1 Introduction to Oracle B2B
This chapter discusses how Oracle B2B enables the secure and reliable exchange of business documents between an enterprise and its trading partners. It also covers how Oracle B2B supports business-to-business document standards, security, transports, messaging services, and trading partner management.
With Oracle B2B used as a binding component within an Oracle SOA Suite composite application, end-to-end business processes can be implemented. Oracle B2B also supports Health Level 7, which enables health care systems to communicate with each other.
This chapter includes the following sections:
1.1 Oracle B2B and Business-to-Business E-Commerce
You can think of an e-commerce transaction between businesses as analogous to a mail or express carrier (shipping) transaction. In both kinds of transactions, the sender must consider the details required for packaging and sending an item, and the requirements of the receiver. Table 1-1 provides an example that compares the two kinds of transactions.
Table 1-1 Comparing Traditional and E-Commerce Transactions
| Shipping Characteristic | Traditional Shipping Transaction | E-Commerce Transaction |
|---|---|---|
|
What is the item to be shipped, that is, the transaction item? |
Cell phone |
Electronic document Document protocols: Custom, EDI EDIFACT, EDI X12, HL7, OAG, positional flat file, RosettaNet, UCCnet, and more |
|
How is the item packaged? |
Box, bubble wrap |
Packaging protocols: SMIME, SOAP, XMLDSig, XMLEncrypt |
|
How is the item sent and received? |
Truck, ship, airplane |
Transport protocols: HTTP, File, FTP, SFTP (SSH FTP), TCP/IP, SMTP, MLLP, and more |
|
Who is the carrier? |
DHL, FedEx, UPS, USPS |
Message exchange protocols: RNIF, AS1, AS2, ebMS, and more |
|
What carrier services are required? |
|
|
This guide describes how to use Oracle B2B to define the document, the packaging, and the delivery. It also covers how to configure trading partners, create and deploy agreements, and monitor a deployment.
1.2 Protocols Supported in Oracle B2B
Oracle B2B supports numerous industry-standard e-commerce protocols for a range of industries, including health care, retail, IT, telecom, electronics, manufacturing, the food industry, and more.
Table 1-2 lists the protocols supported in Oracle B2B.
Table 1-2 Protocols Supported in Oracle B2B
| Protocol Type | Protocol |
|---|---|
|
Document protocol |
|
|
Packaging protocol |
|
|
Transport protocol |
|
|
Message exchange protocol |
|
Note:
Using the Custom and positional flat file document protocols, you can use many other document types, including W3CXML Schema (OAGIS, xCBL, UBL, ebXML, and more). Use Oracle Document Editor to create the guideline documents.
1.3 Oracle B2B Metadata
Oracle B2B instance data is stored and managed within the SOAINFRA schema of your database. Oracle B2B metadata for design-time and configuration is stored and managed through Metadata Services (MDS), available in Oracle Fusion Middleware.
See Managing the MDS Repository in Administering Oracle Fusion Middleware for more information about MDS.
Because documents created in Oracle B2B are stored in the metadata repository, the transaction log for the database can become full. If this problem often occurs, increase the database configuration parameter to allow a larger log file. A larger log file requires more space but reduces the need for applications to retry the operation.
To increase this value, issue the following command:
db2 update database config for soainfra using LOGFILESIZ 8192
1.4 Security Features of Oracle B2B
Oracle B2B leverages the security features of Oracle Platform Security Services, a comprehensive security platform framework.
Oracle Platform Security Service supports:
-
Authentication
-
Identity assertion and management
-
Authorization
-
The specification and management of application-specific policies
-
Credential and key store management through the Credential Store Framework
-
Auditing
-
Role administration, and role and credential mappings
-
The User and Role API
-
Single sign-on solutions
-
Security configuration and management
-
Cryptography
The default administrator user created during Oracle SOA Suite installation is assigned the administrator role, which has access to all Oracle B2B functionality. The default administrator user can create more users and assign the following roles:
-
Host administrator—This role has access to all Oracle B2B functionality. Only a host trading partner user can have the administrator role for all data.
-
Host monitor—This role can access reports and view runtime data for all trading partners.
-
Remote administrator—This role has limited access to the Partners page. Users with this role can view and edit only their own design data (channels, documents, and so on); can view only those agreements for which they are a partner; and can access only their own runtime report data.
-
Remote monitor—This role can access reports and view runtime data related to its own exchange with the host trading partner.
For information about assigning roles, see Adding Trading Partner Users.
The partner data you design, deploy, and manage with the Oracle B2B user interface is secured by its centralized storage in the Metadata Service (MDS) repository.
Other security features include:
-
Transport protocol-based security for HTTP, FTP, Web service security (OWSM) on WS-HTTP and SMTP exchanges
-
Digital envelopes and certificates
-
Digital signatures for host and remote trading partners
-
Integration with Credential Store Framework for storing all passwords and security credentials
-
Secure HTTP (using Secure Socket Layer (SSL))
-
Encrypted Key Store password for a host trading partner
Note:
Oracle B2B runtime does not support the CLIENT-CERT authentication method. Therefore, B2B is not able to post to OAM-SSO protected URLs.
For more information about security, see Oracle Fusion Middleware Securing Applications with Oracle Platform Security Services.
1.4.1 Payload Obfuscation
Oracle B2B supports payload obfuscation before payloads are stored in the instance repository. The security infrastructure of Oracle Fusion Middleware is used to obfuscate, store, and retrieve the payloads, and ensure that payloads in wire messages, business messages, and application messages are visible to authorized users only. The encryption algorithm is not specifiable. Keys are stored in the Credential Store.
At runtime, the payload is obfuscated before it is stored in the instance repository. When this payload is retrieved from the instance store during processing, it is automatically unobfuscated so that B2B engine processes it.
Similarly, in the outbound direction, if payload obfuscation is required, then the payload is obfuscated before it is stored in the instance repository. If exchange-level encryption is specified, then the payload is encrypted using the encryption scheme specified before it is put on the wire.
Payload obfuscation can be configured in Oracle Enterprise Manager Fusion Middleware Control. See Oracle Fusion Middleware Administering Oracle SOA Suite and Oracle Business Process Management Suite and Setting B2B Configuration Properties in Fusion Middleware Control, for more information.
When you enable payload obfuscation, consider the following:
-
Large payloads, as defined in the Large Payload Size parameter on the Configuration tab, are not obfuscated because they are stored in a directory (file system) rather than the instance repository. Storing a large payload in the file system is a security risk.
-
The obfuscated payload can be accessed in the Oracle B2B interface only by authorized users who have access to the document type. The payload is unobfuscated and displayed in the interface for these authorized users. Other users cannot access the document type at all. The users can be provisioned to access document types. See Restricting Access to Document Types, for information about document-type provisioning.
Obfuscation is available for payloads that use multibyte characters, and is available for non-Oracle databases.
If you migrate instance stores that contain obfuscated payloads, then you must ensure that you export the Credential Store Framework (CSF) as well, because the CSF has the key to unobfuscate those payloads (the same key is used for obfuscation and unobfuscation). If this is a new store, then no migration is required because the key is created (if not already present) the first time the payload is obfuscated.
A payload that was obfuscated and persisted in Oracle B2B is passed unobfuscated to other SOA components within a composite application, when using the Default or JMS integration types. Users viewing this unobfuscated payload in other SOA components are responsible for ensuring that the payload is obfuscated and persisted securely, and that users are authorized to view the payload.
1.4.2 Restricting Access to Document Types
Oracle B2B supports payload security by restricting access based on document type. The following user permissions for document-type access are available:
-
Admin permission for all document types
With this permission, the user can add, access, edit, and delete all document types. This user also has access to administrative functions such as import, export, and purge.
-
Admin permission for specified document types
With this permission, the user can access, edit, and delete the specified document types for which he has permission. The user is not allowed to access, edit, or delete the restricted document types. The user cannot add new document types or have access to any administrative functions such as import, export, and purge.
-
Monitor permission for all document types
With this permission, the user can access and view (but not edit or delete) all document types.
-
Monitor permission for specified document types
With this permission, the user can access and view (but not edit or delete) the specified document types. The user cannot access and view the restricted document types.
The default administrator user can restrict document-type access to other roles as follows:
-
The host administrator can be granted access to all document types, in which case this user can restrict document-type access to other host or remote administrators.
-
The host administrator can be granted access only to specified document types, in which case this user cannot restrict document-type access to other host or remote administrators.
-
The remote administrator can be granted access to specified document types only, or all document types pertaining to the remote trading partner. In either case, the remote trading partner administrator cannot create document types in the system, or provision users for that particular remote trading partner. Users can only be provisioned by a host trading partner administrator user.
-
The host monitor can be granted view-only access to all document types or to specified document types, but cannot restrict document-type access to other users.
-
The remote monitor can be granted view-only access to all document types pertaining to the remote trading partner or to specified document types pertaining to the remote trading partner, but cannot restrict document-type access to other users.
Note:
Admin users with access to all Administration tab functions lose admin privileges when permission for any or all document types is assigned, and the Administration tab is no longer available.
See Add Document Types That the User Has Permission to Access for information about how to specify document type access in the Oracle B2B interface.
When access to specific document types is restricted, consider the following:
-
New document definitions for a restricted document type cannot be added.
-
No document types can be imported, exported, or purged.
-
No document types can be modified on the Partners > Documents tab.
-
The restricted document types are listed, but details cannot be viewed or accessed, on the following tabs:
-
Administration > Document tab
-
Reports tabs
-
Metrics tabs
-
-
Agreements that include document definitions for restricted document types cannot be modified or exported.
-
In a SOA composite with a B2B binding component, restrictions on document types are not in effect. All document types are available to any user in the B2B Configuration Wizard of Oracle JDeveloper.
1.5 How Oracle B2B Fits into a SOA Implementation
As a business-to-business gateway, Oracle B2B is used to extend business processes to trading partners. When Oracle B2B is used in a SOA composite application, you can model an end-to-end business process integration.
Oracle SOA Suite provides a complete set of service infrastructure components for designing, deploying, and managing composite applications. The multiple technology components of a composite application share common capabilities, including a single deployment and management model and tooling, end-to-end security, and unified metadata management. See Oracle Fusion Middleware Developing SOA Applications with Oracle SOA Suite for more information.
In a SOA implementation, Oracle B2B functions as a binding component, with network protocols and services that enable message sending and receiving:
-
As a service (inbound), the SOA composite application receives messages from Oracle B2B
-
As a reference (outbound), the SOA composite application passes a message to Oracle B2B, which in turn sends the message to partners.
In addition to messages, Oracle B2B can also send attachments and large payloads in a SOA implementation. See Handling Large Payloads, for information about handling large payloads.
Note:
With the integration of Oracle B2B, Mediator, and BPEL components within Oracle SOA Suite, the XML Gateway Internal Delivery channels are not needed in Oracle B2B 11g to communicate with Oracle E-Business Suite. This can be achieved by using the Oracle Application Adapter available in Oracle SOA Suite.
1.6 Sending a Purchase Order: An Example of a SOA Implementation
This example describes how the components of a SOA composite application are used to send a purchase order that originates from Oracle E-Business Suite.
Figure 1-1is an illustration of this example.
Figure 1-1 An Outbound Purchase Order in a SOA Composite Application
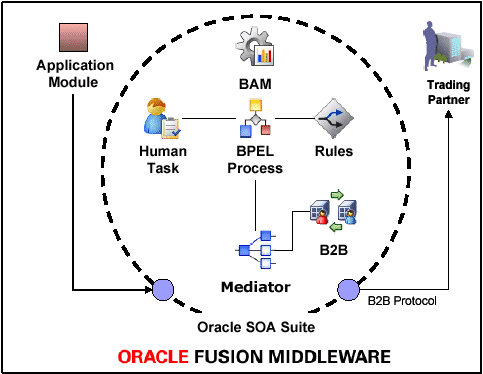
Description of "Figure 1-1 An Outbound Purchase Order in a SOA Composite Application"
The outbound purchase order (P. O.) is an XML document that participates in an end-to-end business process as follows:
-
An application, for example, Oracle E-Business Suite, initiates the P. O. process. The P. O. document uses the application-generated XML.
-
Oracle Mediator receives the P. O. from Oracle E-Business Suite. The P. O. is translated to canonical XML through XSLT Mapper, and is validated by using the schema obtained when the composite application was validated. Oracle Mediator routes the message to Oracle BPEL Process Manager.
-
Oracle BPEL Process Manager receives the P. O. from Oracle Mediator. Business processes such as human workflow, business rules, and error handling can apply before Oracle BPEL Process Manager sends the P. O. back to Oracle Mediator.
-
Oracle Mediator receives the P. O. from Oracle BPEL Process Manager. The P. O. is transformed from canonical XML to the target XML through XSLT Mapper and then routed to Oracle B2B.
-
Oracle B2B receives the P. O. from Mediator, translates the P. O. to EDI native format, for example, and manages the interaction with the trading partner.
-
Oracle Business Activity Monitoring (BAM) monitors the end-to-end process.
See Using Oracle B2B in the Oracle JDeveloper Environment for information about how to include a B2B binding component in a SOA composite application.
1.7 Administering Oracle B2B in the Oracle Fusion Middleware Environment
Several components provide monitoring, configuration, and performance tuning capabilities for Oracle B2B.
-
Oracle Enterprise Manager Fusion Middleware Control—Set Oracle B2B Server properties to enable Enterprise Manager metrics and monitor the Oracle B2B Infrastructure.
See the following for more information:
-
Configuring Oracle B2B and Monitoring Oracle B2B in Administering Oracle SOA Suite and Oracle Business Process Management Suite.
Within the Oracle B2B interface, use the following for monitoring and configuration:
-
Administration > Configuration tab
-
Administration > Reports tab
See Creating Reports.
-
Administration > Metrics link
See Using B2B Metrics .
1.8 Accessibility Options
1.8.1 Enabling Accessibility Features in Oracle B2B
Oracle B2B provides the screen reader option, which enables your screen reader to access and read all components of the application.
To enable the screen reader:
- Click the Enable screen reader mode link in the top right corner.
- The following confirmation message appears: This will enable screen reader mode for the current session. Do you want to continue?
- Click Yes to confirm.
Note:
Where the calendar appears in the user interface, it is not available in Screen Reader mode.