18 Configuring Oracle Managed File Transfer in an Enterprise Deployment
The procedures explained in this chapter guide you through the process of adding Oracle Managed File Transfer to your enterprise deployment.
- About Oracle Managed File Transfer
Oracle Managed File Transfer (MFT) provides a standards-based file gateway. It features design, deployment, and monitoring of file transfers by using a web-based design-time console that includes transfer prioritization, file encryption, scheduling, and embedded FTP and sFTP servers. - Variables Used When Configuring Managed File Transfer
The procedures for installing and configuring Managed File Transfer reference use a series of variables that you can replace with the actual values used in your environment. - Synchronizing the System Clocks
Verify that the system clocks on each host computer are synchronized. - Prerequisites for Creating the Managed File Transfer Domain
Before you create the Managed File Transfer domain, ensure that your existing deployment meets the following prerequisites. - Installing the Software for an Enterprise Deployment
The procedure to install the software for an enterprise deployment is explained in this section. - Creating the Managed File Transfer Database Schemas
Before you can configure an Managed File Transfer domain, you must install the required schemas in a certified database for use with this release of Oracle Fusion Middleware. - Creating the Managed File Transfer Domain for an Enterprise Deployment
You create a separate Managed File Transfer domain by using the Fusion Middleware Configuration Wizard. - Download and Configure Weblogic Remote Console
This section describes how to download and configure the WebLogic Remote Console. - Configuring SSL Certificates for the Domain
This section describes how to configure SSL certificates for the domain. - Configuring a Per Host Node Manager for an Enterprise Deployment
For specific enterprise deployments, Oracle recommends that you configure a per-host Node Manager, as opposed to the default per-domain Node Manager. - Configuring the Domain Directories and Starting the Servers on MFTHOST1
After the domain is created and the node manager is configured, you can then configure the additional domain directories and start the Administration Server and the Managed Servers on MFTHOST1. - Configuring Web Services Manager
This section describes how to configure Web Services Manager. - Propagating the Domain and Starting the Servers on MFTHOST2
After you start and validate the Administration Server and WLS_MFT1 Managed Server on MFTHOST1, you can then perform the following tasks on MFTHOST2. - Modifying the Upload and Stage Directories to an Absolute Path
After you configure the domain and unpack it to the Managed Server domain directories on all the hosts, verify and update the upload and stage directories for Managed Servers in the new clusters. - Configuring the Web Tier for the Extended Domain
Configure the web server instances on the web tier so that the instances route to the proper clusters in the SOA domain. - Validating the Managed File Transfer URLs Through the Load Balancer
This section describes how to validate the configuration of Oracle HTTP Server and to verify that the hardware load balancer routes requests through the OHS instances to the application tier. - Configuring and Enabling the SSH-FTP Service for Managed File Transfer
The Oracle Managed File Transfer enterprise deployment topology is based on the Secure File Transfer Protocol (SFTP) for file transfer. SFTP is a separate protocol, packaged with SSH and designed to work similar to FTP, but over a secure connection. - Creating a New LDAP Authenticator and Provisioning Users for Managed File Transfer
When you configure an Oracle Fusion Middleware domain, the domain is configured by default to use the WebLogic Server authentication provider (DefaultAuthenticator). However, for an enterprise deployment, Oracle recommends that you use a dedicated, centralized LDAP-compliant authentication provider. - Replacing Connect Strings with the Appropriate TNS Alias
Oracle recommends using TNS Alias in the connection strings used by FMW components instead of repeating long JDBC strings across multiple connections pools. - Backing Up the Configuration
It is an Oracle best practices recommendation to create a backup after you successfully extended a domain or at another logical point. Create a backup after you verify that the installation so far is successful. This is a quick backup for the express purpose of immediate restoration in case of problems in later steps.
Parent topic: Configuring the Enterprise Deployment
About Oracle Managed File Transfer
Oracle Managed File Transfer (MFT) provides a standards-based file gateway. It features design, deployment, and monitoring of file transfers by using a web-based design-time console that includes transfer prioritization, file encryption, scheduling, and embedded FTP and sFTP servers.
For more information about Oracle MFT, see Understanding Oracle Managed File Transfer in Using Oracle Managed File Transfer.
About Managed File Transfer in an Enterprise Deployment
Managed File Transfer runs in its own domain, separate from other components, such as Oracle SOA Suite, Oracle Service Bus, and Business Activity Monitoring. Typically, you create the domain and configure the Managed Servers for Managed File Transfer in a single configuration wizard session.
Managed File Transfer uses Oracle Web Services Manager (OWSM), and runs the OWSM services on the same servers as the Managed File Transfer applications.
Figure 18-1 illustrates the Managed File Transfer deployment topology.
For a description of the standard elements shown in the diagram, see Understanding the Typical Enterprise Deployment Topology Diagram.
For a description of the elements shown in the diagram, see Understanding the Primary Oracle SOA Suite Topology Diagrams.
Figure 18-1 Managed File Transfer Topology
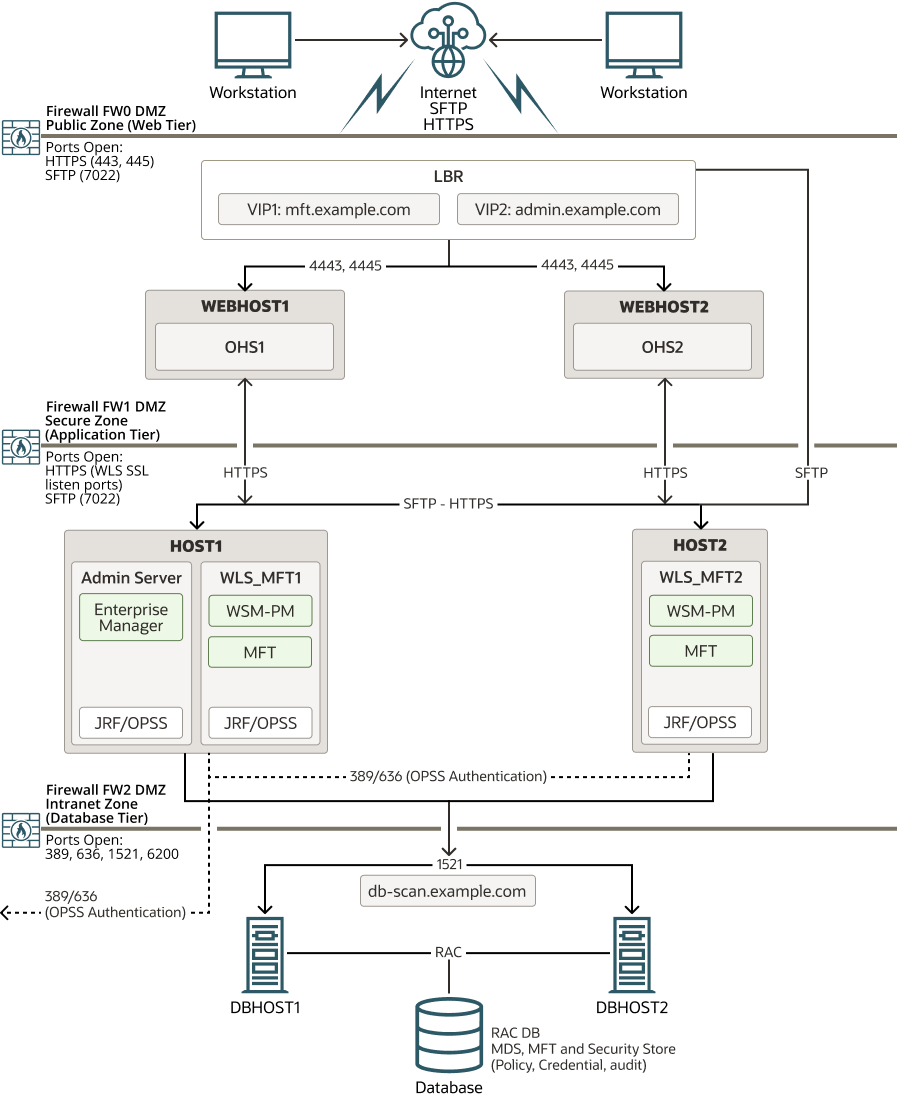
Description of "Figure 18-1 Managed File Transfer Topology"
The Managed File Transfer domain can be configured on the same host as other FMW components. For this reason, Oracle recommends that you use a per host Node Manager configuration. In this configuration, a single Node Manager can control different domains on the same machine. See Configuring a Per Host Node Manager for an Enterprise Deployment.
Parent topic: About Oracle Managed File Transfer
Characteristics of the Managed File Transfer Domain
The following table lists some of the key characteristics of the domain that you are about to create. By reviewing and understanding these characteristics, you can better understand the purpose and context of the procedures used to configure the domain.
Many of these characteristics are described in more detail in Understanding a Typical Enterprise Deployment.
| Characteristic of the Domain | More Information |
|---|---|
|
Uses a separate virtual IP (VIP) address for the Administration Server. |
Configuration of the Administration Server and Managed Servers Domain Directories |
|
Uses separate domain directories for the Administration Server and the Managed Servers in the domain. |
Configuration of the Administration Server and Managed Servers Domain Directories |
|
Uses Oracle Web Services Manager, which is deployed to the same servers as Managed File Transfer |
|
|
Uses the Load Balancer for routing SFTP requests from clients to MFT servers. |
|
|
Uses a single Configuration Wizard session to configure the Infrastructure and Managed File Transfer software on the Managed File Transfer Managed Servers. |
Creating the Managed File Transfer Domain for an Enterprise Deployment |
|
Uses a per host Node Manager configuration. |
About the Node Manager Configuration in a Typical Enterprise Deployment |
|
Requires a separately installed LDAP-based authentication provider. |
Understanding OPSS and Requests to the Authentication and Authorization Stores |
Parent topic: About Oracle Managed File Transfer
Variables Used When Configuring Managed File Transfer
The procedures for installing and configuring Managed File Transfer reference use a series of variables that you can replace with the actual values used in your environment.
The following directory location variables are used in these procedures:
-
ORACLE_HOME
-
JAVA_HOME
-
NM_HOME
-
ASERVER_HOME
-
MSERVER_HOME
-
WEB_ORACLE_HOME
-
WEB_DOMAIN_HOME
See File System and Directory Variables Used in This Guide.
In addition, you reference the following virtual IP (VIP) address that are defined in Reserving the Required IP Addresses for an Enterprise Deployment:
-
ADMINVHN
Actions in this chapter are performed on the following host computers:
-
APPHOST1
-
APPHOST2
-
WEBHOST1
-
WEBHOST2
Note:
Note that for this chapter, APPHOST1 and APPHOST2 provide a more generic variable for the application tier hosts. This is because, depending upon the domain you are creating, the host name variable varies.
Synchronizing the System Clocks
Verify that the system clocks on each host computer are synchronized.
Oracle recommends the use of the Network Time Protocol (NTP). See Configuring a Host to Use an NTP (time) Server.
To verify the time synchronization, query the NTP service by running the chronyc -n
tracking command on each host.
Sample output:
$chronyc -n tracking
Reference ID : A9FEA9FE (169.254.169.254)
Stratum : 3
Ref time (UTC) : Tue Jan 14 15:28:01 2025
System time : 0.000043127 seconds fast of NTP time
Last offset : +0.000034640 seconds
...Prerequisites for Creating the Managed File Transfer Domain
Before you create the Managed File Transfer domain, ensure that your existing deployment meets the following prerequisites.
-
You must have a supported database to install the schemas used by the MFT domain.
-
Verify that you have installed a supported JDK.
-
You must have an existing Oracle home where you have installed the Oracle Fusion Middleware Infrastructure software binaries. This must be a dedicated Oracle home for the Managed File Transfer domain. The Oracle home is typically on shared storage and is available from MFTHOST1 and MFTHOST2. See Shared Storage Recommendations When Installing and Configuring an Enterprise Deployment.
Note that you should not configure the Infrastructure domain, only install the Oracle Fusion Middleware Infrastructure software.
To create the Infrastructure Oracle home, see Installing the Oracle Fusion Middleware Infrastructure on SOAHOST1.
-
Back up the installation. If you have not yet backed up the existing Fusion Middleware Home, Oracle recommends backing it up now.
To back up the existing Fusion Middleware Home and domain, see Performing Backups and Recoveries in the SOA Enterprise Deployments.
-
If you have not done so already, verify that the system clocks on each host computer are synchronized. You can do this by running the date command as simultaneously as possible on the hosts in each cluster.
Alternatively, there are third-party and open-source utilities that you can use for this purpose.
Installing the Software for an Enterprise Deployment
The procedure to install the software for an enterprise deployment is explained in this section.
Starting the Managed File Transfer Installer on MFTHOST1
To start the installation program:
When the installation program appears, you are ready to begin the installation.
Parent topic: Installing the Software for an Enterprise Deployment
Navigating the Installation Screens When Installing Managed File Transfer
The installation program displays a series of screens, in the order listed in the following table.
If you need additional help with any of the installation screens, click the screen name.
| Screen | Description |
|---|---|
|
This screen introduces you to the product installer. |
|
|
Use this screen to automatically search My Oracle Support for available patches or automatically search a local directory for patches that you have already downloaded for your organization. |
|
|
Use this screen to specify the location of your Oracle home directory. This Oracle home should already contain Oracle Fusion Middleware Infrastructure. For more information about Oracle Fusion Middleware directory structure, see Selecting Directories for Installation and Configuration in Planning an Installation of Oracle Fusion Middleware. |
|
|
This screen verifies that your system meets the minimum necessary requirements. If there are any warning or error messages, you can refer to one of the documents in the Roadmap for Verifying Your System Environment section in Installing and Configuring the Oracle Fusion Middleware Infrastructure. |
|
|
Use this screen to verify the installation options that you selected. Click Install to begin the installation. |
|
|
This screen allows you to see the progress of the installation. Click Next when the progress bar reaches 100% complete. |
|
|
Review the information on this screen, then click Finish to dismiss the installer. |
Parent topic: Installing the Software for an Enterprise Deployment
Installing the Software on Other Host Computers
If you have configured a separate shared storage volume or partition for SOAHOST2, then you must also install the software on SOAHOST2. For more information, see Shared Storage Recommendations When Installing and Configuring an Enterprise Deployment.
Note that the location where you install the Oracle home (which contains the software binaries) varies, depending upon the host. To identify the proper location for your Oracle home directories, refer to the guidelines in File System and Directory Variables Used in This Guide.
Parent topic: Installing the Software for an Enterprise Deployment
Verifying the Installation
After you complete the installation, you can verify it by successfully completing the following tasks.
Parent topic: Installing the Software for an Enterprise Deployment
Reviewing the Installation Log Files
Review the contents of the installation log files to make sure that no problems were encountered. For a description of the log files and where to find them, see Understanding Installation Log Files in Installing Software with the Oracle Universal Installer.
Parent topic: Verifying the Installation
Checking the Directory Structure for Managed File Transfer
The contents of your installation vary based on the options that you select during installation.
Use the ls --format=single-colum command to check the list of directory and sub-directories in the /u01/oracle/products/fmw directory:
ls --format=single-colum $ORACLE_HOME bin coherence em install inventory jlib lib mft OPatch opmn oracle_common oraInst.loc osb oui soa wlserver
For more information about the directory structure you should see after installation, see What are the Key Oracle Fusion Middleware Directories? in Understanding Oracle Fusion Middleware.
Parent topic: Verifying the Installation
Creating the Managed File Transfer Database Schemas
Before you can configure an Managed File Transfer domain, you must install the required schemas in a certified database for use with this release of Oracle Fusion Middleware.
Starting the Repository Creation Utility (RCU)
To start the Repository Creation Utility (RCU):
Parent topic: Creating the Managed File Transfer Database Schemas
Navigating the RCU Screens to Create the Managed File Transfer Schemas
Schema creation involves the following tasks:
-
Task 6, "Verifying the Tablespaces for the Required Schemas"
-
Task 8, "Reviewing Completion Summary and Completing RCU Execution"
- Task 1 Introducing RCU
-
Click Next.
- Task 2 Selecting a Method of Schema Creation
-
If you have the necessary permission and privileges to perform DBA activities on your database, select System Load and Product Load. This procedure assumes that you have the necessary privileges.
If you do not have the necessary permission or privileges to perform DBA activities in the database, you must select Prepare Scripts for System Load on this screen. This option generates a SQL script, which can be provided to your database administrator to create the required schema. See Understanding System Load and Product Load in Creating Schemas with the Repository Creation Utility.
Click Next.
- Task 3 Providing Database Connection Details
-
Provide the database connection details for RCU to connect to your database.
-
As Database Type, select Oracle Database enabled for edition-based redefinition.
Note:
Oracle Database enabled for edition-based redefinition (EBR) is recommended to support Zero Down Time upgrades. For more information, see https://www.oracle.com/database/technologies/high-availability/ebr.html. -
In the Host Name field, enter the SCAN address of the Oracle RAC Database.
-
Enter the Port number of the RAC database scan listener, for example 1521.
-
Enter the RAC Service Name of the database.
-
Enter the User Name of a user that has permissions to create schemas and schema objects, for example SYS.
-
Enter the Password of the user name that you provided in step 4.
-
If you have selected the SYS user, ensure that you set the role to SYSDBA.
-
Click Next to proceed, then click OK on the dialog window confirming that the connection to the database was successful.
-
- Task 4 Specifying a Custom Prefix and Selecting Schemas
-
On this page, do the following:
-
Choose Create new prefix, and then enter the prefix that you want to use for the Managed File Transfer schemas. A unique schema prefix is required because you are creating a new domain for Managed File Transfer.
-
From the list of schemas, select the Managed File Transfer schema.
The following dependent schemas are selected automatically:
-
Common Infrastructure Services
-
Oracle Enterprise Scheduler
-
Oracle Platform Security Services
-
User Messaging Service
-
Audit Services
-
Audit Services Append
-
Audit Services Viewer
-
Metadata Services
-
Weblogic Services
-
The custom prefix is used to logically group these schemas together for use in this domain only; you must create a unique set of schemas for each domain as schema sharing across domains is not supported.
Tip:
For more information about custom prefixes, see Understanding Custom Prefixes in Creating Schemas with the Repository Creation Utility.
For more information about how to organize your schemas in a multi-domain environment, see Planning Your Schema Creation in Creating Schemas with the Repository Creation Utility.
Click Next to proceed, then click OK on the dialog window confirming that prerequisite checking for schema creation was successful.
-
- Task 5 Specifying Schema Passwords
-
Specify how you want to set the schema passwords on your database, then specify and confirm your passwords. Ensure that the complexity of the passwords meet the database security requirements before you continue. RCU proceeds at this point even if you do not meet the password polices. Hence, perform this check outside RCU itself.
Tip:
You must make a note of the passwords you set on this screen; you need them later on during the domain creation process.
Click Next.
- Task 6 Verifying the Tablespaces for the Required Schemas
-
On the Map Tablespaces screen, review the information, and then click Next to accept the default values.
Click OK in the confirmation dialog box.
- Task 7 Creating Schemas
-
Review the summary of the schemas to be loaded, and click Create to complete schema creation.
Note:
If failures occurred, review the listed log files to identify the root cause, resolve the defects, and then use RCU to drop and recreate the schemas before you continue.
- Task 8 Reviewing Completion Summary and Completing RCU Execution
-
When you reach the Completion Summary screen, verify that all schema creations have been completed successfully, and then click Close to dismiss RCU.
Parent topic: Creating the Managed File Transfer Database Schemas
Verifying Schema Access
Verify schema access by connecting to the database as the new schema users created by the RCU. Use SQL*Plus or another utility to connect, and provide the appropriate schema names and passwords entered in the RCU.
For example:
Note:
If the database is a plugable database (PDB), the apropriate tns alias that points to the PDB must be used in the sqlplus command.sqlplus FMW1412_MFT/<mft_schema_password>
SQL*Plus: Release 23.0.0.0.0 - Production on Tue Jun 11 10:54:41 2024
Version 23.4.0.24.05
Copyright (c) 1982, 2024, Oracle. All rights reserved.
Last Successful login time: Tue Jun 11 2024 10:52:21 +00:00
Connected to:
Oracle Database 23ai EE Extreme Perf Release 23.0.0.0.0 - Production
Version 23.4.0.24.05
SQL>Parent topic: Creating the Managed File Transfer Database Schemas
Creating the Managed File Transfer Domain for an Enterprise Deployment
Starting the Configuration Wizard
Start the Configuration Wizard as the first step to create the MFT enterprise deployment domain.
To start the Configuration Wizard, navigate to the following directory and start the WebLogic Server Configuration Wizard.:
cd $ORACLE_HOME/oracle_common/common/bin
./config.shNavigating the Configuration Wizard Screens to Configure the MFT Domain
Follow the instructions in this section to create and configure the domain for MFT, with static clusters.
Domain creation and configuration includes the following tasks.
-
Task 1, "Selecting the Domain Type and Domain Home Location"
-
Task 9, "Providing the GridLink Oracle RAC Database Connection Details"
-
Task 13, "Configuring the Administration Server Listen Address"
-
Task 23, "Reviewing Your Configuration Specifications and Configuring the Domain"
-
Task 24, "Writing Down Your Domain Home and Administration Server URL"
- Task 1 Selecting the Domain Type and Domain Home Location
-
You must select a Domain home directory location, optimally outside the Oracle home directory.
Oracle recommends that you locate your Domain home in accordance with the directory structure in What Are the Key Oracle Fusion Middleware Directories? in Understanding Oracle Fusion Middleware, where the Domain home is located outside the Oracle home directory. This directory structure helps avoid issues when you need to upgrade or reinstall software.
To specify the Domain type and Domain home directory:
-
On the Configuration Type screen, select Create a new domain.
-
In the Domain Location field, specify your Domain home directory.
For more information about this screen, see Configuration Type in Creating WebLogic Domains Using the Configuration Wizard
-
- Task 2 Selecting the Configuration Templates
-
On the Templates screen, make sure Create Domain Using Product Templates is selected, then select the following templates:
-
Oracle Managed File Transfer [mft]
Selecting this template automatically selects the following dependencies:
-
Oracle Enterprise Manager
-
Oracle B2B Client
-
Oracle JRF
-
Oracle WSM Policy Manager
-
WebLogic Coherence Cluster Extension
-
For more information about the options on this screen, see Templates in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 3 Configuring High Availability Options
-
This screen appears for the first time when you create a cluster that uses Automatic Service Migration or JDBC stores or both. After you select HA Options for a cluster, all subsequent clusters that are added to the domain by using the Configuration Wizard, automatically apply HA options (that is, the Configuration Wizard creates JDBC stores and configures ASM for them).
On the High Availability Options screen:
-
Select Enable Automatic Service Migration with Database Basis.
-
Set JTA Transaction Log Persistence to JDBC TLog Store.
-
Set JMS Server Persistence to JMS JDBC Store.
Note:
Oracle recommends that you use JDBC stores, which leverage the consistency, data protection, and high availability features of an Oracle database and makes resources available for all the servers in the cluster. So, the Configuration Wizard steps assume that the JDBC persistent stores are used along with Automatic Service Migration.
When you choose JDBC persistent stores, additional unused File Stores are automatically created but are not targeted to your clusters. Ignore these File Stores.
If, for any reason, you want to use Files Stores, you can retain the default values for TLOGs and JMS persistent store options in this screen and configure them in a shared location later. See Task 12, "Selecting Advanced Configuration". Shared location is required to resume JMS and JTA in a failover scenario.
You can also configure TLOGs and JMS persistent stores manually in a post step. For information about the differences between JDBC and Files Stores, and for specific instructions to configure them manually, see Using Persistent Stores for TLOGs and JMS in an Enterprise Deployment.
Click Next.
-
- Task 4 Selecting the Application Home Location
-
On the Application Location screen, specify the value of the APPLICATION_HOME variable, as defined in File System and Directory Variables Used in This Guide.
For more information about the options on this screen, see Application Location in Creating WebLogic Domains Using the Configuration Wizard.
- Task 5 Configuring the Administrator Account
-
On the Administrator Account screen, specify the user name and password for the default WebLogic Administrator account for the domain.
Make a note of the user name and password specified on this screen; you need these credentials later to boot and connect to the domain's Administration Server.
- Task 6 Specifying the Domain Mode and JDK
-
On the Domain Mode and JDK screen:
-
Select Production in the Domain Mode field.
-
In the Enable or Disable Default Ports for You Domain field, use the default values provided for Production Mode:
-
Ensure that Enable Listen Ports (non-SSL Ports) is NOT checked.
-
Ensure that Enable SSL Listen Ports is checked.
-
Ensure that Enable Administration Port (SSL Port) is checked.
Tip:
More information about the options on this screen, including the differences between development mode and production mode, can be found in Domain Mode and JDK in Creating WebLogic Domains Using the Configuration Wizard.
-
-
Select Oracle Hotspot JDK in the JDK field.
Note:
Ensure that it points to the folder where you have installed the JDK. See Installing the JDK Software.
-
- Task 7 Specifying the Database Configuration Type
-
On the Database Configuration Type screen:
-
Select RCU Data to activate the fields on this screen.
The RCU Data option instructs the Configuration Wizard to connect to the database and Service Table (STB) schema to automatically retrieve schema information for the schemas needed to configure the domain.
-
Verify that the Vendor is Oracle and the Driver is *Oracle's Driver (Thin) for Service Connections; Versions: Any.
-
Verify that Connection Parameters is selected.
Note:
If you select Manual Configuration on this screen, you must manually fill in the parameters for your schema on the JDBC Component Schema screen.
After you select RCU Data, fill in the fields as shown in the following table:
Field Description DBMS/Service
Enter the service name for the Oracle RAC database where you install the product schemas. For example:
soaedg.example.com
Be sure this is the common service name that is used to identify all the instances in the Oracle RAC database; do not use the host-specific service name.
Host Name
Enter the Single Client Access Name (SCAN) Address for the Oracle RAC database, which you entered in the Enterprise Deployment Workbook.
Port
Enter the port number on which the database listens. For example,
1521.Schema Owner
Schema Password
Enter the user name and password to connect to the database's Service Table schema.
This is the schema user name and password that was specified for the Service Table component on the Schema Passwords screen in RCU. See Creating the Database Schemas.
The default user name is
prefix_STB, whereprefixis the custom prefix that you have defined in RCU.Click Get RCU Configuration when you finished specifying the database connection information. The following output in the Connection Result Log indicates that the operating succeeded:
Connecting to the database server...OK Retrieving schema data from database server...OK Binding local schema components with retrieved data...OK Successfully Done.
Click Next if the connection to the database is successful.
For more information about the RCU Data option, see Understanding the Service Table Schema in Creating Schemas with the Repository Creation Utility.
For more information about the other options on this screen, see Datasource Defaults in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 8 Specifying JDBC Component Schema Information
-
Verify that the values on the JDBC Component Schema screen are correct for all schemas.
The schema table should be populated, because you selected Get RCU Data on the previous screen. As a result, the Configuration Wizard locates the database connection values for all the schemas required for this domain.
At this point, the values are configured to connect to a single-instance database. However, for an enterprise deployment, you should use a highly available Real Application Clusters (RAC) database, as described in Preparing the Database for an Enterprise Deployment.
In addition, Oracle recommends that you use an Active GridLink datasource for each of the component schemas. For more information about the advantages of using GridLink data sources to connect to a RAC database, see Database Considerations in the High Availability Guide.
To convert the data sources to GridLink:
-
Select all the schemas by selecting the checkbox in the first header row of the schema table.
-
Click Convert to GridLink and click Next.
-
- Task 9 Providing the GridLink Oracle RAC Database Connection Details
-
On the GridLink Oracle RAC Component Schema screen, provide the information that is required to connect to the RAC database and component schemas, as shown in following table.
Element Description and Recommended Value Service Name
Verify that the service name for the Oracle RAC database is the appropriate. For example, soaedg.example.com.
SCAN, Host Name, and Port
Select the SCAN check box.
In the Host Name field, enter the Single Client Access Name (SCAN) Address for the Oracle RAC database.
In the Port field, enter the SCAN listening port for the database (for example,
1521).ONS Host and Port
These values are not required when you are using an Oracle 12c database or higher versions because the ONS list is automatically provided from the database to the driver.
Enable Fan
Verify that the Enable Fan check box is selected, so that the database can receive and process FAN events.
For more information about specifying the information on this screen, as well as information about how to identify the correct SCAN address, see Configuring Active GridLink Data Sources with Oracle RAC in the High Availability Guide.
You can also click Help to display a brief description of each field on the screen.
- Task 10 Testing the JDBC Connections
-
A green check mark in the Status column indicates a successful test. If you encounter any issues, see the error message in the Connection Result Log section of the screen, fix the problem, then try to test the connection again.
By default, the schema password for each schema component is the password you specified while creating your schemas. If you want different passwords for different schema components, manually edit them in the previous screen (JDBC Component Schema) by entering the password you want in the Schema Password column, against each row. After you specify the passwords, select the check box that correspond to the schemas that you changed the password in and test the connection again.
For more information about the other options on this screen, see Test Component Schema in Creating WebLogic Domains Using the Configuration Wizard.
- Task 11 Specifying the Keystore
-
Use the Keystore screen in the Configuration Wizard to specify details about the keystore to be used in the domain.
For a typical enterprise deployment, you can leave the default values. See Keystore in Creating WebLogic Domains Using the Configuration Wizard
- Task 12 Selecting Advanced Configuration
-
To complete domain configuration for the topology, select the following options on the Advanced Configuration screen:
-
Administration Server
This is required to properly configure the listen address of the Administration Server.
-
Node Manager
This is required to configure Node Manager.
-
Topology
This is required to add, delete, or modify the Settings for Server Templates, Managed Servers, Clusters, Virtual Targets, and Coherence.
Note:
-
If any of the above options are not available on the screen, then return to the Templates screen and ensure that you have selected the required templates for this topology.
-
JDBC stores are recommended and selected in Task 3, "Configuring High Availability Options" so there is no need to configure File Stores.
-
- Task 13 Configuring the Administration Server Listen Address
-
On the Administration Server screen:
-
In the Server Name field, retain the default value "AdminServer".
-
In the Listen Address field, enter the virtual host name that corresponds to the VIP of the ADMINVHN that you procured in Procuring Resources for an Enterprise Deployment and enabled in Preparing the Host Computers for an Enterprise Deployment.
For more information about the purpose of using the ADMINVHN virtual host, see Reserving the Required IP Addresses for an Enterprise Deployment.
-
In the Configure Administration Server Ports section, perform the following steps:
-
Leave the Enable Listen Port field unchecked. The Listen Port value will be disabled in grey.
-
Ensure the Enable SSL Listen port field is checked.
-
Leave the default value as 7002 in the SSL Listen Port field.
-
Leave the default value as 9002 in the Administration Port.
-
-
Leave the default value as Unspecified in the Server Group.
-
- Task 14 Configuring Node Manager (Per Host)
-
Select Manual Node Manager Setup as the Node Manager type.
WARNING:
You can ignore the warning in the bottom pane. This guide provides the required steps for the Manual Node Manager configuration.Tip:
For more information about the options on this screen, see Node Manager in Creating WebLogic Domains Using the Configuration Wizard.
For more information about per domain and per host Node Manager implementations, see About the Node Manager Configuration in a Typical Enterprise Deployment.
For information about Node Manager configurations, see Configuring Node Manager on Multiple Machines in Administering Node Manager for Oracle WebLogic Server.
- Task 15 Configuring Managed Servers
-
Use the Managed Servers screen to create the Managed Servers that are required in the Managed File Transfer domain.
-
Change the default server name to
WLS_MFT1in the Server name column. -
Click Add and repeat this process to create a second Managed Server named
WLS_MFT2. -
Use the information in Table 18-1 to fill in the rest of the columns for each MFT Managed Server.
The Managed Server names suggested in this procedure (WLS_MFT1 and WLS_MFT2) are referenced throughout this document; if you choose different names then be sure to replace them as needed,
For more information about the options on this screen, see Managed Servers in Creating WebLogic Domains Using the Configuration Wizard.
Table 18-1 MFT Managed Server
Server Name Listen Address Enable Listen Port Listen Port Enable SSL Port SSL Listen Port Administration Port Server Groups WLS_MFT1
MFTHOST1
Unchecked
Disabled
Checked
7010
9014
MFT-MGD-SVRS
WLS_MFT2
MFTHOST2
Unchecked
Disabled
Checked
7010
9014
MFT-MGD-SVRS
The selected server group ensures that the Managed File Transfer and Oracle Web Services Manager (OWSM) software is targeted to the Managed Server.
There is another server group called MFT-MGD-SVRS-ONLY that targets only MFT but not Oracle Web Services Manager (OWSM) to the server. This is typically used if you want to have Oracle Web Services Manager (OWSM) in a different server rather than with the MFT server.
The server groups target Fusion Middleware applications and services to one or more servers by mapping defined groups of application services to each defined server group. Any application services that are mapped to a given server group are automatically targeted to all servers that are assigned to that group. See Application Service Groups, Server Groups, and Application Service Mappings in Domain Template Reference.
-
- Task 16 Configuring a Cluster
-
Use the Clusters screen to create a new cluster:
-
Click the Add button.
-
Specify
MFT_Clusterin the Cluster Name field. -
Leave the Cluster Address field blank.
-
Specify
mft.example.comin the Frontend Host field. - Specify
0as the Frontend HTTP port and443as the Frontend HTTPS port.
For more information about the options on this screen, see Clusters in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 17 Assigning Server Templates
-
Click Next.
- Task 18 Configuring Dynamic Servers
-
Verify that all dynamic server options are disabled for clusters that are to remain as static clusters.
-
Confirm that the Calculated Machine Names and Calculated Listen Port checkboxes on this screen are unchecked.
-
Confirm that the Server Template and Dynamic Server Groups selections are Unspecified.
-
Click Next.
-
- Task 19 Assigning Managed Servers to the Cluster
-
Use the Assign Servers to Clusters screen to assign Managed Servers to the new cluster.
-
In the Clusters pane, select the cluster to which you want to assign the servers; in this case,
MFT_Cluster. -
In the Servers pane, assign
WLS_MFT1toMFT_Clusterby doing one of the following:-
Click once on
WLS_MFT1to select it, then click on the right arrow to move it beneath the selected cluster (MFT_Cluster)) in the Clusters pane.or
-
Double-click on
WLS_MFT1to move it beneath the selected cluster (MFT_Cluster) in the clusters pane.
-
-
Repeat these steps to assign the WLS_MFT2 Managed Server to MFT_Cluster.
For more information about the options on this screen, see Assign Servers to Clusters in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 20 Configuring Coherence Clusters
-
Use the Coherence Clusters screen to configure the Coherence cluster that is automatically added to the domain.
In the Cluster Listen Port, enter
9991.For Coherence licensing information, Oracle Coherence Products in Oracle Fusion Middleware Licensing Information User Manual.
- Task 21 Creating Machines
-
Use the Machines screen to create five new machines in the domain. A machine is required in order for the Node Manager to be able to start and stop the servers.
-
Select the Unix Machine tab.
-
Click the Add button to create five new UNIX machines.
Use the values in Table 18-2 to define the Name and Node Manager Listen Address of each machine.
-
Verify the port in the Node Manager Listen Port field.
The port number
5556, shown in this example, may be referenced by other examples in the documentation. Replace this port number with your own port number as needed.Note:
If you are installing on a host where additional domains were already configured, and you have already configured a per host Node Manager, then the address and port configured in this screen must be for the existing per host Node Manager.
Table 18-2 Values to Use When Creating Unix Machines
Name Node Manager Listen Address Node Manager Type Node Manager Listen Port MFTHOST1
The value of the MFTHOST1 host name variable or MFTHOST1 alias. For example,
MFTHOST1.example.com.SSL
5556
MFTHOST2
The value of the MFTHOST2 host name variable or MFTHOST2 alias. For example,
MFTHOST2.example.com.SSL
5556
ADMINHOST
Enter the value of the ADMINVHN variable.
SSL
5556
For more information about the options on this screen, see Machines in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 22 Assigning Servers to Machines
-
Use the Assign Servers to Machines screen to assign the Administration Server and the two Managed Servers to the appropriate machine.
The Assign Servers to Machines screen is similar to the Assign Managed Servers to Clusters screen. Select the target machine in the Machines column, select the Managed Server in the left column, and click the right arrow to assign the server to the appropriate machine.
Assign the servers as follows:
-
Assign the AdminServer to the ADMINHOST machine.
-
Assign the WLS_MFT1 Managed Server to the MFTHOST1 machine.
-
Assign the WLS_MFT2 Managed Server to the MFTHOST2 machine.
For more information about the options on this screen, see Assign Servers to Machines in Creating WebLogic Domains Using the Configuration Wizard.
-
- Task 23 Reviewing Your Configuration Specifications and Configuring the Domain
-
The Configuration Summary screen contains detailed configuration information for the domain that you are about to create. Review the details of each item on the screen and verify that the information is correct.
If you need to make any changes, you can go back to any previous screen either by using the Back button or by selecting the screen in the navigation pane.
Domain creation does not begin until you click Create.
In the Configuration Progress screen, click Next when it finishes.
For more information about the options on this screen, see Configuration Summary in Creating WebLogic Domains Using the Configuration Wizard.
- Task 24 Writing Down Your Domain Home and Administration Server URL
-
The Configuration Success screen shows the following items about the domain you just configured:
-
Domain Location
-
Administration Server URL
You must make a note of both items as you need them later; the domain location is needed to access the scripts used to start the Administration Server.
Click Finish to dismiss the Configuration Wizard.
-
Download and Configure Weblogic Remote Console
This section describes how to download and configure the WebLogic Remote Console.
Note:
For the initial configuration steps required in this EDG, you will need access to the AdminServer listen address and administration port. Later on you will configure access from a frontend load balancer.Perform the following steps to download and configure the WebLogic Remote Console:
Configuring SSL Certificates for the Domain
This section describes how to configure SSL certificates for the domain.
Creating Certificates and Certificate Stores for the WebLogic Domain
The Enterprise Deployment Guide provides steps to configure a domain that uses SSL listen addresses for all Weblogic Managed Servers, Weblogic Administration Server and Node Managers in the application tier. To achieve this the required certificates for all servers, machines and NM listen addresses must be created and pointed to from the domain and Node Manager configuration.
In Oracle FMW 14.1.2.0, Oracle WebLogic allows the usage of a per-domain Certificate Authority (CA). In this model, the CertGen and ImportPrivateKey utilities are enhanced to use the domain's secret key to encrypt the passphrases and store them in the domain's DemoCerts.props file. A self-signed Demo CA is automatically created for the domain and it is used for signing certificates for the SSL listen addresses used in the EDG. Although in a real production system, standard CAs should be used, the per-domain CA model implements an SSL system using domain specific CA that provides a higher degree of protection than non-ssl configurations. If you want to use your own custom certificates, see About Using Third Party SSL Certificates in the WebLogic and Oracle HTTP Servers in the Common Configuration and Management Tasks for an Enterprise Deployment chapter.
Oracle recommends using a shared storage location (protected with the appropriate snapshot or file backup tooling) where all the different certificates and stores can be found by the different servers. Perform the following steps to generate an Identity store and a Trust Store that can be used for enabling SSL listeners in a Weblogic Server using a per-domain CA:
-
Download the
generate_perdomainCACERTS.shscript in the maa github repo.https://github.com/oracle-samples/maa/blob/main/1412EDG/generate_perdomainCACERTS.sh
-
Run the script with the following arguments:
- WLS_DOMAIN_DIRECTORY: Directory hosting the Weblogic Domain that the Administration Server uses.
- WL_HOME: The directory within the Oracle home where the Oracle WebLogic
Server software binaries are stored. Typically
/u01/oracle/products/fmw/wlserver. - KEYSTORE_HOME: Directory where appIdentity and appTrust stores will be created.
- KEYPASS: Password used for the weblogic administration user (will be reused for certs and stores).
Example:
./generate_perdomainCACERTS.sh $ASERVER_HOME $ORACLE_HOME/wlserver $KEYSTORE_HOME <keypass>
The script will traverse the
WLS_DOMAIN_DIRECTORY/config/config.xml to find all the listen
addresses used in the domain, generate certificates for all of them, create a Truststore
with the domain CA and the WLS CertGenCA, and import certificates into
a new Identity store. The aliases used in the import will be the same as the hostname
used as listen address. Both the trust store and the identity store will be placed in
the KEYSTORE_HOME directory.
Run the following command to verify if the "domainca" entry is there as a
trustedCertEntry:
keytool -list -keystore $KEYSTORE_HOME/appTrustKeyStore.pkcs12Run the following command to verify if there is a PrivateKeyEntry for
each listen address (the values for ADMINVHN, SOAHOST1 and SOAHOST2):
keytool -list -keystore $KEYSTORE_HOME/appIdentityKeyStore.pkcs12Parent topic: Configuring SSL Certificates for the Domain
Adding Certificate Stores Location to the WebLogic Servers Start Scripts
Once the Identity and Trust Stores are created for the domain some Java properties must
be added to the WebLogic start scripts. These properties are added to the file
setUserOverridesLate.sh in $ASERVER_HOME/bin.
Any customizations you add to this file are preserved during domain upgrade operations
and are carried over to remote servers when using the pack and unpack commands.
-
If you created the Identity and Trust Stores with the script
generate_perdomainCACERTS.sh, as explained in Creating Certificates and Certificate Stores for the WebLogic Domain, then the properties are automatically added to the filesetUserOverridesLate.shin$ASERVER_HOME/bin. Just verify that the file exists and that theEXTRA_JAVA_PROPERTIEShave been added. -
If you are using your own custom certificates, then manually create the file
setUserOverridesLate.shin$ASERVER_HOME/bin. Edit the file and add the variableEXTRA_JAVA_PROPERTIESto set thejavax.net.ssl.trustStoreandjavax.net.ssl.trustStorePasswordproperties with the values used by your EDG system. For example:EXTRA_JAVA_PROPERTIES="${EXTRA_JAVA_PROPERTIES} -Djavax.net.ssl.trustStore=/u01/oracle/config/keystores/appTrustKeyStore.pkcs12 -Djavax.net.ssl.trustStorePassword=mypassword" export EXTRA_JAVA_PROPERTIES
Note:
The order of the extra java properties is relevant. In case that the same property is defined more than once, the later value is used. The custom values must be defined as in the example provided.Parent topic: Configuring SSL Certificates for the Domain
Update Server's Security Settings Using the Remote Console
- Connecting to the Remote Console Using the Administration Server’s Virtual Hostname as Provider
- Updating the WebLogic Servers Security Settings
Parent topic: Configuring SSL Certificates for the Domain
Connecting to the Remote Console Using the Administration Server’s Virtual Hostname as Provider
Note:
For this Remote Console initial access to the Administration Server, it is required that the machine that runs the Remote Console can resolve and connect to the Admin Server's Listen Address. This can be done by starting the Remote Console directly in the node where the Admin Server runs or creating a tunnel to this address from the node where the remote Console is executed.- Using the following default start script to start the Administration
Server:
- Create a new provider in the WebLogic Remote Console as follows:
Configuring KSS with Per-domain CA
For consistency purposes and to use a common CA all across the domain artifacts you may want to use the per-domain CA for KSS (store used by OPSS and other components in the WebLogic Infrastructure/JRF Domain.
Perform the following steps to import the domain CA certificate in the KSS trusted store:
Parent topic: Configuring SSL Certificates for the Domain
Configuring a Per Host Node Manager for an Enterprise Deployment
For specific enterprise deployments, Oracle recommends that you configure a per-host Node Manager, as opposed to the default per-domain Node Manager.
For more information about the advantages of a per host Node Manager, see About the Node Manager Configuration in a Typical Enterprise Deployment.
Creating a Per Host Node Manager Configuration
The step in configuring a per-host Node Manager is to create a configuration
directory and two new node manager configuration files. You must also edit the
default startNodeManager.sh file.
To create a per-host Node Manager configuration, perform the following tasks, first on MFTHOST1, and then on MFTHOST2:
Starting the Node Manager on MFTHOST1
startNodeManager.sh script.
Configuring the Node Manager Credentials
- Access the Domain provider in the Remote Console.
- Click Edit Tree.
- Click Environment > Domain> Security.
- Check the Show Advanced Fields field.
- Set Node Manager Username to the same as the Weblogic Administrator, since this username will be used in other tasks mentioned in this guide.
- Change the NM password. Ensure the Node Manager password is set to the same as the Weblogic Administrator since this password will be used in other tasks mentioned in this guide.
- Click Save. The cart on the top right part of the screen will show full with a yellow bag inside.
- Click the Cart Icon on the top right and select Commit Changes.
Enrolling the Domain with NM
Note:
You will be unable to connect to the Node Manager and use it to start the servers in the domain without performing this step.Adding Truststore Configuration to Node Manager
It is required to add the corresponding truststore configuration for Node
Manager communication with the different WebLogic Server listeners. To do this, edit
Node Manager's start script startNodeManager.sh located at
$NM_HOME and add the variable JAVA_OPTIONS to set the javax.net.ssl.trustStore and
javax.net.ssl.trustStorePassword properties with the values used by
your EDG system. For example:
export JAVA_OPTIONS="${JAVA_OPTIONS} -Djavax.net.ssl.trustStore=/u01/oracle/config/keystores/appTrustKeyStore.pkcs12 -Djavax.net.ssl.trustStorePassword=mypassword"Note:
If you have used thegenerate_perdomainCACERTS.sh script to generate certificates and
stores, the trustStorePassword is the password provided as
"KEYPASS" parameter to the script.
Configuring the Domain Directories and Starting the Servers on MFTHOST1
After the domain is created and the node manager is configured, you can then configure the additional domain directories and start the Administration Server and the Managed Servers on MFTHOST1.
- Disabling the Derby Database
- Starting the Administration Server Using the Node Manager
After you have configured the domain and configured the Node Manager, you can start the Administration Server by using the Node Manager. In an enterprise deployment, the Node Manager is used to start and stop the Administration Server and all the Managed Servers in the domain. - Validating the Administration Server
Before you proceed with the configuration steps, validate that the Administration Server has started successfully by making sure that you have access to the Oracle WebLogic Remote Console and Oracle Enterprise Manager Fusion Middleware Control; both of these are installed and configured on the Administration Servers. - Creating a Separate Domain Directory for Managed Servers on MFTHOST1
When you initially create the domain for enterprise deployment, the domain directory resides on a shared disk. This default domain directory is used to run the Administration Server. You can now create a copy of the domain on the local storage for both MFTHOST1 and MFTHOST2. The domain directory on the local (or private) storage is used to run the Managed Servers. - Starting and Validating the WLS_MFT1 Managed Server on MFTHOST1
After you have configured Node Manager and created the Managed Server domain directory, you can use Oracle Enterprise Manager Fusion Middleware Control to start the WLS_MFT1 Managed Server on MFTHOST1.
Disabling the Derby Database
Starting the Administration Server Using the Node Manager
After you have configured the domain and configured the Node Manager, you can start the Administration Server by using the Node Manager. In an enterprise deployment, the Node Manager is used to start and stop the Administration Server and all the Managed Servers in the domain.
To start the Administration Server by using the Node Manager:
Validating the Administration Server
Before you proceed with the configuration steps, validate that the Administration Server has started successfully by making sure that you have access to the Oracle WebLogic Remote Console and Oracle Enterprise Manager Fusion Middleware Control; both of these are installed and configured on the Administration Servers.
To navigate to Fusion Middleware Control, enter the following URL, and log in with the Oracle WebLogic Server administrator credentials:
https://ADMINVHN:9002/emYou should be able to connect to the Admin Server from the Remote Console as before.
Creating a Separate Domain Directory for Managed Servers on MFTHOST1
When you initially create the domain for enterprise deployment, the domain directory resides on a shared disk. This default domain directory is used to run the Administration Server. You can now create a copy of the domain on the local storage for both MFTHOST1 and MFTHOST2. The domain directory on the local (or private) storage is used to run the Managed Servers.
Placing the MSERVER_HOME on local storage is recommended to eliminate the potential contention and overhead cause by servers writing logs to shared storage. It is also faster to load classes and jars need from the domain directory, so any tmp directory or cache data that the Managed Servers use from the domain directory is processed quicker.
As described in Preparing the File System for an Enterprise Deployment, the path to the Administration Server domain home is represented by the ASERVER_HOME variable, and the path to the Managed Server domain home is represented by the MSERVER_HOME variable.
To create the Managed Server domain directory:
Configuring Web Services Manager
This section describes how to configure Web Services Manager.
Bootstrapping WSM
Note:
If this task is not performed, the WSMPM does not work properly .Parent topic: Configuring Web Services Manager
Propagating the Domain and Starting the Servers on MFTHOST2
After you start and validate the Administration Server and WLS_MFT1 Managed Server on MFTHOST1, you can then perform the following tasks on MFTHOST2.
Unpacking the Domain Configuration on MFTHOST2
Now that you have the Administration Server and the first WLS_WSM1 Managed Server running on MFTHOST1, you can configure the domain on MFTHOST2.
Starting the Node Manager on MFTHOST2
Starting and Validating the WLS_MFT2 Managed Server on MFTHOST2
Use the procedure that is explained in Starting and Validating the WLS_MFT1 Managed Server on MFTHOST1 to start and validate the WLS_MFT2 Managed Server on MFTHOST2.
Modifying the Upload and Stage Directories to an Absolute Path
Configuring the Web Tier for the Extended Domain
Configure the web server instances on the web tier so that the instances route to the proper clusters in the SOA domain.
Setting Frontend Addresses and WebLogic Plugin for the MFT Cluster and the Administration Server
As a security best practice oracle recommends setting a frontend address for the Administration Server and the MFT cluster. In the initial domain creation steps, since OHS and the frontend Load Balancer may have not been configured yet, the frontend setting is avoided to allow verifications using the individual server addresses. However, at this point and before configuring OHS (and the frontend load balancer, if not done yet) it is required to add the pertaining addresses.
Parent topic: Configuring the Web Tier for the Extended Domain
Configuring Oracle HTTP Server for Managed File Transfer
Follow the steps described in Configuring Oracle HTTP Server for an Enterprise Deployment for installing and configuring the OHS servers.
The only difference for MFT is that, instead of creating the
soainternal_vh.conf file, you must create
mft_vh.conf file with the following content, to route the
requests to the MFT Cluster.
Ensure that you edit the file with the appropriate values for Listen, ServerName, VirtualHost, SSLWallet and Location directives:
mft_vh.conf:
###################################################################
# Oracle HTTP Server mod_ossl configuration file: ssl.conf #
###################################################################
# The Listen directive below has a comment preceding it that is used
# by tooling which updates the configuration. Do not delete the comment.
#[Listen] OHS_SSL_PORT
Listen ohshost1.example.com:4443
##
## SSL Virtual Host Context
##
#[VirtualHost] OHS_SSL_VH
<VirtualHost ohshost1.example.com:4443>
ServerName mft.example.com:443
<IfModule ossl_module>
# SSL Engine Switch:
# Enable/Disable SSL for this virtual host.
SSLEngine on
# Client Authentication (Type):
# Client certificate verification type and depth. Types are
# none, optional and require.
SSLVerifyClient None
# SSL Protocol Support:
# Configure usable SSL/TLS protocol versions.
SSLProtocol TLSv1.2 TLSv1.3
# Option to prefer the server's cipher preference order
SSLHonorCipherOrder on
# SSL Cipher Suite:
# List the ciphers that the client is permitted to negotiate.
SSLCipherSuite TLS_AES_128_GCM_SHA256,TLS_AES_256_GCM_SHA384,TLS_CHACHA20_POLY1305_SHA256,TLS_ECDHE_ECDSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_ECDSA_WITH_AES_256_GCM_SHA384,TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256,TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
#Path to the wallet
#SSLWallet "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/keystores/default"
SSLWallet "/u02/oracle/config/keystores/orapki/orapki-vh-WEBHOST1"
<FilesMatch "\.(cgi|shtml|phtml|php)$">
SSLOptions +StdEnvVars
</FilesMatch>
<Directory "${ORACLE_INSTANCE}/config/fmwconfig/components/${COMPONENT_TYPE}/instances/${COMPONENT_NAME}/cgi-bin">
SSLOptions +StdEnvVars
</Directory>
BrowserMatch "MSIE [2-5]" \
nokeepalive ssl-unclean-shutdown \
downgrade-1.0 force-response-1.0
# Add the following directive to add HSTS
<IfModule mod_headers.c>
Header always set Strict-Transport-Security "max-age=63072000; preload; includeSubDomains"
</IfModule>
<Location /wsm-pm>
WLSRequest ON
WebLogicCluster MFTHOST1:7010,MFTHOST2:7010
</Location>
<Location /mftconsole>
WLSRequest ON
WebLogicCluster MFTHOST1:7010,MFTHOST2:7010
</Location>
</IfModule>
</VirtualHost>
Parent topic: Configuring the Web Tier for the Extended Domain
Validating the Managed File Transfer URLs Through the Load Balancer
This section describes how to validate the configuration of Oracle HTTP Server and to verify that the hardware load balancer routes requests through the OHS instances to the application tier.
Configuring and Enabling the SSH-FTP Service for Managed File Transfer
The Oracle Managed File Transfer enterprise deployment topology is based on the Secure File Transfer Protocol (SFTP) for file transfer. SFTP is a separate protocol, packaged with SSH and designed to work similar to FTP, but over a secure connection.
SFTP allows you to limit the number of ports used for file transfer connections. It is preferable to FTP because of its underlying security features and ability to use a standard SSH connection.
- Generating the Required SSH Keys
To enable SFTP, you must generate SSH keys. This procedure needs to be done only once on one of the Managed Servers, because Managed File Transfer shares the same SFTP key for all the servers in the cluster. - Configuring the SFTP Ports
Before you can use the Secure File Transfer Protocol (SFTP) for Oracle Managed File Transfer, you must configure the SFTP Ports. - Configuring Oracle Load Balancer for SFTP Services
- Additional SFTP Configuration Steps for Managed File Transfer
There are several additional configuration steps that you should perform when you use SFTP with Managed File Transfer.
Generating the Required SSH Keys
To enable SFTP, you must generate SSH keys. This procedure needs to be done only once on one of the Managed Servers, because Managed File Transfer shares the same SFTP key for all the servers in the cluster.
Without a valid private key, SSH-FTP server fails to start. To comply with security best practices, you should always use a password-protected private key. Perform the following steps to create the SSH key and configure it for the SFTP embedded servers:
Configuring the SFTP Ports
Before you can use the Secure File Transfer Protocol (SFTP) for Oracle Managed File Transfer, you must configure the SFTP Ports.
Configuring Oracle Load Balancer for SFTP Services
As described in the Configuring Virtual Hosts on the Hardware Load Balancer, the Managed File Transfer requires a TCP virtual server in the load balancer for the Secure File Transfer Protocol (SFTP), in addition to the virtual server for HTTPS. This TCP virtual server directly routes the SFTP requests to the SFTP embedded servers that run on the Managed File Transfer Managed Servers. For consistency, the port used in the hardware load balancer and in the SFTP servers is the same (7022). Ensure you have created the appropriate resources (services, pools, and so on) in your load balancer for this virtual server to allow acces to the SFTP through the load balancer.
Creating a New LDAP Authenticator and Provisioning Users for Managed File Transfer
When you configure an Oracle Fusion Middleware domain, the domain is configured by default to use the WebLogic Server authentication provider (DefaultAuthenticator). However, for an enterprise deployment, Oracle recommends that you use a dedicated, centralized LDAP-compliant authentication provider.
Replacing Connect Strings with the Appropriate TNS Alias
Oracle recommends using TNS Alias in the connection strings used by FMW components instead of repeating long JDBC strings across multiple connections pools.
For more information about how to use TNS alias in your Datasources, see Using TNS Alias in Connect Strings in the Common Configuration and Management Tasks for an Enterprise Deployment chapter.
Backing Up the Configuration
It is an Oracle best practices recommendation to create a backup after you successfully extended a domain or at another logical point. Create a backup after you verify that the installation so far is successful. This is a quick backup for the express purpose of immediate restoration in case of problems in later steps.
The backup destination is the local disk. You can discard this backup when the enterprise deployment setup is complete. After the enterprise deployment setup is complete, you can initiate the regular deployment-specific Backup and Recovery process.
For information about backing up your configuration, see Performing Backups and Recoveries for an Enterprise Deployment.