1 About Network Integrity
Network Integrity enables you to keep two data sources (such as an inventory system and a live network) synchronized, improving data accuracy, which increases your service provisioning success rate. It enables better business planning, based on having an accurate view of your inventory, and supports scheduled or ad-hoc audits to ensure alignment of inventory with your network. Network Integrity can also be used as a convenient way to load network data into your inventory system.
How Network Integrity Works
Network Integrity compares two sets of data to identify and facilitate the correction of differences between the data sets.
Use Network Integrity to discover network data (such as network elements, resources, and services) using discovery or assimilation scans. Use Network Integrity to import inventory data using an import scan. You can filter scan results by specifying search criteria.
The discovered data is compared with the imported data to generate lists of discrepancies, which are instances where the data from the two data sources do not match. Discrepancies can be shown for relevant entities of the device or for other objects. You can select an entity to show a side-by-side comparison of the discovered view and the inventory view. You can then resolve an individual data discrepancy or several data discrepancies.
You can even generate reports from the discovery, import, or discrepancy information.
Figure 1-1 illustrates a typical Network Integrity discovery and discrepancy resolution process flow.
Figure 1-1 Network Integrity Typical Process Flow
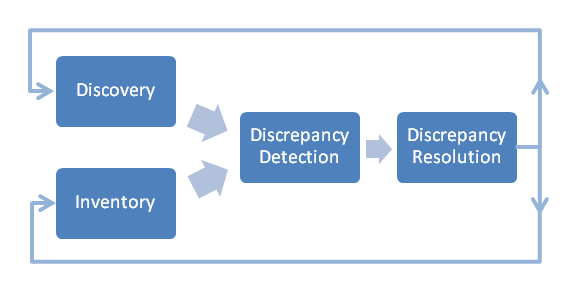
Description of "Figure 1-1 Network Integrity Typical Process Flow "
The typical Network Integrity process flow is:
-
Run an import scan to import inventory data from an inventory system.
-
Run a discovery or assimilation scan, to discover or assimilate network data from a network system, with the Detect Discrepancies option enabled.
Elements, physical resources, and logical resources in the network are discovered by scanning Network Elements (NEs), Element Management Systems (EMSs), and Network Management Systems (NMSs). For example, you poll an NE to find all ports and to determine whether each port is free or assigned, or you poll an optical EMS to find unused ports.
-
Discovered or assimilated entities are matched with the inventory view of networks and services and generate discrepancies. For example, you match the discovered NE and each port on it with objects in inventory.
See "Managing Scans and Viewing Scan Results" for more information.
-
Discrepancies are evaluated in the Network Integrity UI, or by viewing generated reports, which can be studied to obtain a deeper understanding of the inventory discrepancies.
For more information, see "About Discrepancy Detection, Review, and Resolution" and "About the Reporting Solution".
Figure 1-2 Network Integrity UI View of Discrepancies
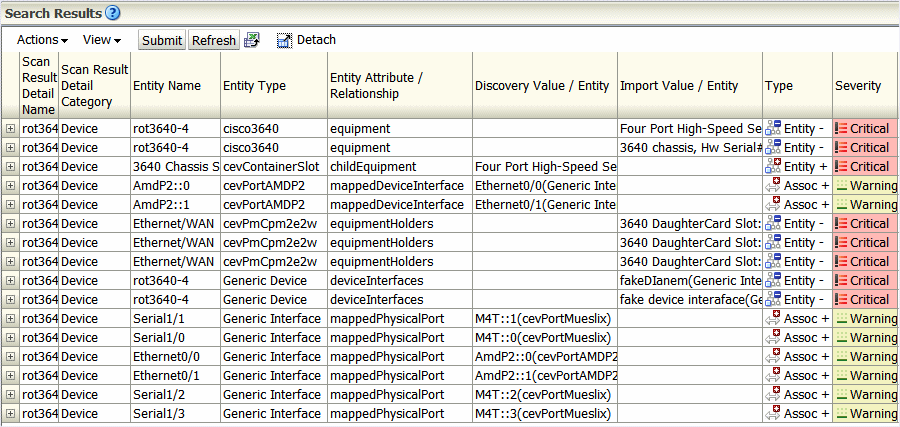
Description of "Figure 1-2 Network Integrity UI View of Discrepancies " -
Discrepancies are corrected using Network Integrity. You can make individual or bulk corrections. Network Integrity synchronizes the discovered data with the inventory reference data. You can assign, rank and annotate discrepancies. Using the UI to perform synchronization reduces the likelihood of errors, compared to making changes manually, and better supports a multi-user environment.
Benefits of Network Integrity
Network Integrity offers a number of benefits for optimizing resource use and increasing provisioning efficiency.
Identifying Stranded Assets
Network Integrity allows you to locate stranded network assets. These are resources that you have, but which don't appear in your inventory. You save capital investment by using all existing resources effectively, rather than obtaining new resources prematurely.
Minimizing Fallout in Flow Through Service Fulfillment
Maintaining an accurate representation of your network means that any service fulfillment activities are more likely to complete successfully, and as designed, without going to fallout, or requiring manual intervention. This means that services are delivered more quickly, and less expensively.
Ensuring Inventory Accuracy for Operations And Planning
With an accurate view of your network, you can plan and provision new services effectively and efficiently. Network element issues can be pinpointed faster and resolved more efficiently.
Automating Manual and Error Prone Procedures
Provisioning errors due to incorrectly identified or unavailable network resources are costly to fix and detrimental to customer satisfaction. Network Integrity allows you to determine where the problems are, and what the root cause is. It then allows you to efficiently resolve these issues (which can be an error-prone activity if performed manually).
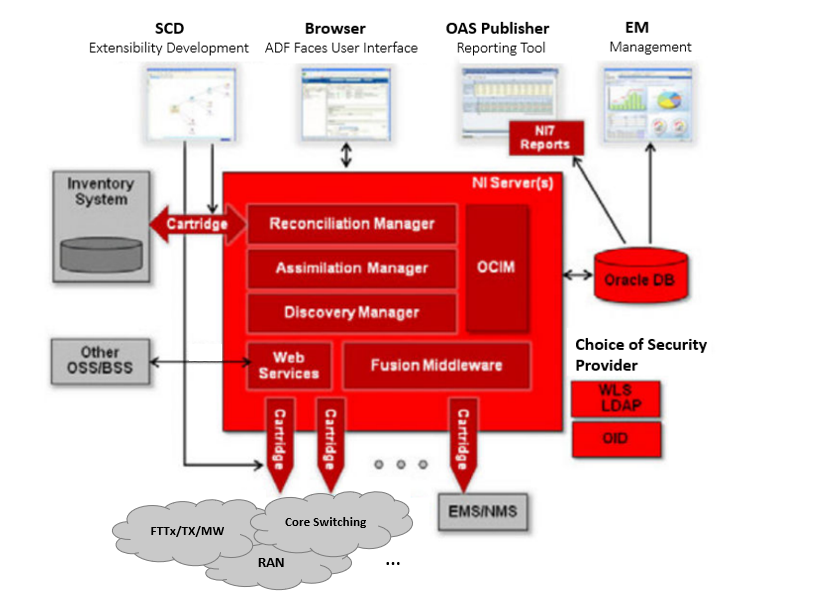
About the Network Integrity Architecture
Figure 1-3 outlines the Network Integrity architecture.
Network Integrity runs on Oracle WebLogic Server, and includes the following features and functions:
-
Support for cartridges developed in Oracle Communications Service Catalog and Design - Design Studio, to provide extensibility. See "Using Service Catalog and Design - Design Studio for Network Integrity".
-
A browser-based web UI based on Oracle Fusion Middleware ADF Faces technology which provides a single user experience for network discovery and data reconciliation. The web UI supports localization. See "About the Network Integrity UI".
-
Reporting provided by Oracle Business Information (BI) Publisher (optional) or other third-party solution. See "About the Reporting Solution".
-
Reference implementations are provided against Oracle Communication Unified Inventory Management (UIM) and MetaSolv Solution (MSS) for the import of data and resolution of discrepancies; support for other third-party systems is possible through extensibility. See "Integrating with Inventory Systems".
-
Support for the Oracle Communications Information Model, which is based on the TM Forum's Information Framework (SID). See "Integrating with UIM".
Note:
Network Integrity 7.4.0 supports Oracle Communications Information Model 7.3.0. For specific technical details about the Oracle Communications Information Model and the Network Integrity information model, see Oracle Communications Information Model Reference and Network Integrity Information Model Reference.
Oracle Communications Information Model Reference and Network Integrity Information Model Reference are located in Network Integrity Developer Documentation on the Oracle software delivery website.
-
Runs on Oracle Fusion Middleware platform. See "About Oracle Fusion Middleware Platform".
-
SOA-based JEE compliant web services API to facilitate customized solutions for external management of Network Integrity. See "Managing Network Integrity Using the Web Services API".
-
Support for application and database clustering for scalability and high availability.
-
Able to integrate with external Security Providers, preventing replication of user accounts and credentials in Network Integrity. See "About User and Identity Management".
About the Network Integrity UI
You use the browser-based web UI to carry out discovery and reconciliation by configuring and scheduling scans, reviewing scan results, and reviewing and resolving data discrepancies.
Features offered by the Network Integrity web UI include:
-
Integrated search functionality: A flexible search function supporting both basic and advanced searches for objects in Network Integrity such as scans. Advanced searches support the specification of multiple values for a particular field. This search functionality provides comprehensive historical results access with filtering options.
-
Intuitive functions and layout: The Network Integrity UI supports a robust, predictable range of user interactions, which make it easy to learn and use. Icons trigger functions such as object creation and deletion. Menus are accessed as standard drop-downs, or by right-clicking on objects. Drag and drop is supported and data sorting is provided in all tables. Table columns can be moved, resized and hidden. Multiple object selection is supported. UI panels can be collapsed and expanded, detached and re-attached.
-
Links panel: Frequently used web links can be placed in the Links panel by the system administrator. For example, you can store links to an inventory system login page or to the technical specifications for equipment on the network.
-
Context-sensitive online Help: The Network Integrity UI provides field-level online Help that offers detailed content on supported functions and features.
-
Internationalization and localization: The Network Integrity UI supports custom localization, allowing the GUI to be presented in different languages.
Using Service Catalog and Design - Design Studio for Network Integrity
Service Catalog and Design - Design Studio is a design-time platform and graphical service creation environment that enables you to design, build, and deploy cartridges. Design Studio supports multiple Oracle Communications applications including Network Integrity. You can use the same Design Studio instance for multiple Oracle Communications products.
Design Studio is based on Eclipse, a popular, open-source development environment. Design Studio provides an integrated development environment to support plug-in configuration and customizations.
You use Design Studio for Network Integrity to develop and deploy Network Integrity cartridges that extend Network Integrity for various environments, applications, or implementations. Network Integrity's cartridge-based architecture promotes cartridge and artifact reuse and extensibility. For example, you can extend Network Integrity with cartridge-based Actions and Address Handlers. Each cartridge is created or customized using Design Studio GUI wizards and editors that:
-
Validate the integrity of configurations.
-
Generate cartridge Java code and other cartridge artifacts.
-
Build the cartridge code.
-
Package the cartridge artifacts into deployable files.
Although many of the cartridge artifacts are produced automatically, you may have to manually write some Java code to complete the cartridge implementation. Cartridges offered by Network Integrity offer:
-
Network discovery
-
Inventory import
-
Data assimilation
-
Discrepancy detection
-
Discrepancy resolution
About Network Integrity Security
Network Integrity conforms to Oracle security standards. Network Integrity should be installed as securely as possible and configured to listen to, read, and write data as securely as possible, to protect the integrity of the information it accesses.
"Network Integrity Security Overview" in Network Integrity Security Guide outlines all Network Integrity security features and explains how to install and configure Network Integrity securely.