


|

|
|
|
|
Enabling Access Control Security
Default authorization consists of an access control checking feature that determines which users can execute a service, post an event, or enqueue (or dequeue) a message on an application queue. There are two levels of access control security: optional access control list (ACL) and mandatory access control list (MANDATORY_ACL). Only when users are authenticated to join an ATMI application does the access control list become active.
By using an access control list, an administrator can organize users into groups and associate the groups with objects that the member users have permission to access. Access control is done at the group level for the following reasons:
The access control checking feature is based on three files that are created and maintained by the application administrator:
By parsing the client's application key, which contains information identifying the client as a valid user and valid group member, an entity (such as a service, event, or application queue) can identify the group to which the user belongs; by checking the tpacl file, an entity can determine whether the client's group has access permission.
The application administrator, application operator, and processes or service requests running with the privileges of the application administrator/operator are not subject to ACL permission checking.
If user-level ACL entries are needed, they may be implemented by creating a group for each user, and then mapping the group to the appropriate application entities in the tpacl file.
How to Enable Optional ACL Security
Default authentication offers an optional ACL (ACL) security level that you invoke by specifying SECURITY ACL in your configuration file. This security level requires that each client provide an application password, a username, and user-specific data, such as a password, to join the ATMI application. If there is no entry in the tpacl file associated with the target application entity, the user is permitted to access the entity.
This security level enables an administrator to configure access for only those resources that need more security. That is, there is no need to add entries to the tpacl file for services, events, or application queues that are open to everyone. Of course, if there is an entry in the tpacl file associated with the target application entity and a user attempts to access that entity, the user must be a member of a group that is allowed to access that entity; otherwise, permission is denied.
To enable the ACL security level, follow these steps.
Instructions for these steps are provided in the following two topics.
Setting Up the UBBCONFIG File
*RESOURCES
SECURITY ACL
AUTHSVC ..AUTHSVC
.
.
.
*SERVERS
AUTHSVR SRVGRP="group_name" SRVID=1 RESTART=Y GRACE=600 MAXGEN=2 CLOPT="-A"
CLOPT="-A" causes tmboot(1) to pass only the default command-line options (invoked by "-A") to AUTHSVR when tmboot starts the ATMI application. By default, AUTHSVR uses the client user information in a file named tpusr to authenticate clients that want to join the ATMI application. tpusr resides in the directory referenced by the first pathname defined in the ATMI application's APPDIR variable.
Setting Up the ACL File
The access control checking feature requires a user file named tpusr, a group file named tpgrp, and an ACL file named tpacl. The ACL file contains mappings of groups to application entities. An entity may be a service, event, or application queue.
The following display is a sample entry in the tpacl file.
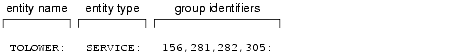
As the administrator, you must define the entries in the tpacl file, which is located in the directory referenced by the first pathname defined in the ATMI application's APPDIR variable. The file is a colon-delimited, flat text file, readable and writable only by the application's administrator.
There are two methods of modifying the ACL entries in the tpacl file: by issuing commands or by changing the values of the appropriate attributes in the ACL_MIB.
Changing ACL Entries Through Commands
You can add, modify, or delete ACL entries in the tpacl file at any time by running one of the following commands.
|
Run . . . |
To . . . |
|---|---|
|
Add an entry |
|
|
Modify an entry |
|
|
Delete an entry |
To run any of these commands, follow these steps.
Changing ACL Entries Through the ACL_MIB
If you prefer not to use the command-line interface, you can add, modify, or delete ACL entries in tpacl by changing the appropriate attribute values in the T_ACLPERM class in the ACL_MIB(5). This method is more efficient than the command-line interface if you want to add several ACL entries simultaneously, since tpacladd(1) allows you to add only one ACL entry at a time.
Of course, the easiest way to access the MIB is via the BEA Administration Console.
How to Enable Mandatory ACL Security
Default authentication offers a mandatory ACL security level that you invoke by specifying SECURITY MANDATORY_ACL in your configuration file. This security level requires that each client provide an application password, a username, and user-specific data, such as a password, to join the ATMI application. If there is no entry in the tpacl file associated with the target application entity, the client is not permitted to access the entity. In other words, an entry must exist in the tpacl file for every application entity that a client needs to access. For this reason, this level is called mandatory.
Of course, if there is an entry in the tpacl file associated with the target application entity and a user attempts to access that entity, the user must be a member of a group that is allowed to access that entity; otherwise, permission is denied.
To enable the MANDATORY_ACL security level, follow these steps.
Instructions for these steps are provided in the following two topics.
Setting Up the UBBCONFIG File
*RESOURCES
SECURITY MANDATORY_ACL
AUTHSVC ..AUTHSVC
.
.
.
*SERVERS
AUTHSVR SRVGRP="group_name" SRVID=1 RESTART=Y GRACE=600 MAXGEN=2 CLOPT="-A"
CLOPT="-A" causes tmboot(1) to pass only the default command-line options (invoked by "-A") to AUTHSVR when tmboot starts the ATMI application. By default, AUTHSVR uses the client user information in a file named tpusr to authenticate clients that want to join the ATMI application. tpusr resides in the directory referenced by the first pathname defined in the ATMI application's APPDIR variable.
Setting Up the ACL File
See Also

|
|

|
|
|
|
Copyright © 2001 BEA Systems, Inc. All rights reserved.
|