21 Managing Directory Schema
21.1 Introduction to Managing Directory Schema
This section introduces you to directory schema management and related topics.
This section introduces you to the following topics:
See Also:
LDAP Schema Overview in Oracle Fusion Middleware Reference for Oracle Identity Management.
21.1.1 Understanding Directory Schema Management
Oracle recommends that you understand the basic concepts of directory components before attempting to add to or modify the base schema in the directory.
A directory schema:
-
Contains rules about the kinds of objects you can store in the directory
-
Contains rules for how directory servers and clients treat information during operations such as a search
-
Helps to maintain the integrity and quality of the data stored in the directory
-
Reduces duplication of data
-
Provides a predictable way for directory-enabled applications to access and modify directory objects
Note:
Every schema object in the Oracle Internet Directory has certain limitations. For example, some objects cannot be changed. These limitations are explained as constraints and rules in this chapter.
21.1.2 Storage Location of Schema Information in the Directory
The directory schema contains all information about how data is organized in the DIT—that is, metadata such as that for an object class, an attribute, a matching rule, and syntax. This information is stored in a special class of entry called a subentry. More specifically, Oracle Internet Directory, following LDAP Version 3 standards, stores this information in subentries of type subSchemaSubentry.
You can add new object classes and attribute types to a subentry of type subSchemaSubentry. You cannot add new matching rules and syntaxes beyond those already supported by Oracle Internet Directory.
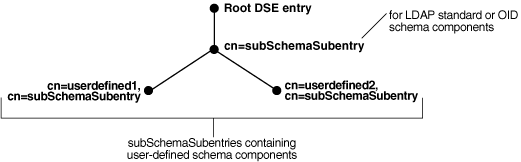
Before 10g (10.1.4.0.1) there was only one subSchemaSubentry, directly under the root DSE entry, called cn=subSchemaSubentry, and you always added object classes and attribute types directly to it. As of 10g (10.1.4.0.1), the entry cn=subSchemaSubentry can now have subordinate entries. Any application using Oracle Internet Directory that must add schema components can create its own subSchemaSubentry under cn=subSchemaSubentry and add the schema components to it. Figure 21-1 shows some subSchemaSubentry entries that were defined by applications, such as cn=userdefined1,cn=subschemasubentry and cn=userdefined2,cn=subschemasubentry.
Best practice is to create one subordinate entry under subschemasubentry for one application or a group of applications. All the attributeTypes and objectClasses related to the application should be put under its corresponding entry under cn=subschemasubentry.
All the schema entries are listed in the root DSE attribute subschemasubentry.
Figure 21-1 Location of Schema Components in Entries of Type subSchemaSubentry
You cannot use bulkload to add subSchemaSubentry entries. You must use ldapadd.
21.1.3 Understanding Object Classes
This section introduces you to object classes and related topics.
This section introduces you to the following topics:
21.1.3.1 About Object Classes
When you add an entry, you associate it with one or more object classes. Each object class contains attributes that you want to associate with the new entry.
For example, if you are creating an entry for an employee, you can associate it with the person object class. This object class contains many of the attributes that you want to associate with that employee entry, including, for example, name, address, and telephone number.
Note:
The attribute page in the Schema tab in Oracle Directory Services Manager includes a Referenced By section that lists the object classes that directly reference an attribute
Each object class derives from a hierarchy of superclasses, and it inherits attributes from these superclasses. By default, all object classes inherit from the top object class. When you assign an object class to an entry, the entry inherits all of the attributes of both that object class and its superclasses.
The attributes that entries inherit from a super class may be either mandatory or optional. Values for optional attributes need not be present in the directory entry.
You can specify for any object class whether an attribute is mandatory or optional; however, the characteristic you specify is binding only for that object class. If you place the attribute in another object class, you can again specify whether the attribute is mandatory or optional for that object class. You can:
-
Add a new, nonstandard object class and assign it existing attributes
-
Select from existing standard object classes
-
Modify an existing object class, assigning it a different set of attributes
-
Add and modify existing attributes
See Also:
LDAP Schema Overview in Oracle® Fusion Middleware Reference for Oracle Identity Management for a list of schema elements installed with Oracle Internet Directory
Entries must be added in a top-down sequence—that is, when you add an entry, all of its parent entries must already exist in the directory. Similarly, when you add entries that reference object classes and attributes, those referenced object classes and attributes must already exist in the directory schema. In most cases this is not a problem because the directory server is delivered with a full set of standard directory objects.
When you add or perform an operation on an entry, you do not need to specify the entire hierarchy of superclasses associated with that entry. You can specify only the leaf object classes. Oracle Internet Directory resolves the hierarchy for the leaf object classes and enforces the information model constraints. This is often called object class explosion. For example, the inetOrgPerson object class has top, person and organizationalPerson as its superclasses. When you create an entry for a person, you must specify only inetOrgPerson as the object class. Oracle Internet Directory then enforces the schema constraints defined by the respective superclasses, namely, top, person, and organizationalPerson.
21.1.3.2 Add Object Classes
When you add object classes, keep the following in mind:
-
Every structural object class must have
topas a superclass. -
The name and the object identifier of an object class must be unique across all the schema components. The actual attribute name and any attribute name aliases must be unique across all attribute names and attribute aliases. The Object Identifier must begin with the unique identifier 2.16.840.1.113894 followed by either the Oracle-supplied prefix.9999 or a site-specific prefix.
-
Schema components referred to in the object class, such as superclasses, must already exist.
-
The superclass of an abstract object class must be abstract also.
-
It is possible to redefine mandatory attributes in a superclass into optional attributes in the new object class. Conversely, optional attributes in a superclass can be redefined into mandatory attributes in the new object class.
See Also:
Subclasses, Superclasses, and Inheritance for a conceptual discussion of these terms
21.1.3.3 Types of Modification to an Existing Object Class
You can perform modifications to an existing object class through Oracle Directory Services Manager and through the command-line tools.
You can make these changes to an object class in the following ways:
-
Change a mandatory attribute into an optional attribute
-
Add optional attributes
-
Add additional superclasses
-
Convert abstract object classes into structural or auxiliary object classes unless the abstract object class is a superclass to another abstract object class
When you modify object classes, keep these guidelines in mind:
-
You cannot modify an object class that is part of the standard LDAP schema. You can, however, modify user-defined object classes.
-
If existing object classes do not have the attributes you need, you can create an auxiliary object class and associate the needed attributes with that object class.
-
You cannot add additional mandatory attributes to an existing object class.
-
You should not modify object classes in the base schema.
-
You cannot remove attributes or superclasses from an existing object class.
-
You cannot convert structural object classes to other object class types.
-
You should not modify an object class if there are entries already associated with it.
21.1.3.4 Limitations for Deleting Object Classes
The limitations on deleting object classes are:
-
You cannot delete object classes from the base schema.
-
You can delete object classes that are not in the base schema if they are not directly or indirectly referenced by other schema components. For example, there may be some directory entries referring to these object classes. Deleting these object classes renders these entries inaccessible.
21.1.4 Understanding Attributes
You can find introduction on how to add, modify or delete attributes.
This section introduces you to the following topics:
21.1.4.1 Introduction to Attributes
You must understand attributes from a conceptual standpoint before attempting operations involving attributes.
In most cases, the attributes available in the base schema will suit the needs of your organization. However, if you decide to use an attribute not in the base schema, you can add a new attribute or modify an existing one.
By default, attributes are multivalued. You can specify an attribute as single-valued by using either Oracle Directory Services Manager or command-line tools.
Note:
The maximum length of a non-binary attribute value is 4000 bytes.
See Also:
-
Understanding the Concept of Attributes in Oracle Internet Directory for a conceptual discussion of attributes
-
Attribute Options for information about attribute options
-
Attribute Syntax in Oracle Fusion Middleware Reference for Oracle Identity Management for information about using syntax to specify the size of the attribute value
.
21.1.4.2 Rules for Adding Attributes
The rules for adding attributes are:
-
The name and the object identifier of an attribute must be unique across all the schema components.
-
Syntax and matching rules must agree.
-
Any super attributes must already exist.
-
The length of an attribute name must not exceed 127 characters.
21.1.4.3 Rules for Modifying Attributes
The rules for modifying attributes are:
-
The name and the object identifier of an attribute must be unique across all the schema components.
-
The syntax of an attribute cannot be modified.
-
A single-valued attribute can be made multi-valued, but a multi-valued attribute cannot be made single-valued.
-
You cannot modify or delete base schema attributes.
21.1.4.4 Rules for Deleting Attributes
The rules for deleting attributes are:
-
You can delete only user-defined attributes. Do not delete attributes from the base schema.
-
You can delete any attribute that is not referenced directly or indirectly by some other schema component.
If you delete an attribute that is referenced by any entry, that entry will no longer be available for directory operations.
Note:
The attribute page in the Schema tab in Oracle Directory Services Manager includes a Referenced By section that lists the object classes that directly reference an attribute
See Also:
Attribute Syntax in Oracle Fusion Middleware Reference for Oracle Identity Management for information about using syntax to specify the size of the attribute value.
21.1.4.5 Index option in Oracle Internet Directory to Search Attributes
Oracle Internet Directory uses indexes to make attributes available for searches. When Oracle Internet Directory is installed, the entry cn=catalogs lists available attributes that can be used in a search.
As of Oracle Internet Directory 11g Release 1 (11.1.1.6.0), a new autocatalog feature is enabled by default in fresh installs. You can also enable it if you have upgraded from a previous release. When this feature is enabled, Oracle Internet Directory automatically indexes attributes when you search for them. You can disable the feature by setting the orclautocatalog attribute of the DSA configuration entry to 0. To modify this attribute from the command line, see Setting System Configuration Attributes by Using ldapmodify. To modify this attribute by using Oracle Enterprise Manager
Fusion Middleware Control, see Configuring Shared Properties.
If the autocatalog feature is not enabled, and you want to use additional attributes in search filters, you must add them to the catalog entry.
You can index an attribute or drop an index from an attribute by using either ldapmodify or catalog. You can also manage attribute indexes by using Oracle Directory Services Manager.
Note:
-
When autocatalog is disabled, if you attempt to perform a search with a non-indexed attribute specified as a required attribute, the server returns a
Function not implementedorDSA unwilling to performerror. -
Autocatalog is performed only when a valid user connects to Oracle Internet Directory. Anonymous bind search does not trigger the autocatalog feature. Also, this event is audited.When two or more clients search the same non-cataloged attribute at the same time, only one thread initiates the catalog process. The other threads return LDAP error 53 and the additional information:
OID-5018: Cataloging for attribute is already in progress. The cataloging thread waits for the cataloging (separate) process to finish or until configuredorclmaxserverresptime. Whenorclmaxserverresptimehas elapsed, the cataloging thread returns LDAP error 53 and the additional info: "OID-5018: Cataloging for attribute is already in progress.The catalog of each attribute is created once only on every directory so this is a one time effect for every non-cataloged attribute. If a search is interrupted due to a client side time-out or an explicit kill command, the in-progress catalog will continue and the subsequent searches on same attribute will succeed once the catalog processing completes. -
You can use Oracle Directory Services Manager to index an attribute only if it has not been used yet. You cannot use Oracle Directory Services Manager to index an attribute that is already in use. To index an attribute that is in use, use ldapmodify as described in Indexing an Attribute by Using ldapmodify, or the Catalog Management tool, as described in Indexing an Attribute by Using the Catalog Management Tool.
Note:
You can index only those attributes that have:
-
An equality matching rule
-
Matching rules supported by Oracle Internet Directory as listed in Attribute Matching Rules in Oracle Fusion Middleware Reference for Oracle Identity Management.
-
Less than 128 characters in their names
21.1.5 Methods to Extend the Number of Attributes Associated with Entries
You can understand how to extend the number of attributes associated with entries.
This section contains these topics:
21.1.5.1 Extending the Number of Attributes Associated with Entries
You can extend the number of attributes for entries. The method you use depends on whether the entries already exist.
If the entry does not yet exist, you can extend the number of attributes before creating the entry in the directory.
For an existing entry, there are two ways to extend the attributes associated with it.
-
Add names of object classes to the list in the
objectclassattribute for each entry. If your directory is relatively small, then this can be a desirable method because it enables searches for entries based on that attribute. However, if your directory is large, then entering the names of object classes to theobjectclassattribute can be very painstaking. -
Use content rules. This may be a more efficient way to extend the content of entries in a large directory.
21.1.5.2 Extending the Number of Attributes before Creating Entries in the Directory
At installation, Oracle Internet Directory provides standard LDAP object classes and several proprietary object classes. You cannot add mandatory attributes to the sets of attributes belonging to these predefined object classes. If a given object class does not contain all the attributes that you want for an entry, then you can do one of the following:
-
Define a new (base) object class
-
Define an object subclass
See Also:
-
Oracle Identity Management LDAP Object Classes in Oracle Fusion Middleware Reference for Oracle Identity Management for a list of object classes in the schema installed with Oracle Internet Directory.
-
Adding Object Classes by Using Oracle Directory Services Manager for instructions on how to define a new object class or object subclass
-
21.1.5.3 Specifications to Extend the Number of Attributes for Existing Entries by Creating an Auxiliary Object Class
You can create an auxiliary object class containing the additional attributes you want for your entry, and then associate that auxiliary object class with the entry. You associate the auxiliary object class with the entry by specifying it in the objectclass attribute for the entry.
See Also:
-
Adding Object Classes by Using Oracle Directory Services Manager for instructions on creating auxiliary object classes
-
Managing Directory Entries in Oracle Internet Directory for instructions on associating an object class with an entry
21.1.5.4 Specifications to Extend the Number of Attributes for Existing Entries by Creating a Content Rule
A content rule, following your specifications, determines the kind of content allowed in any entry that is associated with a particular structural object class. For example, you can specify that any entry associated with the person object class must have, in addition to the attributes in that object class, other attributes as well. The additional attributes can be those of an auxiliary object class, and they can be either mandatory or optional.
Whereas you must list auxiliary classes in the entry—which can be an administrative burden—you do not need to list content rules in the entry.
In addition to the structural object class to which it applies, a content rule can also indicate:
-
Auxiliary object classes allowed for entries governed by the rule
-
Mandatory attributes, in addition to those called for by the structural and auxiliary object classes, required for entries governed by the DIT content rule
-
Optional attributes permitted for entries governed by the DIT content rule, in addition to those called for by structural and auxiliary object classes
This section tells you how to manage content rules by using Oracle Directory Services Manager and command-line tools.
During the process of defining a new content rule, the directory server validates the syntax and ensures that the attributes and object classes listed in the content rule have been defined in the directory.
Content rules can be specified for structural object classes only. The name of the object class is case-insensitive.
You can specify more than one content rule for each structural object class provided the content rules have different labels associated with them.
To modify an existing definition of a content rule, the client must first delete the existing definition and then add the new definition. Simple replacement of a content rule by using the replace command is not allowed.
To delete a content rule, the client must specify only the structural object class and the alphanumeric object identifier of the content rule. Optionally, the client can also specify the associated version of the content rule to be deleted.
21.1.5.5 Rules for Creating and Modifying Content Rules
Content rules are defined as values of the DITContentRule attribute in the subschema subentry (cn=subschemasubentry). They must conform to these rules:
-
The structural object class of the entry identifies the content rule applicable for the entry. If no content rule is present for a structural object class, then entries associated with that object class contain only the attributes permitted by the structural object class definition.
-
Because a content rule is associated with a structural object class, all entries of the same structural object class have the same content rule regardless of their location in the DIT.
-
The content of an entry must be consistent with the object classes listed in the
objectClassattribute of that entry. More specifically:-
Mandatory attributes of object classes listed in the
objectClassattribute must always be present in the entry. -
Optional attributes of auxiliary object classes indicated by the content rule can also be present even if the
objectClassattribute does not list these auxiliary object classes.See Also:
Specifications to Extend the Number of Attributes for Existing Entries by Creating an Auxiliary Object Class for instructions on creating and managing content rules
-
21.1.5.6 Schema Enforcement When Using Content Rules
When validating an object for schema consistency, the directory server uses the content rule for the structural object class of the entry. It also uses all the other object classes listed in the entry.
If more than one content rule exists for an object class, then, when adding or modifying an entry, or when bulkloading data, the following rules apply.
-
An entry can have attributes from all the auxiliary object classes listed in the various content rules. Not specifying an object class in the content rule does not restrict a client from explicitly adding an auxiliary object class in directory entries.
-
An entry must contain values for all the mandatory attributes listed in:
-
The content rules
-
The object classes associated with the entry
-
The auxiliary object classes listed in the content rule applicable to the entry
-
-
Optionally, an entry can contain values for any or all the optional attributes listed in:
-
The content rule
-
The object classes listed in the entry
-
The auxiliary object classes listed in the content rule applicable for the entry
-
-
If any attribute is specified as mandatory, then it overrides any other definition that defines it as optional.
21.1.5.7 Searches for Object Classes Listed in Content Rules
Because the auxiliary object classes listed in content rules are not listed in the objectclass attribute for an entry, you cannot list those object classes as filters when you search for entries. Instead, base your searches on the structural object class that you are interested in. If you must base your search on an auxiliary object class, then add that auxiliary object class to the objectclass attribute in the user objects explicitly.
For example, a content rule for structural object class inetOrgPerson may specify an auxiliary object class orclUser. However, this does not mean that every inetOrgPerson entry in the directory contains orclUser as a value of the objectclass attribute. As a result, the search with the filter objectclass=orclUser fails. Instead of querying for an auxiliary object class contained in the content rule, you should query for structural object classes—for example, objectclass=inetOrgPerson.
To base a search on objectclass=orcluser, add orclUser as one of the values of objectclass attribute in each entry.
These considerations apply also to filters used in access control policies. If you are using a content rule to associate additional auxiliary object classes, then use only the structural object classes in the search filters.
21.1.6 Understanding Attribute Aliases
As of 10g (10.1.4.0.1), you can create aliases for attribute names. For example. you could create the user-friendly alias surname for the attribute sn. After you create an alias for an attribute name, a user can specify the alias instead of the attribute name in an LDAP operation.
You define an alias for an attribute in the LDAP schema definition of the attribute. The directory schema operational attribute attributeTypes has been enhanced to allow you to include aliases in the attribute name list. In previous releases, the format for an attribute name list was:
attributeTypes=( ObjectIdentifier NAME 'AttributeName' ... )
As of 10g (10.1.4.0.1), you may optionally specify:
attributeTypes=( ObjectIdentifier NAME ( 'AttributeName' 'Alias1' 'Alias2' ...) ... )
This is consistent with the LDAP protocol as specified by RFC 2251 and RFC 2252. In the attribute name list, the first item is recognized as the name of the attribute and rest of the items in the list are recognized as attribute aliases. For example, to specify the alias surname for the attribute sn, you would change the schema definition for sn from:
attributeTypes=( 2.5.4.4 NAME 'sn' SUP name )
to:
attributeTypes=( 2.5.4.4 NAME ( 'sn' 'surname') SUP name )
The following rules apply to attribute aliases:
-
An attribute alias name must be unique throughout all the actual attribute names and other attribute aliases across all the schema components.When you define an attribute, the first value in the
attributeTypesdefinitionNAMEfield must be the actual attribute name. You define attribute aliases in theNAMEfield after the actual attribute name. -
Attribute alias names follow the same syntax rules as attribute names.
-
You delete an attribute alias by redefining the attribute without the alias.
See Managing Directory Schema by Using the Command Line.
See Also:
Managing Alias Entries for information about alias entries.
21.2 Managing Directory Schema by Using Oracle Directory Services Manager
You can perform various operations on object classes like searching, adding, deleting using Oracle Directory Services Manager.
This section contains the following topics:
-
Searching for Object Classes by Using Oracle Directory Services Manager
-
Adding Object Classes by Using Oracle Directory Services Manager
-
Deleting Object Classes by Using Oracle Directory Services Manager
-
Viewing Properties of Object Classes by Using Oracle Directory Services Manager
-
Adding a New Attribute by Using Oracle Directory Services Manager
-
Modifying an Attribute by Using Oracle Directory Services Manager
-
Deleting an Attribute by Using Oracle Directory Services Manager
-
Viewing All Directory Attributes by Using Oracle Directory Services Manager
-
Searching for Attributes by Using Oracle Directory Services Manager
-
Adding an Index to a New Attribute by Using Oracle Directory Services Manager
-
Adding an Index to an Existing Attribute by Using Oracle Directory Services Manager
-
Adding an Index to an Existing Attribute by Using Oracle Directory Services Manager
-
Creating a Content Rule by Using Oracle Directory Services Manager
-
Modifying a Content Rule by Using Oracle Directory Services Manager
-
Viewing Matching Rules by Using Oracle Directory Services Manager
21.2.1 Searching for Object Classes by Using Oracle Directory Services Manager
To search for object classes by using Oracle Directory Services Manager:
21.2.2 Adding Object Classes by Using Oracle Directory Services Manager
To add object classes by using Oracle Directory Services Manager:
See Also:
-
Oracle Directory Services Manager online help for further details about adding object classes
21.2.3 Modifying Object Classes by Using Oracle Directory Services Manager
You can add optional, but not mandatory, attributes to an object class already in use by entries. If you add optional attributes to an object class already in use, then no special rules apply, and they are added as empty attributes to those entries.
To modify an object class:
21.2.4 Deleting Object Classes by Using Oracle Directory Services Manager
Note:
Oracle recommends that you do not delete object classes from the base schema. If you delete an object class that is referenced by any entries, those entries then become inaccessible.
Deleting object classes from the base schema might also cause Oracle Directory Services Manager to malfunction.
To delete an object class by using Oracle Directory Services Manager:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- Click + next to Object Classes to expand the Object Classes panel. Use the scroll bar to move through the alphabetical list of Object Classes.
- Select the object class you want to delete.
- Choose Delete from the toolbar, then click Delete in the confirmation dialog.
21.2.5 Viewing Properties of Object Classes by Using Oracle Directory Services Manager
To view all object classes in the schema:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- Click + next to Object Classes to expand the Object Classes panel. Use the scroll bar to move through the alphabetical list of Object Classes.
- Click the Object Class you want to view. The Object Class tab appears on the right side of the page.
- To see more detail about a superclass or attribute of the object class, select the item and click Edit. Click Cancel to return to the object class panel
21.2.7 Modifying an Attribute by Using Oracle Directory Services Manager
To modify an attribute by using Oracle Directory Services Manager:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- In the Attributes panel, select an attribute that you would like to modify. The attribute page appears on the right.
- Modify or add information in editable fields, if any, in the attribute tab.
- Choose Apply.
21.2.8 Deleting an Attribute by Using Oracle Directory Services Manager
Note:
Oracle recommends that you not delete attributes or object classes from the base schema.
Deleting attributes or object classes from the base schema might cause Oracle Directory Services Manager to malfunction.
To delete an attribute:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- In the Attributes panel, select an attribute that you would like to delete.
- Choose Delete from the toolbar in the left panel, then click Delete in the confirmation dialog.
21.2.9 Viewing All Directory Attributes by Using Oracle Directory Services Manager
To view attributes by using Oracle Directory Services Manager:
21.2.10 Searching for Attributes by Using Oracle Directory Services Manager
To search for attributes by using Oracle Directory Services Manager:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, select Schema.
- Expand the Attributes list in the left pane.
- Enter a search term in the Search field in the left pane. You can use an asterisk (
*) or question mark (?) as a wildcard. Click the Go icon or pressEnteron your keyboard. - The results of your search appear in the list in the left pane. To dismiss the search and return to the complete list of attributes, click the Clear search text icon.
21.2.11 Adding an Index to a New Attribute by Using Oracle Directory Services Manager
To add an index to an attribute:
- Create an attribute as described in Adding a New Attribute by Using Oracle Directory Services Manager or in Adding and Modifying Attributes by Using ldapmodify.
- In the New Attribute Type dialog box, select the Indexed box.
21.2.12 Adding an Index to an Existing Attribute by Using Oracle Directory Services Manager
You can use Oracle Directory Services Manager to add an index to an existing attribute only if that attribute is not in use yet.
To add an index to an existing attribute:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, select Schema.
- Select an attribute that is not currently indexed that you want to add the index to.
- Click the The attribute will be cataloged/decataloged icon. When the Confirm Dialog appears, click Confirm.
- The Indexed box indicates that the attribute is indexed.
21.2.13 Dropping an Index from an Attribute by Using Oracle Directory Services Manager
To drop an index from an attribute:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, select Schema.
- Select an attribute that is currently indexed that you want to drop the index from.
- Click the The attribute will be cataloged/decataloged icon. When the Confirm Dialog appears, click Confirm.
- The Indexed box indicates that the attribute is no longer indexed.
21.2.14 Creating a Content Rule by Using Oracle Directory Services Manager
To create a content rule:
21.2.15 Modifying a Content Rule by Using Oracle Directory Services Manager
To modify a content rule:
21.2.16 Viewing Matching Rules by Using Oracle Directory Services Manager
Note:
Matching rules cannot be modified.
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- Expand the Matching Rules list. Matching rules are shown in the list.
- You can search for a matching rule by entering a keyword in the search field, in the same way you search for object classes. See Searching for Object Classes by Using Oracle Directory Services Manager.
- Select a matching rule to see its details in the matching rule tab page on the right.
21.2.17 Viewing Syntaxes by Using Oracle Directory Services Manager
Note:
Syntaxes cannot be modified.
To view syntaxes by using Oracle Directory Services Manager:
- Invoke Oracle Directory Services Manager and connect to the Oracle Internet Directory server as described in Invoking Oracle Directory Services Manager.
- From the task selection bar, choose Schema.
- Expand the Syntaxes list. Syntax names are shown in the list.
- Select a syntax to see its details in the syntax tab page on the right.
21.3 Managing Directory Schema by Using the Command Line
Using command line utilities, you can view schema, add new object class, add new attributes to an auxilary object class and so on.
This section contains the following topics:
21.3.1 Viewing the Schema by Using ldapsearch
You can write the schema to a file by typing:
ldapsearch -h OID_host -p OID_port -q -L -D "cn=orcladmin" \ -b "cn=subschemasubentry" -s base "objectclass=*" > schema.ldif
21.3.2 Adding a New Object Class by Using Command-Line Tools
In this example, an LDIF input file, new_object_class.ldif, contains data similar to this:
dn: cn=subschemasubentry changetype: modify add: objectclasses objectclasses: ( 2.16.840.1.113894.9999.12345 NAME 'myobjclass' SUP top STRUCTURAL MUST ( cn $ sn ) MAY ( telephonenumber $ givenname $ myattr ) )
Be sure to leave the mandatory space between the opening and closing parentheses and the object identifier.
To load the file, enter this command:
ldapmodify -D "cn=orcladmin" -q -h myhost -p 3060 -f new_object_class.ldif
This example:
-
Adds the structural object class named
myobjclass -
Gives it an object identifier of
2.16.840.1.113894.9999.12345. -
Specifies
topas its superclass -
Specifies
cnandsnas mandatory attributes -
Allows
telephonenumber,givenname, andmyattras optional attributes
Note that all the attributes mentioned must exist before the execution of the command.
To create an abstract object class, follow the previous example, replacing the word STRUCTURAL with the word ABSTRACT.
21.3.3 Adding a New Attribute to an Auxiliary or User-Defined Object Class by Using Command-Line Tools
To add a new attribute to either an auxiliary object class or a user-defined structural object class, use ldapmodify. This example deletes the old object class definition and adds the new definition in a compound modify operation. The change is committed by the directory server in one transaction. Existing data is not affected. The input file should be as follows:
dn: cn=subschemasubentry changetype: modify delete: objectclasses objectclasses: old value - add: objectclasses objectclasses: new value
For example, to add the attribute changes to the existing object class country, the input file would be:
dn: cn=subschemasubentry changetype: modify delete: objectclasses objectclasses: ( 2.16.840.1.113894.9999.12345 NAME 'country' SUP top STRUCTURAL MUST c MAY ( searchGuide $ description ) ) - add: objectclasses objectclasses: ( 2.16.840.1.113894.9999.12345 NAME 'country' SUP top STRUCTURAL MUST c MAY ( searchGuide $ description $ changes ) )
To load the file, enter this command:
ldapmodify -D "cn=orcladmin" -q -h myhost -p 3060 -f new_attribute.ldif
21.3.4 Modifying Object Classes by Using Command-Line Tools
To add or modify schema components, use ldapmodify.
See Also:
The ldapmodify command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.
21.3.5 Adding and Modifying Attributes by Using ldapmodify
To add a new attribute to the schema by using ldapmodify, type a command similar to the following at the system prompt:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
The LDIF file contains data similar to this:
dn: cn=subschemasubentry
changetype: modify
add: attributetypes
attributetypes: ( 1.2.3.4.5 NAME 'myattr' SYNTAX
'1.3.6.1.4.1.1466.115.121.1.38' )To specify an attribute as single-valued, include in the attribute definition entry in the LDIF file the keyword SINGLE-VALUE with surrounding white space.
You can find a given syntax Object ID by using either Oracle Directory Services Manager or the ldapsearch command line tool.
See Also:
-
The
ldapmodifycommand-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management for a detailed explanation of ldapmodify and its options -
Viewing Syntaxes by Using ldapsearch for instructions on how to view syntaxes by using either Oracle Directory Services Manager or
ldapsearch
21.3.6 Deleting Attributes by Using ldapmodify
Note:
You can delete only user-defined attributes. Do not delete attributes from the base schema.
To delete an attribute by using ldapmodify, type a command similar to the following at the system prompt:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
The LDIF file contains data similar to this:
dn: cn=subschemasubentry
changetype: modify
delete: attributetypes
attributetypes: ( 1.2.3.4.5 NAME 'myattr' SYNTAX
'1.3.6.1.4.1.1466.115.121.1.38' )You can find a given syntax Object ID by using either Oracle Directory Services Manager or the ldapsearch command line tool.
See Also:
-
The
ldapmodifycommand-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management for a detailed explanation of ldapmodify and its options -
Viewing Syntaxes by Using ldapsearch or Viewing Syntaxes by Using Oracle Directory Services Manager for instructions on how to view syntaxes
21.3.7 Indexing an Attribute by Using ldapmodify
As of Oracle Internet Directory 11g Release 1 (11.1.1.6.0) a new autocatalog feature is enabled by default in fresh installs. You can also enable it if you have upgraded from a previous release. When this feature is enabled, Oracle Internet Directory automatically invokes the catalog command to index attributes when you search for them. If the autocatalog feature is not enabled, and you want to use previously uncataloged attributes in search filters, you must add them to the catalog entry, as in previous releases.
You can add an attribute to the catalog entry by using ldapmodify.
To add an attribute, import an LDIF file by using ldapmodify. For example, to index the attribute displayName, import the following LDIF file by using ldapmodify:
dn: cn=catalogs changetype: modify add: orclindexedattribute orclindexedattribute: displayName
Type a command similar to the following at the system prompt:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
To index the attribute, the ldapmodify command invokes the Catalog Management tool, catalog. For information about that tool, see Creating and Dropping Indexes from Existing Attributes by Using catalog.
21.3.8 Dropping an Index from an Attribute by Using ldapmodify
To drop an index from an attribute by using ldapmodify, specify delete in the LDIF file. For example:
dn: cn=catalogs changetype: modify delete: orclindexedattribute orclindexedattribute: displayName
See Also:
The ldapmodify command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.
21.3.9 Indexing an Attribute by Using the Catalog Management Tool
You can use the Catalog Management tool instead of ldapmodify to index an attribute and to drop an index from an attribute. See Creating and Dropping Indexes from Existing Attributes by Using catalog.
See Also:
The catalog command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.
Note:
Unless you are absolutely sure that the indexes were not created by the base schema that was installed with Oracle Internet Directory, be careful not to use the catalog delete=T option to remove indexes from attributes. Removing indexes from base schema attributes can adversely impact the operation of Oracle Internet Directory.
21.3.10 Adding a New Attribute With Attribute Aliases by Using the Command Line
You add, modify, or delete attribute aliases by creating an LDIF file, then using ldapmodify with the following syntax:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
Note:
DN is not an attribute. You cannot define dn in the schema. Therefore you cannot create an alias for dn.
The following LDIF file adds the attribute myattr with the attribute aliases myalias1 and myalias2:
dn: cn=subschemasubentry
changetype: modify
add: attributetypes
attributetypes: ( 1.2.3.4.5 NAME ( 'myattr' 'myalias1' 'myalias2' ) SYNTAX
'1.3.6.1.4.1.1466.115.121.1.38' )21.3.11 Adding or Modifying Attribute Aliases in Existing Attributes by Using the Command Line
The following LDIF file adds the attribute aliases surname and mysurName to the existing attribute sn:
dn: cn=subschemasubentry changetype: modify delete: attributeTypes attributeTypes: ( 2.5.4.4 NAME 'sn' SUP name ) - add: attributeTypes attributeTypes: ( 2.5.4.4 NAME ( 'sn' 'surname' 'mysurName' ) SUP name )
Type a command similar to the following at the system prompt:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
21.3.12 Deleting Attribute Aliases by Using the Command Line
Use the ldapmodify command to delete attribute aliases. The following LDIF file deletes the attribute alias mysurName but not the attribute alias surName from the attribute sn:
dn: cn=subschemasubentry changetype: modify delete: attributeTypes attributeTypes: ( 2.5.4.4 NAME ( 'sn' 'surname' 'mysurName' ) SUP name ) - add: attributeTypes attributeTypes: ( 2.5.4.4 NAME ( 'sn' 'surname' ) SUP name )
The following LDIF file deletes both attribute aliases, surname and mysurName, from the attribute sn:
dn: cn=subschemasubentry changetype: modify delete: attributeTypes attributeTypes: ( 2.5.4.4 NAME ( 'sn' 'surname' 'mysurName' ) SUP name ) - add: attributeTypes attributeTypes: ( 2.5.4.4 NAME 'sn' SUP name )
21.3.13 Using Attribute Aliases with LDAP Commands
After you define attribute aliases in the LDAP schema, users can substitute the aliases for attribute names in LDAP operations. The following examples show the commands to use and the results to expect:
Table 21-1 shows the aliases used in the examples and the attributes names they represent:
Table 21-1 Attribute Aliases Used in Examples
| Alias | Attribute Name |
|---|---|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
21.3.13.1 Using Attribute Aliases with ldapsearch
The LDAP server recognizes attribute aliases in the search filter string, in the base DN, and in the required attributes list in ldapsearch operations. The search result contains the actual attribute names, unless the user explicitly asks for an alias using the required attributes list. For example, suppose the user specifies the following search, using the aliases organizationalUnit, country, and organization in the base DN and the alias surname in the filter string:
ldapsearch -p 3060 -h myhost \ -b "organizationalUnit=dev,country=us,organization=myorg" \ -s sub "surname=brown"
The search returns a result similar to this:
uid=mbrown,ou=dev,c=us,o=myorg uid=mbrown sn=Brown cn=Mark Brown telephonenumber;office=444006 telephonenumber;mobile=555006 objectclass=organizationalPerson objectclass=top objectclass=person
Now suppose the user specifically asks for the aliases surname, commonname, and userid by including them in a required attributes list, like this:
ldapsearch -p 3060 -h myhost \ -b "organizationalUnit=dev,country=us,organization=myorg" \ -s sub "surname=brown" surname commonname userid phone
Because the user specifically included the aliases, the search returns a result similar to this:
uid=mbrown,ou=dev,c=us,o=myorg surname=Brown commonname=Mark Brown userid=mbrown phone;office=444006 phone;mobile=555006
21.3.13.2 Using Attribute Aliases with ldapadd
The LDAP server recognizes attribute aliases in place of attribute names during the add operation. When the LDAP server stores the entry, it replaces the alias with the actual attribute name.
The command-line format is:
ldapadd -h host -p port -D cn=orcladmin -q -f ldif_file_name
The user could provide an LDIF file like this:
dn: userid=mbrown,organizationalUnit=dev,country=us,organization=myorg objectclass: account objectclass: organizationalPerson userID: mbrown surname: Brown commonName: Mark Brown userpassword: password phone;office: 444006 phone;mobile: 555006
The entry is stored as if the file contained the attribute names instead of the aliases. On subsequent LDAP searches, however, the DN is returned as it was entered when added or modified:
dn: userid=mbrown,organizationalUnit=dev,country=us,organization=myorg
This is standard behavior for LDAP search results. The DN is always returned with the same format that was used when the entry was created.
21.3.13.3 Using Attribute Aliases with ldapmodify
The LDAP server recognizes attribute aliases in place of attribute names during the modify operation.
The command-line format is:
ldapmodify -D "cn=orcladmin" -q -h host -p port -f ldif_file_name
The user could provide an LDIF file like this:
dn: userid=mbrown,organizationalUnit=dev,country=us,organization=myorg changetype: modify replace: surname surname: davis
The entry is stored as if the file contained the attribute names instead of the aliases. On subsequent LDAP searches, however, the DN is returned as it was entered when added or modified:
dn: userid=mbrown,organizationalUnit=dev,country=us,organization=myorg
This is standard behavior for LDAP search results. The DN is always returned with the same format that was used when the entry was created.
21.3.13.4 Using Attribute Aliases with ldapdelete
The LDAP server recognizes attribute aliases in the DN provided for delete operations. For example, suppose the user provides a request like this, with the aliases userid, organizationalUnit, country, and organization in the search filter:
ldapdelelete -D "cn=orcladmin" -q -p 3060 \ -h myhost "userid=mbrown,organizationalUnit=dev,country=us,organization=myorg"
The server deletes the entry as if the user had typed:
ldapdelelete -D "cn=orcladmin" -q -p 3060 \ -h myhost "uid=mbrown,ou=dev,c=us,o=myorg"
21.3.13.5 Using Attribute Aliases with ldapmoddn
The LDAP server recognizes attribute aliases in the DN, the new RDN, and the new parent DN options. For example, suppose the user types the command line:
ldapmoddn -D "cn=orcladmin" -q \ -b "userid=mbrown,organizationalUnit=dev,country=us,organization=myorg"\ -R "userid=mdavis"
The LDAP server interpret the command line as if the user had typed
ldapmoddn -D "cn=orcladmin" -q -b "uid=mbrown,ou=dev,c=us,o=myorg" \ -R "uid=mdavis"
The entry is stored as if the file contained the attribute names instead of the aliases. On subsequent LDAP searches, however, the DN is returned as it was entered when added or modified:
dn: userid=mbrown,organizationalUnit=dev,country=us,organization=myorg
This is standard behavior for LDAP search results. The DN is always returned with the same format that was used when the entry was created.
21.3.14 Managing Content Rules by Using Command-Line Tools
The format of a content rule is:
DITContentRule ::= SEQUENCE {oids ALPHA-NUMERIC-OID, structuralObjectClass OBJECT-CLASS, LABEL CONTENT-LABEL OPTIONAL, auxiliaries SET (1..MAX) OF OBJECT-CLASS OPTIONAL, mandatory SET (1..MAX) OF ATTRIBUTE OPTIONAL, optional SET (1..MAX) OF ATTRIBUTE OPTIONAL, precluded SET (1..MAX) OF ATTRIBUTE OPTIONAL }
You can use ldapmodify with an LDIF file such as the following to add a content rule:
dn: cn=subschemasubentrychangetype: modify add: contentrules contentrules: ( 2.16.840.1.113894.9999.1.1 OBJECTCLASS 'exampleObjClassName' LABEL abc AUX exampleAuxObjClassName MUST businessCategory MAY ( description $ host ) )
The following section describes the Content Rule Parameters. Note that the attributes and object class names are case-sensitive.
-
oids
A unique object identifier (oids) for the content rule similar to the one for an object class or attribute definition. It must be a unique numeric value that begins with 2.16.840.1.113894 followed by .9999 or a site-specific prefix.
-
LABEL
The content label of the content rule as applied in the directory.
-
structuralObjectClass
The structural object class to which the content rule applies.
-
auxiliaries
The auxiliary object classes allowed for an entry to which the content rule applies.
-
mandatory
User attribute types contained in an entry to which the content rule applies. These are in addition to those mandatory attributes that the entry contains as a result of its association with its specified structural and auxiliary object classes.
-
optional
User attribute types that may be contained in an entry to which the content rule applies. These are in addition to those that the entry may contain as a result of its association with its specified structural and auxiliary object classes.
21.3.15 Viewing Matching Rules by Using ldapsearch
Note:
Matching rules cannot be modified.
To view matching rules, type:
ldapsearch -L -D "cn=orcladmin" -p port -q -b "cn=subschemasubentry" -s base "objectclass=*" matchingrules
See Also:
The ldapsearch command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.
21.3.16 Viewing Syntaxes by Using ldapsearch
Note:
Syntaxes cannot be modified.
To view syntaxes, type:
ldapsearch -L -D "cn=orcladmin" -p port -q -b "cn=subschemasubentry" -s base "objectclass=*" ldapsyntaxes
See Also:
The ldapsearch command-line tool reference in Oracle Fusion Middleware Reference for Oracle Identity Management.