Recommended Deployment Configurations
This section describes recommended architectures for deploying Oracle products with secure Internet access.
Figure 2-1 shows a simple deployment architecture.
Figure 2-1 Simple Firewall Deployment Configuration
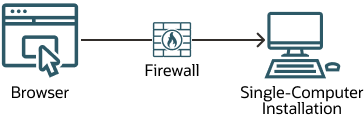
This single-computer deployment can be cost effective for small organizations. However, it can't provide high availability because all components are stored on the same computer.
Figure 2-2 shows a good practice configuration based on an Internet-Firewall-DMZ-Firewall-Intranet architecture.
Figure 2-2 DMZ Deployment Configuration
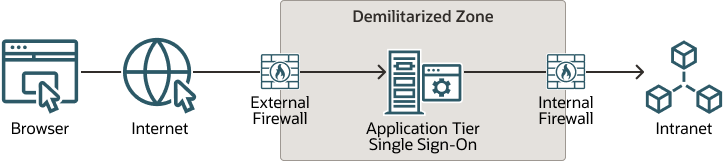
A "demilitarized zone" (DMZ) refers to a server that's isolated by firewalls from both the Internet and the intranet, and which acts a buffer between them. The firewalls that separate DMZ zones provide two essential functions:
-
Blocking any traffic types that aren't allowed.
-
Providing intrusion containment if any successful intrusions take over processes or processors.