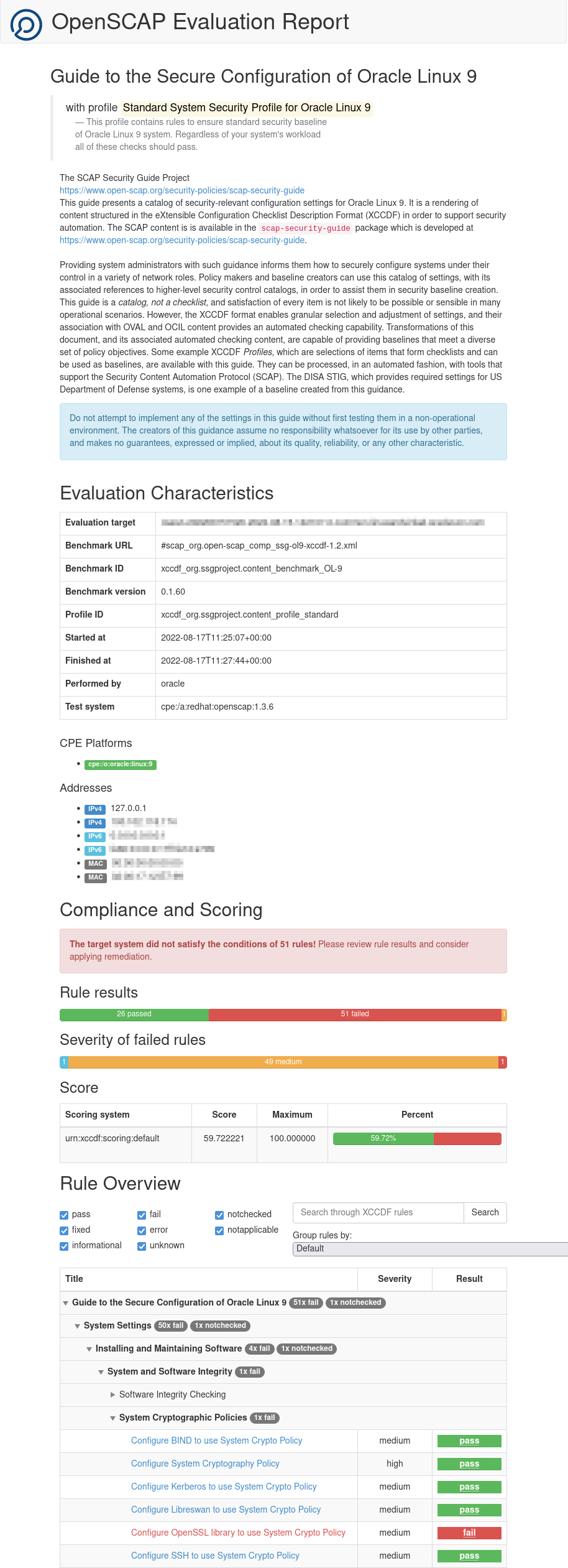
4 Checking Compliance With XCCDF Profiles
Use the the oscap command to check how the system complies with a security compliance checklist. OSCAP can generate reports and display information about the system by using XCCDF profiles. These can help you harden a system to meet particular security requirements, recommendations, or guidelines. XCCDF profiles can be contained either in an XCCDF file or within a SCAP data stream file.
Validating an XCCDF File or Data Stream File
oscap sub commands to check that XCCDF and data stream files are correctly formatted.
To check that an XCCDF file is valid, use oscap xccdf validate and examine the exit code. This validates the file against its schema.
To validate an XCCDF file, run the following command:
oscap xccdf validate /path/to/xccdf-file.xml \
&& echo "ok" || echo "exit code = $? not ok"If the XCCDF file is valid, the command example returns:
okNote:
Various XCCDF files and other SCAP security guide files are included in the scap-security-guide package.
To validate a source data stream file against its schema, use oscap ds sds-validate. XCCDF content can be bundled and included within a single source data stream file, often included as part of the scap-security-guide package and are preferred for shipping many SCAP related artifacts.
To validate a source data stream file, run the following command:
oscap ds sds-validate /path/to/ds-file.xml \
&& echo "ok" || echo "exit code = $? not ok"If the source data stream file is valid, the command example returns:
okDisplaying Available Profiles
A profile contains generic security recommendations that apply to all Oracle Linux installations and other security recommendations that are specific to the intended usage of a system. You can use these unmodified, or adapt them to create profiles that test the system's compliance with site security policies.
Use oscap info to display profiles that work with a checklist file such as the SCAP Security Guide XCCDF file or a SCAP data stream that contains XCCDF content. The syntax is as follows:
oscap info path/file.xmlFor example:
oscap info /usr/share/xml/scap/ssg/content/ssg-ol9-ds.xmlSample output:
Document type: Source Data Stream
Imported: date amd time
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-ol9-xccdf.xml
Generated: (null)
Version: 1.3
Checklists:
Ref-Id: scap_org.open-scap_cref_ssg-ol9-xccdf.xml
WARNING: Datastream component 'scap_org.open-scap_cref_security-oval-com.oracle.elsa-ol9.xml.bz2' points out to the
remote 'https://linux.oracle.com/security/oval/com.oracle.elsa-ol9.xml.bz2'. Use '--fetch-remote-resources'
option to download it.
WARNING: Skipping 'https://linux.oracle.com/security/oval/com.oracle.elsa-ol9.xml.bz2' file which is referenced
from datastream
Status: draft
Generated: date
Resolved: true
Profiles:
Title: ANSSI-BP-028 (enhanced)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced
Title: ANSSI-BP-028 (high)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high
Title: ANSSI-BP-028 (intermediary)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediary
Title: ANSSI-BP-028 (minimal)
Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal
Title: Centro Criptológico Nacional (CCN) - STIC for Oracle Linux 9 - Advanced
Id: xccdf_org.ssgproject.content_profile_ccn_advanced
Title: Centro Criptológico Nacional (CCN) - STIC for Oracle Linux 9 - Basic
Id: xccdf_org.ssgproject.content_profile_ccn_basic
Title: Centro Criptológico Nacional (CCN) - STIC for Oracle Linux 9 - Intermediate
Id: xccdf_org.ssgproject.content_profile_ccn_intermediate
Title: DRAFT - Unclassified Information in Non-federal Information Systems and Organizations
(NIST 800-171)
Id: xccdf_org.ssgproject.content_profile_cui
Title: Australian Cyber Security Centre (ACSC) Essential Eight
Id: xccdf_org.ssgproject.content_profile_e8
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Title: Australian Cyber Security Centre (ACSC) ISM Official
Id: xccdf_org.ssgproject.content_profile_ism_o
Title: DRAFT - Protection Profile for General Purpose Operating Systems
Id: xccdf_org.ssgproject.content_profile_ospp
Title: PCI-DSS v4.0 Control Baseline for Oracle Linux 9
Id: xccdf_org.ssgproject.content_profile_pci-dss
Title: Standard System Security Profile for Oracle Linux 9
Id: xccdf_org.ssgproject.content_profile_standard
Title: DISA STIG for Oracle Linux 9
Id: xccdf_org.ssgproject.content_profile_stig
Title: DISA STIG with GUI for Oracle Linux 9
Id: xccdf_org.ssgproject.content_profile_stig_gui
Referenced check files:
ssg-ol9-oval.xml
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
ssg-ol9-ocil.xml
system: http://scap.nist.gov/schema/ocil/2
security-oval-com.oracle.elsa-ol9.xml.bz2
system: http://oval.mitre.org/XMLSchema/oval-definitions-5
Note:
You can ignore warnings about remote data stream components when viewing information about XCCDF profiles, but when performing an evaluation you must either use the --fetch-remote-resources option for OSCAP to automatically download these resources, or manually download the resources beforehand and use the --local-files option to provide the path of these components.
The ssg-ol9-ds.xml data stream file contains information about where to download OVAL definitions so that evaluations can audit against the most recent version of these definitions.
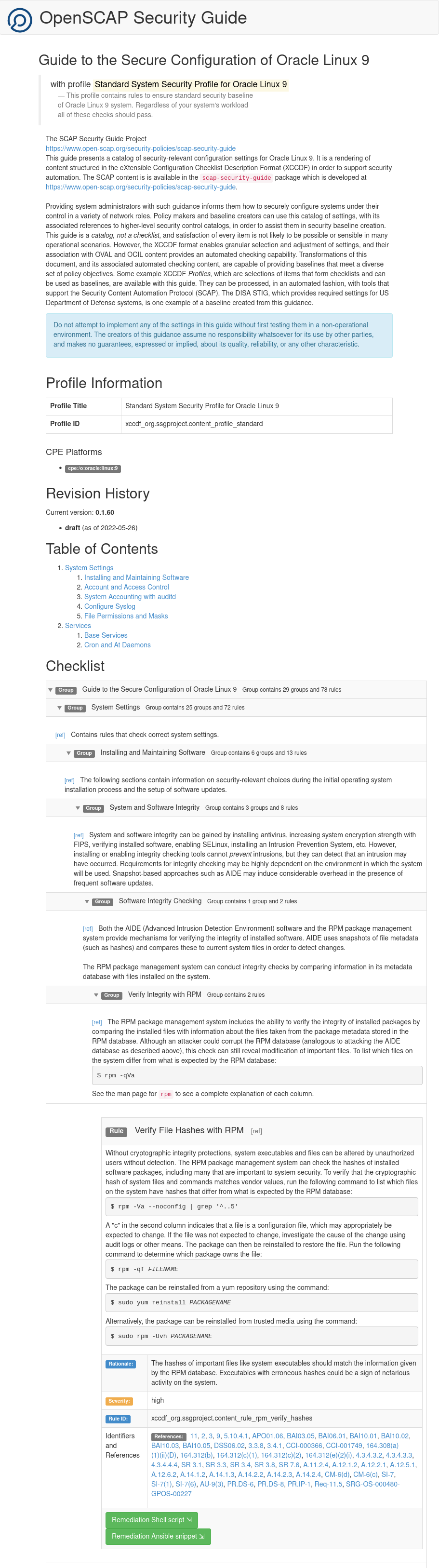
Displaying Profile Information
This task shows you how to find out more information about a specific profile.
To view information about a profile, use the oscap info command with the --profile option. The syntax is as follows:
oscap info --profile profile_id path/file.xmlFor example, to find out information about the Health Insurance Portability and Accountability Act (HIPAA) profile, xccdf_org.ssgproject.content_profile_hipaa:
oscap info --profile xccdf_org.ssgproject.content_profile_hipaa /usr/share/xml/scap/ssg/content/ssg-ol9-ds.xmlTip:
Most examples in this guide use the full profile ID, but you can specify a profile by using its short ID instead. The short ID is whatever appears after profile_ in the full profile ID. For example, instead of --profile xccdf_org.ssgproject.content_profile_hipaa, you can use --profile hipaa.
Sample output:
Document type: Source Data Stream
Imported: date and time
Stream: scap_org.open-scap_datastream_from_xccdf_ssg-ol9-xccdf.xml
Generated: (null)
Version: 1.3
WARNING: Datastream component 'scap_org.open-scap_cref_security-oval-com.oracle.elsa-ol9.xml.bz2' points out to the remote
'https://linux.oracle.com/security/oval/com.oracle.elsa-ol9.xml.bz2'. Use '--fetch-remote-resources' option to download it.
WARNING: Skipping 'https://linux.oracle.com/security/oval/com.oracle.elsa-ol9.xml.bz2' file which is referenced from datastream
Profile
Title: Health Insurance Portability and Accountability Act (HIPAA)
Id: xccdf_org.ssgproject.content_profile_hipaa
Description: The HIPAA Security Rule establishes U.S. national standards to protect individuals’ electronic personal health
information that is created, received, used, or maintained by a covered entity. The Security Rule requires appropriate
administrative, physical and technical safeguards to ensure the confidentiality, integrity, and security of electronic
protected health information. This profile configures Oracle Linux 9 to the HIPAA Security Rule identified for securing
of electronic protected health information. Use of this profile in no way guarantees or makes claims against legal
compliance against the HIPAA Security Rule(s).Running a Scan Against an XCCDF Profile
This task describes how to use the oscap xccdf eval command to scan a system against an XCCDF profile and generate a compliance evaluation report.
Generating a Full Security Guide
oscap xccdf generate guide command to create a full security guide. The security guide provides a catalog of security configuration settings for the system and often includes example bash remediation scripts and Ansible snippets that can be run to automatically resolve issues.
Caution:
Always test remediation scripts before applying them to production systems.
Customizing a Profile
You can customize an OpenSCAP security profile to tailor security rules and variable values for an organization's requirements. To customize an OpenSCAP security profile, you use the autotailor tool, which is provided by the scap-security-guide package.
The autotailor command syntax is as follows:
autotailor [options] -o tailoring_file -p profile_id datastream profile-
[options] -
Use
--var-value VARIABLE=VALUEto set variable values,--select RULE_IDor--unselect RULE_IDto select and clear rules, or other availableautotailoroptions. -
-o tailoring_file -
Output file to write the tailoring data.
-
-p profile_id -
Identifier for the custom profile.
-
datastream -
Path to the source datastream file.
autotailorrequires a SCAP datastream as input and doesn't work with individual XCCDF files. -
PROFILE -
The profile to base the customization on.
For more information on the autotailor tool, see the autotailor(8) manual page.