Overview of Digest Authentication
The following sections provide a basic overview of Digest authentication, and describe Digest authentication support and configuration in Converged Application Server.
What Is Digest Authentication?
Digest authentication is a simple challenge-response mechanism used to authenticate a user over SIP or HTTP. Digest authentication is fully described in RFC 2617.
When using Digest authentication, if a client makes an un-authenticated request for a protected server resource, the server challenges the client using a nonce value. The client uses a requested algorithm (MD5 by default) to generate an encrypted response—a Digest—that includes a username, password, realm, the nonce value from the challenge, the SIP method, and the requested URI.
The server verifies the client Digest by recreating the Digest value and comparing it with the client's Digest. To recreate the Digest value the server requires a hash of the "A1" value (see RFC 2617) that includes, at minimum, the nonce, username, password and realm name. The server either recreates the hash of the A1 value using a stored clear-text password for the user, or by obtaining a precalculated hash value. Either the clear-text password or precalculated hash value can be stored in an LDAP directory or accessed from an RDBMS using JDBC. The server then uses the hash of the A1 value to recreate the Digest and compare it to the client's Digest to verify the user's identity.
Digest authentication provides secure authorization over HTTP because the clear text password is never transmitted between the client and server. The use of nonce values in the client challenge also ensures that Digest authentication is resistant to replay attacks. See Figure 3-1 for a more detailed explanation of the challenge-response mechanism for a typical request.
Digest Authentication Support in Converged Application Server
Converged Application Server includes LDAP Digest Identity Asserter security providers for asserting the validity of a client's Digest using LDAP or an RDBMS. A separate authorization provider is required to complete the authentication process (see "Configure an Authenticator Provider").
The Digest Identity Asserter only verifies a user's credentials using the
client Digest. After the Digest is verified, the configured authorization provider
completes the authentication process by checking for the existence of the user (by
username) and also populating group membership for the resulting
javax.security.auth.Subject.
The Digest Identity Asserter provider requires that user credentials be stored in an LDAP server or RDBMS in one of the following ways:
-
Unencrypted (clear text) passwords. The simplest configuration stores users' unencrypted passwords in a store. If you choose this method, Oracle recommends using an SSL connection to the LDAP store or database to reduce the risk of exposing clear text passwords in server-side network traffic. Some LDAP stores do not support storing unencrypted passwords by default; in this case you must create or use a dedicated credential attribute on the LDAP server for storing the password. See Configure the LDAP Server or RDBMS for more information.
- Reverse-Encrypted Passwords. Converged Application Server provides a utility to help you compute the Encryption Key, Encryption Init Vector, and Encrypted Passwords values used when you configure the Digest Authorization Identity Asserter provider.
- A pre-calculated hash of each password, username, and realm. If storing unencrypted or reverse-encrypted passwords is unacceptable, you can instead store a pre-calculated hash value of the username, security-realm, and password in a new or existing attribute in LDAP or an RDBMS. The Digest Identity Asserter then retrieves only the hash value for comparison to the client-generated hash in the Digest. Storing pre-calculated hash values provides additional security.
The LDAP Digest Identity Asserter is compatible with any LDAP provider that permits storage of a clear text password or pre-calculated hash value.
Note:
You cannot change the schema for the built-in LDAP store to add a dedicated field for storing clear text passwords or pre-calculated hash values. However, you can use the predefined "description" field to store password information for testing or demonstration purposes.
If you do not use the DefaultAuthenticator provider for authentication decisions, you must make DefaultAuthenticator an optional provider (ControlFlag="SUFFICIENT" or lower) before you can use Digest authentication. This will generally be the required configuration in production installations where a separate LDAP store is used to maintain clear text or hashed password information.
Figure 3-1 Digest Authentication in Converged Application Server
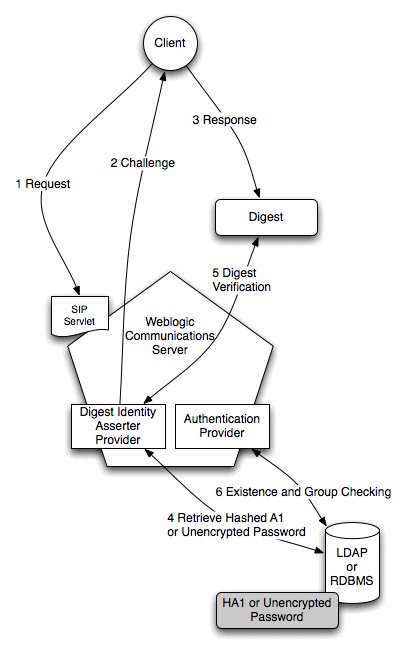
- The client makes an unauthorized request for a protected application
resource. (You protect SIP Servlet resources by specifying the
@SipSecurityannotation. See RFC 359, sections 22.3.10.) - The Digest Identity Asserter provider generates a challenge string
consisting of the nonce value, realm name, and encryption algorithm (either MD5 or
MD5-sess). The SIP container delivers the challenge string to the client.
Note:
The Digest Identity Asserter maintains a cache of used nonces and timestamps for a specified period of time. All requests with a timestamp older than the specified timestamp are rejected, as well as any requests that use the same timestamp/nonce pair as the most recent timestamp/nonce pair still in the cache. - The client uses the encryption algorithm to create a Digest consisting of the username, password, real name, nonce, SIP method, request URI, and other information described in RFC 2617.
- The Digest Identity Asserter verifies the client Digest by recreating the Digest value using a hash of the A1 value, nonce, SIP method, and other information. To obtain a hash of the A1 value, the Identity Asserter either generates HA1 by retrieving a clear-text password from the store, or the Identity Asserter retrieves the pre-calculated HA1 from the store.
- The generated Digest string is compared to the client's Digest to verify the user's identity.
- If the user's identity is verified, an authentication provider then
determines if the user exists and if it does, the authentication provider populates
the
javax.security.auth.Subjectwith the configured group information. This step completes the authentication process.Note:
If you do not require user existence checking or group population, you can use the special "no-op" Identity Assertion Authenticator to avoid an extra connection to the LDAP Server; see "Configure an Authenticator Provider" for more information.After authentication is complete, the SIP Servlet container performs an authorization check for the logged in
javax.security.auth.Subjectagainst the@SipConstraintannotation inside the@SipSecurityannotation. See JSR 359, sections 20.8, 22.3.10.1 and 22.3.10.2.
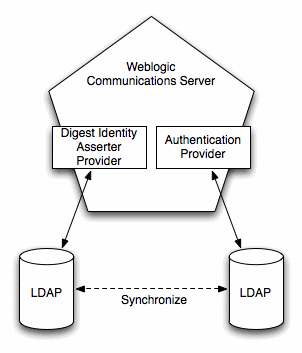
The LDAP Digest Identity Asserter and the configured Authentication provider can either use the same LDAP store or different stores.
Note:
If you use multiple LDAP stores, you must also create some infrastructure to keep both stores synchronized in response to adding, removing, or changing user credential changes. Maintaining LDAP stores in this manner is beyond the scope of this documentation.Figure 3-2 Multiple LDAP Servers