Managing Oracle Directory Services Manager's Java Key Store
odsm.cer JKS, and deleting expired certificates. It includes the following sections:Introduction to Managing ODSM's Java Key Store
Oracle Directory Services Manager (ODSM) stores its private key, certificate and trusted certificates in a Java Key Store (JKS).
As administrator, you are responsible for managing ODSM's JKS. One important task you must perform is to remove ODSM certificates from the JKS when they have expired. This appendix explains how.
The first time ODSM is invoked, it generates a random password and assigns the password to its JKS. The JKS file has the name odsm.cer. The file resides in a directory with a name of the form:
$DOMAIN_HOME/config/fmwconfig/servers/AdminServer/applications/odsm/conf
ODSM stores the password to its JDK in the Credential Store Framework (CSF), a secure storage framework provided by Oracle. The WebLogic server administrator can retrieve the JDK password stored in the CSF.
ODSM also generates a self-signed certificate for itself and stores it in its JKS. This self-signed certificate is valid for 15000 days from the date of generation. This self-signed certificate is intended for testing purposes only. Oracle recommends replacing this self-signed certificate with a certificate signed by a Certificate Authority (CA) for production purposes.
There is no web-based tool for managing a JKS. To manage ODSM's JKS, you use keytool, a command-line tool shipped with the Oracle JRE or JDK.
See Also:
-
The section about configuring the credential store in the Oracle Fusion Middleware Application Security Guide for more information about the CSF.
-
For information about Oracle Java, including the JavaTM Cryptography Architecture API Specification & Reference and keytool - Key and Certificate Management Tool, see:
Retrieving ODSM's Java Key Store Password
To manage Oracle Directory Services Manager's Java Key Store, you must first retrieve Oracle Directory Services Manager's Java Key Store password.
There are two methods for retrieving this password:
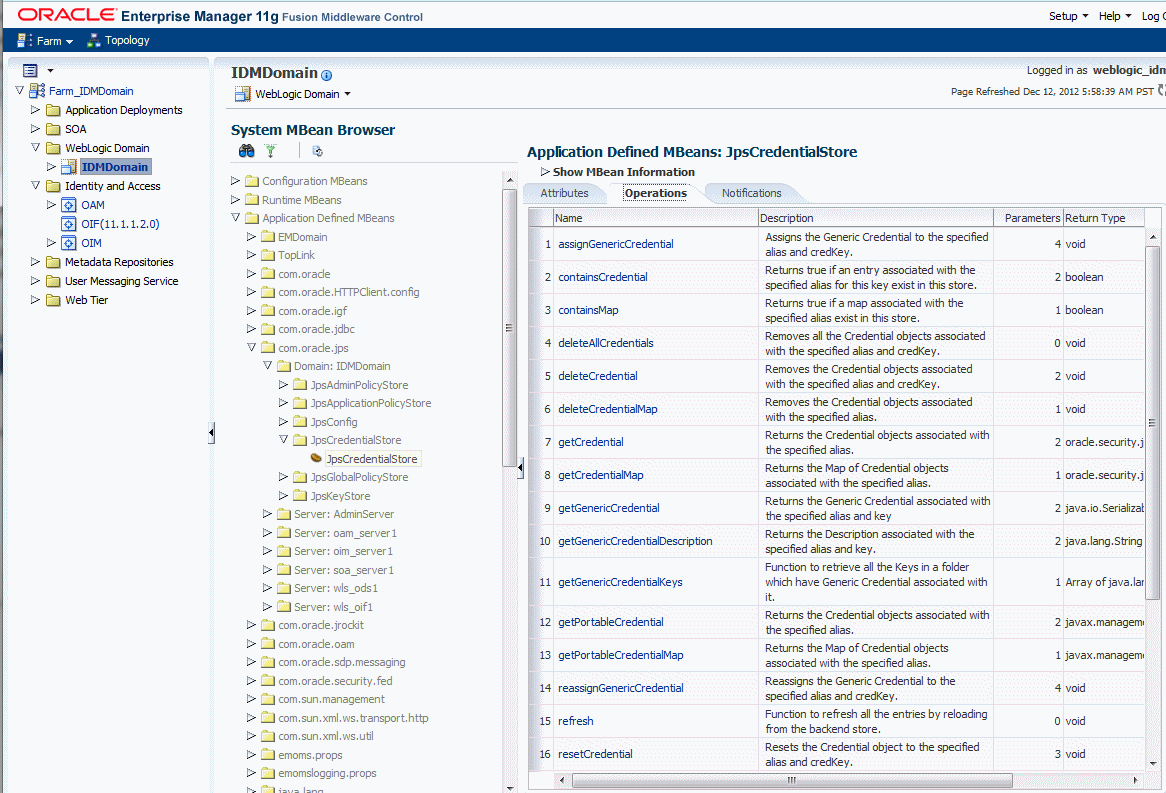
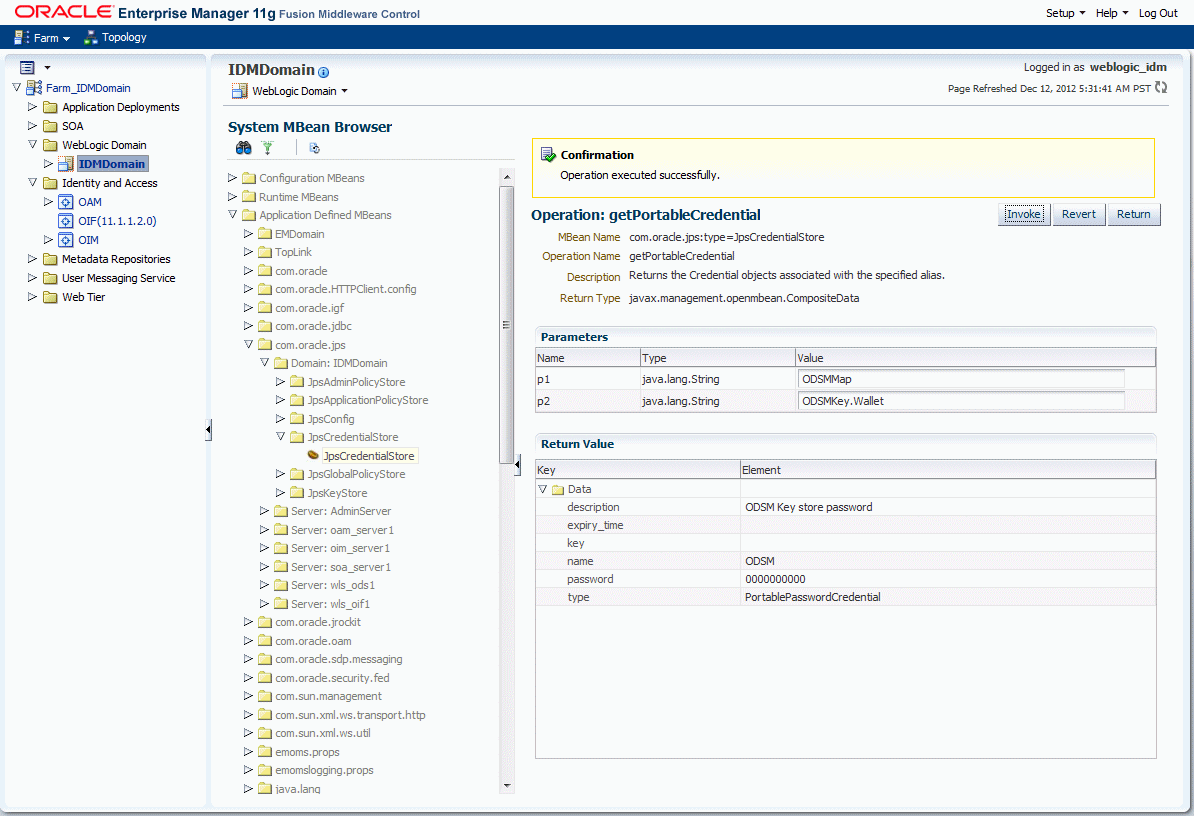
Retreiving Password Using Enterprise Manager Fusion Middleware Control
Use Enterprise Manager to retrieve the Oracle Directory Services Manager's Java Key Store password.
Perform the following steps:
Retrieving Password Using a Python Script
If you do not have Enterprise Manager, you can retrieve the Oracle Directory Services Manager's Java Key Store password by using a Python script.
To retrieve this password, perform the following steps:
See Also:
For more information, refer to the following publications:
-
Managing Keys and Certificates with the Keystore Service in Oracle Fusion Middleware Securing Applications with Oracle Platform Security Services
Listing the Contents of odsm.cer Java Key Store
After you retrieve the JKS password, you can manage the JKS by using keytool.
To list the contents of odsm.cer, use the keytool command, as follows:
cd directory_where_odsm.cer_resides JAVA_HOME/bin/keytool -list -keystore odsm.cer \ -storepass password_obtained_from_CSF
For example:
$ cd DOMAIN_HOME/config/fmwconfig/servers/AdminServer/applications/odsm/conf $ JAVA_HOME/bin/keytool -list -keystore odsm.cer -storepass "&M)S86)/RB" -v Keystore type: JKS Keystore provider: SUN Your keystore contains 2 entries Alias name: serverselfsigned Creation date: Dec 26, 2008 Entry type: PrivateKeyEntry Certificate chain length: 1 Certificate[1]: Owner: CN=OVD, OU=Development, O=Oracle, L=Redwood Shores, ST=California, C=US Issuer: CN=OVD, OU=Development, O=Oracle, L=Redwood Shores, ST=California, C=US Serial number: 495586b6 Valid from: Fri Dec 26 17:36:54 PST 2008 until: Wed Jun 24 18:36:54 PDT 2009 Certificate fingerprints: MD5: 6C:11:16:F3:88:8D:18:67:35:1E:16:5B:3E:03:8A:93 SHA1: F4:91:39:AE:8B:AC:46:B8:5D:CB:D9:A4:65:BE:D2:75:08:17:DF:D0 Signature algorithm name: SHA1withRSA Version: 3 ******************************************* ******************************************* Alias name: cn=rootca, o=oracle, c=us (0) Creation date: Dec 31, 2008 Entry type: trustedCertEntry Owner: CN=RootCA, O=Oracle, C=US Issuer: CN=RootCA, O=Oracle, C=US Serial number: 0 Valid from: Tue Dec 30 02:33:11 PST 2008 until: Mon Jan 24 02:33:11 PST 2050 Certificate fingerprints: MD5: 72:31:7B:24:C9:72:E3:90:37:38:68:40:79:D1:0B:4B SHA1: D2:17:84:1E:19:23:02:05:61:42:A9:F4:16:C8:93:84:E8:20:02:FF Signature algorithm name: MD5withRSA Version: 1 ******************************************* *******************************************
Deleting Expired Certificates
There is no automatic mechanism for removing certificates from the JDK when they expire.
As administrator, you must determine when a certificate has expired and remove it.
This section contains the following topics:
Determining the Expiration Date of a Certificate
This section helps you to determine the expiration date of a certificate.
As explained in Listing the Contents of odsm.cer Java Key Store, you list all certificates in odsm.cer by using keytool. The listing contains the valid dates for each certificate. For example, the following certificate is valid until Sat Oct 31 09:41:23 PDT 2008:
Alias name: cn=ovd, ou=development, o=MyCompany, l=redwood shores, st=california, c=us (1241455283) Creation date: May 5, 2008 Entry type: trustedCertEntry Owner: CN=OVD, OU=Development, O=MyCompany, L=Redwood Shores, ST=California, C=US Issuer: CN=OVD, OU=Development, O=Oracle, L=Redwood Shores, ST=California, C=US Serial number: 49ff1ab3 Valid from: Mon May 04 09:41:23 PDT 2008 until: Sat Oct 31 09:41:23 PDT 2008 Certificate fingerprints: MD5: 93:0E:41:5E:95:88:71:BD:8A:49:ED:A9:29:3B:0A:1E SHA1: 84:C6:75:60:D9:BE:7B:CA:D6:8B:B5:4B:97:E4:20:39:44:82:FE:93 Signature algorithm name: SHA1withRSA Version: 3
If certificate's validity period has expired, delete it using keytool as explained in the next section.
Deleting a Certificate
To delete a certificate in odsm.cer, use keytool.
Execute the following command:
cd directory_where_odsm.cer_is_present JAVA_HOME/bin/keytool -delete -keystore odsm.cer -storepass password_obtained_from_CSF -alias "cn=rootca, o=oracle, c=us (0)"
For example
$> JAVA_HOME/bin/keytool -delete -keystore odsm.cer \ -storepass "&M)S86)/RB" -alias "cn=rootca, o=oracle, c=us (0)" [Storing odsm.cer]