5 Mail Service Administration
This chapter describes how to administer the mail service in Oracle Communications Convergence.
See "Enabling Core Services for Convergence" for information about enabling services.
Managing Attachment Previewing
By default, Convergence can preview only JPG, GIF, and TXT email attachments. In a desktop environment, native applications must be installed to view email attachments such as Office documents, or browser plug-ins must be installed in the browser to enable Convergence to preview PDF attachments.
If Convergence is integrated with Oracle Outside In Transformation Server, Convergence is capable of previewing many different file types regardless of the web browser, including DOC and XLS type email attachments.
See Convergence Installation and Configuration Guide for information about installing Outside In Transformation Server and configuring it for Convergence.
About Outside In Transformation Server and the Outside In Proxy
Each time a user previews an attachment, Convergence attempts to open it in the browser. If Convergence is not able to open the attachment by default, it sends the attachment to Outside In Transformation Server. The transformation server transforms the attachment into HTML, which Convergence can render in the browser.
The transformation server can handle a large number of simultaneous requests by placing attachment requests in a queue.
The Outside In proxy creates a temporary directory for each user requesting to view attachments. For each transformation, the Outside In proxy creates a temporary subdirectory under the user directory. The Outside In proxy passes the input directory containing the transformed attachment and the output directory of the transformed attachment to the Transformation Server. The Outside In proxy deletes the subdirectory after a configurable time-out period has passed.
The Convergence server manages file management to the transformation server. Convergence uses a session cookie and a server-generated URL token for each attachment request. For security, Convergence masks the URL token.
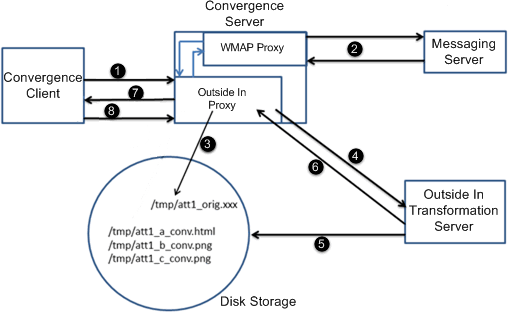
Figure 5-1 shows the attachment preview workflow.
Figure 5-1 Convergence Attachment Request Workflow
Description of "Figure 5-1 Convergence Attachment Request Workflow"
The following list explains the attachment preview workflow from Figure 5-1.
-
The Convergence client sends the request to the Convergence server.
If the request is for an attachment type that can be rendered natively in the browser, the request is sent to the WMAP proxy.
If the request is for an attachment type that cannot be rendered natively in the browser, the request is first passed to the Outside In proxy, and then to the WAMP proxy.
-
The request is sent to the Messaging server. The Messaging server sends the attachment back to the Convergence server.
-
For attachment types that cannot be rendered natively in the browser, the Outside In proxy sends the response from the Messaging server to the disk storage.
-
For attachment types that cannot be rendered natively in the browser, the Outside In proxy communicates where it saved the attachment to the Outside In Transformation server, and also informs the transformation server where to save the attachment after it has been converted.
-
For attachment types that cannot be rendered natively in the browser, the transformation server converts the attachment into a format that can be natively rendered in the browser and saves it to the directory provided by the Outside In proxy.
-
For attachment types that cannot be rendered natively in the browser, the transformation server informs the Outside In proxy that it has completed transforming the file.
-
If the original request was for an attachment type that could be rendered native in the browser, the Convergence server sends the attachment to the browser.
If the original request was for an attachment type that could not be rendered native in the browser, the Outside In proxy provides the browser with a redirection URL to the transformed attachment on the disk storage.
-
If the original request was for an attachment type that could not be rendered native in the browser, the Convergence client accesses the transformed attachment using the URL provided by the Outside In proxy and renders it in the browser.
Configuring File Directory Access
Convergence and Outside In Transformation Server have to be configured so that they can both read and write attachments in the storage disk. Convergence must have full permissions to the storage disk to read, write, and delete files.
The Convergence Server and the Outside In Transformation Server can run on the same machine or on different machines. Configure the transformation server as a network file system (NFS).
-
If the transformation server is running on Solaris:
-
Share the /export/tsdir/ directory.
chmod 700 /export/tsdir
-
Edit /etc/dfs/dfstab and add the following line:
share -F nfs -d [-o root=host_name] "tsdir" /export/tsdirInclude the -o parameter when the Convergence server and the transformation server are running as local root, where host_name is the host name of the Convergence server. Omit the -o parameter when the Convergence server and the transformation server are running as the same user.
-
Create a soft link or mount to the NFS directory. For example:
-s //net/host_name/export/tsdir /export/tsdir
-
-
If the transformation server is running on Linux:
-
Share the /export/tsdir/ directory:
chmod 700 /export/tsdir
-
If the Convergence server and the transformation server are running as the same user, edit /etc/exports and add the following line:
/export/tsdir
If the Convergence server and the transformation server are running as local root, edit /etc/exports and add the following line:
/export/tsdir host_name(rw,no_root_squash) -
Create a soft link or mount to the NFS directory. For example:
-s //net/host_name/export/tsdir /export/tsdir
-
The Outside In proxy generates a unique URL for each attachment and provides it to the Convergence client.
The following example shows the sample configuration settings for Outside In proxy in the Convergence configuration.xml file:
<OINService>
<ServiceName v="SUN_OIN_SERVICE"/>
<BackendServiceDetails>
<Enable v="true"/>
<HostName v="oin server name"/>
<PortNumber v="60611"/>
</BackendServiceDetails>
<TsdirPath v="/export/tsdir"/>
<AutoPruneInterval v="5"/>
</OINService>
You can use the iwcadmin command to configure the parameters for the Outside In proxy.
Managing Attachment Life Cycles
The Outside In proxy manages the life cycle of attachments, including temporary directories, file creation, deletion, and purging, and the number of directories and disk space per user.
By default, the Outside In proxy automatically deletes an attachment from the storage disk after five minutes.
Use the iwcadmin command to configure the duration after which attachments are deleted from the storage disk. For example, to configure the proxy to delete attachments from the disk after three minutes:
iwcadmin -o oin.autopruneinterval -v 3
Supporting Extended Character Locales
Oracle Outside In Transformation Server supports many typical font sets and some extended font sets. However, depending on the locales being used in your deployment, you may need to install and configure additional font sets to support the rendering of attachments.
By default, when the transformation server cannot render characters because the font is missing, it replaces the character with an asterisk. For example, if a user is using Convergence with the Japanese locale, but the transformation server does not have access to Japanese font sets, the transformation server will render attachments with asterisks.
Install all required fonts on the host machine where the transformation is installed and export the GDFONTPATH environment variable.
See the Oracle Outside In Technology documentation for more information.
Customizing Transformation Blacklist
The Outside In Transformation Server blacklist enumerates the types of files that are prevented from being sent to the transformation server, such as ZIP files or EXE files.
You can customize the blacklist to add or remove file types. See the discussion about customizing the attachment blacklist in for more information.
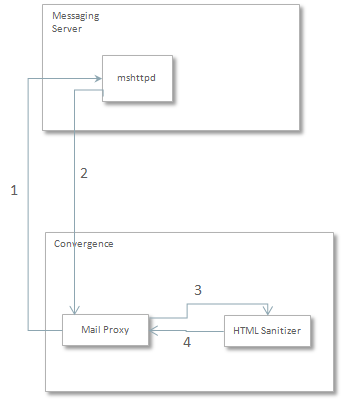
About HTML Filtering
You can configure Convergence to filter embedded HTML content from email messages, because such content could contain malicious code. By default, HTML filtering is enabled. When HTML filtering is enabled:
-
Convergence removes specified elements, attributes, protocols, and CSS properties from incoming email messages before routing the messages to users.
-
Convergence provides an option to allow the URLs in inline styles in email messages. This can be set by using the mail.htmlsanitizer.allowurlsinstyle parameter. This option should be enabled only when the URL referenced in the email message is from trusted source and is secure. See "Convergence Properties Reference" for information on mail.htmlsanitizer.allowurlsinstyle.
Convergence includes a default whitelist, a blacklist, a CSS whitelist of HTML elements, attributes, protocols, and CSS properties. Whitelisted and CSS whitelisted entries are permitted in email messages. Blacklisted entries are removed from email messages. Elements, attributes, protocols, and CSS properties that do not appear on any of these whitelists are treated as blacklist entries.
Figure 5-2 shows the approach that is used for HTML filtering in Convergence.
Configuring HTML filtering consists of the following tasks:
Enabling and Disabling HTML Filtering
You enable and disable HTML filtering using the iwcadmin command. By default, HTML filtering is enabled.
To enable or disable HTML filtering, enter:
iwcadmin -o mail.htmlsanitizer.enable -v {true|false}when the mail.htmlsanitizer.enable parameter is set to false, HTML content is not displayed in the email message. Only the text or plain content is displayed in the Convergence email message. To display the HTML content, set the role.http.convergencefilterenabled parameter to true in the Messaging Server. See the discussion about HTML Filtering in your Messaging Server documentation.
Note:
In Convergence 3.0.1 patch sets, the HTML filtering is disabled by default. If you are installing Convergence 3.0.1 patch sets, see Table 5-1 for the information on recommended configurations for HTML filtering in Convergence and Messaging Server.
Table 5-1 Recommended Configurations for HTML Filtering in Different Releases of Convergence and Messaging Server
| Convergence | Messaging Server | Recommended Configuration in Convergence | Recommended Configuration in Messaging Server |
|---|---|---|---|
|
3.0.3 X |
8.1.X and later |
mail.htmlsanitizer.enable = true |
No additional configurations required |
|
3.0.2 X |
8.0.2.2 and later |
mail.htmlsanitizer.enable = true |
No additional configurations required |
|
3.0.2 X |
8.0.2.2 and later |
mail.htmlsanitizer.enable = false |
http.convergencefilterenabled = 1 http.enableblacklistfilter = 1 |
|
3.0.1.1.0 to 3.0.1.4.0 |
8.0.2 to 8.0.2.1 |
mail.htmlsanitizer.enable = true/false |
http.convergencefilterenabled = 1 http.enableblacklistfilter = 1 |
|
3.0.1.1.0 to 3.0.1.4.0 |
Below 8.0.2 |
mail.htmlsanitizer.enable = true/false |
No additional configurations available |
|
Below 3.0.1.1.0 |
Below 8.0.2 |
No additional configurations available |
No additional configurations available |
Note:
Convergence releases before 3.0.1.1.0 release were completely dependent on the blacklist based filtering provided by Messaging Server for HTML filtering. Whitelist based filtering was introduced in Convergence 3.0.1.1.0 release. Oracle recommends Convergence for HTML filtering rather than Messaging Server.The blacklist filter (http.enableblacklistfilter) has been disabled from Messaging Server 8.0.2 release onwards and a new parameter, http.convergencefilterenabled, has been introduced for HTML filtering. Only when this parameter is set to 1, mshttpd will send HTML content in the message body and expects the content to be sanitized by Convergence.
Configuring HTML Filtering in Convergence
The default Convergence whitelist includes all known safe HTML elements, attributes, and protocols. The default Convergence blacklist includes all known potentially harmful HTML elements, attributes, and protocols. The default Convergence CSS whitelist includes all known safe CSS properties.
Blacklist takes precedence over whitelist; that is, if an element is present in both whitelist and blacklist, the element will be considered as blacklisted and the element will not be allowed in the email content.
You use the iwcadmin command to create an additional whitelist, blacklist, CSS whitelist with additional elements, attributes, protocols, or CSS properties.
It is not possible to modify the default whitelist, blacklist, or CSS whitelist. The contents of the default lists are deliberately excluded from this documentation, as such information could be used to target whitelisted values.
To configure the additional blacklist:
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "filtering_value"
To configure the additional whitelist:
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "filtering_value"
To configure the additional CSS properties for whitelist:
iwcadmin -o mail.htmlsanitizer.additionalCSSwhitelist -v "filtering_value"
Where filtering_value is a comma-separated list of HTML elements, attributes, protocols, or CSS properties.
The following example shows a sample configuration using the additional blacklist:
-
Do not allow attribute1 and attribute2 on all elements
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "attribute1, attribute2"
-
Do not allow attribute1 on element1 only.
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "attribute1@element1"
-
Do not allow element1 and element2.
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "@element1,@element2"
-
Do not allow element1. Do not allow attribute1 on any element. Do not allow attribute2 on element2.
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "@element1,attribute1, attribute2@element2"
-
Do not allow attribute1, attribute2 and attribute3 on element1.
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "attribute1@element1,attribute2@element1, attribute3@element1"
-
Do not allow protocol1. Colon(:) at end indicates it is a protocol.
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "protocol1:"
For example:
iwcadmin -o mail.htmlsanitizer.additionalblacklist -v "@source,srcdoc@iframe,ftp:"
With this settings, HTML element source, srcdoc attribute of HTML element iframe, and ftp protocol will not be allowed in the mail content.
The following example shows a sample configuration using the additional whitelist:
-
Allow attribute1 and attribute2 on all elements
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "attribute1, attribute2"
-
Allow attribute1 on element1 only.
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "attribute1@element1"
-
Allow element1 and element2.
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "@element1,@element2"
-
Allow element1. Allow attribute1 on any element. Allow attribute2 on element2.
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "@element1,attribute1, attribute2@element2"
-
Allow attribute1, attribute2 and attribute3 on element1.
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "attribute1@element1,attribute2@element1, attribute3@element1"
-
Allow protocol1. Colon(:) at end indicates it is a protocol.
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "protocol1:"
For example:
iwcadmin -o mail.htmlsanitizer.additionalwhitelist -v "testattr2@div, abc:"
With this settings, testattr2 (custom attribute) of HTML element div, and protocol abc (custom protocol) will be allowed in the mail content.
Note:
For additionalwhitelist and additionalblacklist, if an attribute is specified without an associated element, then that attribute will not be allowed on any element.
The following example shows a sample configuration while configuring the additional CSS properties for whitelist:
iwcadmin -o mail.htmlsanitizer.additionalCSSwhitelist -v "item_1,item_2"
where item is a CSS property like visibility and z-index.
Note:
Only few additional CSS properties can be added to the whitelist. You can check the logs to identify the unsupported CSS property and remove it from the whitelist.
Convergence allows the URLs in inline styles in email messages. This can be set by using the mail.htmlsanitizer.allowurlsinstyle parameter. Enabling this option is vulnerable to XSS. This option should be enabled only when the URL referenced in the email message is from trusted source and is secure.
In this example, the image.png displays in the email message when mail.htmlsanitizer.allowurlsinstyle is set to true:
<span style="background-image: url(http://example.com/image.png)"></span>
Restricting Attachment Types for End-Users
You can configure the type of files that can be attached to an email in Convergence 3.0.3.4.0. Depending on the configuration , the end user will not be able to attach any restricted file types, such as .dll, .exe, .py and will also not be able to save it on draft. If the user tries to upload a restricted attachment, an error message will be displayed in the Convergence UI.
- client.enableAttachmentRestriction: This parameter can be set to true/false to enable or disable this feature. By default, this feature is disabled.
- client.restrictedExtensionTypes: This parameter can be used to set the attachment types that have to be restricted.
- Set
client.enableMailAttachmentRestrictionto true using the IWCAdmin CLI:./iwcadmin -o client.enableAttachmentRestriction -v true. - Check the value of
client.restrictedExtensionTypesto verify the attachment types to be restricted are part of the list.If its not part of the existing list, update the parameter to include the attachment type.
- Edit
<data-directory>/WEB-INF/web.xmland uncomment the MailAttachmentFilter related entries, servlet filter and filter-mapping. - Navigate to the installed directory and redeploy convergence in the
Application
server:
where /tmp/wlspass file contains the Weblogic admin password.$ cd /opt/sun/comms/iwc/sbin $ ./config-weblogic deploy /tmp/wlspass - Restart the application server.
Restricting Number of Emails that can be sent to Recipients in a Defined Time Period
- Edit <data-directory>/WEB-INF/web.xml file and and uncomment the RateLimitFilter entries, servlet filter and filter-mapping.
- Go to installed directory and re-deploy Convergence
in the application
server:
$ cd /opt/sun/comms/iwc/sbin $ ./config-weblogic deploy /tmp/wlspass- Where /tmp/wlspass file contains the Weblogic admin password.
Enabling Anti-Spam
You can configure Convergence to take action against spam messages in the following ways:
-
By setting the anti-spam related parameters in Convergence
-
By integrating a spam filter in Messaging Server in addition to setting the anti-spam related parameters in Convergence
Configuring Convergence to Combat Spam
Set the following parameters in Convergence:
-
mail.spam.enableaction: Set this parameter to true to enable the anti-spam functionality. Setting this parameter will enable users to take action against spam messages.
iwcadmin -o mail.spam.enableaction -v true
-
mail.spam.folder: Set this parameter to the folder name into which spam messages should be moved.
iwcadmin -o mail.spam.folder -v SpamFolder
You must restart the Oracle WebLogic server after making the configuration changes.
When you set the parameters, the following spam related functionality is enabled in the Convergence client:
-
A system folder is made available as the designated spam folder. This is based on the value set for the mail.spam.folder parameter assigned by the administrator.
-
Users will be able to mark messages as spam or not spam. Messages marked as spam are moved into the designated spam folder and messages that are marked as not spam are moved into the Inbox.
Configuring Messaging Server to Combat Spam
A more effective way to counter spam messages is to deploy a spam filer at the back-end Messaging Server in addition to enabling the anti-spam functionality in Convergence. For information on how to integrate a spam filter with the Messaging Server, see the Messaging Server documentation.
After integrating the spam filter, set the value of the service.feedback.spam parameter in Messaging Server to the email address at which spam reports are accepted.
configutil -o service.feedback.spam -v email_address
When you set this parameter, the following spam related functionality will be available to the Convergence client.
-
Users will be able to mark messages as spam. When users mark a message as spam, the message is flagged in the message store, and forwarded to the email address set for the service.feedback.spam configuration utility option. The spam messages are marked in the message list and displayed with a warning in the message viewer.
-
Users will be able to mark messages incorrectly identified as spam, as not spam. When the user marks incorrectly identified spam messages as not spam, the flag is removed from the message in the message store.
If Messaging Server is configured with a spam filter that accepts reports of messages that are incorrectly identified as spam, set the value of the parameter service.feedback.notspam to the email address at which Convergence will forward the messages marked as not a spam.
configutil -o service.feedback.notspam -v email_addressNote:
You must restart Messaging Server after making these configuration changes.
Disabling Rich Text Formatting
You can disable rich text formatting in Convergence. When rich text formatting is disabled, email messages are sent in plain text.
To disable rich text formatting, set the client.enablertfcompose configuration property to false. By default, this parameter is set to true. For example:
iwcadmin -o client.enablertfcompose -v false
Enabling Sound Alerts
Users can configure their Convergence to play a sound alert when they receive a new email message.
For enabling sound alerts, the following configuration change has to be done in Oracle Weblogic server:
-
Create a file titled mimemappings.properties under the <Convergence_Domain>/config folder and add mp3=audio/mpeg.
OR
Modify the <Convergence_Domain>/servers/ManagedServer/tmp/_WL_user/<Convergence>/<value>/war/WEB-INF/web.xml to add the following:
<mime-mapping> <extension>mp3</extension> <mime-type>audio/mpeg</mime-type> </mime-mapping> - Restart Weblogic Managed Server.