Guidelines for Managing Target Credentials
Preferred Credentials simplify access to managed targets by storing target login credentials in the Management Repository. Users can access an Enterprise Manager target that recognizes those credentials without being prompted to log into the target. Preferred credentials are set on a per user basis, thus ensuring the security of the managed enterprise environment. Default credentials can be set for a particular target type as well as target credentials for a particular target. The target credentials override the default credentials.
Do not set preferred credentials for group/common accounts such as SYSMAN. If preferred credentials are set for common accounts, then the accountability of the use of these credentials is lost. The following SQL statements can be used to report the list of users who have the preferred credentials set:
SELECT t.target_name,tc.user_name,tc.credential_set_name FROM MGMT_TARGET_CREDENTIALS tc, MGMT_TARGETS t WHERE tc.target_guid=t.target_guid SELECT t.target_name,tc.user_name, tc.set_name FROM EM_TARGET_CREDS tc, MGMT_TARGETS t WHERE tc.target_guid=t.target_guid and tc.user_name = 'SYSMAN'
Credentials can be stored as Named Credentials and then privileges granted to other users to use, update or own the credentials. These credentials can be used for jobs, patching or other administration tasks on specific targets or globally. Eligible credential types include username/password, SSH-key for host and Kerberos for database. This method allows administrators to configure Named Credentials for privileged access and grant to specific users. Auditing tracks Named Credential creation, modification and usage.
Named Credentials provide a secure mechanism in Enterprise Manager to allow for separation of privilege management from privilege delegation for targets. Using Named Credentials an organization can separate the management of the specific username/password/authentication details from the actual authority to use these credentials. This is an essential tool in modern, secure organizations where there needs to be certainty that a malicious user cannot conduct operations outside Enterprise Manager using a set of known credentials obtained from inside Enterprise Manager. Additionally, the management of a central set of Named Credentials removes a significant burden on the proliferation of credentials information across many Enterprise Manager administrators and also therefore reduces the likelihood of these being used outside the Enterprise Manager environment or helps prevent against the accidental publication of credentials.
Automate Monitoring and Non-monitoring User Credential Password Management
Password lifecycle management plays a crucial role in maintaining a secure database (DB) environment. This becomes a burden when dealing with hundreds or perhaps thousands of databases. This typically involves changing the password for a user and then updating all Enterprise Manager configurations that use this password for monitoring or managing a database.
Enterprise Manager lets you use the job system to automate database password change/rotation tasks for both monitoring and non-monitoring database users with the respective jobs: Change the Password for the Database Monitoring User and Change the Password for a Database User. Both job types let you schedule jobs on Oracle Database and Cluster Database instances.
You can either explicitly specify a new password or optionally auto-generate a new password using either the current password or an explicitly specified Reference Password as the basis for auto-generation. Once Enterprise Manager changes the password to a generated one, this auto-generated password will not be known to anyone but Enterprise Manager and its components, e.g., the agent. Any target-scoped named credentials for the user will also be updated. The user-defined password option typically makes sense for a one-time scheduled job since manually having to run this job periodically will not effectively change the password across job runs. Having Enterprise Manager auto-generate random passwords is more effective from a security standpoint.
Note:
This job does not have the ability to understand password policy updates and new security standards and expects the specified password (when Auto-Generate is selected as No) or reference password to be compliant with current password policies in effect on the databases. When using Yes (Based on Current Password) the expectation is that the current password is compliant with the password policies in effect.
IMPORTANT: Both jobs, (Change the Password for the Database Monitoring User and Change the Password for a Database User), support users in Data Guard environments with SYSDBA and SYSDG privileges except the SYS user itself. To change the password on the standby database, it relies on the Oracle Database 12.2 and higher feature of auto-propagating passwords from the primary database to the standby database. It does not support changing monitoring passwords for Data Guard environments with either a Far Sync or Snapshot Standby database.
Warning Regarding Data Guard Environments
If there is a significant (> 1 minute) apply lag to any standby instance, the standby instance may be briefly shown as down in Enterprise Manager after the job completes until the new password is updated on the standby via redo log apply.
Automatic Password Management works for the following situations:
Beginning with Oracle Enterprise Manager 13c Release 5 Update 4 (13.5.0.4)
- Monitoring users for DB targets, DBSNMP and custom (Non-DBSNMP)
- Non-monitoring user with NORMAL on the Enterprise Manager repository target
Beginning with Oracle Enterprise Manager 13c Release 5 Update 6 (13.5.0.6)
- Monitoring and non-monitoring users with SYS* (SYSDBA, SYSDG, etc.)
roles, including DB users with SYS roles for the Enterprise Manager
repository target.
Note:
This feature is also available with Oracle Enterprise Manager 13c Release 4 Update 18 (13.4.0.18).
Beginning with Oracle Enterprise Manager 13c Release 5 Update 12 (13.5.0.12)
- Support specifying a Reference Password which can be used (instead of the current password) as a basis for password auto-generation
This section discusses the following topics:
Automate Monitoring User Password Management
You can automate password management for users (monitoring only) that discovered database instances in Enterprise Manager console via the Change the Password for the Database Monitoring User job type.
When an Oracle database is installed, a DBSNMP user is provisioned out-of-the-box that is primarily used for monitoring that database from Enterprise Manager. The DBSNMP username and password are used both during discovery and for collecting metrics from the Enterprise Manager agent. DBSNMP is also used when collecting metrics that show up on the database home page in the Enterprise Manager console. Alternatively, you may choose to use a different user (Non-DBSNMP) as the database monitoring user.
Password rotation is a normal part of the security policy for all users, and this typically applies to the DBSNMP user or any other dedicated monitoring user as well. This task usually involves changing the password for this database user (DBSNMP or Non-DBSNMP) and then updating all Enterprise Manager configurations that use this password for monitoring/administrating that database. A new password can be user-specified or auto-generated by Enterprise Manager.
IMPORTANT: The password change job should be used for DBSNMP (or other monitoring users) configured with the Normal Role, SYSDBA, or SYSDG and where Enterprise Manager is the only product/user attempting to access the actual database as this user. See Automate Monitoring and Non-monitoring User Credential Password Management for more information.
Required Target Privileges
- CONFIGURE_TARGET
- CONNECT_TARGET
- BLACKOUT_TARGET
- EDIT_CREDENTIAL (monitoring and any saved named credentials)
Note:
The EDIT_CREDENTIAL privilege is required because the job blacks out the targets and updates the credentials/monitoring configuration both on the target and in Enterprise Manager as well as updating any named credentials for this database user in Enterprise Manager.
Configuring and Scheduling the Job
-
From the Enterprise menu, choose Job and then Activity. On the Activity page, click Create Job. The Select Job Type dialog displays.
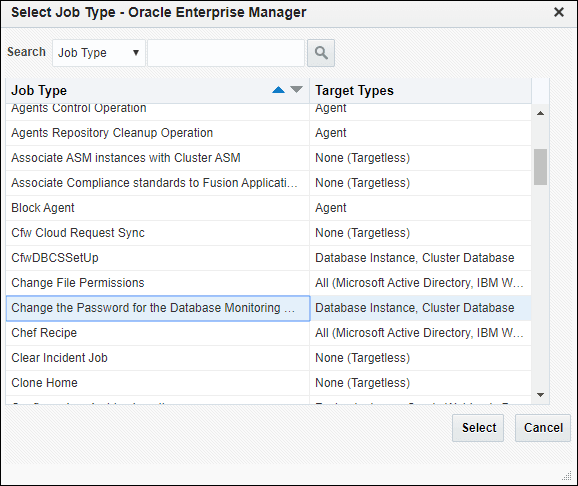
Choose the Change the Password for the Database Monitoring User job type and click Select.
-
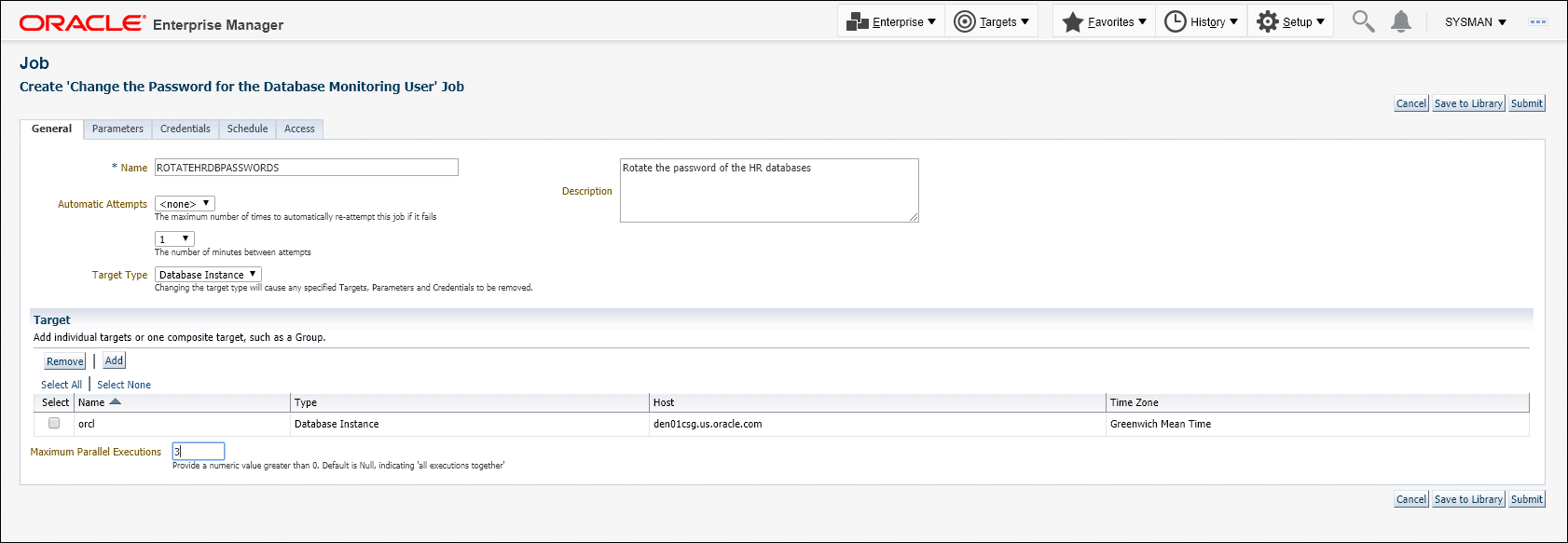
Define the job by specifying the required attributes (Job Name, Description, etc.) as well as selecting list of targets on which to schedule/run the job.
Note:
Instead of selecting a list of targets, you could also create a dynamic group and select the group. When selecting a dynamic group, all instances of type Oracle Database and Cluster Database present in the group will have the monitoring user passwords updated when the job is executed.If there are a large number of targets being selected, it is recommended to specify a reasonable number of Maximum Parallel Executions for your environment (around 3) so that all of these jobs are not executed in parallel. Running large numbers of jobs in parallel will not only overload the job system, but also cause your targets to be in blackout concurrently.
-
Specify a New Password if you do not want Enterprise Manager to auto-generate a password as shown below.
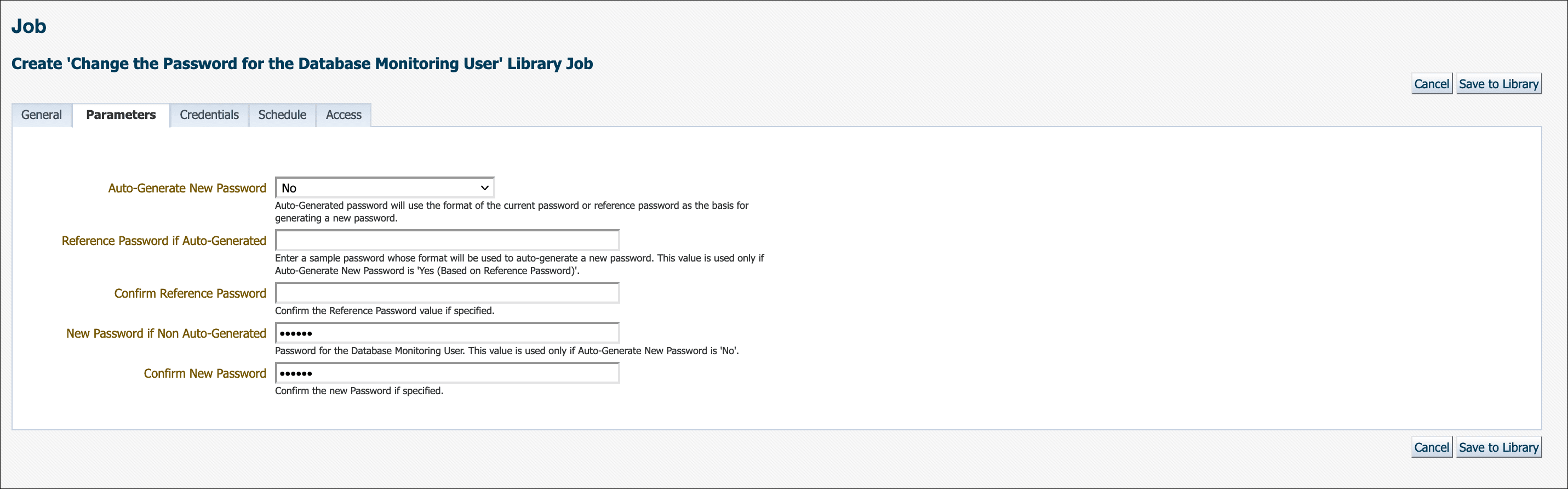
Auto-Generate New Password must be set to No. Enter the new password. If the new password and confirmation do not match, an inline error message will appear and you will not be able to submit the job.
If no parameters are specified in the Parameters tab, then a new password will be generated. Auto-generated passwords are only known to and managed by Enterprise Manager.
There are two explicit options for Auto-Generate New Password. Initially, auto-generating a new password used only the format of the current password as the basis for generating a new one. Beginning with Enterprise Manager 13c Release 5 Update 12 (13.5.0.12), there is now an additional option to auto-generate a new password based on the reference password. This means that you can enter a sample password in the provided field and Enterprise Manager will use the format of the sample as the basis for auto-generating a new password.
Note:
When selecting Auto-Generate New Password: Yes (Based on Reference Password) you must ensure your sample/reference password is compliant with your current enterprise's password policies for Enterprise Manager to auto-generate a new compliant password. This option is useful for when your password policy changes (e.g., minimum password length increases) and the current password is no longer compliant and thus needs to be changed.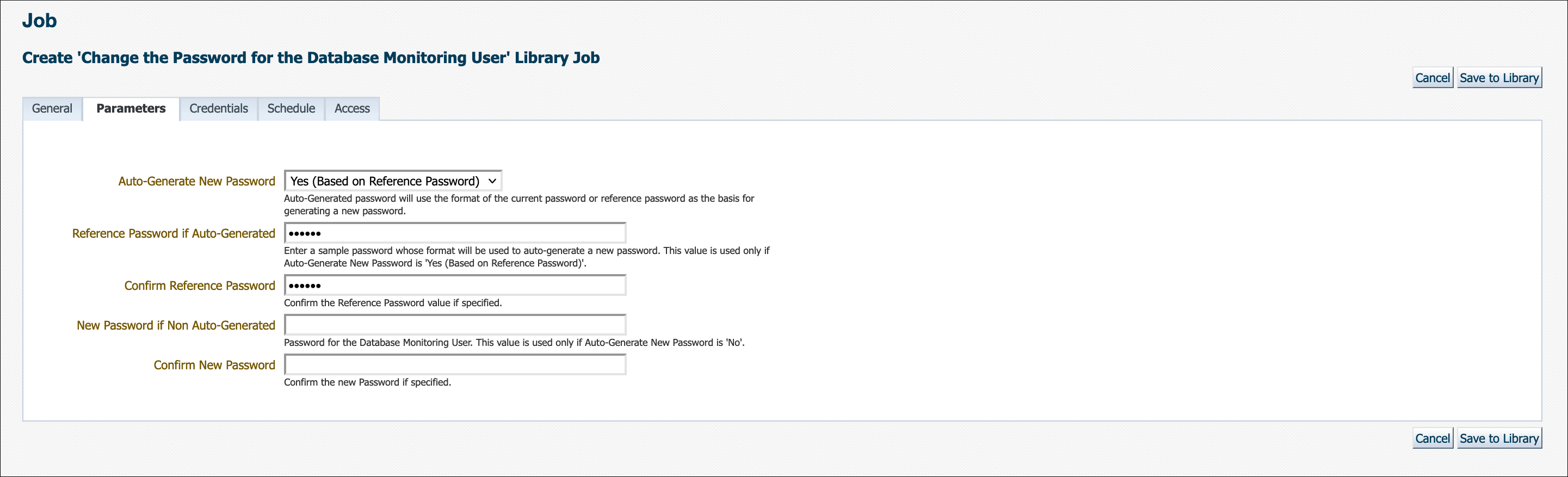
-
Define a schedule for this job. This would typically be the interval after which the monitoring user password needs to be changed as per the password profile defined for the database.
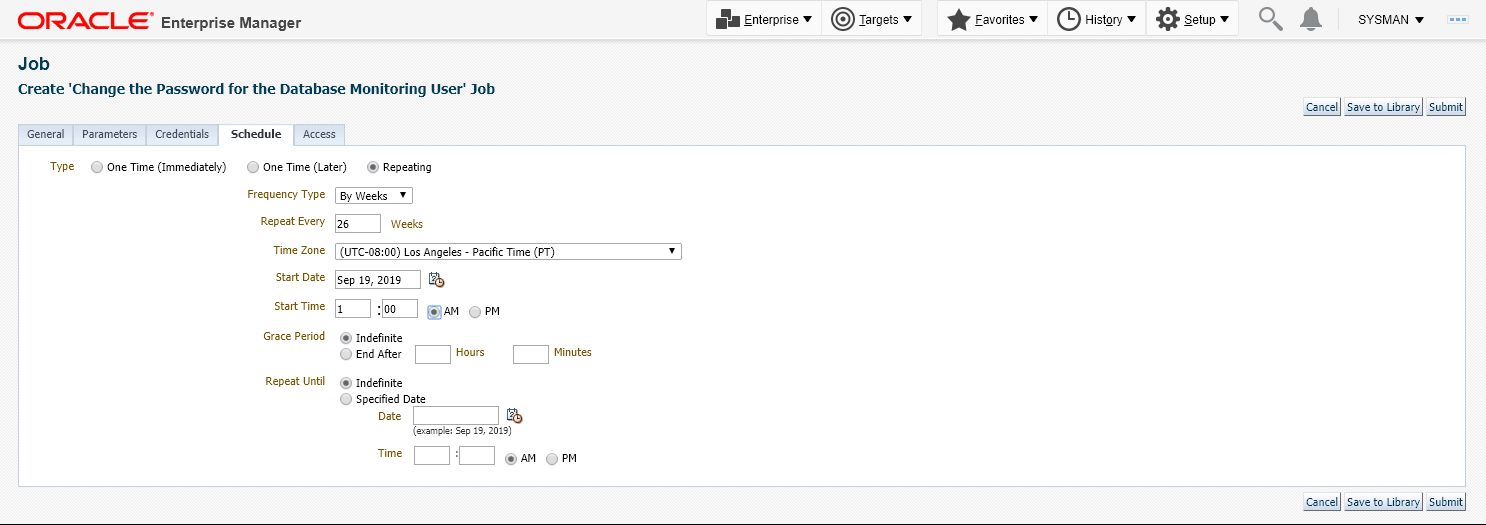
Click Submit.
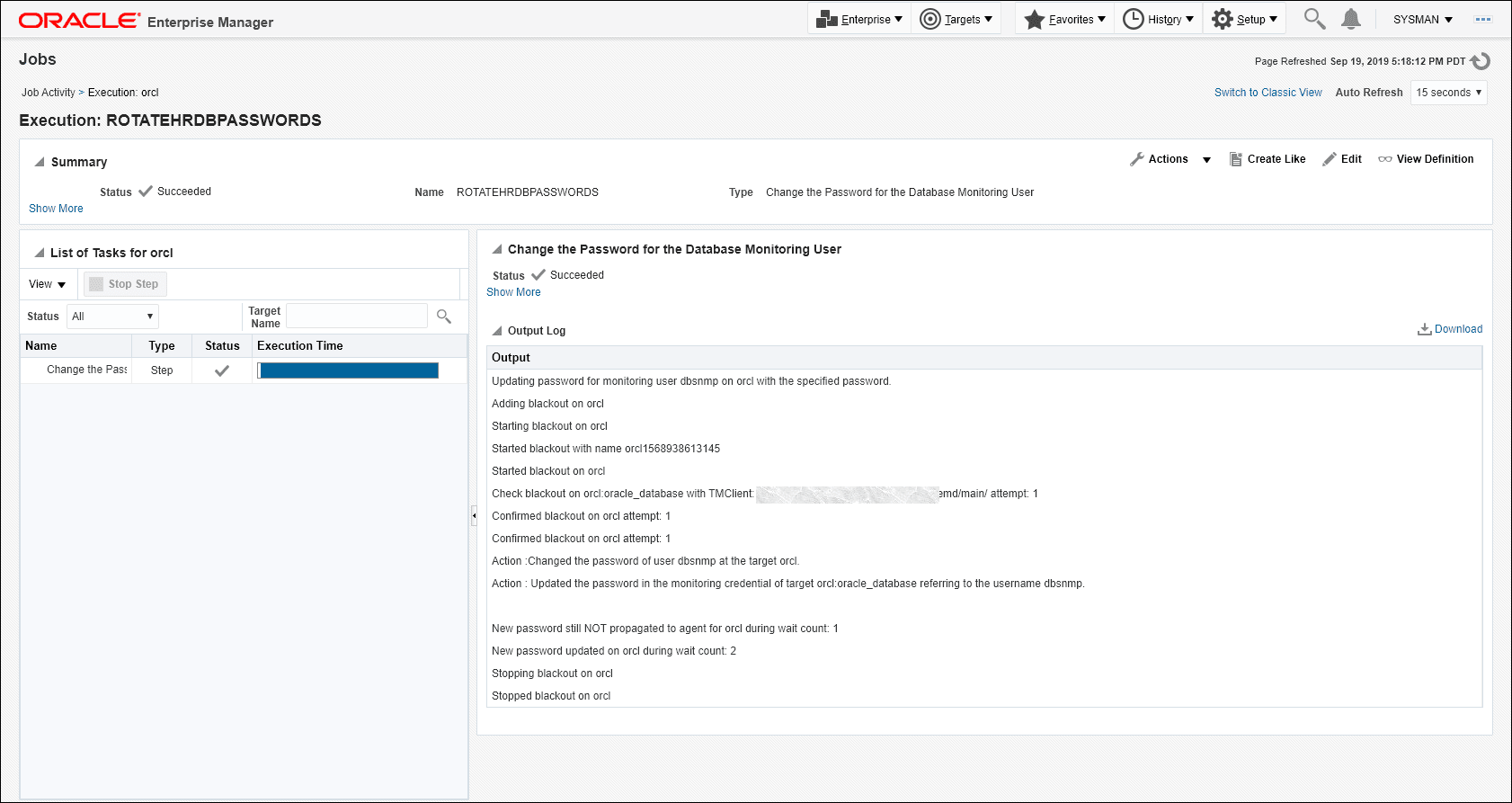
Viewing the job run output (executions per target)
You can view the status/output of the password change job by clicking on the job name in the Job Activity table as shown below.
Automate Non-monitoring User Password Management
For custom non-monitoring database users, you can use the Change the Password for a Database User job type to automate password management. This task usually involves changing the password for this database user and then updating all Enterprise Manager configurations that use this password for monitoring/administrating that database. For more information, see Automate Monitoring and Non-monitoring User Credential Password Management.
Note:
Custom monitoring credentials (based on user-defined credential sets) will also be updated if these credentials are defined for the user specified in the job parameters.
In order to execute this job type, you must have the following Enterprise Manager privileges.
- CONNECT_TARGET
- CONFIGURE_TARGET
- EDIT_CREDENTIAL
Note:
This privilege is required for the target-scoped Named Credential on the target for the user specified in the job parameter. - CREATE_JOB
Note:
This privilege is needed to create and submit the job.
This job requires the username to be specified as an input argument to the job and expects a named credential with a valid current password to be defined on the database target(s) on which the job is invoked.
Configuring and Scheduling the Job
-
From the Enterprise menu, choose Job and then Activity. On the Activity page, click Create Job. The Select Job Type dialog displays.
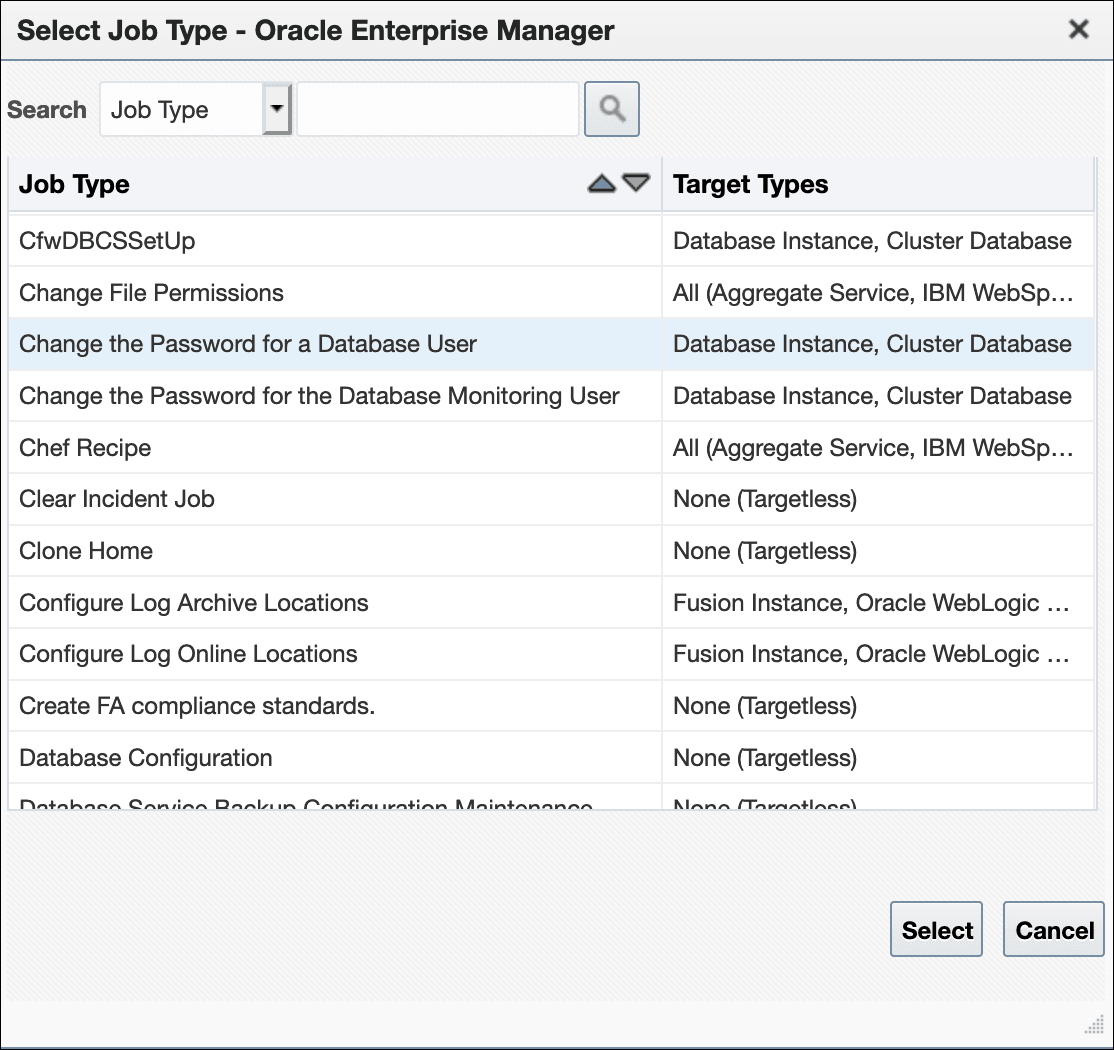
-
Choose the Change the password of the Database User job type and click Select.
-
Define the job by specifying the required attributes (Job Name, Description, etc.) as well as selecting list of targets on which to schedule/run the job.
Note:
Instead of selecting a list of targets, you could also create a dynamic group and select the group. When selecting a dynamic group, all instances of type Oracle Database and Cluster Database present in the group will have the database user passwords updated when the job is executed.If there are a large number of targets being selected, it is recommended to specify a number reasonable for your environment (around 3) so that all of these jobs are not executed in parallel. Running large numbers of jobs in parallel will not only overload the job system.
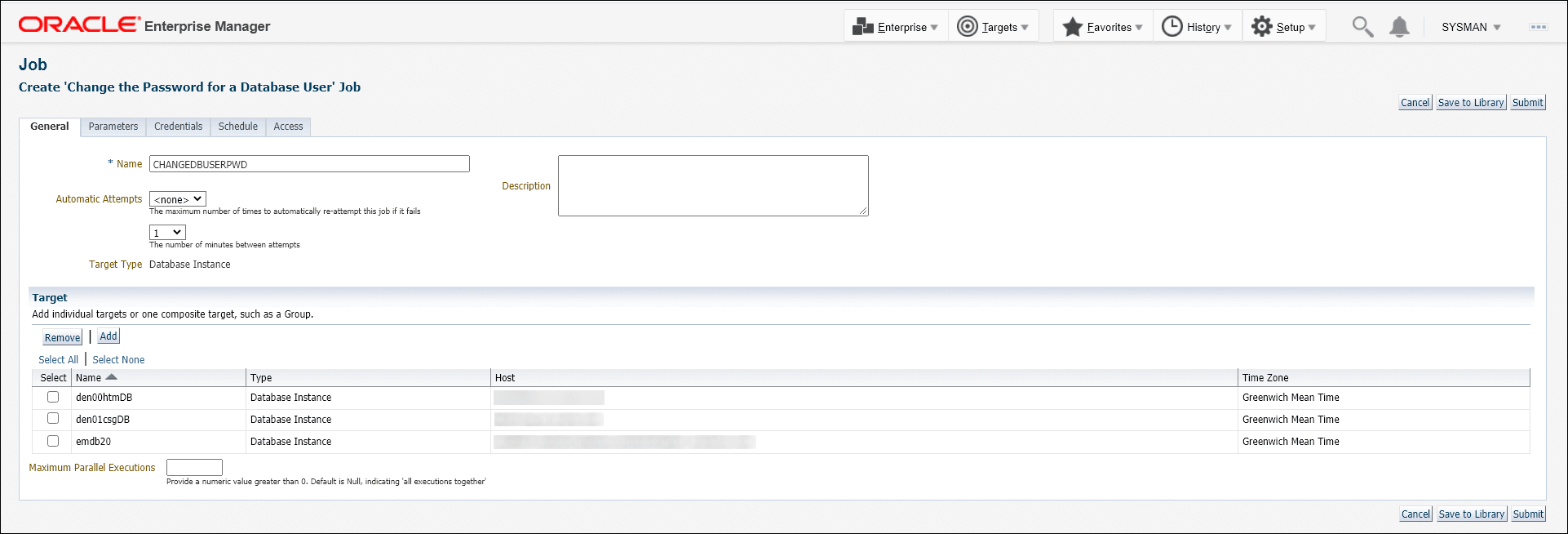
-
Define the job type Parameters. In this case the Database User is the user whose password needs to be changed/rotated. The job will check for the existence of ONE and only ONE Named Credential defined on each of the database instances defined for the job. The job will generate an error if there are no Named Credentials or more than one Named Credentials defined for this user on a DB target that is specified for the job. An error will also occur if this user is the default Monitoring user for the DB target.
-
Specify a New Password if you do not want Enterprise Manager to auto-generate a password as shown below.
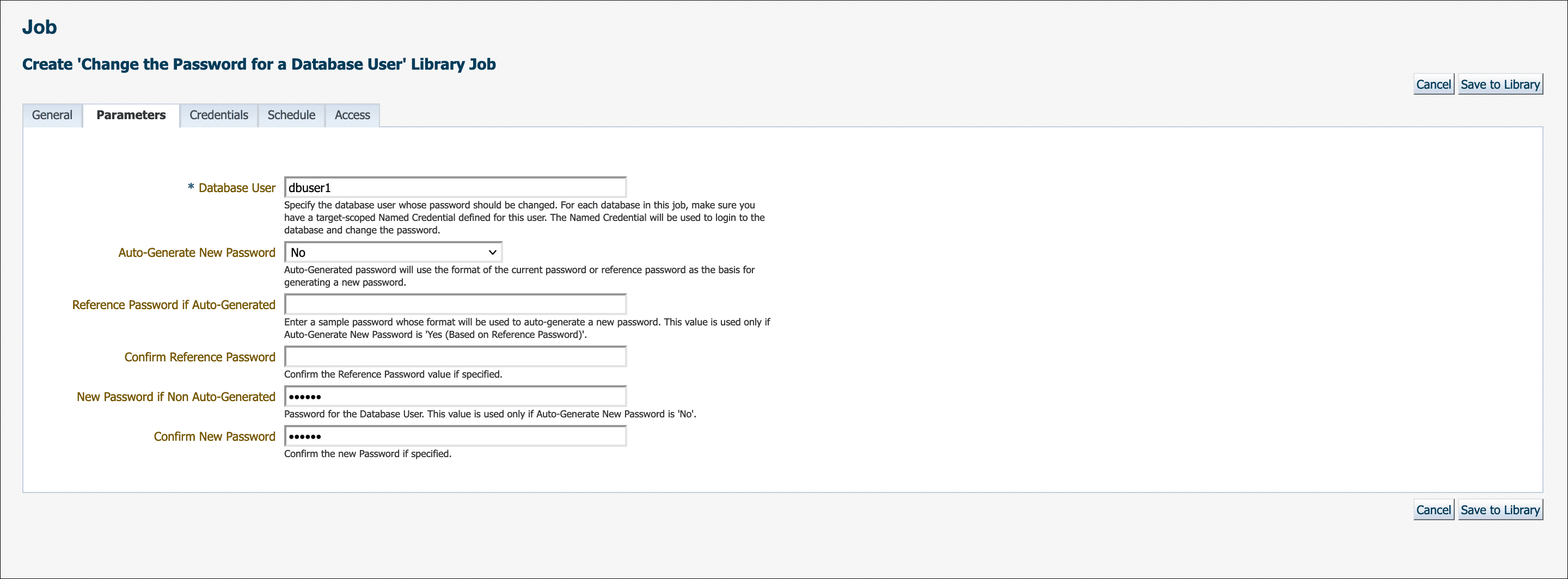
Auto-Generate New Password must be set to No. Enter the new password. If the new password and confirmation do not match, an inline error message will appear and you will not be able to submit the job.
If no parameters are specified in the Parameters tab, then a new password will be generated. Auto-generated passwords are only known to and managed by Enterprise Manager.
There are two explicit options for Auto-Generate New Password. Initially, auto-generating a new password used only the format of the current password as the basis for generating a new one. Beginning in Enterprise Manager 13c Release 5 Update 12 (13.5.0.12), there is now an additional option to auto-generate a new password based on the reference password. This means that you can enter a sample password in the provided field and Enterprise Manager will use the format of the sample as the basis for auto-generating a new password.
Note:
When selecting Auto-Generate New Password: Yes (Based on Reference Password) you must ensure your sample/reference password is compliant with your current enterprise's password policies for Enterprise Manager to auto-generate a new compliant password. This option is useful for when your password policy changes (e.g., minimum password length increases) and the current password is no longer compliant and thus needs to be changed.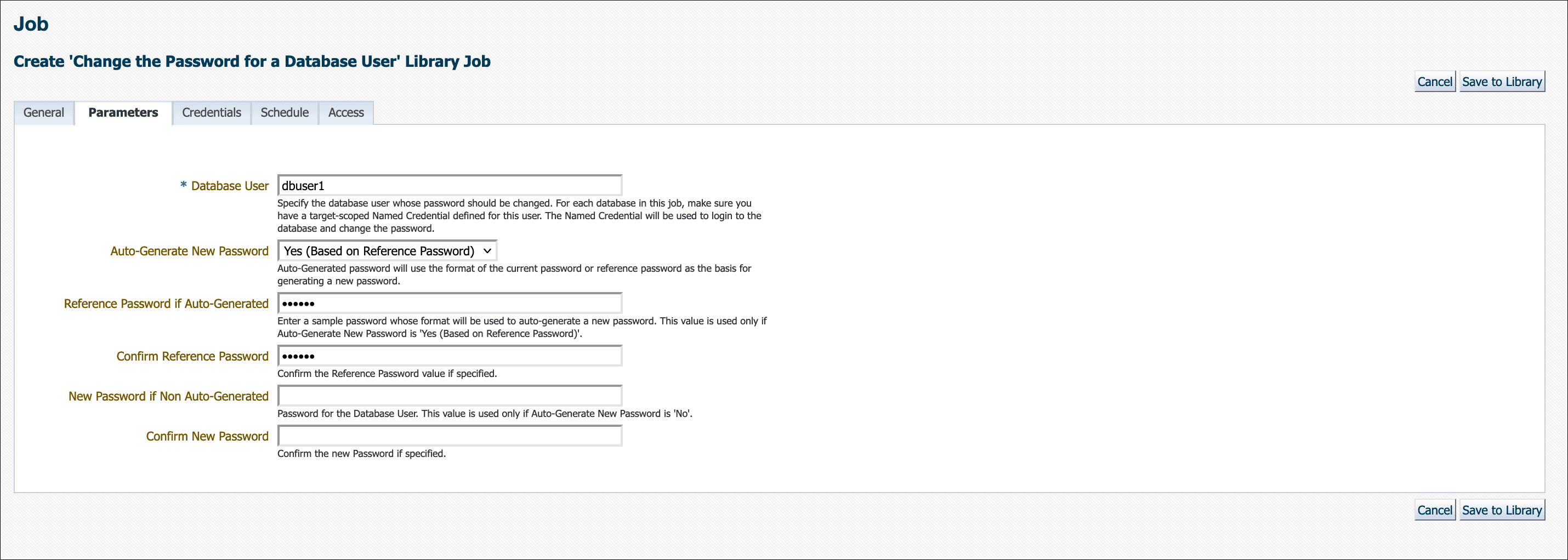
-
Define a schedule for this job. This would typically be the interval after which the monitoring user password needs to be changed as per the password profile defined for the database.
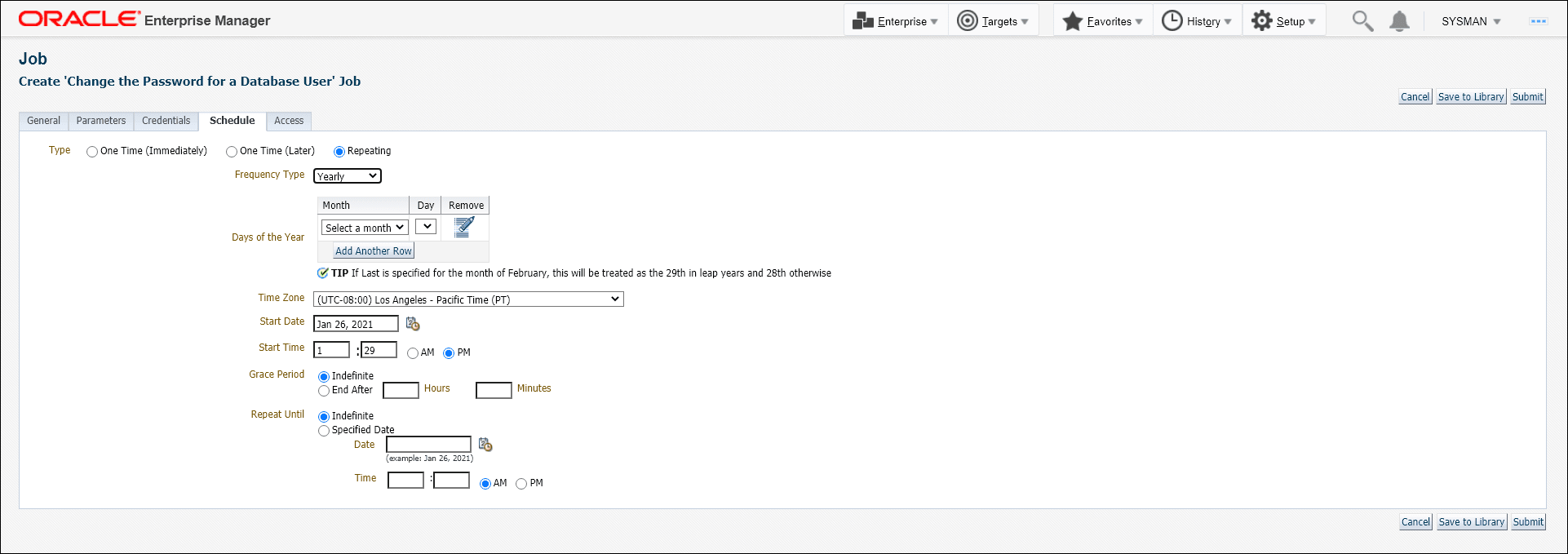
Click Submit.
Best Practices for Credentials
-
Use EMCLI to automate routine password changes on privileged named credentials, this allows one administrator to know and update the password for granted users.
-
Utilize named credentials when setting preferred credentials to simplify credential management.
-
Do not set preferred credentials for group/common accounts such as SYSMAN.