovery" describes this task.
-
-
Configure tape devices that are network-accessible but are not locally attached.
You must decide which media servers should control the tape devices and, for each media server, specify an attachment between the media server and the tape device. The procedure is identical to configuring a tape device attached locally to a media server.
-
Verify each device attachment as described in "Verifying Tape Device Configuration".
-
Inventory each tape library, and then list its volumes as described in "Updating Tape Library Inventory".
Each volume in a tape library should show either a barcode or the status unlabeled. If a library shows a slot as occupied, then this slot is in an invalid state.
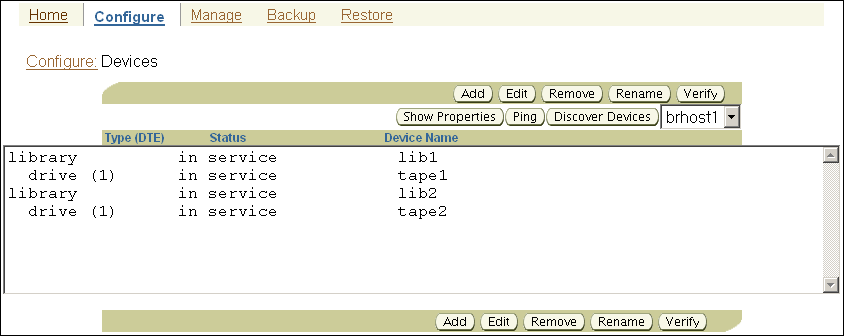
Displaying the Devices Page
The Devices page, illustrated in Figure 7-2, lists each tape library and tape drive that is currently in the administrative domain. The page lists the type, status, and name of every tape device.
To display the Devices page:
Manually Configuring Tape Libraries
Automatic Device Discovery is the recommended method for configuring a tape library for use with Oracle Secure Backup. This section explains how to manually configure a tape library.
See Also:
To configure a tape library:
See Also:
Configuring Automatic Tape Drive Cleaning for a Library
Oracle Secure Backup can automatically clean each tape drive in a tape library. A cleaning cycle is initiated either when a tape drive reports that it needs cleaning or when a specified usage time has elapsed.
Oracle Secure Backup checks for cleaning requirements when a cartridge is either loaded into or unloaded from a tape drive. If at that time a cleaning is required, then Oracle Secure Backup loads a cleaning cartridge, waits for the cleaning cycle to complete, replaces the cleaning cartridge in its original storage element, and continues with the requested load or unload.
To configure automatic cleaning for a tape library:
Configuring Tape Drives
The preferred method of configuring devices is by using automated device discovery. The following procedure describes the steps to configure tape drives manually.
This section explains how to configure a tape drive for use with Oracle Secure Backup. If the tape drive you want to configure is attached to a tape library, then you must configure the tape library first, as described in "Manually Configuring Tape Libraries".
To configure tape drives for use with Oracle Secure Backup:
Configuring an NDMP Copy-Enabled Virtual Tape Library
An NDMP copy-enabled virtual tape library (VTL) is a virtual tape library with an embedded NDMP server and multiple access paths. The embedded NDMP server allows offloading the I/O associated with volume duplication from the application running on the media server to the VTL.
An NDMP copy-enabled virtual tape library (VTL) must be represented in Oracle Secure Backup as a group of tape devices with multiple attach specifications. This ensures that the inventory data coming through the multiple access paths is identical.
Two Oracle Secure Backup host objects must be created to represent the VTL. One object must be associated with the media server to which the VTL is attached. The other host object must be associated with the VTL's embedded NDMP server. Both host objects must be assigned the media server role in Oracle Secure Backup.
One Oracle Secure Backup library device object with two attach specifications must be created for the virtual library. One access path is through the media server to which the VTL is attached. The other access path is through the embedded NDMP server.
An Oracle Secure Backup tape device object with two access paths must also be created for each virtual drive contained within the virtual library. As in the virtual library case, one access path is through the media server, and the other is through the embedded NDMP server.
One Oracle Secure Backup library device object with a single attach specification must be created for the physical library. The access path is through the VTL's embedded NDMP server. An Oracle Secure Backup tape device object with a single attach specification must also be created for each physical drive contained within the physical library. As in the physical library case, the access path is through the VTL's embedded NDMP server.
Note:
Multiple media servers may be able to access the physical library and its drives if they are all connected to a shared SAN. In this case, the Oracle Secure Backup device objects for the physical library and its drives must be created with multiple attach points.
Here is an example of the obtool commands that would be used to configure an NDMP copy-enabled VTL. Many of the options that would be specified in a real environment have been omitted for clarity. Also, the device names shown are simply placeholders that may differ from the actual names in a real environment.
See Also:
Oracle Secure Backup Administrator's Guide for more information on NDMP copy-enabled virtual tape libraries
Adding Tape Device Attachments
Oracle Secure Backup distinguishes between a tape device and a device attachment. Automated Device Discovery makes it so that it is no longer necessary to manually configure device attachments in Oracle Secure Backup. This section is added as a reference for situations where detailed understanding of the process of manually configuring device attachments in Oracle Secure Backup is needed. A device attachment is the means by which that tape device is connected to a host and Oracle Secure Backup uses this attachment as a data path to communicate with the device. Each drive or library accessed by Oracle Secure Backup has one or more attachments.
Before configuring a device attachment, refer to the description of the mkdev command in Oracle Secure Backup Reference. The description of the aspec placeholder describes the syntax and naming conventions for device attachments.
To configure device attachments:
- After adding or editing a device, click Attachments.
- Select a host in the Host list.
- In the Raw device field, enter the raw device name. This is the operating system's name for the device, such as a Linux or UNIX attach point or a Windows device file. For example, a tape library name might be
/dev/obl0on Linux and//./obl0on Windows. - Click Add to add the attachment.
Pinging Device Attachments
You can ping a device attachment to determine whether the tape device is accessible to Oracle Secure Backup using that attachment. Pinging device attachments is a good way to test whether you set up the attachment properly.
When you ping a device, Oracle Secure Backup performs the following steps:
-
Establishes a logical connection to the device
-
Inquires about the device's identity data with the
SCSIINQUIRYcommand -
Closes the connection
If the attachment is remote from the host running the Oracle Secure Backup Web tool (or obtool), then Oracle Secure Backup establishes an NDMP session with the remote media server to effect this function.
To ping an attachment from the Attachments page:
Multiple Attachments for SAN-Attached Tape Devices
A tape device attached to a SAN often has multiple attachments, one for each host with local access to the tape device through its Fibre Channel interface. A tape device attached to a SAN is also distinguished by a World Wide Name (WWN), an internal identifier that uniquely names the tape device on the SAN. Systems such as a Network Appliance filer permit access to tape devices attached to a SAN through their WWN. Oracle Secure Backup includes a reference to the WWN in the device attachment's raw device name.
Tape devices such as certain Quantum and SpectraLogic tape libraries appear to be connected directly to an Ethernet LAN segment and accessed through NDMP. In fact, Oracle Secure Backup views these devices as having two discrete components:
-
A host, which defines the IP address and which you configure through the Oracle Secure Backup Web tool Hosts page or the
mkhostcommand -
A tape device, which has one attachment to the single-purpose host that serves as the front end for the tape device
Devices such as DinoStor TapeServer use a single host to service multiple tape devices.
For NDMP servers that run version 2, other data might be required to define SCSI parameters needed to access the tape device. These parameters are sent in an NDMP message called NDMP_SCSI_SET_TARGET. Oracle Secure Backup NDMP servers do not use this data or this message.
See Also:
The description of the mkdev command aspec placeholder in Oracle Secure Backup Reference, which describes the syntax and naming conventions for device attachments
Configuring Multihosted Device Objects
A multihosted device, also known as a shared device, is a tape library shared by multiple hosts within a single administrative domain. Shared devices are common in environments that deploy SAN or iSCSI-based tape equipment. These technologies give the user the flexibility to have multiple direct connections from hosts to tape devices, which enables all hosts to act as media servers.
When a device is shared by multiple hosts, a single device object is used to ensure that it is known by its serial number across all members of the Oracle Secure Backup administrative domain. The configuration is done behind the scenes using automated device discovery and multiple attachments will be created, one for each device on each media server by which the device will be accessed.
Table 7-1 shows the correct configuration of a single tape library and tape drive shared by two hosts: host_a and host_b. After the devices are configured, Oracle Secure Backup is aware of the devices and handles device reservation properly.
Table 7-1 Correct Configuration for Tape Library and Tape Drive
| Tape Device Object | Attach Point 1 | Attach Point 2 |
|---|---|---|
|
|
|
|
|
|
|
|
If the device is configured as two separate device objects that point to the same physical device, then there is potential for contention. In this case, simultaneous backups to the these devices fail. Table 7-2 shows the incorrect configuration of a single tape library and tape drive shared by two hosts: host_a and host_b.
Table 7-2 Incorrect Configuration for Tape Library and Tape Drive
| Tape Device Object | Attach Point |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
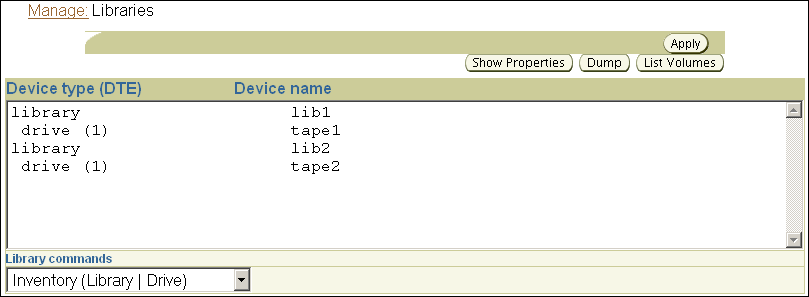
Updating Tape Library Inventory
An initial inventory of the storage element contents should be taken immediately after adding a new tape library to your Oracle Secure Backup administrative domain. This is necessary before Oracle Secure Backup will be able to use the library.
To update a tape library or tape drive inventory using the Oracle Secure Backup Web tool:
Verifying and Configuring Added Tape Devices
This section explains how to verify that tape devices are reachable, display information about these devices, and configure serial number checking.
This section contains the following topics:
Displaying Device Properties
The Oracle Secure Backup Web tool can display tape device properties including:
-
Whether a tape device is in service
-
Which host or hosts the tape device is connected to
-
The tape device type
When a tape device is in service, then Oracle Secure Backup can use it; when it is not in service, then Oracle Secure Backup cannot use it. When a tape device is taken out of service, no more backups are dispatched to it.
To display tape device properties:
Pinging Tape Devices
To determine whether a tape device is reachable by Oracle Secure Backup through any available attachment, ping the tape device. You should ping each tape device after it is configured or discovered, to check it's accessibility status.
To ping a tape device:
Note:
Pinging a tape library causes each service member tape drive in the tape library to be pinged as well.
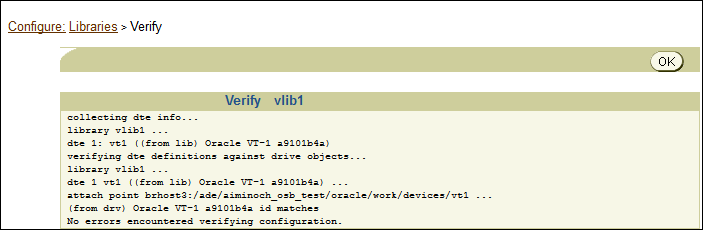
Verifying Tape Device Configuration
Oracle Secure Backup provides the following method for confirming that libraries and tape devices are configured correctly.
To verify tape device configuration:
Setting Serial Number Checking
You can use the Oracle Secure Backup Web tool to enable or disable tape device serial number checking. If serial number checking is enabled, then whenever Oracle Secure Backup opens a tape device, it checks the serial number of that device. If the tape device does not support serial number reporting, then Oracle Secure Backup simply opens the tape device. If the tape device does support serial number checking, then Oracle Secure Backup compares the reported serial number to the serial number stored in the device object. Three results are possible:
-
There is no serial number in the device object.
If Oracle Secure Backup has never opened this tape drive since the device was created or the serial number policy was enabled, then it cannot have stored a serial number in the device object. In this case, the serial number is stored in the device object, and the open succeeds.
-
There is a serial number in the device object, and it matches the serial number just read from the device.
In this case, Oracle Secure Backup opens the tape device.
-
There is a serial number in the device object, and it does not match the serial number just read from the device.
In this case, Oracle Secure Backup returns an error message and does not open the tape device.
Note:
Oracle Secure Backup also performs serial number checking as part of the --geometry/-g option to the lsdev command in obtool. This option causes an Inquiry command to be sent to the specified device, and lsdev displays its vendor, product ID, firmware version, and serial number.
To enable or disable tape device serial number checking:
-
From the Oracle Secure Backup Web tool Home page, click Configure.
The Configure page appears.
-
In the Advanced section, click Defaults and Policies.
The Configure: Defaults and Policies page appears as shown in Figure 7-5.
Figure 7-5 Configure Details and Policies Page
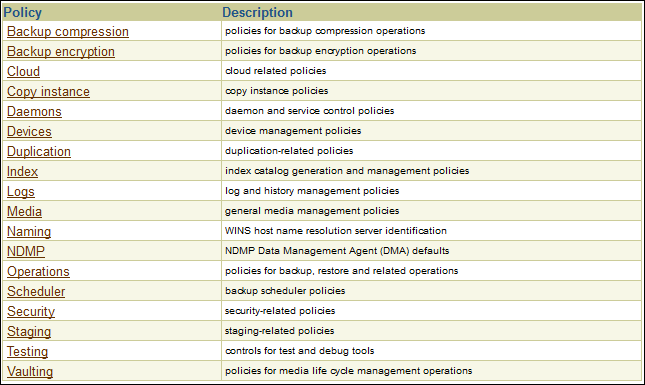
Description of "Figure 7-5 Configure Details and Policies Page" -
In the Policy column, click devices.
The Configure: Defaults and Policies > Devices page appears as shown in Figure 7-6.
Figure 7-6 Defaults and Policies for Devices
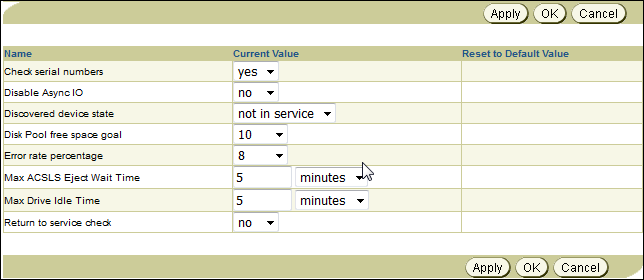
Description of "Figure 7-6 Defaults and Policies for Devices" -
Do one of the following:
-
Select Yes from the Check serial numbers list to enable tape device serial number checking. This is the default setting.
-
Select No from the Check serial numbers list to disable tape device serial number checking.
-
-
Click OK.
The Configure: Defaults and Policies page appears with a success message.
Configuring Disk Pools
Before you can store backups on a disk pool, you must configure the disk pool as a device in your administrative domain. Unlike tape devices, disk pools can be accessed concurrently by independent backup and restore jobs.
This section contains the following topics:
Displaying the Defined Disk Pools
You must have the query and display information about devices right to display disk pools.
To display the list of currently defined disk pools using the Web tool:
- On the Oracle Secure Backup Web tool Home page, click Configure.
- In the Basic section, click Devices.
- The Configure: Devices page is displayed. It lists all the currently-defined backup containers (disk pools, tape libraries, and tape drives). The details displayed for each backup container are the device name, status, and type of device.
Creating Disk Pools
To store your backups to a file-system on disk, you must first configure a device that corresponds to this file-system directory. You must have the manage devices and change device state right to create disk pools.
See Also:
Oracle Secure Backup Administrator's Guide for an overview of disk pools
To create a disk pool using the Web tool:
Caution:
In a dedup filesystem, the amount of disk space occupied by a diskpool (as reported by OS commands, such as "df -h") is lower than the standard storage. If you create a diskpool on a dedup filesystem and overfill the filesystem, Oracle Secure Backup utilities for managing disk space will not report accurate sizes for diskpools on dedup filesystems.
Editing Disk Pool Properties
You can use the Web tool to edit disk pool properties. You must have the manage devices and change device state right to edit disk pool properties.
To edit the properties of a disk pool:
Renaming Disk Pools
You must have the manage devices and change device state right to edit disk pool properties.
To rename a disk pool:
Removing Disk Pools
You need the manage devices and change device state right to remove a disk pool.
To remove a disk pool:
Managing Hosts in the Administrative Domain
After you configure hosts in the administrative domain, you can manage the hosts by performing any of the following tasks:
Viewing the Hosts in the Administrative Domain
To view hosts in the administrative domain:
Figure 7-7 Oracle Secure Backup Web Tool: Hosts Page
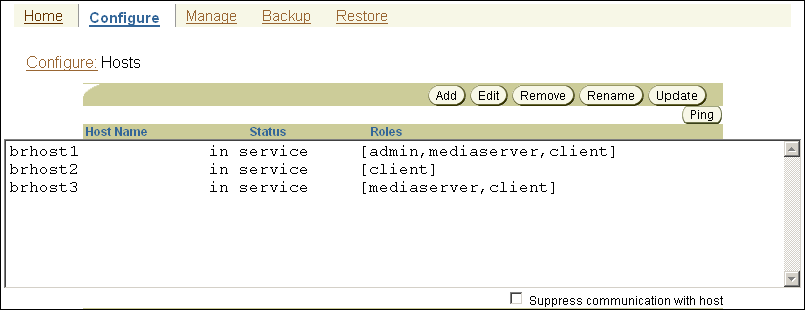
Description of "Figure 7-7 Oracle Secure Backup Web Tool: Hosts Page"
Note:
You can also view the current list of hosts with the obtool lshost command.
Updating Hosts in the Administrative Domain
When you add or modify a host in an Oracle Secure Backup administrative domain, Oracle Secure Backup exchanges messages with that host to inform it of its changed state. If you make changes to your administrative host, your client will likely contain outdated configuration information. Update Host can be used to send fresh state information to the client.
Updating is useful only for hosts running Oracle Secure Backup natively. Hosts accessed in NDMP mode, such as NAS devices, do not maintain any Oracle Secure Backup state data and therefore it is not necessary to update their state information.
To update a host:
- Display the Hosts page as described in "Viewing the Hosts in the Administrative Domain".
- Select the name of the host to be updated.
- Click Update.
Removing Hosts from an Administrative Domain
This section explains how to remove a host from an Oracle Secure Backup administrative domain. When you remove a host, Oracle Secure Backup destroys all information pertinent to that host, including:
-
Configuration data
-
Incremental backup state information
-
Metadata in the backup catalog for this host
-
Each device attachment
-
PNI references
When you remove a host, Oracle Secure Backup contacts that host and directs it to delete the administrative domain membership information it maintains locally. You can suppress this communication if the host is no longer accessible.
To remove a host:
Configuring Cloud Storage Devices
Before you can store backups on a cloud storage device, you must configure it as a device in your administrative domain.
This section contains the following topics:
Prerequisites for Configuring Storage Devices for OCI Classic
You must complete the following tasks before you can configure an Oracle Secure Backup cloud storage device for Oracle Cloud Infrastructure Classic:
-
Subscribe to Oracle Cloud Infrastructure Object Storage Classic.
-
Acquire your login credentials and identity domain.
The information provided in this topic explains how to perform each of these tasks.
Subscribing to Oracle Cloud
Oracle Cloud Infrastructure Object Storage Classic offers different storage options with and without replication. In addition to object storage, Oracle provides Oracle Cloud Infrastructure Archive Storage Classic which provides storage for long term retention. To access these services, you must first acquire a subscription.
See Also:
-
Storage Classic for further details about these services
-
Get Started with Oracle Cloud for information about free trials and subscriptions
Acquiring Login Credentials and an Identity Domain
When you subscribe to Oracle Cloud services, a unique identifier, called an identity domain, is created for all of your services. It is recommended that you create an identity domain administrator user to manage your cloud services. You must have the Storage_Administrator and Storage_ReadWriteGroup roles in order to do so.
After you receive your identity domain and user credentials, you can use them to create login accounts for other users who need to access the services. To access storage services from Oracle Secure Backup, it is recommended that you create another user that has the Storage_Administrator role.
See Also:
-
Adding Users and Assigning Roles for more information about Oracle Cloud Storage roles and users
Configuring an Authentication Object for Oracle Cloud Infrastructure
You must create an authentication object for Oracle Cloud Infrastructure before you can configure a cloud storage device that stores backups in Oracle Cloud Infrastructure Object Storage. The authentication object contains information such as the public key fingerprint, private key file, identity domain, and tenancy information that is required to authenticate Oracle Secure Backup with Oracle Cloud Infrastructure.
Before configuring an authentication object for Oracle Cloud Infrastructure:
-
You must have the
modify domain configurationright. -
You must have an Oracle Cloud account with access to Oracle Cloud Infrastructure Object Storage. See Object Storage.
-
You must generate a key pair file that contains a public key and a private key used to authenticate with Oracle Cloud Infrastructure, as described in How to Generate an API Signing Key. Both keys must be in
PEMformat. The private key is stored on the media server, not in Oracle Cloud. -
You must configure the key pair in the Oracle Cloud Infrastructure Console as described in How to Upload the Public Key. This generates a fingerprint for the key.
To create an authentication object for Oracle Cloud Infrastructure:
Creating Cloud Storage Devices for Oracle Cloud Infrastructure
Use the mkdev command or the Oracle Secure Backup Web tool to create a new cloud storage device for Oracle Cloud Infrastructure.
manage devices and change device state rights to create cloud storage devices for Oracle Cloud Infrastructure. An authentication object for Oracle Cloud Infrastructure must also be configured.
To create a cloud storage device for Oracle Cloud Infrastructure using the Web tool:
Creating Cloud Storage Devices for Oracle Cloud Infrastructure Classic
Use the mkdev command or the Oracle Secure Backup web tool to create a new cloud storage device for Oracle Cloud Infrastructure Classic. You must have the manage devices and change device state rights to create cloud storage devices.
To create a cloud storage device using the Web tool:
Displaying the Defined Cloud Storage Devices
You must have the query and display information about devices right to display cloud storage devices.
To display the list of currently defined cloud storage devices using the Web tool:
- On the Oracle Secure Backup Web tool Home page, click Configure.
- In the Basic section, click Devices.
- The Configure: Devices page is displayed. It lists all the currently-defined backup containers. The details displayed for each backup container are the type of device, status, and device name.
Editing Cloud Storage Device Properties
You can use the Web tool to edit properties of cloud storage devices. You must have the manage devices and change device state rights to edit properties.
Using the Web tool to edit cloud storage device properties
Renaming Cloud Storage Devices
You must have the manage devices and change device state right to rename cloud storage devices.
Using the Web tool to rename a cloud storage device
Removing Cloud Storage Devices
You need the manage devices and change device state rights to remove cloud storage device.
Using the Web tool to remove a cloud storage device
About Cloud Certificates
Oracle Secure Backup uses a Cloud server CA certificate to make an SSL connection to the Oracle Cloud server. Every region in the Cloud has specific certificates.
Oracle Secure Backup installation creates a Cloud wallet in Oracle Secure Backup Home and populates the wallet with default certificates. A Cloud wallet can contain multiple certificates.
In certain situations, it may be required to add a new Cloud certificate to the Oracle Secure Backup Cloud Wallet. For example, Oracle Cloud Infrastructure publishes a new certificate for connecting to the Cloud.
Oracle Secure Backup does not add new certificates automatically to the Cloud wallet.
This section contains the following topics:
Adding Certificates to the Cloud Wallet
Add new certificates to the existing Cloud wallet, keeping the old certificates in the wallet intact.
Adding a
new certificate to the wallet can resolve the ORA-29024: Certificate
validation failure error.
Note:
Add the new certificate to the Cloud wallet on the Oracle Secure Backup administrative server and on all media servers in the domain.
To add a new certificate to the Cloud wallet:
-
Download a Cloud server Certification Authority (CA) certificate.
-
Import the certificate into the Cloud wallet.
Manually Creating a Cloud Wallet
Oracle Secure Backup installation creates a Cloud Wallet automatically in the Oracle Secure Backup Home.
obcm utility. When you create a new Cloud Wallet manually, Oracle
Secure Backup creates an empty wallet without any certificates.
WARNING:
Manually creating a new Cloud wallet deletes the old wallet and removes all the existing certificates stored in it. It is not recommended to create a Cloud wallet manually.
To manually create a Cloud wallet:
Note:
Oracle Secure Backup requires a Cloud Wallet on the administrative server and on all media servers in the domain.