Kerberos and RADIUS Authentication
In addition to logging in to a target database using a conventional username and password, you can also use named credentials to administer Oracle Databases in your Enterprise Manager environment. Enterprise Manager named credentials support both Kerberos (Username/Password and Keytab) and RADIUS credential types.
- Basic management operations accessed through a direct database connection from the Enterprise Manager Management Server (e.g. Users page)
- Database performance pages, including Performance Hub
- Execute SQL and SQL script jobs
This section covers the following:
Kerberos Keytab
To use Kerberos Keytab for database target authentications, you create a named credential in Enterprise Manager of type DBKerberosKeytabCreds where you define a username and ketyab file. There are two ways in which a keytab file can be implemented:
Upload the Content of the Ketyab File to the OMS/Repository
You can physically upload the content of the keytab file to the OMS and repository in much the same way SSH-based credentials are defined. When defining the named credential with the DBKerberosKeytabCreds credential type, Enterprise Manager will use this keytab to log in and connect to the database target. You will need to update the keytab contents in Enterprise Manager whenever the keytab is changed due to password being rotated by updating the named credential.
The following graphic illustrates how to specify the keytab file when creating a named credential.
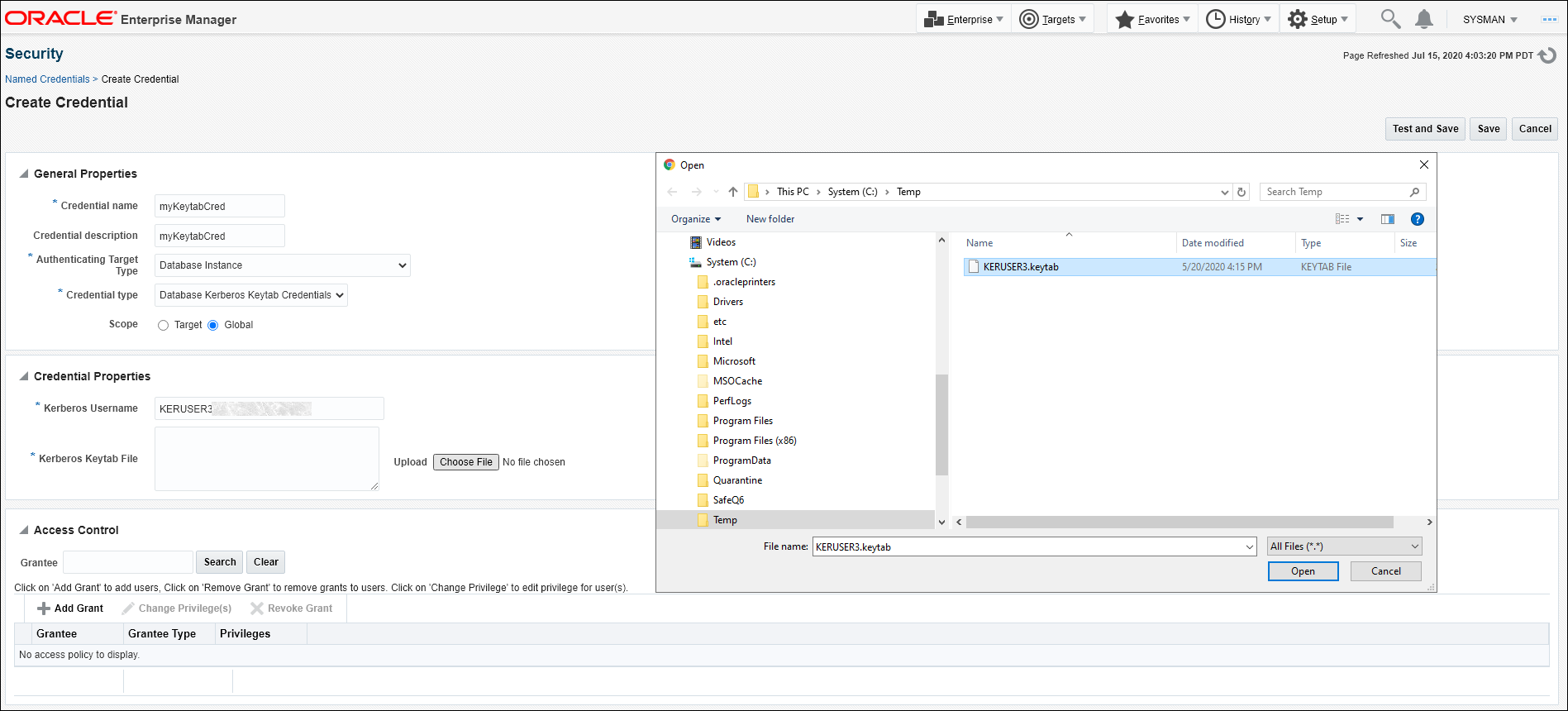
Provide the Full Path to the Keytab File
You can also provide the full path to the keytab file that is accessible from the OMS (or each of the OMSes for multi-OMS environments). The keytab file must be present at the same location on the filesystem (this could be a single copy of the keytab file that is NFS mounted) and secured with the appropriate file permissions that would allow the OMS user to have at least read access to it. You will need to keep the file in this location updated with any changes to the keytab. This can be done completely independently and outside of Enterprise Manager.
The following graphic illustrates how to define instances of the DBKerberosKeytabCreds credential type.
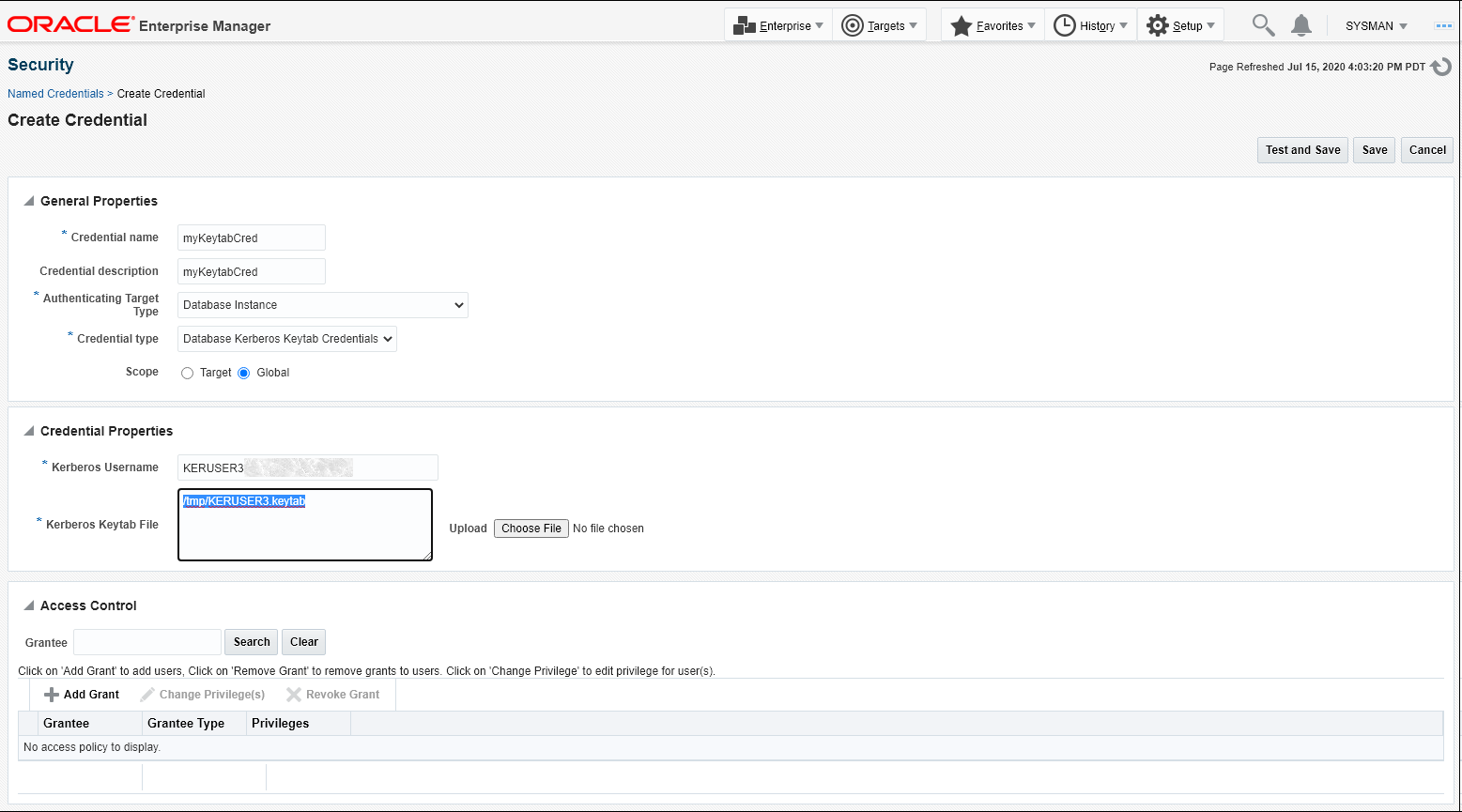
One-time Database Target Login Using Any Supported Credential Type
You can perform one-time database target login using any of the supported credential types, instead of being forced to pre-define a named credential and then use that to log in to the database target. This is useful in situations where you do not want to save any credentials or keytab files in Enterprise Manager and want to use a local file (say on your laptop) to log in each time. This file can then be updated independent of Enterprise Manager.
When you select the New radio button for Credential on the database login page, a drop down menu displays allowing you to select from a list of credential types enabled for the database target.
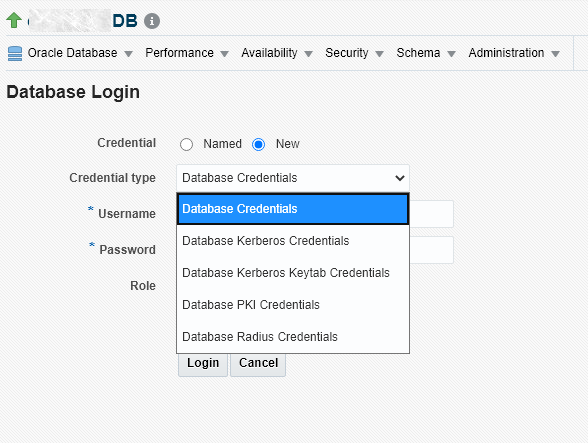
Enabling One-time Login
You enable one-time login using multiple credential types as well as enabling support for the two new credential types (RADIUS and Kerberos Keytab) via the OMS property oracle.sysman.db.multiCredTypeLogin.
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true
A value of false (or property not set) will disable this functionality and revert to the authentication functionality from Oracle Enterprise Manager 13c Release 5 Update 5 (13.5.0.5) and earlier. The default value is false if the property is absent.
Customizing the Credential Type Selection Menu for One
You can customize the list of credential types that appear in the Credential Type selection menu for one-time login shown above via the following OMS properties :
emctl set property -name oracle.sysman.db.enable_radius_auth -value trueEnable RADIUS. Default is false if property is absent.
emctl set property -name oracle.sysman.db.enable_kerberos_auth -value trueEnable both Kerberos-based credential types for one-time login on the database login page. The default is false if the property is absent.
Note:
None of the above property setting/changes require a restart of the OMS.
Example:
Say you want to enable one-time login to database targets using Kerberos username-password or Kerberos username-keytab. You would set the following OMS properties to enable the credential type drop-down on the database login page:
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true
AND
emctl set property -name oracle.sysman.db.enable_kerberos_auth -value true
If the above OMS properties are not set, you will still be able to define named credentials for Kerberos or RADIUS and use those to log into the database targets.
RADIUS
You can log into a target database as a database user that is externally authenticated using RADIUS. Although the entire process is transparent from an Enterprise Manager client perspective, specific connection parameters need to be specified via JDBC during the database login. The database itself acts as a RADIUS client and passes information from the database client (Enterprise Manager) to the RADIUS server to authenticate the user. RADIUS-based login only supports synchronous authentication mode.
Note:
Choosing the RADIUS authentication option requires users who log into the target database be aware that RADIUS authentication is necessary.
Synchronous Login
Enterprise manager supports one-time database login using RADIUS by setting following OMS properties:
emctl set property -name oracle.sysman.db.enable_radius_auth -value true
AND
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true
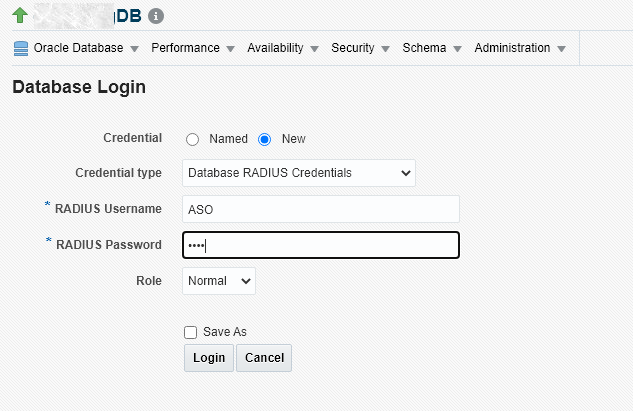
Enabling the RADIUS authentication type provides a full-fledged RADIUS credential type that will prompt for the username and password, as shown in the following graphic.
Co-existance with an Earlier Version of Radius Authentication
If you are using the existing option of specifying the OMS RADIUS property and used the Enable Radius checkbox in the database login UI, set the following OMS properties as shown below to revert back to the original behavior for RADIUS credentials.
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value false (or unset this property if previously set via emctl delete property -name oracle.sysman.db.multiCredTypeLogin)
emctl add property -name oracle.sysman.db.enable_radius_auth -value true
Upgrade Implications
If you are currently using this feature via the OMS RADIUS property being set, an upgrade to the latest version will NOT result in any visible changes, by default. You can explicitly enable the new RADIUS credential type and enable multi-login support with both the DBCredsType and DBRadiusCredsType options being displayed in the drop-down selection for one-time login by explicitly setting emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true
You will need to unset the OMS property for multiCredTypeLogin mentioned above to false (or delete the property) to revert to original behavior if desired or will now need to define new named credentials of type DBRadiusCreds to log in to target database using RADIUS
Setting the following parameters will return RADIUS authentication to the original Enterprise Manager 13c Release 4 behavior on the one-time login screen.
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value falseOR
emctl delete property -name oracle.sysman.db.multiCredTypeLoginYou must also ensure the follwing property continues to be set:
emctl add property -name oracle.sysman.db.enable_radius_auth -value false (or remove the property)Setting Kerberos/RADIUS-based Named Credentials as Preferred Credentials
Two credential sets are created specifically for Oracle database, RAC database, and PDB target types.
The credential sets are:
- Normal Database Credentials (Advanced)
- SYSDBA Database Credentials (Advanced)
You can associate predefined Named Credentials of type Kerberos/Kerberos Keytab or RADIUS to these credential sets.
Note:
If you define a Named Credential with Role SYSDG, then these Named Credentials can be associated with the SYSDBA Database Credentials (Advanced) credential set as it is assumed that you are using SYSDG-based user credentials in lieu of accessing the database targets as a user with SYSDBA role.There are three ways to set Kerberos/RADIUS credential types as Preferred Credentials on database targets.
- Set Named Credentials from the Enterprise Manager Console
- Define and Set a Kerberos/RADIUS Credential as a Preferred Credential via the One-Time Database Login Option
- Set Kerberos/RADIUS credentials as Preferred Credentials using emcli
Set Named Credentials from the Enterprise Manager Console
First, create and save Named Credentials of type
RADIUS or KERBEROS. Then,
you can set RADIUS/Kerberos credential types as Preferred
Credentials on databases and related targets directly
from the Enterprise Manager console. To access the Preferred
Credentials page, from the Setup menu, select Security and
then Preferred Credentials. Select your target type and click
Manage Preferred Credentials.
Define and Set a Kerberos/RADIUS Credential as a Preferred Credential via the One-Time Database Login Option
You can set the following OMS properties to enable a one-time database login using a new RADIUS/Kerberos credential type.
emctl set property -name oracle.sysman.db.enable_radius_auth -value true
emctl set property -name oracle.sysman.db.enable_kerberos_auth -value true
emctl set property -name oracle.sysman.db.multiCredTypeLogin -value true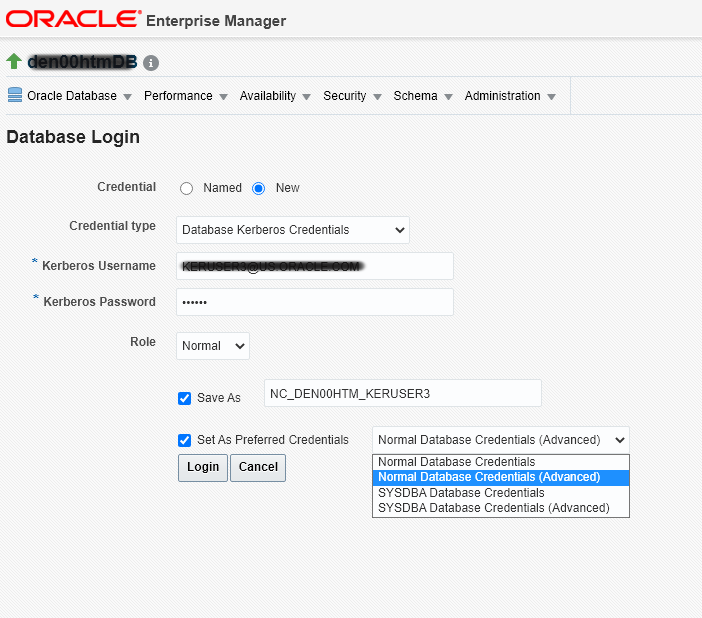
Once the above Preferred Credentials are set on the database and/or related target, they can be used for underlying jobs (like ExecuteSQL or SQLScript) that support these advanced credentials types.
Logging in from the Enterprise Manager console to the target is similar to using regular database (username/password) Preferred Credential sets. For example if Normal Database Credentials (Advanced) is set as a Preferred Credential for a given database target (and Normal Database Credentials is NOT set), navigating to any Enterprise Manager console page for this database target (requiring a database login as a user with Normal role) will result in an auto-login to the database target as this Kerberos/RADIUS user that is represented by the Preferred Credential being set.
Set Kerberos/RADIUS
Credentials as Preferred Credentials Using
emcli
You can use emcli to associate
Kerberos/RADIUS-based Named Credentials as Preferred Credentials on
a database or related target using emcli commands
shown in the following examples.
To set a SYSDBA Kerberos-based Named Credential as a Preferred Credential on the database target emdb020DB:
emcli set_preferred_credential -set_name="DBCredsSYSDBAASO" -target_name="emdb020DB" -target_type="oracle_database" -credential_name="NC_EMDB020D_KEYTAB_SYSDBA" To set a Normal RADIUS based Named Credential as a Preferred Credential of type Normal Database Credentials (Advanced) on the database target den01csgDB:
emcli set_preferred_credential -set_name="DBCredsNormalASO" -target_name="den01csgDB" -target_type="oracle_database" -credential_name="NC_DEN01CSG_ASO" Propagation of Kerberos/RADIUS Subject and Role Across Database Logins
When you log into a database target as a Kerberos/RADIUS user and then navigate to a UI page in the Enterprise Manager console to access another database target that requires a database login with a specific role, Enterprise Manager will log in automatically using the original Kerberos user and role if that user is a valid user on the second database.
However, if there is a Preferred Credential defined for the second database with the appropriate role, then that Preferred Credential will be used for the DB login instead of the cached Kerberos credentials.
Example:
The DataGuard Administration page requires a database login with as a SYSDBA user. If there is a Kerberos/RADIUS Preferred Credential set defined for the database target under SYSDBA Database Credentials (Advanced) and no SYSDBA database credentials are defined, then accessing the DataGuard Administration page for the first time on a database target will result in an auto-login using the Kerberos/RADIUS credentials defined as a Preferred Credential on defined as a Preferred Credential for the SYSDBA Database Credentials (Advanced) credential set.
If both SYSDBA Database Credentials AND SYSDBA Database Credentials (Advanced) are defined on the same target, then the regular SYSDBA database credential set will take precedence.