Active Directory-based Call Routing
A large percentage of enterprises use call servers with Active Directory (Domain Controller) such as Media Servers, Exchange Servers, and Lync Servers. For enterprises that integrate these servers in parallel to their existing communications infrastructure, or transition from their legacy Private Branch Exchange (PBX) to these types of servers, Active Directory becomes a more efficient and cost-effective way of routing the incoming calls within the core enterprise network.
Clients using Microsoft servers such as a Lync Server deploy their own URI. Therefore, a user in a network with both a desk phone and a Lync client has an IP PBX extension/URI for the desk phone, and a different URI for the Lync client. Currently, all PSTN traffic is sent by default to a legacy PBX in the core network. If the PBX does not recognize the extension/URI, the PBX forwards it to the Lync client. Sending traffic to the PBX first and then to the Lync Server can be costly in terms of compute resources and licensing fees. Routing all incoming sessions from a SIP trunk to the Lync Server first and then to a PBX can be costly.
As a solution, the Oracle® Enterprise Session Border Controller (E-SBC) initiates a query to the Active Directory to initially determine the type of incoming call. The E-SBC then stores data used to facilitate the routing decision of the call (performed by Lightweight Directory Access Protocol (LDAP)) and routes the call the first time to the applicable destination (PBX or Lync Server).
In scenarios where a user has both a Lync phone and a legacy PBX phone, calls destined for the Lync phone number can be routed to the PBX phone number, or calls destined for the PBX phone number can be routed to the Lync phone number. The destination depends on the current E-SBC configuration. The E-SBC uses the information stored in the enterprise’s Active Directory, compares it to the ESD configuration and then determines which phone number to utilize for the destined user.
Note:
The Active Directory-based call routing feature supports confidential and secure LDAP traffic support by using SSL/TLS (LDAPS).Active Directory-based call routing is a feature of the E-SBC that facilitates the routing of incoming calls to the appropriate destinations within the Enterprise core network. The E-SBC LDAP query to the Active Directory yields whether or not the phone number is associated with a call Server or the PBX.
When the
E-SBC receives an
inbound SIP INVITE over a SIP Trunk (![]() ), it checks the current LDAP configuration in the
E-SBC. Depending on this
configuration, the
E-SBC then accesses the
Enterprise’s Active Directory to search for the applicable number being called
via an LDAP query (
), it checks the current LDAP configuration in the
E-SBC. Depending on this
configuration, the
E-SBC then accesses the
Enterprise’s Active Directory to search for the applicable number being called
via an LDAP query (![]() ). When the query has found the number to forward the
call, the
E-SBC routes the call
directly to the call server client (
). When the query has found the number to forward the
call, the
E-SBC routes the call
directly to the call server client (![]() ) or to the IP PBX phone (
) or to the IP PBX phone (![]() ) and
) and
![]() ) as shown in the illustration below.
) as shown in the illustration below.
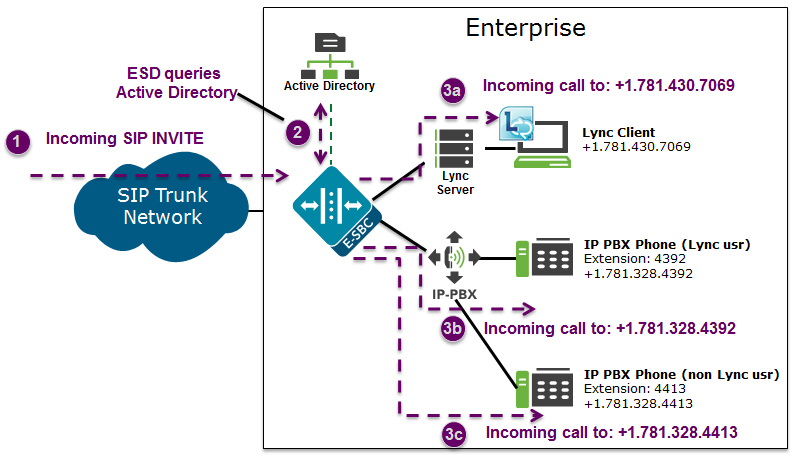
The Enterprise is responsible for migrating phone numbers from the legacy PBX to the call server by making the necessary updates in their Active Directory in order for the E-SBC to route the call properly. In the illustration above, the IP PBX extension (4392) is the primary telephone number (+1.781.328.4392); a secondary transition number (+1.781.430.7069) is assigned to Lync.
LDAP in the Oracle® Enterprise Session Border Controller
Lightweight Directory Access Protocol (LDAP) is the Protocol that the Oracle® Enterprise Session Border Controller uses to perform queries to the Enterprise’s Active Directory to determine where to route incoming calls (to the call server or the IP PBX) in the Enterprise network. Session requests and responses are sent/received based on the Oracle® Enterprise Session Border Controller’s LDAP routing configuration. LDAP determines the destination (call server user or non-call server user) and forwards the call accordingly.
The Oracle® Enterprise Session Border Controller, using LDAP, performs the following on an inbound call:
- Creates an LDAP search filter based on the dialed number and the configured LDAP attributes.
- Sends an LDAP search query to the configured LDAP Server.
- Creates a route list based on the query response received from the LDAP Server.
- Routes calls to both the call server and the IP PBX. The routing order is dependent on the LDAP attribute configuration and/or whether there was an exact match for the dialed phone number in the Enterprise’s Active Directory for the call server or the IP-PBX.
Note:
You configure LDAP Servers, filters, and local policy routing using the ACLI objects and attributes. For more information about configuring LDAP, see Configuring LDAP.The Oracle® Enterprise Session Border Controller keeps a permanent LDAP session open to all configured call servers. It sends an LDAP bind request on all established connections, to those servers. The first call server is considered the primary LDAP Server, and all others are secondary LDAP servers. If a query request sent to the primary server fails, the Oracle® Enterprise Session Border Controller sends the request to the next configured LDAP Server, until the request is successful in getting a response. If no response is received by the Oracle® Enterprise Session Border Controller and the Oracle® Enterprise Session Border Controller cannot find another route successfully, (all Oracle® Enterprise Session Border Controller configured attributes have been exhausted (local policies, policy attributes, etc.)), it sends a busy to the caller.
LDAP performs call routing based on LDAP attributes configured on the Oracle® Enterprise Session Border Controller. The route-mode attribute setting determines how LDAP handles the called number when accessing the Enterprise’s Active Directory. Routing modes can be set to any of the following:
- Exact-match-only (default)
- Attribute-order-only
- Exact-match-first
The following paragraphs describe each of these route-modes.
Exact-match-only
If the LDAP route-mode attribute is set to exact-match-only, the Oracle® Enterprise Session Border Controller performs as follows.
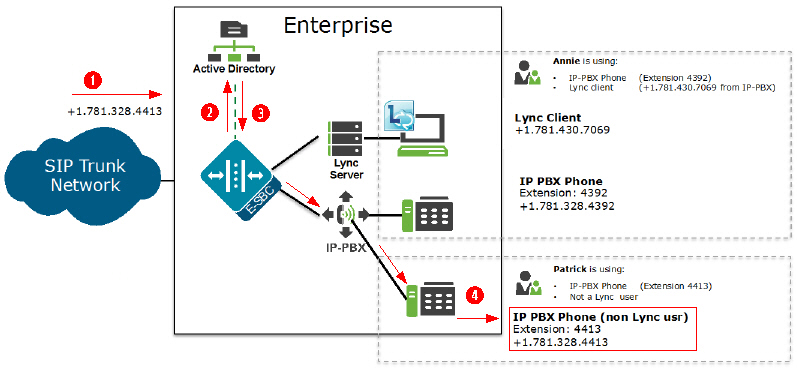
The Oracle® Enterprise Session Border Controller receives an incoming call to the Enterprise network. If the LDAP route-mode attribute on the Oracle® Enterprise Session Border Controller is set to exact-match-only, LDAP queries the Active Directory to find the number that matches exactly to the incoming number. If the number is found, the Oracle® Enterprise Session Border Controller forwards the call to the client’s applicable phone in the Enterprise network.
| Number | Description |
|---|---|
| ① | Call comes into the Enterprise network (+1.781.328.4413) |
| ② | Using the configured route-mode of exact-match-only, LDAP queries the exact matching number in the Enterprise’s Active Directory. |
| ③ | The Active Directory finds the matching number and that number is included in the response to the LDAP query. |
| ④ | The Oracle® Enterprise Session Border Controller forwards the call to the destination phone number (same number as the number that initially called into the Enterprise in Step 1 (+1.781.328.4413)). |
Attribute-order-only
If the LDAP route-mode attribute is set to attribute-order-only, the Oracle® Enterprise Session Border Controller performs as follows.
The order in which the LDAP attributes are configured on the Oracle® Enterprise Session Border Controller determines the priority of each route. If an incoming call is destined for the IP-PBX , but the attribute name for a Lync client is configured first, the Oracle® Enterprise Session Border Controller uses the corresponding next hop (Lync Server) to create the first route in the route list.
An entry in an LDAP search response must have at least one attribute that it matches in the Active Directory.
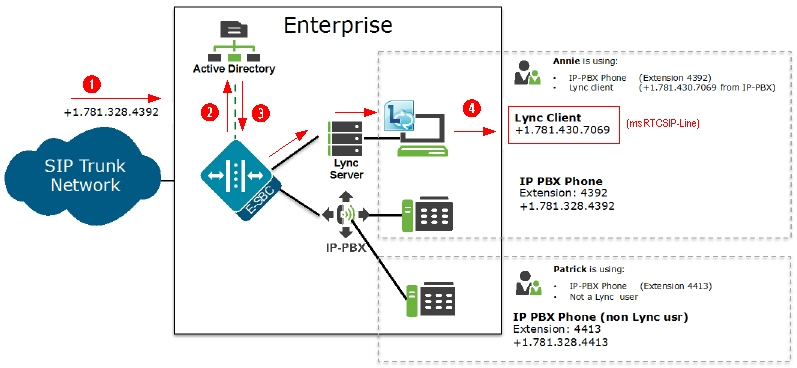
For example, the incoming phone number could be +1.781.328.4392 (which matches the IP-PBX phone number), and the attribute name msRTCSIP-Line (Lync attribute) in the response could be +1.781.430.7069 (Lync phone number). A route is created for the Lync phone number, even though the incoming phone number matches the IP-PBX phone number, since the msRTCSIP-Line attribute was configured first. Therefore, the Oracle® Enterprise Session Border Controller forwards the call to the Lync destination.
Likewise, if an Enterprise uses the same phone number for both Lync and IP-PBX phones, and the attribute-name msRTCSIP-Line is configured first (a Lync attribute), the Oracle® Enterprise Session Border Controller uses the corresponding next hop (Lync Server) to create the first route in the route list.
| Number | Description |
|---|---|
| ① | Call comes into the Enterprise network (+1.781.328.4392) |
| ② | Using the configured route-mode of attribute-order-only, LDAP queries the Active Directory for the matching number. |
| ③ | The Active Directory responds with the phone
number associated with the first configured LDAP attribute (+1.781.430.7069).
In the illustration above, the number was associated with a Lync Client (msRTCSIP-Line) that was configured first in the LDAP configuration. |
| ④ | The Oracle® Enterprise Session Border Controller forwards the call to the applicable destination phone number from the Active Directory response. (+1.781.430.7069). |
If you configure the attribute name msRTCSIP-Line first, the Oracle® Enterprise Session Border Controller uses the corresponding next hop (Lync Server) to create the second highest priority route in the route list. For example, the dialed telephone number could be +1.781.328.4392 (IP-PBX phone number), and the attribute-name msRTCSIP-Line in the response could be +1.781.430.7069 (Lync phone number). A route is created for the Lync phone number, even though the dialed telephone number is the PBX phone number.
Exact-match-first
If the LDAP route-mode attribute is set to exact-match-first, the Oracle® Enterprise Session Border Controller performs as follows.
When the LDAP query is sent to the Active Directory, the first exact match of the incoming phone number that the LDAP query finds in the Directory, is the number whose corresponding route gets the highest priority in the route list. For all other routes configured on the Oracle® Enterprise Session Border Controller, the ordering of LDAP attributes in the LDAP configuration determines the priority for each route.
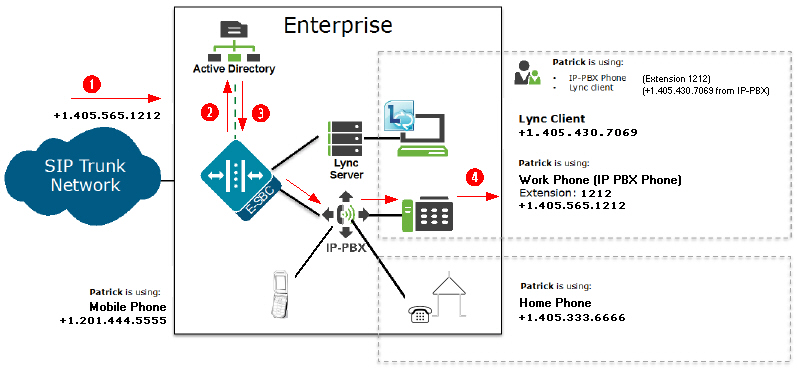
For example, if the incoming number is +1.405.565.1212, and the Active Directory includes a configured mobile number first (+1.201.444.5555), a home number second (+1.405.333.6666) , and a work number third(+1.405.565.1212), the LDAP query searches the mobile number first, then the home number, then finds the exact match on the work phone number. The Active Directory responds with the destination information for the work phone number and the Oracle® Enterprise Session Border Controller creates a route list with this exact phone number, and then forwards the call accordingly.
| Number | Description |
|---|---|
| ① | Call comes into the Enterprise network (+1.405.565.1212) |
| ② | Using the configured route-mode of exact-match-first, LDAP queries the Active Directory for the matching number. |
| ③ | The LDAP query searches throughout the Active
Directory until it finds the first exact match on the number. Active Directory
responds with the exact phone number associated with the incoming number
(+1.405.565.1212).
In the illustration above, the number was associated with the work phone. |
| ④ | The Oracle® Enterprise Session Border Controller forwards the call to the applicable destination phone number from the Active Directory response. (+1.405.565.1212). |
LDAP Messages
When you enable LDAP message logging in the Active Directory, the Oracle® Enterprise Session Border Controller (E-SBC) sends LDAP messages to the sipdldap.log. This log records all received and sent LDAP messages. Messages are in ASCII encoded binary format.
Additionally, when LDAP is invoked for routing, the LDAP messages display in the GUI under the Monitor and Trace tab. For more information about viewing LDAP messages in the GUI, see the Web GUI User Guide.
Note:
The E-SBC also supports transmitting LDAP messages using the IPFIX Protocol for the Palladion Mediation Engine.LDAP Failure Events
If an incoming session to a primary phone number routed to Lync fails, the phone number is routed to the IP PBX. If failures occur during LDAP queries for all LDAP Servers, the Oracle® Enterprise Session Border Controller logs the failure to the sipdldap.log, and proceeds with normal configured routing policies, if available.
Note:
The Oracle® Enterprise Session Border Controller always establishes the TCP/TLS connection towards the configured LDAP server(s). If a TCP connection fails, the Oracle® Enterprise Session Border Controller continues to attempt to re-establish the connection.An LDAP connection failure can be due to any one of the following events:
- Oracle® Enterprise Session Border Controller receives a CANCEL message (LDAP connection termination). The Oracle® Enterprise Session Border Controller detects this if it receives or issues an 'unbind' operation. The session is then closed down at TCP/TLS.
- Oracle® Enterprise Session Border Controller receives a call failure message from Lync (TCP/TLS socket termination). If either side receives a finish message (FIN) or reset message (RST), the TCP socket closes per standard behavior, which triggers the LDAP layer to detect connection failure. The Oracle® Enterprise Session Border Controller fails over to a secondary LDAP Server, if configured; otherwise it periodically attempts to reconnect to the Primary LDAP Server.
- Oracle® Enterprise Session Border Controller is unreachable and SIP session towards Lync times out. User is enabled for Lync but the Lync Server is unreachable by the Oracle® Enterprise Session Border Controller so a timeout occurs. When consecutive LDAP queries timeout, the Oracle® Enterprise Session Border Controller concludes that the LDAP session has failed, and then proceeds to terminate the TCP/TLS connection.
The number of consecutive queries that timeout before a connection is considered failed, and the number of successive query timeouts for each LDAP Server can be set via configuration.
Oracle® Enterprise Session Border Controller Limitations using LDAP
The Oracle® Enterprise Session Border Controller uses LDAP in the Active Directory when determining the destination of incoming calls. However, the Oracle® Enterprise Session Border Controller has the following limitations when using LDAP:
- Supports LDAP sessions over the Oracle® Enterprise Session Border Controller media interfaces only (i.e., not on wancom0).
- Supports LDAPv3 only.
- Establishes a session over the following connections only:
LDAP over TCP - default
LDAP over TLS (LDAPS)
Configuring LDAP
LDAP is the Protocol that the Active Directory uses for general interaction between and LDAP client and an LDAP server. You can configure the LDAP Server(s) in your network, and set the filters and the local policy that the LDAP Server uses when handling inbound Lync and PBX calls in the Enterprise core network.
You can use the following objects in the ACLI to configure LDAP.
| Object | XML Tag | ACLI Path | Description |
|---|---|---|---|
| ldap-config | ldapConfig | session-router->ldap-config | Configures the LDAP functionality on the
Oracle® Enterprise Session Border Controller (i.e., name, state, LDAP servers, realm,
authentication mode, username, password, LDAP search filters, timeout limits,
request timeouts, TCP keepalive, LDAP security type, LDAP TLS profile, and LDAP
transactions).
Note: This is a multiple-instance object. |
| ldap-transaction | ldapTransaction | session-router->ldap-config-> ldap-transaction | Configures the application transaction type for
LDAP, determines route priority in the route list, and configures the LDAP
configuration attributes. You configure this object for LDAP search queries in
call routing.
Note: This is a multiple-instance object. |
| ldap-cfg-attributes | ldapCfgAttributes | session-router->ldap-config-> ldap-transaction->ldap-cfg-attributes | Configures the Active Directory attribute name,
next hop for routing SIP requests, the realm for the next hop, a regular
expression pattern, and a format for the attribute value. You configure this
object for LDAP search queries in the Active Directory.
Note: This is a multiple-instance object. |
| policy-attributes | policyAttributes | session-router->local-policy-> policy-attributes | Configures the ldap: prefix with the name of
the ldap-config. This allows the
Oracle® Enterprise Session Border Controller to send LDAP queries to the Active Directory
server(s) configured in the ldap-config element whenever there is a match for
the corresponding local-policy.
Note: An ldap-config with the LDAP name specified for this parameter must be configured for the next hop. An LDAP next hop is supported only for SIP to SIP calls. This is a multiple-instance object. |
Configuring ldap-config
You use the ldap-config object in the ACLI to create and enable an LDAP configuration on the ESD.
To configure ldap-config:
Configure ldap-transactions
Use the ldap-transactions object in the ACLI to configure the application transaction type for Lightweight Directory Access Protocol (LDAP), to determine route priority in the route list, and to configure the LDAP configuration attributes for LDAP search queries in call routing.
Configuring ldap-cfg-attributes
You use the ldap-cfg-attributes object in the ACLI to configure the Active Directory attribute name, next hop for routing SIP requests, the realm for the next hop, a regular expression pattern, and a format for the attribute value. You configure this object for LDAP search queries in the Active Directory.
To configure ldap-cfg-attributes:
Configuring policy-attributes
You use the policy-attributes object in the ACLI to configure the ldap: prefix with the name of the ldap-config. This allows the ESD to send LDAP queries to the Active Directory server(s) configured in the ldap-config element whenever there is a match for the corresponding local-policy.
Note:
An ldap-config with the LDAP name specified for this value must be configured for the next hop. An LDAP next hop is supported only for SIP to SIP calls.To configure policy-attributes for LDAP:
LDAP Error Messages
The ESD displays errors messages if the LDAP configuration objects are not properly configured. The following error messages for LDAP may display:
For all ldap-config objects:
- if an ldap-tls-profile is
specified, and a tls-profile with that name has not been configured, the
following error displays:
ERROR: ldap-config [xyz] has reference to tls-profile [abc] which does not exist.
- if a realm has not been
configured for an ldap-config, the following error displays:
ERROR: ldap-config [xyz] has reference to realm [abc] which does not exist.
For all ldap-cfg-attributes:
- if a realm has not been
configured for an ldap-config, the following error displays:
ERROR: ldap-config [xyz] has reference to realm [abc] which does not exist.
For local policy-attributes:
- if the ldap-config object is
configured corresponding to every ldap-config specified in the next-hop(s) in
all policy-attribute subelements, and the
next-hop value is not recognized,
the following error displays:
ERROR: local-policy-attribute [route; ldap:ldap-config-name] from local-policy [xyz] has reference to next-hop [ldap:ldap-config-name] which does not exist
- if the ldap-config object is
not enabled, the following error displays:
ERROR: local-policy-attribute [route; ldap:ldap-config-name] from local-policy [xyz] has reference to next-hop [ldap:ldap-config-name] which is not enabled
LDAP Show Commands
The ESD rovides specific LDAP statistics you can display using the show ldap command in the ACLI. The following is an example of the show ldap command output. These statistics include LDAP status information over Period and Lifetime monitoring spans, as well as information on active LDAP sessions. LDAP search query information displays for a Lifetime monitoring span only.
ACMEPACKET# show ldap
LDAP Status -- Period -- -------- Lifetime --------
Active High Total Total PerMax High
Client Trans 0 0 0 0 0 0
Server Trans 0 0 0 0 0 0
Sockets 1 1 0 1 1 1
Connections 0 0 0 0 0 0
---- Lifetime ----
Recent Total PerMax
Query 0 0 0
Modify 0 0 0
LDAP Requests 0 0 0
LDAP Errors 0 0 0
LDAP Rejects 0 0 0
LDAP Expires 0 0 0
LDAPD Errors 0 0 0The following table describes each column in the above output.
| Column Heading | Description |
|---|---|
| Client Trans | Total number of ESD LPAD transactions currently occurring and those that have occurred over the lifetime of the Active Directory. |
| Server Trans | Total number of LDAP Server transactions currently occurring and those that have occurred over the lifetime of the Active Directory. |
| Sockets | Total number of active and past sockets established from the Active Directory on the ESD to the LPAD Server. |
| Connections | Total number of active and past connections established from the Active Directory on the ESD to the LPAD Server. |
| Query | Total number of LDAP queries that occurred in the Active Directory on the ESD. |
| Modify | Total number of modified LDAP call routes in the Active Directory. |
| LDAP Requests | Total number of LDAP call route Requests in the Active Directory. |
| LDAP Errors | Total number of errors that occurred for LDAP call routes in the Active Directory. |
| LDAP Rejects | Total number of LDAP call routes that were rejected in the Active Directory. |
| LDAP Expires | Total number of times LDAP timed out or expired in the Active Directory. |
| LDAPD Errors | Total number of errors that occurred for the LDAP Daemon (LDAPD) in the Active Directory. |