2 Deploy with the Container Engine for Kubernetes
The Converged Application Server can be deployed in OCI using Oracle's Container Engine for Kubernetes.
Oracle Cloud Infrastructure Container Engine for Kubernetes is a fully-managed, scalable, and highly available service that you can use to deploy your containerized applications to the cloud. Use Container Engine for Kubernetes (abbreviated OKE) when your development team wants to reliably build, deploy, and manage cloud-native applications. You specify whether to run applications on virtual nodes or managed nodes, and Container Engine for Kubernetes provisions them on Oracle Cloud Infrastructure in an existing OCI tenancy.
To learn more about OKE, view the OKE documentation.
Architecture Overview
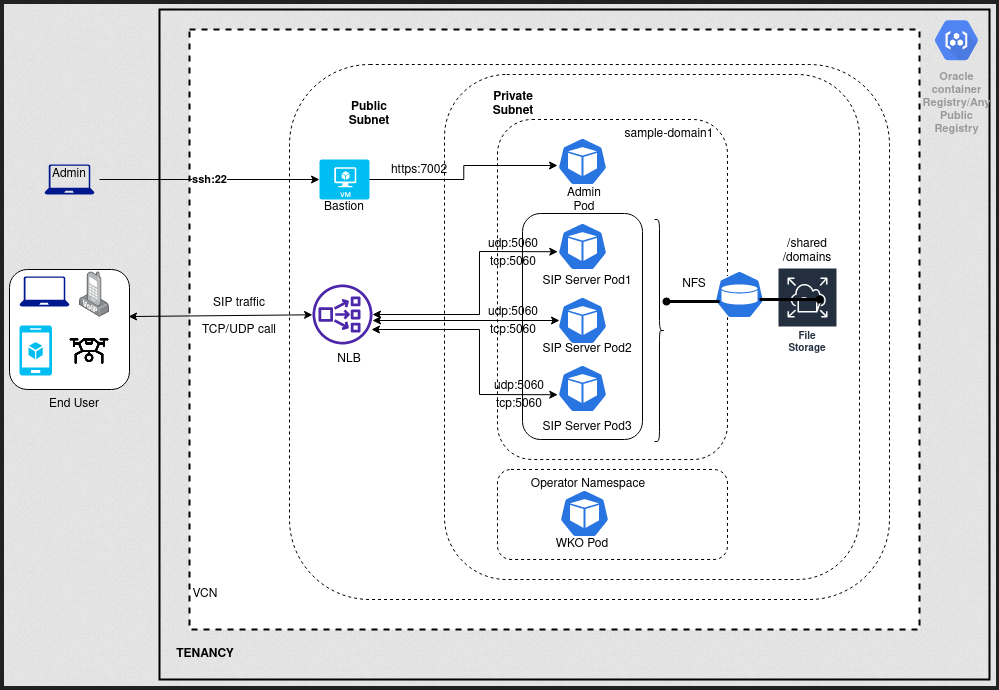
The Converged Application Server deployed with OKE uses the following OCI services:
- Container Engine for Kubernetes: The Container Engine for the Kubernetes cluster has three worker nodes so that the OCCAS-Coherence clusters themselves have the highest availability.
- File Storage: The domain configuration files are stored on shared storage that is accessible from all WebLogic servers in the cluster, on File Storage. Because of this setup, you don't need to rebuild Docker images for changes in the domain configuration, backup is faster and centralized, and logs are stored by default on persistent storage.
- Load Balancing: By default, the WebLogic servers (admin or clustered managed servers) created by the operator (WKO) are not exposed outside the Container Engine for Kubernetes cluster. The Converged Application Server uses the OCI Network Load Balancer, which supports TCP and UDP, to expose an application to the outside world.
- Registry: A Converged Application Server image can be pulled from https://container-registry.oracle.com/. Optionally, the Docker images can be stored in a private Oracle Cloud Infrastructure Registry repository.
Create the Kubernetes Cluster
Before creating a Kubernetes cluster, follow the steps in Preparing for Container Engine for Kubernetes to set the correct Identity and Access Management (IAM) policy.
- Log in to the Console for your OCI Tenancy.
- From the OCI Menu, select Developer Services and then Container Clusters (OKE).
- If the compartment has not been set, select your compartment from the left-hand drop-down list.
- Click Create Cluster and then Quick Create and then Submit.
- Enter a name for the cluster.
- Select the Kubernetes version.
- Select Managed Node type.
- Select the shape of each worker node in the cluster and the number of
nodes in each subnet.
To ensure the highest performance for those demanding workloads, Container Engine for Kubernetes allows you to select bare metal instances or even GPU instances on which to run your containers.
- Click Next and then Create cluster.
- After the cluster is created, you access the cluster in one of two
ways:
- Using kubectl in Cloud Shell
- Using kubectl installed locally
See Accessing a Cluster Using Kubectl for more information.
- Run
kubectl cluster-infoorkubectl config viewto confirm the configuration.
After the cluster has been created:
- Select Menu, and then Networking, and thenVNC.
- Note the subnets and their CIDR blocks.
Create and Configure the File Storage Service
When deployed with OKE, the Converged Application Server depends on the File Storage service.
- From the OCI Menu, select Storage and then Mount Targets under the File Storage section.
- Click Create Mount Target
- Select the VCN of your cluster and the subnet of your worker nodes.
If you require extra isolation, you may optionally setup additional VCN routing and security.
- Click Create.
- Select the created Mount Target.
- Under the Exports section, click Create Export to create a file system for the Persistent Volume.
- Accept the defaults and click Create.
Install the Kubernetes Weblogic Operator with OKE
The WebLogic Kubernetes Operator supports running your WebLogic Server domains on Kubernetes. It lets you encapsulate your entire WebLogic Server installation and layered applications into a portable set of cloud neutral images and simple resource description files.
kubectl get pods -n sample-weblogic-operator-ns[weblogic-kubernetes-operator]$ kubectl get pods -n sample-weblogic-operator-ns
NAME READY STATUS RESTARTS AGE
weblogic-operator-7885684685-4jz5l 1/1 Running 0 2m32s
[weblogic-kubernetes-operator]$Note:
If you are installing the EFK stack and setelkIntegrationEnabled to true, then the READY column will
display 2/2 when both containers are ready. If you are not installing the EFK stack
and left elkIntegrationEnabled as false, then the READY column will
display 1/1 when the container is ready.
Download Domain Creation Files
In addition to downloading the occas_generic.jar file,
you need to download the domain creation files.
Create a Persistent Volume
Create a persistent volume and a persistent volume claim to make the shared file system accessible from the pods.
Choose the Image
The Oracle Communications Converged Application Server image is located on the Oracle Container Registry.
Create Kubernetes Secret
Create a Kubernetes secret in order to pull from a private or public registry.