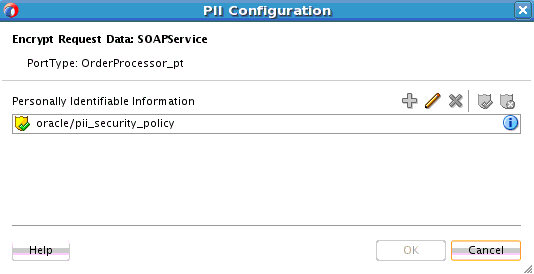
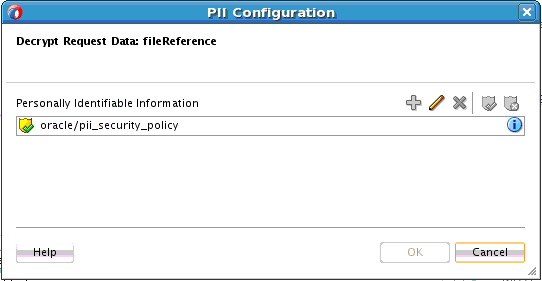
How to Encrypt and Decrypt Specific Fields of Messages
Note:
-
You must decrypt PIIs when an encrypted message leaves the composite. If you attach a PII policy to a service binding component and do not attach a PII policy to a reference binding component, PIIs in the outbound message are not decrypted. This is not a recommended practice, and you receive a runtime error.
-
PIIs encrypted in one SOA composite application cannot be decrypted in another SOA composite application.
To encrypt and decrypt specific fields of messages: