2.4 About Commands
- Obtain system status and operational status
- Modify system configuration
- Obtain measurement reports
The following sections describe how to enter commands through a system terminal. Command correction, keywords, parameters, and syntax are described.
Entering Commands
All commands are entered at the command prompt (>), located in the bottom window of the terminal display. After entering a command, you must press the Enter key. When the command has executed (an output message appears in the display to indicate execution), \2ou can enter another command. The F9 function key allows you to interrupt a running command; however, you cannot enter another command until the running command completes its operation.
Commands are not case sensitive; therefore, either uppercase or lowercase characters can be used. Intermixing (using both upper and lower case) characters does not create an error message, but you must use the correct command syntax.
Action Commands
Throughout this manual, the term “action command” is used in the description of some dependencies, as in the sentence “No other action command can be in progress when this command is entered.”
Action commands are used to effect changes to the state
of entities within the system, such as cards and signaling links. For example,
use the
inh-card command to change the state
of the card to Out-of Service - Maintenance Disabled (OOS-MT-DSBLD).
Table 2-1 lists the action commands and shows which type of system entity they are associated with.
Table 2-1 Action Commands and Associated System Entity
| Action Commands | System Entity |
|---|---|
| act-slk, alw-slk, canc-slk, dact-slk, inh-slk, unhb-slk, blk-slk,ublk-slk, tst-slk | Link Commands |
| act-alm-trns, canc-alm-trns, rls-alm | Alarm Commands |
| alw-trm, inh-trm | Terminal Commands |
| alw-card, inh-card, rmv-card | Card Commands |
Command Keywords and Parameters
Commands consist of two parts: keywords and parameters. Keywords identify the principal action to be performed by the system, and consist of one to three words. Most commands also require parameters to further define the command operation.
Parameters are entered after the keyword. Each parameter must be separated from the keyword or the previous parameter with a colon. If a parameter has multiple values, the values entered are discrete and must be separated with a hyphen or comma. The parameters can be entered in any order.
Some command parameters have built-in default values that are used if a value is not specified. To accept a default value, press Enter after the desired keyword and parameters have been entered.
Use the following delimiters when entering commands:
- :separates parameters
- - or , —separates multiple values within a parameter block
- = —use as delimiter between the parameter and input value
The following is an example of a command entry:
> dact-slk:loc=1101:port=a
The keyword in the above example is
dact-slk (Deactivate Signaling Link).
The first parameter for this command is
loc=1101 (the actual card location in
the system for the link being cancelled, based on equiptment location). The
second parameter is
port=a. This parameter signifies which
signaling link port on the card in the designated location has the link that is
to be cancelled.
If an error is made while typing commands, use the Delete key to make corrections, one character at a time.
Note:
If the same parameter is entered more than once in a command, the system accepts the last parameter value that was entered. Any values for the parameter that were entered earlier in the command are ignored.Keyboard Functions
Some keyboard functions used with commands are described in the previous section. Keyboard functions available for use with commands are listed in Table 2-2. Arrow key functions are further described following the table.
Table 2-2 Keyboard Functions
| VT320 Key Sequence | KSR Key Sequence | Description |
|---|---|---|

|

|
The Up arrow key recalls the previous commands entered at the prompt, one command at a time. The Up arrow key scrolls backwards through up to 10 commands for a KSR, VT320, or SCCS terminal, and up to 20 commands for an IP UI telnet terminal. See page 4-13 for a description of the Up arrow key functions. |

|

|
The Left arrow key backspaces the underline cursor without erasing. |

|

|
The Down arrow key recalls the previous command entered at the prompt, one parameter at a time. If the Up arrow key is pressed and more than one command has been entered in the session, pressing the Down arrow key displays one previously entered command at a time.The Down arrow key scrolls forward through up to 10 commands for KSR, VT320, and SCCS terminals and up to 20 commands for IP UI telnet terminals. See page 4-14 for a description of the down arrow key functions. |

|

|
The Right arrow key recalls the last command entered at the prompt, one character at a time. |
|
F6 |
F6 |
The F6 Function key refreshes the terminal screen, including any characters already input on the command line and the command response line. |
|
F7 |
F7 |
The F7 Function key clears the scroll buffer. This enables a user to stop useless information from passing to the scroll region of the system terminal. |
|
F8 |
F8 |
The F8 function key enables you to stop and restart the scrolling of information on the terminal screen. |
|
F9 |
F9 |
The
F9
Function key allows you to interrupt a running command so that you can enter
another command. Output and processing of the interrupted command continue.
Pressing
F9 is the
same as issuing the
The commands that can be interrupted by pressing
F9 are
listed in the description of the
If the terminal is running one of the listed commands and you
press
F9,
output and processing are cancelled. This function works only on the same
terminal that is running the command you want to cancel. To cancel a command
from another terminal, use the
|
|
F10 |
F10 |
The F10 Function key displays help information for the last command that was entered, including parameters, parameter formats, and the command class. |
|
F11 |
F11 |
The F11 Function key allows you to toggle the terminal’s mode of operation from VT320 to KSR and from KSR to VT320. This function key has no effect on IP UI telnet terminals. |
|
Not Available |
Control-A |
Control-A allows you to enter a command in the KSR mode. |
|
Control-S |
Control-S |
Used with the
sw or
both flow
control (see the
|
|
Control-Q |
Control-Q |
Used with the
sw or
both flow
control (see the
|
|
Ins |
Ins |
When Insert is toggled on, typed characters are inserted into the command line, moving existing characters to the right. When toggled off, typed characters overwrite existing characters. |
|
Del |
Del |
Deletes one character at a time from the right; the cursor stays in position. |
|
Backspace |
Backspace |
Deletes a character and moves the cursor one space to the left. |
Arrow Key Operation
The arrow keys are used to move the cursor to a different position in a command, and to display part or all of a command that was previously entered.
On KSR, VT320, and SCCS terminals, you can scroll through the last 10 commands that were entered at the terminal during the session. On IP UI telnet terminals, you can scroll through the last 20 commands that were entered at the terminal during the session. Part or all of one command at a time is displayed. When you have scrolled through the complete list of up to 10 or 20 commands, the scrolling wraps back to the beginning of the list.
The list of previously entered commands is cleared when
a terminal is inhibited and allowed (inh-trm:trm=xx and
alw-trm:trm=xx) and when a file
transfer is initialized with the
act-file-trns command.
There are two modes of command recall for Up and Down arrow keys:
- Edit Mode
Edit Mode includes any key operation that changes the command at the prompt, such as the Delete key, the Back Space key, or an alphanumeric key. Pressing one of these keys to enter or change a command puts the terminal into Edit Mode. Pressing the Enter key (or carriage return) takes the terminal out of Edit Mode.
- Non-edit Mode
Pressing the Enter key (or carriage return) puts the terminal into Non-edit Mode. A terminal remains in Non-edit Mode when you press an arrow key, a Function key, or the Insert key, which do not change the command at the prompt. When you press a key that changes the command, the terminal goes into Edit Mode until you press the Enter key again.
Up Arrow Key
The Up arrow key is used to recall up to the last 10 commands (KSR, VT320, and SCCS terminals) or the last 20 commands (IP UI telnet terminals) entered at the prompt during the session.
- In Edit Mode
- You enter 3 characters of a command at the prompt and press the Up arrow key. If the previous command was 6 characters long, then the last 3 characters of the previous command are recalled and displayed after the 3 characters that you entered at the prompt.
- You enter 10 characters of a command at the prompt and press the Up arrow key. If the previous command was 6 characters long, none of the previous command is displayed. The command that you entered remains as you entered it at the prompt.
- Entering part or all of a command at the prompt puts the terminal into Edit Mode. In Edit Mode, the last (or previous) command is recalled only if the command length of the last command is greater than the command at the prompt. For example:,
- In Non-edit Mode
- When you have pressed the Enter key and there is no command at the prompt, or you have pressed the Insert key or a Function key, the terminal is in Non-edit Mode.
- When you press the Up arrow key in Non-edit Mode, and you have entered at least one previous command, the last command that you entered is displayed at the prompt. Pressing the Up arrow key again clears the command at the prompt (if any) and displays the next previous command that you entered (if any). By continuing to press the Up arrow key, you can scroll backwards through the last 10 commands (KSR, VT320, \2nd SCCCS terminals) or the last 20 commands (IP UI telnet terminals) that you entered at the terminal. The display wraps back to the most recent of the entered commands when all of the available commands have been recalled. The terminal remains in Non-edit Mode until you press a key that changes the displayed command.
Down Arrow Key
In Edit Mode, the Down arrow key recalls the last command that was entered at the terminal, one parameter at a time. The recalled parameter is displayed at the end of the entry that currently appears at the prompt.
- If the Up arrow has not been pressed just before pressing the Down arrow key, \2he Down arrow key recalls the last command that was entered at the terminal, one parameter at a time.
- If the Up arrow key is the last key that was pressed before the Down arrow key is pressed, the Down arrow key scrolls forward through the last 10 commands (KSR, VT320, \2nd SCCS terminals) or last 20 commands (IP UI telnet terminals), displaying one complete command each time the key is pressed. The scrolling wraps to the beginning of the list when all of the available commands have been displayed.
Right Arrow Key
Each time the Right arrow key is pressed, one character of the last command is recalled and the cursor moves one position to the right. When the last command is completely displayed, pressing the Right arrow key does not cause any cursor movement or character display.
Left Arrow Key
The Left arrow key moves the underline cursor one position to the left without erasing the character. The underline cursor can be moved until it reaches the first character at the left of the command. If the Left arrow key is pressed again after the cursor reaches the first character of the command, the bell sounds.
Command Output and Messages
Reports and outputs generated through retrieve or report status commands are followed by a semi-colon (;) to signify the end of the output (this is in compliance with TL1 standards).
The following types of output messages are used on the system:
- Command Accepted-Processing: The command has been accepted by the application’s command handler as syntactically correct. This message is displayed in the command area of the terminal display.
- Command Completed-The command has been entered, and the system has completed processing. This message is displayed in the scroll area of the terminal display.
- Command Executed-The command has been entered, and the system has completed processing. This message is displayed in the command area of the terminal display.
- Command Failed-The command was executed but failed due to an external reason, such as the link is not equipped or a disk drive is unable to communicate. The reason for the failure is included in this message.
- Command Rejected-The command syntax could be
incorrect, or a parameter value is incorrect (semantic error). This message is
displayed in the command area of the terminal display.
The reason for rejecting the command (command syntax or incorrect parameter value) is included in this message.
- Command Aborted-The command syntax and the parameter values are ok, but for some reason the command was aborted (for example, a disk drive is inaccessible). This message is displayed in the scroll area of the terminal display.
- Command Response Messages-A command is entered at the terminal, and the response to that command is echoed on that same terminal. These messages are displayed in the scroll area of the terminal display.
- Unsolicited Messages-An example of unsolicited messages are the messages delivered in response to alarm conditions. These messages are displayed in the scroll area of the terminal display.
The unsolicited messages can be directed to a specific
terminal or printer by using the
chg-trm command to assign one or more
of the groups of unsolicited output messages shown in
Table 2-3
to the specified terminal or printer.
Table 2-3 Unsolicited Output Message Groups
|
Application Server |
Application Subsystem |
|
Card |
Clock |
|
Debug |
Global Title Translation |
|
Gateway Screening |
Measurements Maintenance |
|
Monitor |
MPS |
|
SEAS Maintenance |
Security Administration |
|
System Maintenance |
Database Administration |
|
Traffic Measurements |
Program Update |
|
Link Maintenance |
LNP Subscription |
|
LNP Database Administration |
To configure a terminal to receive unsolicited LNP
database administration and LNP subscription messages, the LNP feature must be
turned on (see the
enable-ctrl-feat command).
Command Output Banners
When a command is executed in the system, one or more banner lines appear in the output that is displayed for the command.
Figure 2-3 Output Banner Format
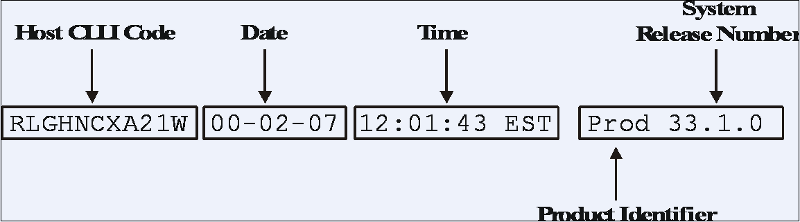
The following fields appear in each output banner:
- Host CLLI code—a maximum of
one alphabetic character and ten alphanumeric characters. The CLLI code
uniquely identifies the system in terms of its physical location. The CLLI code
must be unique among all elements in the system.
The CLLI code contains the following information:
- City—4 characters
- State— 2 characters
- Building— 2 characters
- Equipment type —3 characters
- Date—year-month-day
- Time—hour: minute: second time zone
- System Release Number— contains a product identifier
and the version ID number.
The product identifier, which is shown as ‘Prod’ in Figure 2-3 and the output examples in this manual, will appear as “EAGLE5”.
The version ID number identifies the GPL set that is specific to the software release that is expected to be installed on the system as approved loads. The format of the version ID number is maj.min.maint.notused.rampspin, defined as follows:
- maj—the major release ID
- min—the minor release ID
- maint—the maintenance release ID
- notused—this field is not used and is always 0
- rampspin—the ramp spin release ID
System Security
User IDs and passwords protect the system from unauthorized entry into the system and enhance system security. To enter the system through a terminal, a user must enter a valid user ID and password at the system prompt, and the user ID and password must be authorized for use together. A user ID identifies a user to the system.
To maintain the security of the system, passwords should be changed periodically and user IDs should be deleted whenever there is a personnel change.
When prompted to enter a new password, a different password should be provided. This is the responsibility of the user, and is not enforced by the EAGLE.
Rules for User ID and Password Administration
The rules for administering User IDs User IDs and passwords, rules for administering passwords are:
- The maximum number of user ID-password combinations is 100.
- The maximum length of the user ID is 16 characters.
- The maximum length of the password is 12 characters;
the minimum length is site provisionable using the
chg-secu-dfltcommand, and it can be from 1 – 12 characters long. - User IDs and passwords may contain any printable characters except the characters used as command delimiters: colon (:), comma (,), \2yphen (-), or equal sign (=).
- Each user ID must begin with an alpha character.
- A password must contain:
- At least as many characters as specified on the
minlen parameter of the
chg-secu-dfltcommand - At least as many alphabetic characters as
specified on the
alpha parameter of the
chg-secu-dfltcommand - At least as many numeric characters as specified
on the
num parameter of the
chg-secu-dfltcommand - At least as many punctuation characters as
specified on the
punc parameter of the
chg-secu-dfltcommand
- At least as many characters as specified on the
minlen parameter of the
- A password must not contain the associated user ID.
Command Classes
Each user ID and password combination is assigned to one or more command classes to control the set of system security commands that a user may enter.
There are 8 unique non-configurable command classes: Basic, Database Administration, Debug, Link Maintenance, Program Update, Security Administration, System Maintenance, and LNP Basic. (The Basic command class is assigned to all users as a default.)
There are 32 available configurable command classes. See
the
chg-cmd command description and the
chg-cmdclass command description for
information about naming and assigning commands to configurable command
classes.
See the
chg-user command description or the
ent-user command description for more
information on configuring user IDs and passwords and assigning command
classes.
Login Security Checks
loginsystem securityTo aid in system security, the system maintains a record of when a password was last changed and requires a user to change the password when it is older than the site-specified maximum password age. The system also keeps track of the elapsed time between successful logins. If the time between successful logins exceeds the site-specified maximum, a user is not allowed access to the system. The site systems administrator also has the ability to revoke a user ID.
When a user first logs into the system, the default unauthorized user warning is displayed as follows
NOTICE: This is a private computer system.
Unauthorized access or use may lead to prosecution.
Additional security is available for the system in that multiple logins using the same user ID are prohibited.
Intrusion Alert
To alert the system administrator to a possible attempt by an unauthorized person trying to log into the system, the system issues a scroll area message. When 5 or more consecutive attempts to log into the system have failed, the following scroll area message is sent to all terminal ports that can receive unsolicited Security Administration messages:
Info: xxxxxxxxxx successive LOGIN failures on port pp
- xxxxxxxxxx is the number of consecutive login failures on the port (1 – 4,294,967,295)
- pp is the terminal port (1 – 40) on which the login attempts were made
When the attempt to log into the system is successful after a series of failed consecutive login attempts, or if the active MASP reboots, the count of failed consecutive login attempts for that port is reset to 0.
Attempts to log into the system that are not completed normally, are not considered login attempts and are not included in the count of failed consecutive login attempts. For example, while prompting for a password you might use the F9 key to abort the command, or errors might occur when the system is looking up a user ID or password.
Login Procedure
The commands described in this manual are entered at a terminal connected to the system.
Before you can enter most of the commands, you must
enter the
login command to log into the system
and open a user session. You must enter the login command with a valid user ID
and password combination. When the system accepts your user ID and password as
valid, you can enter commands at the terminal in the user session.
The first procedure in this section explains how to log
into the system using the
login command.
The procedures that follow the login procedure explain how to handle common situations that can arise when you log into the system.
- You must change the password the first time that you log in with a new user ID and password.
- The user ID and password that you enter are not accepted as valid.
- Your password has expired and must be changed.
- Someone else has already logged on with your user ID and password; the system does not allow the same ID and password to be used on two terminals at the same time.
Note:
You can enter the act-user command instead of the login command.Log into the System for a User Session
Your User ID and Password were not Accepted
Your User ID is Already Being Used
Login Error Messages
- E2262 Cmd Rej: Password too long, 12 maximum
- E2263 Cmd Rej: Password does not contain enough characters
- E2264 Cmd Rej: Password verification failed
- E2750 Cmd Rej: UserID already logged on (or is logging on) another port
- E2751 Cmd Rej: UserID has been revoked
- E2752 Cmd Rej: UserID has become obsolete and cannot be used
- E2753 Cmd Rej: Password does not contain enough alphabetic characters
- E2754 Cmd Rej: Password does not contain enough numeric characters
- E2755 Cmd Rej: Password does not contain enough punctuation characters
- E2756 Cmd Rej: Failed reading the password table
- E2757 Cmd Rej: Invalid userID/password combination
- E2758 Cmd Rej: ALPHA+NUM+PUNC must not be greater than 12
- E2759 Cmd Rej: Revocation of security admin userID not allowed
- E2760 Cmd Rej: Failed reading the security defaults table
- E2761 Cmd Rej: Password cannot contain userID
See the
chg-secu-dflt command description for
information on different options the system administrator has for configuring
the system for password requirements.
The following is an example of the information that might be displayed in the scroll area, depending on your site TM configuration:
New password must contain
- from 8 to 12 characters
- at least 1 alphabetic character(s) (a - z)
- at least 1 numeric character(s) (0 - 9)
- at least 1 punctuation character(s) (for example, $%@#)
Logout Procedure
When a terminal session is completed, perform the following logout procedure to log out of the system Log Out Of the System. The terminal returns to an input idle state.
Note:
You can use thedact-user command instead of the
logout command.