Setting Up Load Balancing in NAT Mode
The following procedure describes how to configure Keepalived in NAT mode to implement a basic failover and load balancing configuration on two servers. One server acts as the primary, the other acts as a backup, with the primary server having a higher priority than the backup server. Both servers use VRRP to monitor the current routing state. For more information about VRRP, see Using Keepalived With VRRP.
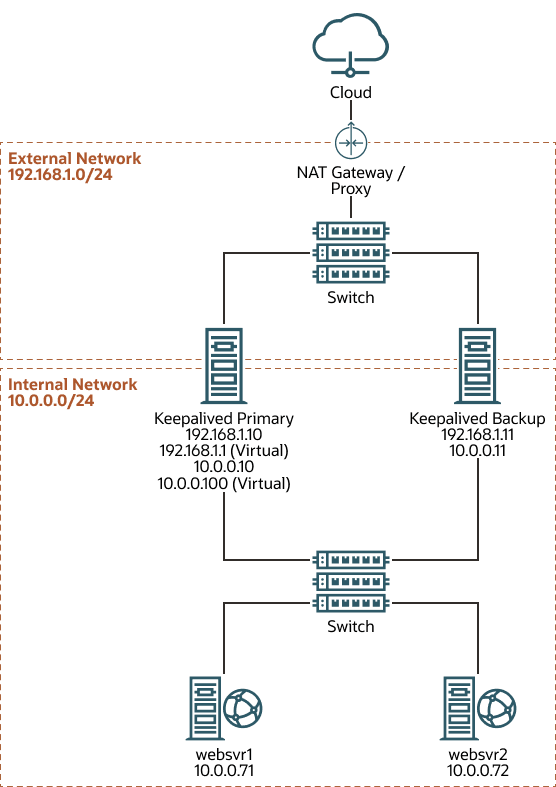
In this procedure, the example servers each have two network interfaces. The first interface is connected to an external network (192.168.1.0/24). The second interface is connected to an internal network (10.0.0.0/24), on which two web servers are accessible.
The following figure shows that the Keepalived primary server
has the following network addresses:
192.168.1.10, 192.168.1.1
(virtual), 10.0.0.10, and
10.0.0.100 (virtual).
The Keepalived backup server has the following network addresses:
192.168.1.11 and 10.0.0.11.
For IP addresses, websrv1 has 10.0.0.71 and
websrv2 has 10.0.0.72.
Figure 3-1 Keepalived Configuration for Load Balancing in NAT Mode
keepalived servers to verify the service is running correctly: sudo journalctl -u keepalivedConfiguring Firewall Rules for Keepalived NAT-Mode Load Balancing
If you configure Keepalived to use NAT mode for load balancing with the servers on the internal network, the Keepalived server handles all inbound and outbound network traffic and hides the existing backend servers by rewriting the source IP address of the real backend server in outgoing packets with the virtual IP address of the external network interface.
The following example shows how to move interface enp0s9 to the
internal zone, while interface enp0s8 remains in the
public zone.
To configure a Keepalived server to use NAT mode for load balancing: