Privileged Access Management Integration
Introduction
Privileged Access Management (PAM) solutions eliminate the need for hard-coded application credentials embedded in applications, scripts, or configuration files, and allow highly sensitive passwords to be centrally stored, logged, and managed within the Vault. This unique approach enables organizations to comply with internal and regulatory compliance requirements of periodic password replacement, and monitor and audit privileged access across all systems, databases, and applications.
PAM solutions help provide secure privileged access to critical assets including database and hosts by centrally managing account passwords. PAM solutions provide access rules for both privileged and non-privileged accounts to control who can use those accounts to log on to your assets. As Enterprise Manager (EM) customers incorporate different PAM providers like CyberArk, Centrify, HashiCorp, Oracle Key Vault, etc. Now, we have an extensible Enterprise Manager credential framework that is integrated with PAM providers. This integration allows you to perform tasks such as active database management, database patching, and running host commands in a manner that is compliant with security compliance policies.
Here are some of the benefits of the PAM integration with Enterprise Manager:
-
It provides an extended credentials framework, utilizing an external store for secure management.
-
It facilitates the retrieval of database or host credentials from the repository or PAM Store and supplies them to EM subsystems, such as jobs and deployment procedures.
-
Given PAM's secure nature, the integration supports token-based authorization for access control.
-
With multiple PAM providers available, EM provides a registration system for PAM scripts to securely fetch credentials for databases and hosts stored in PAM.
-
The data model included enables mapping of credential attributes into EM Credential types.
-
It offers flexibility, allowing users to create new PAM-based named credentials or modify existing ones to retrieve credentials from an external store.
-
EM ensures secure password retrieval from PAM for databases or hosts, enabling tasks like job execution and database patching while adhering to established security policies.
Note:
PAM integration with Enterprise Manager only works with Named Credentials.
The diagram below depicts how EM interacts with PAM to retrieve the credentials for databases or hosts from an external store to carry out tasks in EM such as executing jobs on host or database patching using Fleet Maintenance.
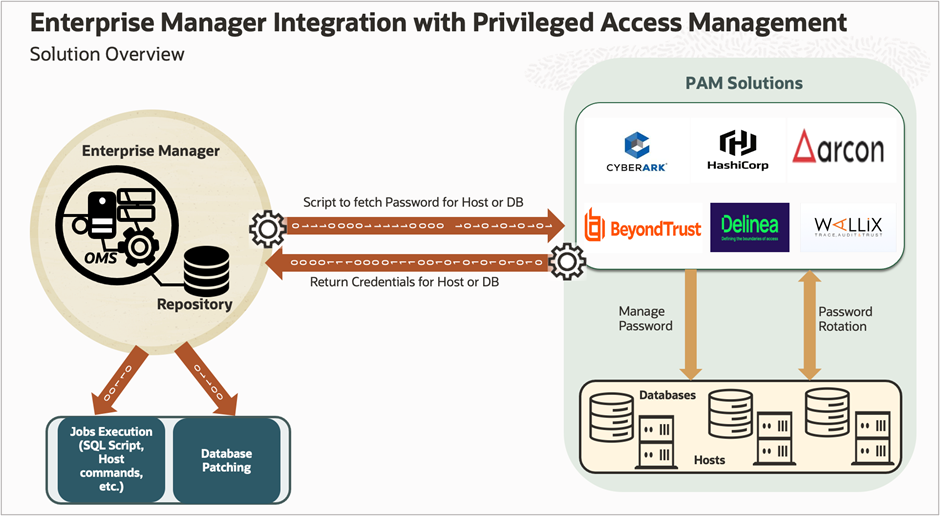
Using the PAM integration, EM retrieves database and host credentials that are stored in the external PAM store. To accomplish this, you need to write the integration script that will be registered in EM with all the PAM attributes. When EM requires the database or host credentials for workflows including database patching or running jobs, the credential framework interacts with the external PAM provider and retrieves the password for databases or hosts and passes that credential object to the underlying workflows.
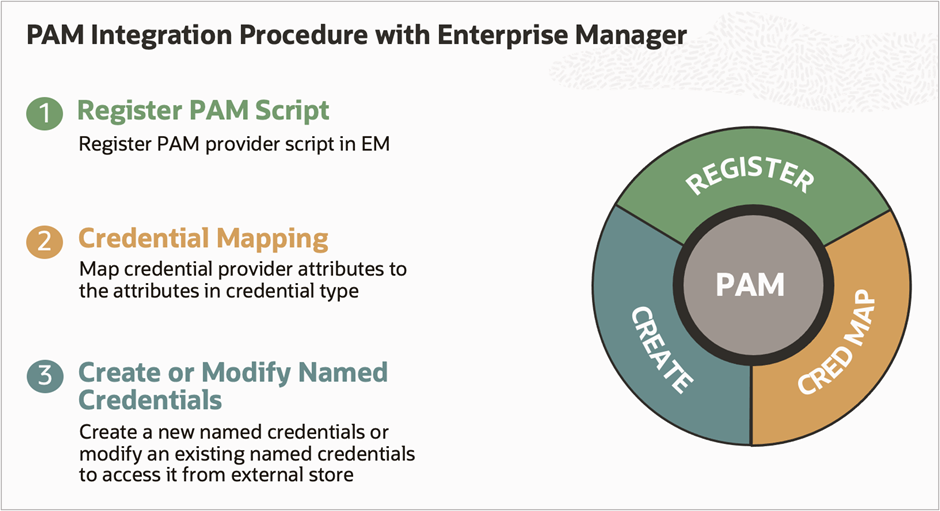
PAM integration with EM consists of three simple steps for all PAM providers.
Understanding the User Roles
The implementation of the PAM solution requires the collaboration of two key administrative roles: the EM Administrator and the PAM Security Administrator. These administrators jointly oversee the integration process, ensuring a seamless and secure setup.
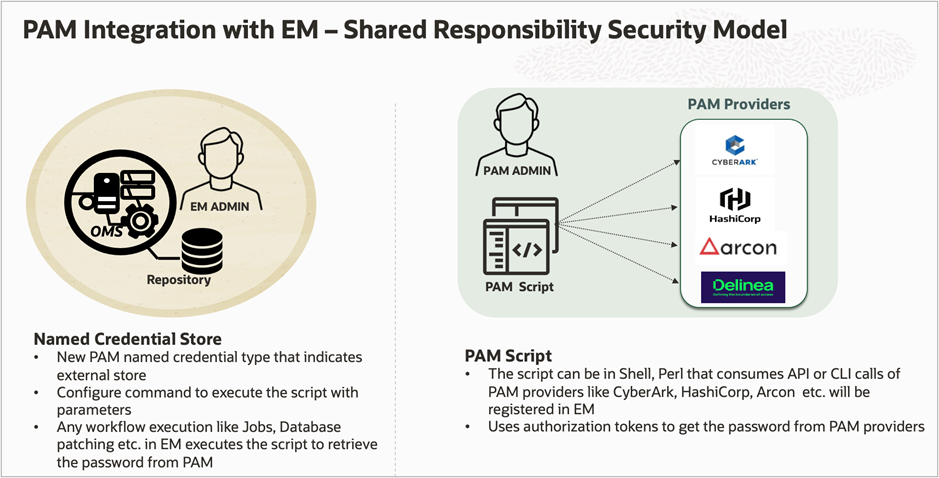
PAM Security Administrator Role
A PAM security team should guide the EM administrator team to build a script and provide the necessary parameters required for the script execution. This script is required to access the PAM provider using REST endpoints to retrieve credentials for databases or hosts at runtime. The script can be written in Shell or Perl.
EM Administrator Role
An EM Administrator, which is a predefined role within the EM system, is responsible for crafting the PAM script. This Administrator registers this script in EM and creates the necessary mappings using EM CLI.
Prerequisites
Minimum EM version required: Oracle Enterprise Manager 13c Release 5 Update 14 (13.5.0.14).
Configuration
Step 1: Develop a script to access PAM credentials
As a PAM Security Administrator, work with your Security or PAM team to develop a script for PAM tools such as CyberArk, HashiCorp, and Oracle Key Vault. This custom script connects to a PAM system and retrieves the necessary credentials. The script must meet the following requirements:
-
Must be written in Shell or Perl. Binary files are not supported.
-
Can use any method to fetch credentials like REST or command line tool.
-
Each credential stored in the PAM system can be referred to using a unique identifier, called a Credential Key. The Credential Key should also be passed on as an argument to the script. You can decide how the argument should be passed, for example any of the formats listed below:
sh getcreds.sh -k CredKeysh getcreds.sh -credkey CredKeysh getcreds.sh CredKey -
Credentials or authentication tokens required to authenticate a PAM system should be passed through
stdinaskey:valuepair, not specified in the script. Use one of the ways as shown below:-
The script only requires an authentication token to access the PAM system. When the script is run, it should prompt you to input the auth token via
stdin:sh getcreds.sh -k CredKey authtoken:token -
The script requires the PAM username and password for the PAM system authentication. Upon running the script, it requests you to provide the PAM username and password, which will be entered through
stdin:pamuser:user pampassword:password -
The script requires multiple authentication mechanisms to access the PAM system, including the PAM username, password, certificate path, and certificate key. When executed, the script will prompt you to input the PAM username and password, along with the certificate details:
pamuser:user pampassword:password pamcertpath:path pamcertkey:keyA script built to accept certain input parameters securely through
stdincan be configured as is in Enterprise Manager, so when EM executes the script it passes the values for such input parameters throughstdin.
-
-
The script should fetch and print the credentials in a name:value format as shown below.
sh getcreds.sh -k EMDB/sysman pamuser:user pampassword:passwordIn the above example, EMDB/sysman is the Credential key and user/password is the credential fetched from the PAM system.
-
The script should capture error/exception during execution. The errors should be formatted as string, and should be written to
stderrfor EM to read and show it in GUI and in calling subsystem processes. - The script will be run on any of the OMS hosts in a multi-OMS setup, so all the software installation and configuration required for script execution should be done on all the OMS hosts.
Step 2: Register the PAM Provider with EM
As an EM Administrator, register the PAM provider with EM using the EM CLI command emcli config_cred_provider.
This is a new verb that allows the credential provider to be configured with the required attributes.
emcli config_cred_provider
[-provider_name=\"provider name\"]
[-provider_type=\"provider type\"]
[-access_cred_type=\"cred type\"]
-params="params"
[-refparams="params"]
[-input_file="FILE:file_path"]
[-separator="separator:attribute_name:character"]
[-subseparator="subseparator:attribute_name:character"]
Options:
-
-provider_name: Name of the provider to configure and should contain only alphabets, numbers, hyphen(-) and underscore(_) and not exceed 64 characters. -provider_type: Credential provider type. The current allowed value isScriptProvider.-
-access_cred_type: The type of credential that is required to authenticate against this credential provider.Example: In case of using PAM user credentials to authenticate with PAM system then create named credentials of type "Host Credentials using the PAM user and password and provide
-access_cred_type="HostCreds"and then map the named credential to PAM provider created usingset_credprovider_cred. -
-params: Comma separated set of name=value pairs. It can be used in conjunction with- input_fileto specify tags to file paths that contain longer content.Example:
-params="Command:sh %ScriptFile% -key %CredKey%;StdInVars:CACertLoc,AuthToken;ScriptFileExt:sh;Script:getCyberArkPassword"-
Example commands that need to be run to fetch credential from PAM depending on the script type being used:
sh %ScriptFile% -key %CredKey%perl %ScriptFile% -k %CredKey%
ScriptFileandCredKeyare mandatory keywords, while%ScriptFile%will be replaced by the script file name (in OMS file system), and%CredKey%will be replaced by the credential key provided while creating the named credential. -
StdInVars: list of input parameters separated by comma that needs to be passed through standard inputExample:
StdInVars:AuthToken; StdInVars:CACertLoc,AuthToken; -
ScriptFileExt: supported script file extensions:shpl
Script: tag pointing to the actual script file path which will be defined in the parameterinput_file.
-
-
-input_file: to specify tag pointing to actual file path.Example:
-input_file="getCyberArkPassword:/u01/app/pam_scripts/getcreds.sh" -
-refparams: Comma separated set of name=value pairs. Can be used to map input parameters to integration script to any of three below mentioned OMS properties:- "oracle.sysman.core.security.auth.cred_provider_prop1"
- "oracle.sysman.core.security.auth.cred_provider_prop2"
- "oracle.sysman.core.security.auth.cred_provider_prop3"
Example:
sh getcreds.sh -k CredKey
pamuser:user
pampassword:password
authtoken:token./emcli config_cred_provider
-provider_name="CyberArk"
-provider_type=ScriptProvider \
-params="Command:sh %ScriptFile% -k %CredKey%;StdInVars:CACertLoc,AuthToken;ScriptFileExt:sh;Script:getCyberArkPassword"\
-input_file="getCyberArkPassToken:/u01/app/pam_scripts/getcreds.sh"\
-refparams="AuthToken:oracle.sysman.core.security.auth.cred_provider_prop1,CACertLoc:oracle.sysman.core.security.auth.cred_provider_prop2"Once the script is registered in EM, it is stored in the repository table EM_NC_CREDPROVIDER_PARAMS and you can run a select query to see the data. Here is an example of a query:
SELECT * FROM EM_NC_CREDPROVIDER_PARAMS;Note:
If you would like to re-create the PAM provider registration with EM, you can use the emcli delete_cred_provider command and then execute the emcli config_cred_provider command to re-create it.
Step 3: Create the Credentials Attributes Mappings
Credentials mappings map the keys in the script output (user and password in this example) to credential attributes like HostUserName and HostPassword. Store an attribute mapping to convert stored attributes to those required by credential type. In order to find the credential type attribute names, run the following command:
emcli get_credtype_metadata -authtargettype=<authenticating target type> -credtype=<credential type>For example, the following command lists the attribute names for HostCreds credential type and host target type.
emcli get_credtype_metadata -authtargettype=host -credtype=HostCredsRun the following command to create the credentials mappings:
emcli store_cred_mapping
-mapper_name="mapper name"
-mapper_desc="mapper description"
-cred_type="cred type"
-attributesmap="attributes map"Options:
-mapper_name: Name of the mapper.-mapper_desc: Description of the mapper-cred_type: Type of credential that this mapping is intended for.-attributesmap: Comma separated set ofname=valuepairs that maps attributes stored in the credential provider to attributes of the specified credential type.
Here are some examples of mappings for a host and a database:
-
Host
emcli store_cred_mapping -mapper_name="PAMtoHostCreds" -mapper_desc="Map PAM credential attributes to HostCreds type" -auth_target_type=host -cred_type="HostCreds" -attributesmap="user:HostUserName;pass:HostPassword" -
Database
emcli store_cred_mapping -mapper_name="PAMtoDBCreds" -mapper_desc="Map PAM credential attributes to DBCreds type" -auth_target_type=oracle_database -cred_type="DBCreds" -attributesmap="user:DBUserName;pass:DBpassword"
Once the credential mapping is created this information is stored in the EM repository tables EM_NC_CRED_MAPPERS and EM_NC_CRED_MAPPER_COLUMNS.
Here is an example to check in repository database:
SELECT m.mapper_name, m.cred_type_name, mc.storage_attr, mc.cred_attr FROM EM_NC_CRED_MAPPERS m, EM_NC_CRED_MAPPER_COLUMNS mc WHERE mc.mapper_guid = m.mapper_guid ORDER BY m.mapper_name;
Note:
If you want to re-create the credential mapping, you can use the emcli delete_cred_mapping command and then execute the emcli store_cred_mapping command to re-create it.
Case 1: If the username is not passed while creating the PAM based named credentials, then it should be returned in the script output as shown below.
Example: If you don’t pass the database username in the attributes while creating PAM based named credentials, then it should be returned in the script and mapped using the store_cred_mapping command for Enterprise Manager to understand.
./emcli create_named_credential
-cred_name=OEM_SYSPAM -auth_target_type=oracle_database
-cred_type=DBCreds
-alt_cred_storage
-cred_provider=PAM360
-cred_key="HRDB/sys"
-cred_mapping=PAM360toDBCreds
-attributes="DBRole:SYSDBA"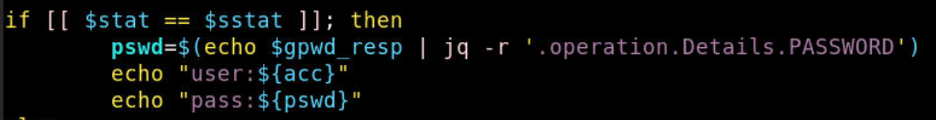
./emcli store_cred_mapping
-mapper_name="PAM360toDBCreds"
-mapper_desc="Map PAM 360 credential attributes to DBCreds type"
-auth_target_type=oracle_database
-cred_type="DBCreds"
-attributesmap="user:DBUserName;pass:DBpassword"Case 2: If the username is passed while creating the PAM based named credential, then the script can be built just to return the password as shown below:
Example: If you pass the DB username in the attributes while creating PAM based named credentials, then only the password can be returned in the script and mapped using the store_cred_mapping command for Enterprise Manager to understand.
./emcli create_named_credential
-cred_name=OEM_SYSPAMD
-auth_target_type=oracle_database
-cred_type=DBCreds
-alt_cred_storage
-cred_provider=PAM360
-cred_key="HRDB/sys"
-cred_mapping=PAM360toDBCreds
-attributes="DBUserName:sys;DBRole:SYSDBA"
./emcli store_cred_mapping
-mapper_name="PAM360toDBCreds"
-mapper_desc="Map PAM 360 credential attributes to DBCreds type"
-auth_target_type=oracle_database
-cred_type="DBCreds"
-attributesmap="pass:DBpassword"Step 4: Create or Modify the Named Credentials
Starting with Oracle Enterprise Manager 13c Release 5 Update 20 (13.5.0.20) credentials can be created using the CLI or the UI.
To create credentials using the UI, from the Settings drop-down menu, go to Security, and click Named Credentials. Click Create, and select the PAM radio button for the Credential Properties options.
Note:
To have the PAM option available in the UI, make sure to complete steps 2 and 3: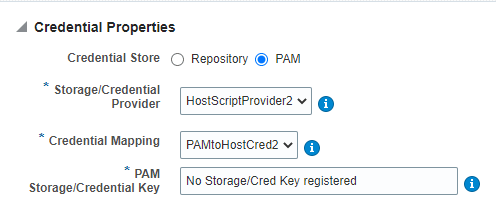
Follow the steps bellow to create the credentials as an EM Administrator, using the CLI:
-
Use an EM CLI verb to create the new credentials in EM with an alternate credential storage type. The following example creates the named credential ssh1 based on the SSH key named credentials for host myhost.example.com. It indicates that the credential attributes are stored in the OracleKeyVault credential provider at the location emssh1 and that the mapping named OKVSSHCreds can map the attributes required for the HostSSHCreds credential type.
emcli create_named_credential -cred_name=ssh1 -auth_target_type=host -cred_type=HostSSHCreds -target_name="myhost.example.com" -target_type=host -cred_scope=instance -alt_cred_storage -cred_provider=<PAM Provider> -cred_key=emssh1 -cred_mapping=OKVSSHCreds
-
Modify the Named Credentials as needed. Similar to create_named_cred, the modify_named_credential verb also takes the additional parameters : alt_cred_storage, cred_provider, cred_key, cred_mapping
The following example modifies the named credential ssh1 based on the SSH key named credentials for host myhost.example.com. It indicates that the credential attributes are stored in the OracleKeyVault credential provider at the location emssh1 and that the mapping named OKVSSHCreds can map the attributes required for the HostSSHCreds credential type.
emcli modify_named_credential -cred_name=<credential name> -auth_target_type=host -cred_type=HostSSHCreds -target_name="myhost.example.com" -target_type=host -cred_scope=instance -alt_cred_storage -cred_provider=OracleKeyVault-cred_key=emssh1 -cred_mapping=OKVSSHCreds
Examples:
emcli modify_named_credential -cred_name=ORACLE -cred_type=HostCreds -target_type=host -cred_scope=global -alt_cred_storage -cred_provider=PAM360 -cred_key="DBHost/oracle" -cred_mapping=PAM360toHostCreds
emcli modify_named_credential -cred_name=OEM_SYS -cred_type= DBCreds -auth_target_type=oracle_database -cred_scope=global -alt_cred_storage -cred_provider=PAM360 -cred_key="HRDB/sys" -cred_mapping=PAM360TODBCREDSThe credential name, type and owner, and storage provider and key, and mapper name are stored in the EM repository tables EM_NC_CRED_MAPPERS and EM_NC_CREDS.
Here is an example of a query of this data:
SELECT c.cred_owner, c.cred_type_name, c.cred_name, c.storage_provider, c.storage_key, m.mapper_name FROM EM_NC_CREDS c, EM_NC_CRED_MAPPERS m WHERE c.cred_name IN ('MANIDB_SYSMAN', 'DBSNMP_LOCAL') AND c.storage_cred_mapper_guid = m.mapper_guid (+) -
Validate the stored credential by querying the registered and configured PAM provider. The list_cred_mappings is a new verb that shows the result of the earlier store_cred_mapping requests. The list_credential_providers is a new verb that shows the result of the earlier config_cred_provider request.
emcli list_credential_providers
Lists the configured credential providers.
emcli list_cred_mappings -cred_type="cred_type" [-cred_owner="cred_owner"]
Lists the configured credential mappings for a given credential type (and optional credential owner).
Options:
-cred_type: lists the credential type for which the mappings are requested
At the completion of these steps, the PAM provider is registered with EM and either a new credential or a modified existing named credential is set up to use the external storage type.
Configuration of Multi-OMS Environments
PAM integration allows the use of the predefined OMS properties mentioned below to set the input parameters of the integration script. However, these OMS properties are local to each OMS and it is required to set values for the properties on each OMS as needed in the multi-OMS environment.
- oracle.sysman.core.security.auth.cred_provider_prop1
- oracle.sysman.core.security.auth.cred_provider_prop2
- oracle.sysman.core.security.auth.cred_provider_prop3
$ emctl set property
-name "oracle.sysman.core.security.auth.cred_provider_prop1"
-value "<value provided by your internal security team>"The rest of the setup steps should be executed only once from one of the OMS servers:
config_cred_provider(Step 2): should be executed only once from one of the OMS servers, and the script content will be stored in the database as a CLOB. The executable script is created in an internal EM directory on each OMS, whenever a PAM credential is invoked.store_cred_mapping(Step 3): should be executed only once from one of the OMS servers. The contents of the mapping is stored in the EM repository database, and will be used while processing the script output.create_named_credential/modify_named_credential(Step 4): should be executed from one of the OMS servers
PAM configurations supported in EM
Case 1
Use global OMS properties to store script input parameters for PAM system authentication. This is useful when you have a dedicated PAM user for the PAM system access.
"oracle.sysman.core.security.auth.cred_provider_prop1""oracle.sysman.core.security.auth.cred_provider_prop2""oracle.sysman.core.security.auth.cred_provider_prop3"
Example:
sh getcreds.sh -k CredKey
pamuser:user
pampassword:password
authtoken:token./emcli config_cred_provider-provider_name="CyberArk"\
-provider_type=ScriptProvider\
-params="Command:sh %ScriptFile% -k %CredKey%;StdInVars:CACertLoc,AuthToken;ScriptFileExt:sh;Script:getCyberArkPassword"\
-input_file="getCyberArkPassToken:/u01/app/pam_scripts/getcreds.sh"\
-refparams="AuthToken:oracle.sysman.core.security.auth.cred_provider_prop1,CACertLoc:oracle.sysman.core.security.auth.cred_provider_prop2"Case 2
Use a named credential to store the PAM authentication details like the PAM user credentials. This is useful when you use individual PAM credentials for the PAM system access.
-
The script that prompts you to enter PAM user details:
sh getcreds.sh -k CredKey pamuser:user pampassword:password -
Create a config cred provider with access to the credential type HostCreds:
./emcli config_cred_provider-provider_name="CyberArk"\ -provider_type=ScriptProvider\ -access_cred_type="HostCreds"\ -params="Command:sh %ScriptFile% -k %CredKey%;StdInVars:CACertLoc,AuthToken;ScriptFileExt:sh;Script:getCyberArkPassword"\ -input_file="getCyberArkPassToken:/u01/app/pam_scripts/getcreds.sh"\ -refparams="AuthToken:oracle.sysman.core.security.auth.cred_provider_prop1" -
Create a named credential to store PAM user details:
emcli create_named_credential -cred_name="PAMCreds" -auth_target_type=host -cred_type=HostCreds -attributes="HostUserName:pam_username;HostPassword:pam_password" -
Set credential to be used for cred provider:
emcli set_credprovider_cred -provider_name= CyberArk -cred_name="PAMCreds"
Typical Use cases
The PAM integration with EM provides a key benefit for the Database Lifecyle Management capabilities, the patching with Fleet Maintenance in particular. This integration allows the use of named credentials stored with PAM to be used during patching tasks.
Patching with Fleet Maintenance
Here are some examples of use cases you can try using Fleet Maintenance. For more information, see Database Fleet Maintenance
Frequently Asked Questions about PAM Integration with Enterprise Manager
- What are the components of a PAM integration script?
- How does Enterprise Manager read errors resulting from running the PAM integration script?
- How does the PAM integration script get stored within EM and how does EM handle tampering with the script?
- How do you map the script output to an Enterprise Manager credential object?
- What are the parameters to be passed in the config_cred_provider EM CLI command?
- What are the available global parameters to be used with the PAM integration feature in EM?
- What are the file permissions to be set on the script to register a PAM provider in EM?
- How do you avoid long running times of the PAM integration script?
What are the components of a PAM integration script?
The PAM Integration script Includes: inputs, processing logic and outputs:
-
Inputs: parameters passed to the script by Enterprise Manager.
-
Body: processing logic that depends on PAM product/solution.
-
Outputs: the script output that Enterprise Manager reads and maps to the credential object.
As mentioned above, Enterprise Manager only understands the PAM integration script inputs and outputs.
- Inputs to script are configured while creating the PAM credential provider using the
emcli config_cred_providercommand. - The script output is mapped to Enterprise Manager credential object using the
emcli store_cred_mappingcommand.
How does Enterprise Manager read errors resulting from running the PAM integration script?
Enhance the PAM integration script to catch all the errors/exceptions and write all error messages to stderr for Enterprise Manager to process as shown below:
-
Write to
stderrin the shell script using the syntax:echo "error message" 1>&2
Enterprise Manager reads the error messages from the stderr and shows them in the graphical interface, and when calling sub-system processes, such as jobs and deployment procedures.
Example: Error message written to stderr will be shown in EM GUI and EM Jobs as shown below.
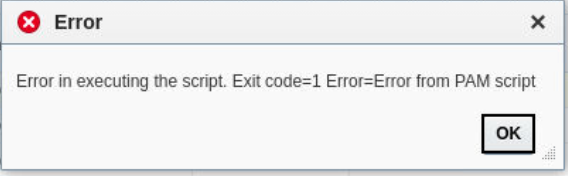
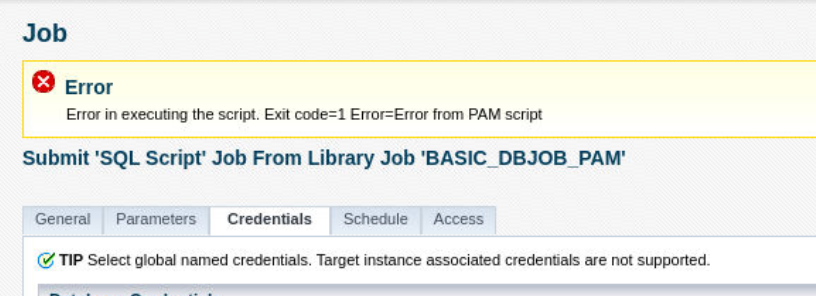
How does the PAM integration script get stored within EM and how does EM handle tampering with the script?
Step 1: Enterprise Manager supports script in Shell and Perl.
The contents of the script are stored in the repository database as CLOB data when the emcli config_cred_provider command is executed to register the script in EM.
Step 2: When the PAM based named credential is invoked after executing emcli config_cred_provider:
- It creates the executable integration script stored as CLOB in the EM repository in the internal EM directory.
- If the script file already exists, EM validates the checksum of the script in the internal directory with the checksum of the script in the form of CLOB data, and if the checksum value is the same for both, then it continues to use the integration script in the path. If not, it creates a new integration script file in the EM internal directory with the new CLOB data for the script execution. Any subsequent PAM credential invocation uses the same integration script file in the path which is already created if it is not tampered by any user, or updated by executing the
emcli config_cred_provider.
Any tampering or security breach of the script is addressed within Enterprise Manager using checksum validation as explained above.
How do you map the script output to an Enterprise Manager credential object?
Case 1
If the username is not passed while creating the PAM based named credential, then the script output should include username as shown below:
Example: If you don’t pass DB username in the attributes while creating PAM based named credential, then it should be included in the script output and map it using store_cred_mapping command for Enterprise Manager to read it from script output and map it to EM credential object.
./emcli create_named_credential
-cred_name=OEM_SYSPAM
-auth_target_type=oracle_database
-cred_type=DBCreds
-alt_cred_storage
-cred_provider=PAM360
-cred_key="HRDB/sys"
-cred_mapping=PAM360toDBCreds
-attributes="DBRole:SYSDBA"./emcli store_cred_mapping
-mapper_name="PAM360toDBCreds"
-mapper_desc="Map PAM 360 credential attributes to DBCreds type"
-auth_target_type=oracle_database
-cred_type="DBCreds"
-attributesmap="user:DBUserName;pass:DBPassword"Case 2
If the username is passed while creating the PAM based named credential, then the script can be built just to return the password in the output as shown below:
Example: If you pass the DB username in the attributes while creating the PAM based named credential, then only the password can be returned in the script output, and map it using the store_cred_mapping command for Enterprise Manager to read it from the script output and map it to the EM credential object.
./emcli create_named_credential
-cred_name=OEM_SYSPAMD
-auth_target_type=oracle_database
-cred_type=DBCreds
-alt_cred_storage
-cred_provider=PAM360
-cred_key="HRDB/sys"
-cred_mapping=PAM360toDBCreds
-attributes="DBUserName:sys;DBRole:SYSDBA"./emcli store_cred_mapping
-mapper_name="PAM360toDBCreds"
-mapper_desc="Map PAM 360 credential attributes to DBCreds type"
-auth_target_type=oracle_database
-cred_type="DBCreds"
-attributesmap="pass:DBPassword"What are the parameters to be passed in the config_cred_provider EM CLI command?
emcli config_cred_provider
[-provider_name=\"provider name\"]
[-provider_type=\"provider type\"]
-params="params"
[-refparams="params"]
[-input_file="FILE:file_path"][-separator="separator:attribute_name:character"]
[-subseparator="subseparator:attribute_name:character"]Options:
-provider_name: Name of the provider to configure. Name should contain only alphabets, numbers, hyphen(-) and underscore(_) and not exceed 64 characters.
-provider_type : Optional. Credential provider type. This must be one of the supported provider types: ScriptProvider.
-params : Comma separated set of name=value pairs.
-input_file: to specify tags to file paths that contain longer content.
-refparams: Comma separated set of name=value pairs. Can be used to map PAM provider parameters to OMS properties such as: "oracle.sysman.core.security.auth.cred_provider_prop1".
Note:
config_cred_provider: if executed for the first time, it behaves like a creation, and later executions with the same provider_name behaves like a modification. To modify any of the provider details, execute the emcli config_cred_provider command with the same provider name.
What are the available global parameters to be used with the PAM integration feature in EM?
As part of this feature, Enterprise Manager has three global parameters configured to be used for storing PAM parameters, such as authentication token and authentication details.
Customer can use any of the below pre-configured parameters for the PAM integration.
oracle.sysman.core.security.auth.cred_provider_prop1
oracle.sysman.core.security.auth.cred_provider_prop2
oracle.sysman.core.security.auth.cred_provider_prop3
What are the file permissions to be set on the script to register a PAM provider in EM?
Only read permission are required to be set for the script while executing the emcli config_cred_provider command. EM reads the contents of the script and stores them as CLOB data in the EM Repository.