10 Preparing the Oracle Cloud Infrastructure for an Enterprise Deployment
If you plan to deploy Identity and Access Management on Oracle Cloud Infrastructure (OCI) using the Oracle Container Engine for Kubernetes, you have to configure OCI to facilitate the deployment. Create the required OCI components to perform the deployment.
Note:
The instructions provided in this guide are correct at the time of publishing. Due to the evolving nature of the OCI interface, you may find minor changes in the options. See the Oracle Cloud Infrastructure documentation to obtain the latest steps.- About the OCI Deployment
This illustration shows all the OCI components that you require to deploy Oracle Identity and Access Management on OCI. It shows the different network requirements and how the OCI components fit into those networks. Each subnet is protected by security lists. - Creating an SSH Key Pair
You can configure OCI by using the Oracle Cloud Console and a bastion node. The SSL certificates provide a secure access to the bastion node, compute instances, OKE worker nodes, and database hosts. You have to create an SSL certificate on the host you use to configure OCI. This host could be a laptop or a desktop. - Creating an OCI Compartment
Create a container in your OCI tenancy to hold the deployment. - Creating an OKE Cluster in OCI
You can create a cluster in OKE in one of two ways: by creating a quick cluster with minimum user input or by manually creating a cluster that provides more flexibility. - Creating a Bastion Node
You cannot access the cluster directly because the cluster is in a dedicated subnet. You can use a bastion node to access the cluster. The bastion node will be publicly available. - Creating Compute Instances for Oracle HTTP Servers
The web tier resides in its own subnet separated from both the load balancer and the application tier. This section describes the procedures to create two compute instances for the web tier, place them in different fault domains, and set up security lists and route tables to facilitate access. - Creating File Systems and Mount Targets
You need to create NFS file systems for Kubernetes Persistent Volumes and Oracle HTTP Server installations. - Creating Load Balancers
You need to create two OCI load balancers. One of these load balances is used to direct public traffic and the other for internal call backs. The load balancer used for internal traffic is not available outside the OCI container. - Creating a Network Load Balancer
This step is required only if you want to configure a load balancer to route traffic to the Kubernetes worker nodes. - Creating a Database
There are several different databases that you can create in OCI. For this example, a bare metal RAC database will be created. You may need to create one or more databases. - Creating a Vault
A vault is used to store the credentials of your deployment. At present, the only Oracle Identity and Access Management product using a vault is Oracle Advanced Authentication (OAA). OAA can use either an OCI-based vault (recommended) or a file-based vault. - Creating a DNS Server
This is an optional task. It is important that all host names are resolvable, including the load balancer virtual hosts. You can make them resolvable by adding entries to the local hosts files. However, in OCI, using a private DNS server is the simpler method. - Updating Kubernetes CoreDNS
- Validating Your Environment
Perform the checks described in this section to ensure that your environment is ready for a deployment. - Preparing a Disaster Recovery Environment
A disaster recovery environment is a replica of your primary environment located in a different region from the primary region. This environment is a standby environment that you switch over to in the event of the failure of your primary environment.
Parent topic: Preparing for an Enterprise Deployment
About the OCI Deployment
This illustration shows all the OCI components that you require to deploy Oracle Identity and Access Management on OCI. It shows the different network requirements and how the OCI components fit into those networks. Each subnet is protected by security lists.
Figure 10-1 An Illustration of the OCI Layout for OKE
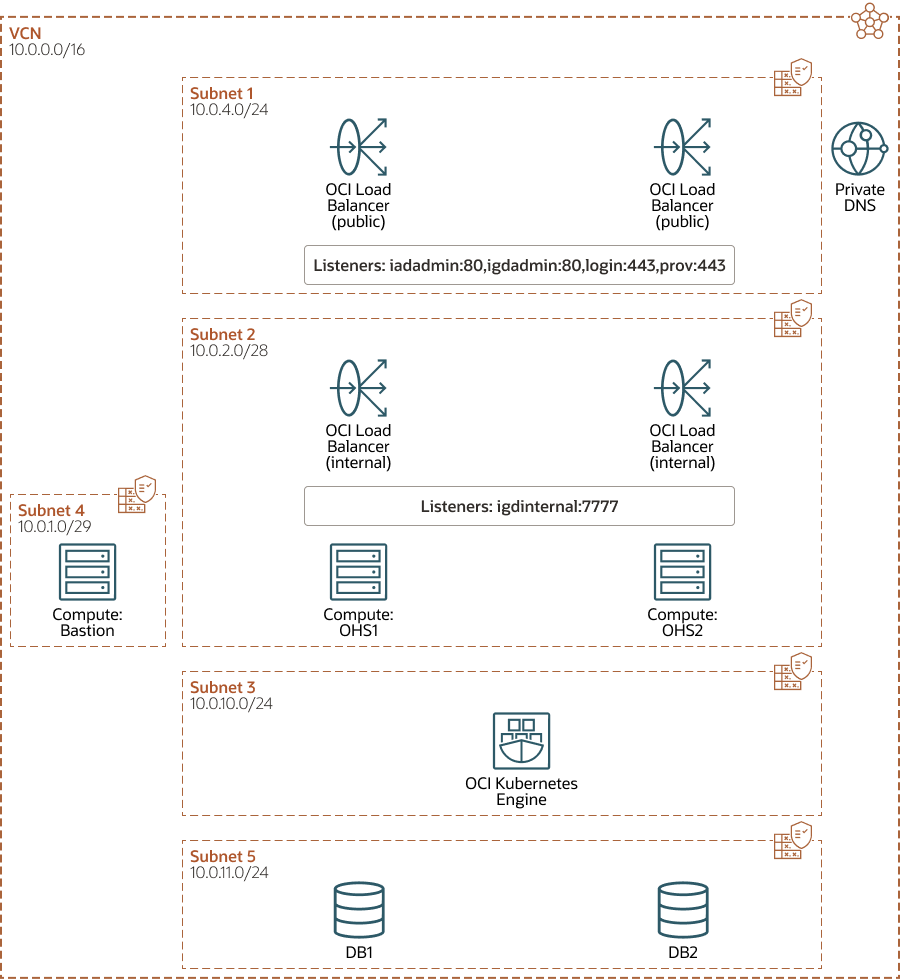
- VCN: There will be one public Virtual Cloud Network which provides external access to the environment. For security reasons, the VCN is broken down into a several subnets.
- Subnets: The VCN is divided into several subnets to ensure that the network traffic is routed only to the areas requiring it. For instance, traffic to the database subnet will not be available directly from the internet. Traffic is available only to the Application (OKE) tier, which interacts with the database subnet.
- Security Lists: Security lists provide an additional layer of security that allows traffic only into and out of a subnet, based on the ports and protocols permitted.
- Bastion Node: The Bastion node is a compute instance inside the VCN that you can log in to. The Bastion node can communicate with all the components inside the deployment. The Bastion node is used for setting up the environment and for ongoing management. Therefore, you must lock down access to the Bastion node to ensure that it is accessed only by clients on your corporate network who are registered with it using an SSL key pair.
- Load balancer: The two LBaaS services are created within the OCI framework. The public-facing load balancer is used to access the Oracle Identity and Access Management deployment from the internet. The private load balancer is for internal traffic, routing it is not available outside of the VCN. The public load balancer is the only internet-facing part of your deployment (except for the Bastion node).
- Oracle Container Engine for Kubernetes (OKE): This is where your application is deployed inside the Kubernetes containers. It is not visible to the internet directly. The Oracle HTTP servers are not deployed in the OKE cluster. These servers are placed into a separate demilitarized zone (DMZ).
- Compute Instances: You require a minimum of two compute instances to host your Oracle HTTP servers. These are placed into a demilitarized zone (DMZ) below the load balancers. The load balancers send requests to the OHS servers, which pass the traffic onto the application residing within the OKE cluster.
- Database: The database(s) are present in a dedicated subnet below the OKE cluster.
- DNS: The DNS server is optional. It is used internally to provide name resolution. You can achieve name resolution by maintaining entries in the individual host files.
The following sections describe the procedure to set up the components depicted in this illustration:
Creating an SSH Key Pair
You can configure OCI by using the Oracle Cloud Console and a bastion node. The SSL certificates provide a secure access to the bastion node, compute instances, OKE worker nodes, and database hosts. You have to create an SSL certificate on the host you use to configure OCI. This host could be a laptop or a desktop.
After you create the certificate on the device, share it with the OCI resources to enable access to the resources and to manage them. If you use more than one device, you have to register the SSL keys for all those devices.
If you do not have an SSL certificate for the device you are using, create the cetificate using the following command:
ssh-keygen -t rsa -N "" -b 2048 -f id_rsaThis command creates two files id_rsa and
id_rsa.pub in the .ssh directory under the
home directory. These are the certificate files you will use to access the OCI
resources.
Creating an OCI Compartment
Create a container in your OCI tenancy to hold the deployment.
- Log in to the Oracle Cloud Infrastructure Console, select Identity, and then click Compartments.
- Click Create Compartment.
- Specify a Name and Description.
- Click Create Compartment.
Creating an OKE Cluster in OCI
Creating an OKE Cluster Using Quick Cluster
The first step in preparing OCI is to create an OKE cluster. This step creates the virtual cloud network, the OKE cluster, and the worker nodes.
To create a quick cluster with default settings:
Parent topic: Creating an OKE Cluster in OCI
Creating an OKE Cluster Manually
To create an OKE cluster manually, you should complete the steps explained in this section. If you want to link two VCNs together, for example, use one VCN for the primary deployment and the other for the DR (Disaster Recovery) deployment, it is essential that the Network CIDRS/IP Addresses do not overlap.
For example, you could use 10.0.0.0/16 for your primary network and 10.1.0.0/16 for your DR network.
- Creating an Oracle Virtual Cloud Network
- Adding Additional Security Rules
- Creating an API Security List
- Creating an API Subnet
- Creating the OKE Cluster
Parent topic: Creating an OKE Cluster in OCI
Creating an Oracle Virtual Cloud Network
These steps will create a public and private subnet.
Parent topic: Creating an OKE Cluster Manually
Adding Additional Security Rules
Parent topic: Creating an OKE Cluster Manually
Creating an API Security List
Parent topic: Creating an OKE Cluster Manually
Creating an API Subnet
Parent topic: Creating an OKE Cluster Manually
Creating the OKE Cluster
Parent topic: Creating an OKE Cluster Manually
Creating a Bastion Node
You cannot access the cluster directly because the cluster is in a dedicated subnet. You can use a bastion node to access the cluster. The bastion node will be publicly available.
Note:
The basion node is the window to your environment. Therefore, access to the bastion node should be strictly controlled.The creation of a bastion node includes the following steps:
Creating Security Lists
You need to create security lists which enable the bastion node to communicate with the subnet that the Kubernetes cluster uses. In addition, you need to allow access to the bastion node from the internet. This section describes the minimum steps you need to perform to enable this access. You should harden your security lists to ensure that only certain machines/networks have access to this node. Information about restricting access beyond the SSL key generated earlier is outside the scope of this document.
To create security lists:
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking > Virtual Cloud Networks and click the name of your Virtual Cloud Network.
- Select Security Lists from the list of resources.
Parent topic: Creating a Bastion Node
Creating a Private Security List
Table 10-3 Description for Ingress and Egress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
22 |
|
|
Ingress |
CIDR |
10.0.1.0/29 |
ICMP |
||
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
Note:
10.0.1.0 is the subnet you will use for the bastion node. You can change this value if required.Parent topic: Creating Security Lists
Creating a Public Security List
Table 10-4 Description for Ingress and Egress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range | Type |
|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
ICMP |
3 |
||
|
Ingress |
CIDR |
0.0.0.0/0 |
ICMP |
|||
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
Note:
10.0.1.0 is the subnet you will use for the bastion node. You can change this value if required. Unless otherwise stated, leave the values blank.Parent topic: Creating Security Lists
Creating a Setup Security List
During the set up of Oracle Identity and Access Management, the bastion node requires access to some of the Kubernetes services that get created as part of the build process.
The access is not required after the build process is complete. For manageability reasons, a separate security list is created for this purpose. This way, after the setup is complete, you just have to remove the security list from the subnet. If further setups are required, you can add as needed.
-
Private subnet for Node Manager
-
db-subnet.
To create a setup security list:
Table 10-5 Description for Ingress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range | Comment |
|---|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
30701 |
OAM Administration Server Kubernetes Service Port |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
31800 |
|||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
31920 |
Note:
The destination ports listed above are dependent on the values you provide to your installation. Sample values will be used for consistency within this guide.
The destination port range of 31800 and 31920 are required if you are deploying Elasticsearch.
Parent topic: Creating Security Lists
Creating a Route Table
You should create a route table which enables the bastion node to communicate with the subnet that the Kubernetes cluster uses. In addition, you should also enable access to the bastion node from the internet.
To create a route table:
Parent topic: Creating a Bastion Node
Creating a Subnet for the Bastion Node
After you create the security rules and route table, you should create a subnet and assign the security rules and route table to it.
Parent topic: Creating a Bastion Node
Adding the Security List to the Kubernetes Node Subnet
To enable communication between the bastion subnet and the Kubernetes Cluster Subnet, you need to add the private security list to the Kubernetes Node subnet.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- From your Kubernetes Cluster Summary screen, click the VCN
Name that looks similar to
oke-vcn-quick-clustername-id. - Click the Kubernetes node network that looks similar to
oke-nodesubnet-quick-clustername-id-regional. - Click Add Security List.
- Select your compartment.
- Select the private bastion security list. For example:
bastion-private-seclist. - Click Add Security List.
- Repeat the above steps to add the and
bastion-setup-seclistsecurity list.
Parent topic: Creating a Bastion Node
Creating the Bastion Compute Instance
After defining the networking details, create the bastion node.
Parent topic: Creating a Bastion Node
Connecting to the Bastion Node
You can now connect to the bastion node using the following SSH command:
ssh -i id_rsa opc@BastionIPAddressAlternatively, if you are using SSH agent forwarding, which enables you to use your local SSH keys instead of leaving the keys (without passphrases) on the server, then you can use the following command:
ssh -A opc@BastionIPAddressParent topic: Creating a Bastion Node
Configuring the Bastion Node
After you create the bastion node, you need to configure it. Perform the following steps to configure the bastion node:
Note:
To perform the steps in this section, you will require the following information from the Oracle Cloud Infrastructure Console:
- User OCID: To obtain your User OCID, click your profile in the OCI Console (top right) and select User Settings to view your OCID.
- Tenancy OCID: To obtain your Tenancy OCID, click your profile in the Oracle Cloud Infrastructure Console (top right) and select your tenancy to view the tenancy OCID.
- Region: The region in which you have deployed the cluster.
- Setting Up the OCI CLI to Download Kubeconfig
- Installing Helm
- Installing Git
- Installing X11 Packages
- Installing Other Packages
- Enabling X11 Forwarding
- Setting Up the Hosts File
Parent topic: Creating a Bastion Node
Setting Up the OCI CLI to Download Kubeconfig
Parent topic: Configuring the Bastion Node
Installing Helm
Helm is required by the WebLogic Operator and Oracle Unified Directory. To install Helm on to the bastion node, run the following commands:
$ curl -fsSL -o get_helm.sh
https://raw.githubusercontent.com/helm/helm/main/scripts/get-helm-3
$ chmod 700 get_helm.sh
$ ./get_helm.sh
$ helm version
version.BuildInfo{Version:"v3.13.1",
GitCommit:"3547a4b5bf5edb5478ce352e18858d8a552a4110",
GitTreeState:"clean", GoVersion:"go1.20.8"}Parent topic: Configuring the Bastion Node
Installing Git
Git contains sample code to deploy Oracle Fusion Middleware on Kubernetes. Install GIT using the following command:
sudo yum install git -yParent topic: Configuring the Bastion Node
Installing X11 Packages
For security reasons, the Oracle HTTP Server is not installed inside the Kubernetes cluster. To install the Oracle HTTP Server, you need to install the X11 packages to enable X11 forwarding. Use the following command to install the X11 packages:
sudo yum install -y libXrender libXtst xauth xterm ncParent topic: Configuring the Bastion Node
Installing Other Packages
sudo yum install -y openldap javaFor information about using automation scripts, see Automating the Identity and Access Management Enterprise Deployment.
Parent topic: Configuring the Bastion Node
Enabling X11 Forwarding
Parent topic: Configuring the Bastion Node
Setting Up the Hosts File
curl commands to the load balancer. Because the bastion node uses the private DNS, the IP addresses returned for the load balancer end points is through the internal network that the bastion host does not have access to. To get around this issue, create an entry in the bastion hosts file for each entry point that points to the public IP address of the load balancer.
Note:
You cannot perform this step until you have created the load balancers. See Creating Load Balancers.129.1.1.3 login.example.com prov.example.com iadadmin.example.com igdadmin.example.comParent topic: Configuring the Bastion Node
Creating Compute Instances for Oracle HTTP Servers
The web tier resides in its own subnet separated from both the load balancer and the application tier. This section describes the procedures to create two compute instances for the web tier, place them in different fault domains, and set up security lists and route tables to facilitate access.
- Creating a Service Gateway
- Creating Security Lists
- Creating an OHS Security List
- Adding the OHS Security List to the Kubernetes Subnet
- Creating a Route Table
- Creating a Subnet for Web Nodes
- Creating the OHS Compute Instances
- Editing OHS Compute Instance Fault Domain
- Connecting to the OHS Nodes
- Configuring the OHS Nodes
Creating a Service Gateway
The web tier is not accessible to the internet directly. But it will require access to internal resources to perform operations such as accessing yum for adding the required packages and performing upgrades. To enable access to these internal systems, you need to create a service gateway if the system did not automatically create one for you.
To create a service gateway:
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Creating Security Lists
You need to create security lists which enable web tier nodes to communicate with the subnet that the Kubernetes cluster uses. In addition, you need to enable access to the web tier hosts from the load balancer. This section describes the minimum steps you need to perform to enable this access. You should harden your security lists to ensure that only certain machines/networks have access to this node. This part is outside the scope of this guide.
To create security lists:
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking > Virtual Cloud Networks and click the name of your Virtual Cloud Network.
- Select Security Lists from the list of resources.
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Creating an OHS Security List
During the running of Oracle Identity Management, the web tier hosts pass through the requests to the Kubernetes services that get created as part of the provisioning process. You need to create a security list to enable this communication to take place.
Table 10-6 Description for Ingress Rules
| Rule Type | Type | Source CIDR | Protocol | Destination Port Range | Comment |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30701 |
OAM Administration Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30510 |
OAM Policy Manager Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30410 |
OAM Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30711 |
OIG Administration Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30140 |
OIM Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30801 |
SOA Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30901 |
OUDSM Server Kubernetes Service Port |
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
30777 |
Nginx Ingress Controller |
Note:
The destination ports listed in this table are dependent on the values you provide to your installation.Parent topic: Creating Compute Instances for Oracle HTTP Servers
Adding the OHS Security List to the Kubernetes Subnet
The security list now needs to be added to the subnet used by Kubernetes.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking > Virtual Cloud Networks and click the name of your Virtual Cloud Network.
- Select the Kubernetes sublist from the list of displayed
subnets. The subnet will have a name similar to
oke-nodesubnet-<ClusterName>-<id>. - Click Add Security List.
- Select the compartment and the security list you created earlier. For example:
ohs-seclist. See Creating an OCI Compartment and Creating an OHS Security List. - Click Add Security List.
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Creating a Route Table
You need to create a route table which enables the web tier nodes to communicate with the subnet that the Kubernetes cluster uses.
To create a route table:
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Creating a Subnet for Web Nodes
Now that you have created security rules and route table, you can create a subnet and assign the security rules and route table to it.
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Creating the OHS Compute Instances
Now that the networking has been defined, you can create the web tier nodes.
The summary screen displays the private IP address assigned to the web tier node. Make a note of this address. You will need it for connecting to the node.
Repeat the steps for the second node.
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Editing OHS Compute Instance Fault Domain
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Connecting to the OHS Nodes
You cannot connect to the web tier hosts directly. You must use the bastion node. You can connect to the web tier hosts after you have connected to the bastion node. See Connecting to the Bastion Node.
Note:
When you created the compute instance, you specified the SSH key you would use to connect to the host. If you used the same key as your laptop/desktop, you should use SSH Agent forwarding to connect to the web host. Alternatively, you can also use the SSH key you created on the bastion host.You can now connect to the web host from the bastion node using the following SSH command:
ssh -i id_rsa opc@webhostIPAddressAlternatively, if you are using SSH agent forwarding, which enables you to use your local SSH keys instead of leaving the keys (without passphrases) on the server, you can use the same pass through command:
ssh -A opc@webIPAddressParent topic: Creating Compute Instances for Oracle HTTP Servers
Configuring the OHS Nodes
After you create the web tier nodes, you need to configure them. Perform the following steps to configure the nodes:
- Installing X11 Packages
- Installing Additional Packages
- Enabling X11 Forwarding
- Preparing the Compute Instance for Use by Oracle HTTP Server
- Using the Firewall
- Creating a Software Owner Account
- Preparing the Hosts File
- Connecting to the Compute Instances to Install OHS
Parent topic: Creating Compute Instances for Oracle HTTP Servers
Installing X11 Packages
For security reasons, the Oracle HTTP Server is not installed inside the Kubernetes cluster. To install the Oracle HTTP Server, you have to install the X11 packages to enable X11 forwarding.
Use the following commands to install the X11 packages:
sudo yum repolistsudo yum install -y libXrender libXtst xauth xterm nc xorg-x11*Parent topic: Configuring the OHS Nodes
Installing Additional Packages
The Oracle HTTP Server requires additional packages to be present as part of the installation. Use the following command to install these additional packages:
sudo yum install -y libaio-devel* compat-libstdc++-* compat-libcap* gcc-c++-* ksh* libnsl*Parent topic: Configuring the OHS Nodes
Enabling X11 Forwarding
Parent topic: Configuring the OHS Nodes
Preparing the Compute Instance for Use by Oracle HTTP Server
You may also need to install additional Linux packages required to install the Oracle HTTP server, as well as setting the kernel parameters. See Preparing the Kubernetes Host Computers for an Enterprise Deployment.
Parent topic: Configuring the OHS Nodes
Using the Firewall
The compute instance is created using an Oracle Linux image. The image comes with a built-in firewall, which is enabled by default. Even though you have security rules defined in your network, the Linux server rejects these requests because of the built-in Linux firewall.
You can decide to use this extra firewall or rely on your OCI security rules.
Opening the Ports in the Firewall
Parent topic: Using the Firewall
Disabling the Firewall
To disable the firewall, run the following commands:
sudo systemctl stop firewalld
sudo systemctl disable firewalldParent topic: Using the Firewall
Creating a Software Owner Account
It is not good practice to install the Oracle software using the OPC user. It is better to create a custom user to own the software. You can create a custom user by running the following commands:
sudo adduser -u 1001 oracle
sudo groupadd -g 1002 oinstall
sudo usermod -a -G oinstall oracle
sudo usermod -g oinstall oracleParent topic: Configuring the OHS Nodes
Preparing the Hosts File
The nature of the networks in an OCI environment means that the Oracle HTTP Server instances will not have access to the public load balancer. This can cause issues when the Oracle HTTP Server tries to access some virtual hosts.
In later sections, you will create a public load balancer for connections from the outside world to your system. See Creating a Public Load Balancer.
You will also create a private load balancer to allow you to route requests from the private subnets to this load balancer. See Creating a Private Load Balancer.
/etc/hosts file on the web hosts, which looks as
follows:IP ADDRESS OF PRIVATE LOAD BALANCER login.example.com10.0.2.7 login.example.comParent topic: Configuring the OHS Nodes
Connecting to the Compute Instances to Install OHS
To install the Oracle HTTP Server, you will need access to a graphical display. To get this access, you should use X11 Forwarding.
For detailed instructions for installing OHS, see Installing and Configuring Oracle HTTP Server.
Parent topic: Configuring the OHS Nodes
Creating File Systems and Mount Targets
You need to create NFS file systems for Kubernetes Persistent Volumes and Oracle HTTP Server installations.
The filesystems that you have to create are described in Storage Requirements for an Enterprise Deployment.
Overview of Preparing the File System for an Enterprise Deployment
It is important to set up your storage in a way that makes the enterprise deployment easy to understand, configure, and manage.
This chapter provides an overview of the process of preparing the file system for an enterprise deployment. Oracle recommends setting up your storage according to information in this chapter. The terminology defined in this chapter is used in the diagrams and procedures throughout the guide.
Parent topic: Creating File Systems and Mount Targets
Summary of File Systems
See Table 4-3 for details of the file systems you have to create.
You have to mount the file systems to the bastion node only during the initial set up.
Parent topic: Creating File Systems and Mount Targets
Creating a File System
Note:
Create a new mount target only for the first persistent volume (PV). Subsequent PVs should use the same mount target.Parent topic: Creating File Systems and Mount Targets
Setting the Mount Target Storage Reporting
When you install Oracle products, the installer checks the available disk storage. This check fails when you use an OCI file system. The system displays a message saying that there is insufficient disk space. To overcome this error, you can configure OCI to report a specified amount of free space.
Parent topic: Creating File Systems and Mount Targets
Creating a PV Security List
Even though you have created the mount point in the same subnet as you want to use it, you still need to create a security list to access it. The web tier entries have already been added. However, you still need to create a security list for the OHS mount target.
Table 10-7 Description for Ingress and Egress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range |
|---|---|---|---|---|---|---|
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.10.0/24 |
UDP |
2048 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.1.0/29 |
UDP |
2048 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
||
|
Ingress |
CIDR |
10.0.2.0/28 |
UDP |
2048 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.10.0/24 |
UDP |
111 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.1.0/29 |
UDP |
111 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
111 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
2048-2050 |
||
|
Egress |
CIDR |
10.0.2.0/28 |
UDP |
111 |
Note:
The rules for the bastion subnet are required only for the initial set up/configuration.Parent topic: Creating File Systems and Mount Targets
Adding the Security List to the Subnet
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking > Virtual Cloud Networks and click the name of your Virtual Cloud Network.
- Select oke-nodesubnet.
- Click Add Security List.
- Select the security list you created earlier. For example:
pv-seclist. See Creating a PV Security List. - Click Add Security List.
- Repeat Steps 1 to 6 for the subnets
web-subnetand thebastion-subnet.
Parent topic: Creating File Systems and Mount Targets
Mounting File Systems on Hosts
Each mount target has a different IP address. To determine how to mount a given file system:
Parent topic: Creating File Systems and Mount Targets
Creating Load Balancers
You need to create two OCI load balancers. One of these load balances is used to direct public traffic and the other for internal call backs. The load balancer used for internal traffic is not available outside the OCI container.
For more information about load balancers, see Getting Started with Load Balancing.
Creating a Public Load Balancer
This load balancer directs traffic from the internet to the Oracle HTTP Servers, which in turn pass on the traffic to the Kubernetes pods.
The public load balancer will send traffic to and from the user via SSL but after the traffic moves inside the OCI Virtual Network, it is sent unencrypted. The decryption occurs due to SSL Termination. You will need to provide your own SSL certificate or create a self-signed certificate for testing purposes.
To create a public load balancer, perform the following steps:
- Creating a Self-Signed Certificate
- Creating a Security List
- Creating a Route Table
- Creating Subnets for the Load Balancer
- Creating a Load Balancer
- Uploading Load Balancer Certificates
- Creating Host Names
- Creating Listeners
- Updating the Default Listener
Parent topic: Creating Load Balancers
Creating a Self-Signed Certificate
You can create a self-signed certificate on any host which has access to the
openssl packages. The following example is from a Linux box (in
this case the bastion server was used).
For more information, see Doc ID 2617046.1.
If you prefer, you can also use a certificate provided by a recognized certificate authority.
To create a self-signed certificate:
ca.crtloadbalancer.crtloadbalancer.key
Parent topic: Creating a Public Load Balancer
Creating a Security List
The security list determines who can access the load balancer and where the load balancer is allowed to send requests.
To create a private security list:
Table 10-9 Description for Ingress and Egress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
80 |
|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
443 |
|
|
Egress |
CIDR |
10.0.2.0/28 |
TCP |
7777 |
Note:
10.0.2.0 is the subnet you will use for the web tier.Parent topic: Creating a Public Load Balancer
Creating a Route Table
You need to create a route table which enables the load balancer to communicate with the internet.
To create a route table:
Parent topic: Creating a Public Load Balancer
Creating Subnets for the Load Balancer
The public load balancer is placed into an isolated subnet. The load balancer is created as a pair so that if one fails, the second one takes on the work load. The load balancers reside in availability domains and a different subnet is created for each load balancer. By using different subnets for the load balancers, you create stricter access rules enabling public access only to the load balancer but not the components for which it load balances.
Parent topic: Creating a Public Load Balancer
Uploading Load Balancer Certificates
As the load balancer routes SSL requests, you need to upload the certificates for the load balancer. If you have created a self-signed certificate, add the details of that certificate. If you have your own certificates, upload those.
To upload the certificates:
Parent topic: Creating a Public Load Balancer
Creating Host Names
Host names are used to filter the different entry points into the load balancer. You need to create a host name for each load balancer virtual host described in Summary of the Load Balancer Virtual Servers Required for an Enterprise Deployment.
You have to create the following host names:
iadadmin.example.comigdadmin.example.comlogin.example.comprov.example.com
To create the load balancer host names:
Note:
If you want to limit the admin access to users inside the network, you should create the hostsiadadmin.example.com and
igdadmin.example.com in the private load balancer.
Parent topic: Creating a Public Load Balancer
Creating Listeners
You need to create a listener for each host name you have created
earlier. See Creating Host Names. The iadadmin listener has been created at the
time of creating the load balancer. See Creating a Load Balancer.
Table 10-10 Summary of Public Load Balancer Listeners
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
|
http |
80 |
ohs_servers |
|
|
|
|
http |
80 |
ohs_servers |
|
|
|
|
https |
443 |
Yes |
ohs_servers |
|
|
|
https |
443 |
Yes |
ohs_servers |
|
To create the load balancer listeners:
Note:
If you want to limit the admin access to users inside the network, create the listenersiadadmin.example.com and igdadmin.example.com
in the private load balancer.
Parent topic: Creating a Public Load Balancer
Updating the Default Listener
When you created the load balancer, a default listener also gets created. You have to assign the newly created host name to this listener.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click the load balancer. For example: public-loadbalancer.
- Select Listeners from the resource list.
- To edit the listener, click the three dots next to the name, and then click Edit.
- Set the host name to the host name you created earlier. For example: iadadmin. See Creating Host Names.
- Click Update Listener.
Parent topic: Creating a Public Load Balancer
Creating a Private Load Balancer
The private load balancer, which is used to route internal call backs, resides in the same subnet as the Oracle web servers. This load balancer services requests generated from inside the application.
Note:
Web servers issuecurl commands to
login.example.com. Therefore, you also need to define this on the
private load balancer because the web servers do not have direct access to the public
load balancer. You can use the same certificates that you used when you created the
public load balancer.
To create a private load balancer, perform the following steps:
- Creating a Load Balancer
- Creating Host Names
- Updating the Default Listener
- Uploading Load Balancer Certificates
- Creating Listeners
Parent topic: Creating Load Balancers
Creating Host Names
Host names are used to filter the different entry points into the load balancer. You need to create a host name for each load balancer virtual host described in Summary of the Load Balancer Virtual Servers Required for an Enterprise Deployment.
igdinternal.example.comlogin.example.comiadadmin.example.comigdadmin.example.com
Note:
login.example.com is defined here for internal traffic routing. The EDG uses network segregation. If you do not define it here, calls to login.example.com will attempt to communicate using the public network and fail.
To create the load balancer host name:
Parent topic: Creating a Private Load Balancer
Updating the Default Listener
When you created the load balancer, a default listener also gets created. You have to assign the newly created host name to this listener.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click the load balancer. For example: internal_loadbalancer.
- Select Listeners from the resource list.
- To edit the listener, click the three dots next to the name, and then click Edit.
- Set the host name to the host name you created earlier. For example: igdinternal. See Creating Host Names.
- Click Update Listener.
Parent topic: Creating a Private Load Balancer
Uploading Load Balancer Certificates
As the load balancer routes SSL requests, you need to upload the certificates for the load balancer. If you have created a self-signed certificate, add the details of that certificate. If you have your own certificates, upload those.
To upload the certificates:
Parent topic: Creating a Private Load Balancer
Creating Listeners
You need to create a listener for each host name you have created earlier. See Creating Host Names.
Table 10-11 Summary of Private Load Balancer Listeners
| Name | Protocol | Port | SSL | Backend Set | Host Name |
|---|---|---|---|---|---|
|
igdinternal |
http |
7777 |
No |
ohs_servers |
|
|
login |
https |
443 |
Yes |
ohs_servers |
|
|
iadadmin |
http |
80 |
No |
ohs_servers |
|
|
igdadmin |
http |
80 |
No |
ohs_servers |
|
To create the load balancer listeners:
Parent topic: Creating a Private Load Balancer
Creating a Network Load Balancer
This step is required only if you want to configure a load balancer to route traffic to the Kubernetes worker nodes.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Navigate to Networking and click Load Balancers.
- Click Create Load Balancer.
- Select Network Load Balancer and click Create Load Balancer.
- In the Create Network Loadbalancer section, specify the
following information:
- Load Balancer Name: Select a name for your load balancer. For example: k8workers.
- Visibility Type: Select Private.
- Virtual Cloud Network: Select Virtual Cloud Network.
- Subnet: Select the same subnet as the Kubernetes worker nodes. For example: one-nodesubnet-quick-<clustername>-<id>.
- Compartment: Select the compartment.
- Click Next.
- In the Listener screen, specify the following information:
- Listener: Select TCP.
- Type: Select TCP.
- Select Use Any Port.
- Click Next.
- In the Backend Set screen, specify the following information:
- Backend Set Name: Select K8Workers.
- Click Add Backends.
- In the Backends screen, ensure that all the worker nodes are selected, and then click Add Backends.
- Health Check Policy - Select TCP and set the port to 22. Use the default values for all other values.
- Click Next.
- Review the details and click Create.
Creating a Database
There are several different databases that you can create in OCI. For this example, a bare metal RAC database will be created. You may need to create one or more databases.
See Preparing an Existing Database for an Enterprise Deployment for details on the databases and services you should create. This section shows an example of creating one of these databases in OCI.
Creating a Security List
Table 10-12 Description for Ingress and Egress Rules
| Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Destination Port Range |
|---|---|---|---|---|---|
|
Ingress |
CIDR |
0.0.0.0/0 |
TCP |
22 |
|
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
1521 |
|
|
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
6200 |
|
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
1521 |
|
|
Ingress |
CIDR |
10.0.10.0/24 |
TCP |
6200 |
|
|
Ingress |
CIDR |
10.0.1.0/29 |
TCP |
1521 Note: Used for set up only. |
|
|
Egress |
CIDR |
0.0.0.0/0 |
All Protocols |
Note:
10.0.11.0 is the subnet to use for the database. You can change this value, if required.Parent topic: Creating a Database
Creating a Route Table
You need to create a route table which enables the database to communicate with the OKE cluster.
To create a route table:
Parent topic: Creating a Database
Creating Subnets for the Database
The database is placed into an isolated subnet.
To create subnets for the database:
Parent topic: Creating a Database
Creating the Database
After establishing the network, you can now create the database.
Note:
After the database is created, OCI adds a suffix to the database name. Ensure that you use the complete name including this suffix when configuring the database as described in Preparing an Existing Database for an Enterprise Deployment.Parent topic: Creating a Database
Creating a Secondary Pluggable Database
When you create the database, it creates a single pluggable database (PDB). A single PDB may be sufficient for your needs.
However, if you require more PDBs so that OAM, OIG, OIRI, and OAA use different PDBs in the same database, you have to create additional PDBs. See Creating a PDB Using an Existing PDB as a Template.
You can do this either at the database level or, if you are using Oracle OCI, through the OCI console. For adding a PDB at the database level, see Creating a PDB Using an Existing PDB as a Template.
- Log in to the Oracle Cloud Infrastructure for your tenancy.
- Navigate to Oracle Database and click Oracle Base Database (VM, BM).
- Click the DB system hosting the database.
- Click the Container Database Name from the list of displayed databases.
- Click Pluggable Databases in the Resources menu.
- Click Create Pluggable Database.
- Add a name for the new pluggable database and enter the TDE wallet password for the container database. This password may be the same as the database SYS password if you opt not to set an explicit value.
- Click Create Pluggable Database.
- Repeat Step 6 through Step 8 for each additional pluggable database you require.
Parent topic: Creating a Database
Connecting to the Database Node
You can now connect to the database node using the following SSH command:
ssh -A opc@databaseNodeIPAdddressConnect to DB node 1 from the bastion node using the command:
ssh -A opc@dbnode1After you connect to DB node 1 as opc, connect to the oracle user using
the following command:
sudo su - oracleParent topic: Creating a Database
Configuring the Database
After you create the skeletal database, you should configure the database as described in Preparing an Existing Database for an Enterprise Deployment.
Parent topic: Creating a Database
Creating a Vault
A vault is used to store the credentials of your deployment. At present, the only Oracle Identity and Access Management product using a vault is Oracle Advanced Authentication (OAA). OAA can use either an OCI-based vault (recommended) or a file-based vault.
- Log in to the Oracle Cloud Infrastructure for your tenancy.
- Select Identity and Security and click Vault.
- Click Create Vault and specify the following
details:
- Compartment - Select the compartment you created earlier. See Creating an OCI Compartment.
- Name – Enter a name for the vault. For example: oaavault.
- Select Make it a private vault.
- Click Create Vault.
Creating the API Key
- Log in to the Oracle Cloud Infrastructure Console.
- Select Profile and click User Settings.
- On the User Settings screen, select API Keys.
- Click Add API Key.
- Click Download API Key. Keep this file safe.
- Click Add.
- Click Close.
Parent topic: Creating a Vault
Creating a DNS Server
This is an optional task. It is important that all host names are resolvable, including the load balancer virtual hosts. You can make them resolvable by adding entries to the local hosts files. However, in OCI, using a private DNS server is the simpler method.
By default, the compute hosts are configured to use a private DNS server. You have to add the entries only for the local hosts.
Creating DNS Records
After you create the zone, you can create records in the zone for each host. There are two types of DNS records that have to be created:
- A Record: This is an IP address association with a host name.
- CNAME: This is an alias for the A Record.
If you have multiple hosts using the same IP address, Oracle recommends you to create one 'A Record' and multiple 'CNAME' records.
To create a record:
Parent topic: Creating a DNS Server
Updating Kubernetes CoreDNS
The Kubernetes cluster resolves hostnames using the built-in CoreDNS server. By default, this server will not interact with the corporate DNS server. You must configure this server to either perform local hostname resolution for the application end points or to resolve those end points using the corporate DNS server.
-
Create a config map with your custom hosts in called
coredns_custom.yaml. For example:apiVersion: v1 kind: ConfigMap metadata: name: coredns-custom namespace: kube-system data: example.server: | example.com { hosts { 1.1.1.1 login.example.com 1.1.1.2 prov.example.com 1.1.1.3 iadadmin.example.com 1.1.1.4 igdadmin.example.com 1.1.1.5 igdinternal.example.com fallthrough } } - Save the file.
-
Create the config map using the following command:
kubectl create -f coredns_custom.yaml - Restart CoreDNS using the
command:
kubectl rollout restart -n kube-system deploy corednsEnsure that the CoreDNS pods restart without any issue, using the command:kubectl get pods -n kube-systemEnsure that the custom config has been loaded by using the following command:kubectl get configmaps --namespace=kube-system coredns-custom -o yamlIf any errors occur, use the following command to view them:kubectl logs -n kube-system coredns--<ID>Correct the errors by editing the configmap again.
Validating Your Environment
Perform the checks described in this section to ensure that your environment is ready for a deployment.
For the bastion node
- Check the network
connectivity
ping webhost1.example.comping webhost2.example.com - Resolve the public address of the load
balancer
ping login.example.comping prov.example.com - Check that Kubernetes is
working
kubectl get nodesPing each of the worker nodes that are listed as the output of the above command.
From the Web Tier
-
Ensure that the kubernetes worker node names are resolvable
nslookup k8workers -
Verify if the web tier can communicate with the Kubernetes worker nodes which includes the port that you communicate on. If you are using an ingress controller, then this will be the node port assigned to that ingress controller. If you are using individual nodePort Services, then you should check each of those ports.
Use the following command to check network connectivity:
nc -zv <WORKER_NODE> <PORT>For example, if your ingress server is using NodePort server 30777 then the command is as follows:
nc -zv 1.1.1.1 30777Ncat: Version 7.70 ( https://nmap.org/ncat ).
Ncat: Connected to 1.1.1.1:30777.
Ncat: 0 bytes sent, 0 bytes received in 0.01 seconds.
-
Resolve the public address of the load balancer
ping login.example.com
Preparing a Disaster Recovery Environment
A disaster recovery environment is a replica of your primary environment located in a different region from the primary region. This environment is a standby environment that you switch over to in the event of the failure of your primary environment.
The standby environment will be a separate cluster, ideally in a different data center. If the cluster is dedicated to the application, the second cluster should be a mirror of the primary cluster with the same number and specifications of worker nodes. If your cluster is a multi-purpose cluster that is used by different applications, ensure sufficient spare capacity in the standby site to run the full application workload of the primary cluster.
Each Kubernetes cluster will run the same operating system version and the Kubernetes major release.
Your network will be such that:
- The primary and standby database networks communicate with each other to facilitate the creation of a Data Guard database.
- The primary and standby file system networks communicate with each
other to facilitate the replication of the file system data. If you have to run the
Rsyncprocess to achieve the replication inside the cluster, then the primary Kubernetes worker network will be able to communicate with the Kubernetes worker network on the standby site. - A global load balancer will be used to direct the traffic between the primary and standby sites. This load balancer is often independent of the site-specific load balancers used for on-site communication.
- The SSL certificates used in the load balancers must be the same in each load balancer. The traffic should not be aware when the load balancer switches sites.
There are several ways to create a DR environment. This document makes the following assumptions:
- You will create an exact replica of your primary environment.
- The DR environment will reside in the same tenancy as your primary environment.
- The DR environment will reside in the same compartment as your primary environment.
- The DR environment will reside in a different region from your primary environment.
You will create the standby environment using the same steps as the primary environment, followed by the steps to create an OKE cluster, with the following characteristics:
- The VCN must use different CIDRs. For example,
10.0.0.0/16for the primary cluster and10.1.0.0/16for the standby cluster. - Subnets will use different IP address ranges. For example, a primary subnet may be
10.0.4.0/24and the equivalent standby subnet would be10.1.4.0/24. - The load balancer virtual host names will be the same.
- The load balancer SSL certificates will be the same.
- The ports used will be the same.
- The webhost names will be the same.
- Dedicated bastion nodes will exist.
After you create both the environments, complete the following additional steps:
Creating a Dynamic Routing Gateway
A dynamic routing gateway (DRG) is required to ensure that two different virtual cloud networks (VCNs) can communicate with each other. Each site requires a DRG. Therefore, perform the following steps on each site.
Parent topic: Preparing a Disaster Recovery Environment
Creating a Dynamic Routing Gateway Attachment
After you create the DRG, you should attach it to the VCN of the site.
Parent topic: Preparing a Disaster Recovery Environment
Creating a Remote Peering Connection
Parent topic: Preparing a Disaster Recovery Environment
Connecting the Site 1 and Site 2 VCNs
Before you perform this step, ensure that you have created the Dynamic Routing Gateway (RPG) (see Creating a Dynamic Routing Gateway and the Remote Peering Connection (RPC) (see Creating a Remote Peering Connection) on both the sites. The following steps will help link the two sites.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking and click Dynamic Routing Gateway.
- Select the Dynamic Routing Gateway you created earlier. For example,
site1-DRG. See Creating a Dynamic Routing Gateway. - From the list of resources, select Remote Peering Connections Attachments.
- From the Remote Peering Connections Attachments section, select the Remote
Peering Connection you created earlier. For example,
site1-RPC. See Creating a Remote Peering Connection. Make a note of the Remote Peering Connection OCID displayed at the top of the screen.
Perform the following steps on Site 2:
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking and click Dynamic Routing Gateway.
- Select the Dynamic Routing Gateway you created earlier. For example,
site1-DRG. See Creating a Dynamic Routing Gateway. - From the list of resources, select Remote Peering Connections Attachments.
- From the Remote Peering Connections Attachments section, select the Remote
Peering Connection you created For Site 2. For example,
site2-RPC. For instructions, see Creating a Remote Peering Connection. - Click Establish Connection and enter the following
information:
- Region: Select the region that hosts Site 1.
- Remote Peering Connection OCID: Enter the RPC OCID from Site 1, obtained above.
- Click Establish Connection.
The Peering Status changes to Peered. This change may take a few minutes.
Parent topic: Preparing a Disaster Recovery Environment
Creating Routing Tables for Dynamic Routing Gateways
For subnets in Site 1 to communicate with subnets in Site 2, you should create routing entries in both directions.
Parent topic: Preparing a Disaster Recovery Environment
Creating the Security Lists for Subnets
After creating routes between the subnets, you need to create security lists for each network and add them to the corresponding subnet.
- Log in to the Oracle Cloud Infrastructure Console for your tenancy.
- Select Networking and click Virtual Cloud Networks.
- From the list of resources, select Security Lists.
- Select a security list. For example,
db-seclist. - From the list of resources, select Ingress Rules.
- Click Add Ingress Rules.
- Enter the information, as described in Table 10-14 and Table 10-15.
- Click Add Ingress Rule.
- From the list of resources, select Egress Rules.
- Click Add Ingress Rules.
- Enter the information, as described in Table 10-14 and Table 10-15.
- Click Add Ingress Rule.
Table 10-16 Security List for Site 1
| List | Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range | Type |
|---|---|---|---|---|---|---|---|---|
|
db-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
TCP |
1521 |
|||
|
db-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
TCP |
6200 |
|||
|
Security List for Private Subnet for VCN |
Ingress |
CIDR |
10.1.11.0/24 |
31444 |
||||
|
Pv-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
TCP |
111 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
TCP |
2048-2050 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
UDP |
111 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.1.11.0/24 |
UDP |
2048 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.1.11.0/24 |
TCP |
111 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.1.11.0/24 |
TCP |
2048-2050 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.1.11.0/24 |
UDP |
111 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.1.11.0/24 |
UDP |
2048 |
Table 10-17 Security List for Site 2
| List | Rule Type | Type | Source CIDR | Destination CIDR | Protocol | Source Port Range | Destination Port Range | Type |
|---|---|---|---|---|---|---|---|---|
|
db-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
1521 |
|||
|
db-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
6200 |
|||
|
Security List for Private Subnet for VCN |
Ingress |
CIDR |
10.0.11.0/24 |
31444 |
||||
|
Pv-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
111 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
TCP |
2048-2050 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
UDP |
111 |
|||
|
Pv-seclist |
Ingress |
CIDR |
10.0.11.0/24 |
UDP |
2048 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.0.11.0/24 |
TCP |
111 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.0.11.0/24 |
TCP |
2048-2050 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.0.11.0/24 |
UDP |
111 |
|||
|
Pv-seclist |
Egress |
CIDR |
10.0.11.0/24 |
UDP |
2048 |
Parent topic: Preparing a Disaster Recovery Environment
Checking the Site Connectivity
After configuring the Dynamic Gateway and Security Lists, use the Network Path Analyzer to validate inter-region connectivity.
Parent topic: Preparing a Disaster Recovery Environment