Oracle Access Manager and Single Sign-On
Oracle Access Manager is a Java Platform, Enterprise Edition (Java EE)-based enterprise-level security application that provides restricted access to confidential information and centralized authentication and authorization services. Oracle Access Manager, a component of Oracle Fusion Middleware, is a Single Sign-On solution for authentication and authorization.
Authentication servers enable an application to authenticate users by means of a shared authentication token or authentication authority. That means that a user authenticated for one application is automatically authenticated for all other applications within the same authentication domain.
Forms applications use a single sign-on solution only for obtaining database connection information from Oracle Internet Directory or Oracle Platforms Security Services (OPSS). Exiting a Forms application does not perform a single sign-on logout unless the application has been coded with one of the SSO logout features introduced in Oracle Forms 12c. Similarly, logging out of a single sign-on session does not terminate an active Forms session unless the application has been coded with one of the Forms SSO logout features. The database session exists until the Forms Runtime (for example, frmweb.exe) on the server terminates, usually by explicitly exiting the form.
Oracle Forms Services provides out-of-the box support for single sign-on for as many Forms applications as run by the server instance with no additional coding required in the Forms application.
Note:
Oracle Forms Services applications run in a single sign-on environment using the OID (or OPSS) and authentication server combinations. Supported versions can be found in the Product Certification Guide.
- Certifications, see Oracle Fusion Middleware Supported System Configurations.
- Oracle Access Manager, see Understanding Single Sign-On with Access Manager.
- Oracle Internet Directory, see Configuring SSO Providers for Oracle Identity Manager.
- Oracle Platform Security Services, see Introduction to Oracle Platform Security Services.
If you redeploy the forms JavaEE application and override its context root servlet alias when running the custom Forms application in single sign on mode, you might run into the following error:
FRM-60209 error obtaining credentials from Oracle Platform
Security Services: missing resource
FRM-60209 error obtaining credentials from Oracle Platform Security
Services in oracle.forms.servlet.LBServletBundle
- Deploy the custom Forms JavaEE applications.
In this example, we use sales and salesservlet as the context root and application, respectively.
context-root forms-> sales servlet-alias frmservlet-> salesservlet - Create the mappings in the forms.conf file.
Here is an example of how to do this for the sales application.
<Location /sales/> SetHandler weblogic-handler WebLogicCluster example.com:9010 DynamicServerList OFF </Location> - Add the following in the Forms OAM Registration meta-data files,
FormsOAMRegRequest2Ports.xmlandFormsOAMRegRequest.xml, stored in$ORACLE_HOME/forms/provisionthe directory.Entry Change this... To this... protectedResourcesList<protectedResourcesList> <resource>/forms/frmservlet?*oamMode=true*</resource> <resource>/reports/rwservlet/*</resource> </protectedResourcesList><protectedResourcesList> <resource>/forms/frmservlet?*oamMode=true*</resource> <resource>/sales/salesservlet?*oamMode=true*</resource> <resource>/reports/rwservlet/*</resource> </protectedResourcesList>excludedResourcesList<excludedResourcesList> <resource>/forms/frmservlet?*ifcmd=startsession*</resource> <resource>/forms/lservlet*</resource> <resource>/forms/lservlet/**</resource> <resource>/forms/java/**</resource> <resource>/forms/html/**</resource> </excludedResourcesList><excludedResourcesList> <resource>/forms/frmservlet?*ifcmd=startsession*</resource> <resource>/forms/lservlet*</resource> <resource>/forms/lservlet/**</resource> <resource>/forms/java/**</resource> <resource>/forms/html/**</resource> <resource>/sales/salesservlet?*ifcmd=startsession*</resource> <resource>/sales/lservlet*</resource> <resource>/sales/lservlet/**</resource> <resource>/sales/java/**</resource> <resource>/sales/html/**</resource> </excludedResourcesList> - Perform the partner app registration using the
frmconfighelperscripts. - Grant the following OPSS grants. Connect to WLST and run the following:
grantPermission(codeBaseURL="file:${domain.home}/servers/${weblogic.Name}/tmp/ _WL_user/salesapp_14.1.2/-", permClass="oracle.security.jps.service.keystore.KeyStoreAccessPermission", permTarget="stripeName=salesapp,keystore=formsks,alias=*,Action=*") - Restart the WebLogic servers.
Single Sign-On Components used by Oracle Forms
There are various Single Sign-On components in Oracle Fusion Middleware that are involved when running Forms applications in single sign-on mode with an authentication server.
The following figures, describes the high level overview of the various components involved in the single sign-on deployment setup of Forms Services.
Figure -26 Components involved in the Single Sign-On Deployment Setup of Forms Services with OPSS as the Forms Identity Store
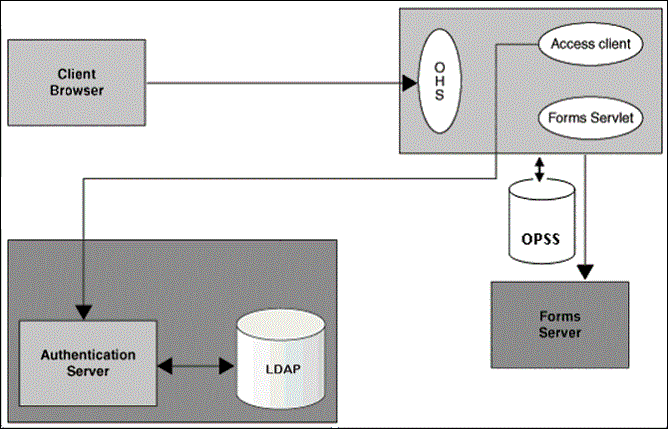
Description of "Figure -26 Components involved in the Single Sign-On Deployment Setup of Forms Services with OPSS as the Forms Identity Store"
Figure -27 Components involved in the Single Sign-On Deployment Setup of Forms Services with (Oracle Internet Directory) OID Identity as the Forms Identity Store
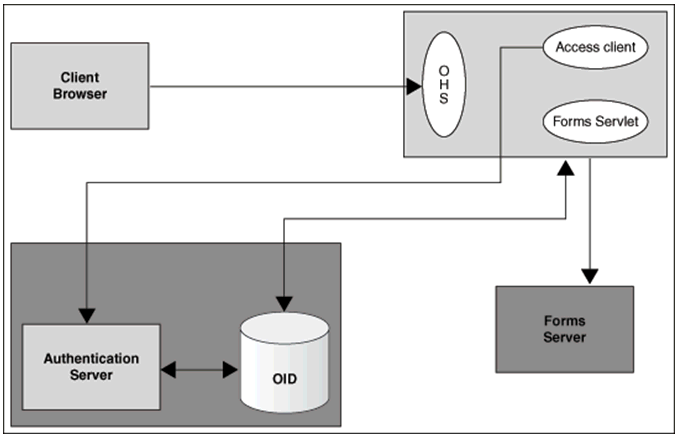
Description of "Figure -27 Components involved in the Single Sign-On Deployment Setup of Forms Services with (Oracle Internet Directory) OID Identity as the Forms Identity Store"
Following is the description of the components mentioned in the above figure:
-
Authentication Server
-
Oracle Access Manager (OAM Server) - Oracle FMW authentication server that provides a full range of security functions, including Web single sign-on, authentication and authorization. When running Forms Services, Oracle Internet Directory can be used as the Identity Store. Oracle Access Manager can use
webgateas the access client configured with Oracle HTTP Server.
-
-
Access Client
-
webgate- WebGate provides single sign-on support. It intercepts incoming HTTP requests and forwards them to the Access Server for authentication. Oracle Forms Services can usewebgateas an access client with OAM server.
-
-
Forms Identity Store
-
It is the storage for Forms Resource Access Descriptors, which contains the Forms Server database connection information. Oracle Platform Security Services (OPSS) or Oracle Internet Directory (OID) can be used as a Forms Identity Store. Oracle Platform Security Services (OPSS) is set as the default Forms Identity Store, but Forms administrators can use Oracle Enterprise Manager to change the Forms Identity Store to Oracle Internet Directory (OID) and back to Oracle Platform Security Services.
-
-
OAM Server Identity Store - Oracle Internet Directory (OID) is an LDAP server that is used as the Identity store by the Oracle Access Manager (OAM) authentication server and the Forms applications. Any LDAP server certified for use with OAM can be used in an Oracle Forms environment when the Identity Store for Forms is OPSS and not OID.
Note:
When Oracle Internet Directory (OID) is used as the Forms Identity Store, the same Oracle Internet Directory (OID) instance should be set as the Oracle Access Manager's primary identity store.
-
Forms Servlet - The Oracle Forms Services component accepts the initial user request to start a Forms application. The Forms servlet detects if an application requires authentication, directs the request to the authentication server and accesses the Oracle Internet Directory to obtain the database connect information.
Authentication Flow
The following figures describes the authentication flow of authentication server support in Oracle Forms, the first time the user requests an application URL that is protected by authentication server:
Figure -28 Authentication Flow for First Time Client Request
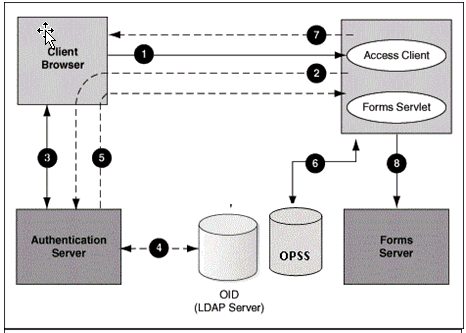
Description of "Figure -28 Authentication Flow for First Time Client Request"
Figure -29 Authentication Flow for First Time Client Request
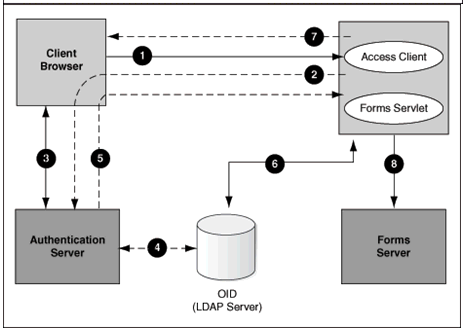
Description of "Figure -29 Authentication Flow for First Time Client Request"
These steps describe the authentication flow mentioned in the above figure:
- The user requests a Forms URL similar to
http(s)://<hostname>:<port>/forms/frmservlet?config= <application>&...Note:
Use the HTTP port number in the Forms URL for Forms applications that use single sign-on. The Forms URL is similar tohttp://<host name>:<http port>/forms/frmservlet?config=ssoappwhere<ssoapp>is the name of the section in forms configuration file with single sign-on (ssoMode) enabled. - The Forms servlet redirects the user to the authentication server login page.
- The user provides user name and password through the login form.
- The password is verified through Oracle Internet Directory (LDAP Server).
- The user is redirected to the URL with
sso_useridinformation. - The Forms servlet retrieves the database credentials from Forms Identity Store.
- The Forms servlet sets the
sso_useridparameter in the Run form session and permits the applet to connect to the Forms listener servlet. - The Forms servlet starts the Forms server.
Figure -30 describes the authentication flow of single sign-on support in Oracle Forms Services when a user, authenticated through another partner application, requests an application that is protected by authentication server.
Figure -30 Authentication Flow for Subsequent Client Requests
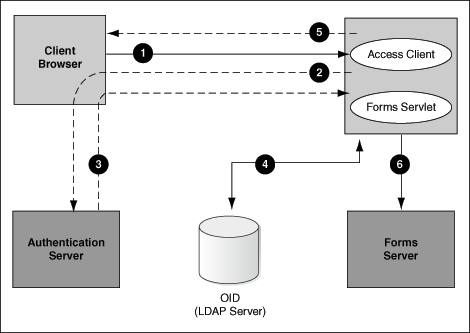
Description of "Figure -30 Authentication Flow for Subsequent Client Requests"
These steps describe the authentication flow mentioned in the above figure:
- The user requests the Forms URL.
- The Forms servlet redirects the user to the authentication server and its login page.
- The user is redirected to the URL with the
sso_useridinformation. - The Forms servlet retrieves the database credentials from the Forms Identity Store.
- The Forms servlet sets the
sso_useridparameter in the Runform session and the applet connects to the Forms listener servlet. - The Forms servlet starts the Forms server.