


|

|
|
|
|
Default Authentication and Authorization
The default authentication and authorization plug-ins provided by the ATMI environment of the BEA Tuxedo product work in the same manner that implementations of authentication and authorization have worked since they were first made available with the BEA Tuxedo system.
An application administrator can use the default authentication and authorization plug-ins to configure an ATMI application with one of five levels of security. The five levels are:
At the lowest level, no authentication is provided. At the highest level, an access control checking feature determines which users can execute a service, post an event, or enqueue (or dequeue) a message on an application queue. The security levels are briefly described in the following table.
Note: The term client is synonymous with client process, meaning a specific instance of a client program in execution. An ATMI client program can exist in active memory in any number of individual instances.
An application administrator can designate a security level by setting the SECURITY parameter in the UBBCONFIG configuration file to the appropriate value.
The default is NONE. If SECURITY is set to USER_AUTH, ACL, or MANDATORY_ACL, then the application administrator must configure a system-supplied authentication server named AUTHSVR. AUTHSVR performs per-user authentication.
An application developer can replace AUTHSVR with an authentication server that has logic specific to the ATMI application. For example, a company may want to develop a custom authentication server so that it can use the popular Kerberos mechanism for authentication.
Client Naming
Upon joining an ATMI application, a client process has two names: a combined user-client name and a unique client identifier known as an application key.
Two client names are reserved for special semantics: tpsysadm and tpsysop. tpsysadm is treated as the application administrator, and tpsysop is treated as the application operator.
User-Client Names
When an authenticated client joins an ATMI application, it passes a username and client name to tpinit(3c) in a TPINIT buffer if the application is written in C, or to TPINITIALIZE(3cbl) in a TPINFDEF-REC record if the application is written in COBOL. The username and client name, as well as other security-related fields in the TPINIT buffer/ TPINFDEF-REC record, are described in the following table.
For an authenticated security level (USER_AUTH, ACL, or MANDATORY_ACL), the username, client name, and user-specific data are transferred to AUTHSVR without interpretation by the BEA Tuxedo system. The only manipulation of this information is its encryption when transmitted over the network from a Workstation client.
Application Key
Every time a client joins an ATMI application, it is assigned a 32-bit application key by the BEA Tuxedo system. The client cannot reset the key other than by terminating its association and joining the ATMI application as a different user.
The assigned application key is the client's security credential. The client provides its application key with every service invocation as part of the TPSVCINFO structure in the appkey field. (See tpservice(3c) in the BEA Tuxedo ATMI C Function Reference for more information about TPSVCINFO.)
The following table shows how the application key is set for various security levels and clients. All application key assignments are hardcoded except the last item in the table.
In addition, any message that originates from tpsvrinit(3c) or tpsvrdone(3c) in a C program (TPSVRINIT(3cbl) or TPSVRDONE(3cbl) in COBOL) is assigned the application key of the administrator: 0x80000000. The application key of the client is assigned to messages that pass through a server but originate at a client; an exception to this rule is described in Replacing Client Tokens with Server Tokens.
A user identifier (UID) is an integer, between 0 and 128K, that is used by the application to refer to a particular user. A group identifier (GID) is an integer, between 0 and 16K, that is used by the application to refer to an application group.
User, Group, and ACL Files
To use access control, an application administrator must maintain lists of (1) users, (2) groups, and (3) and mappings of groups to application entities (such as services, events, and application queues). The third type of list, a mapping of groups to application entities, is known as the access control list (ACL).
When a client tries to access an application resource, such as a service, the system checks the client's application key and thus identifies the group to which the user belongs. Next, the system checks the ACL for the target resource and determines whether the client's group has access permission. The application administrator, application operator, and processes or service requests running with the privileges of the application administrator or operator are not subject to ACL permission checking.
The user, group, and ACL files are located in the application_root directory, where application _root is the first pathname defined for the APPDIR variable. The following figure identifies these files and specifies the administrative commands available for controlling each list.
Default User, Group, and ACL Files
Note: For an ATMI application running on the Compaq VMS operating system, the names of the user, group, and ACL files have .dat extensions: tpusr.dat, tpgrp.dat, and tpacl.dat. The files are colon-delimited, flat text files that can be read and written only by the application administrator—the owner of the TUXCONFIG file referenced by the TUXCONFIG variable. The format of the files is irrelevant, since the files are fully administered with a set of dedicated commands. Only the application administer is allowed to use these commands. An application administer can use the tpaclcvt(1) command to convert security data files to the format needed by the ACL checking feature. For example, on a UNIX host machine, an administrator can use tpaclcvt to convert the /etc/password file and store the converted version in the tpusr file. The same administrator can use tpaclcvt to convert the /etc/group file and store the converted version in the tpgrp file. The AUTHSVR server uses the user information stored in the tpusr file to authenticate users who want to join the ATMI application. Optional and Mandatory ACLs The ACL and MANDATORY_ACL security levels constitute the default authorization implementation for the ATMI environment in the BEA Tuxedo product. When the security level is ACL, if there is no entry in the tpacl file associated with the target application entity, the client is permitted to access the entity. This security level enables an administrator to configure access for only those resources that need more security. That is, there is no need to add entries to the tpacl file for services, events, or application queues that are open to everyone. When the security level is MANDATORY_ACL, if there is no entry in the tpacl file associated with the target application entity, the client is not permitted to access the entity. For this reason, this level is called mandatory. There must be an entry in the tpacl file for each and every application entity that the client needs to access. For both the ACL and MANDATORY_ACL security levels, if an entry for an application entity exists in the tpacl file and the client attempts to access that entity, the user associated with that client must be a member of a group that is allowed to access that entity; otherwise, permission is denied. For some ATMI applications, it may be necessary to use both system-level and application-level authorization. An entry in the tpacl file can be used to control which users can access a service, and application logic can control data-dependent access, for example, which users can handle transactions for more than a million dollars. Note that there is no ACL permission checking for administrative services, events, and application queues with names that begin with a dot (.). For example, any client can subscribe to administrative events such as .SysMachineBroadcast, .SysNetworkConfig, and .SysServerCleaning. In addition, there is no ACL permission checking for the application administrator, application operator, or processes or service requests running with the privileges of the application administrator or operator. See Also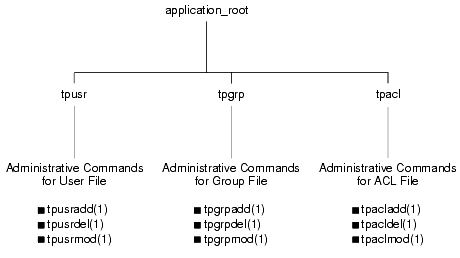

|

|
|
|
|
Copyright © 2001 BEA Systems, Inc. All rights reserved.
|