Configuring Authentication
Enterprise Manager authentication is the process of determining the validity of the user accessing Enterprise Manager. The authentication feature is available across the different interfaces such as Enterprise Manager console and Enterprise Manager Command Line Interface (EM CLI).
Enterprise Manager's authentication framework consists of pluggable authentication schemes that let you use the type of authentication protocol best suited to your environment.
Note:
Oracle Enterprise Manager relies on the underlying WebLogic Server that is part of the OMS stack for external Authentication methods. For this reason, Enterprise Manager can be authenticated using any authentication method that is supported by Oracle WebLogic Server. Note that only some providers have been certified so far although theoretically it should be possible to configure for all.
Supported Authentication Schemes
Enterprise Manager supports the following authentication schemes:
-
Repository-Based Authentication:
This scheme involves saving the administrator's username and password in the Enterprise Manager repository and performing validation against these saved values whenever a user logs on to the Enterprise Manager console. An Enterprise Manager user created is also a repository (database) user. By using this option, you can take advantage of all the benefits of Oracle database user management that this authentication method provides such as password control through the password profile, enforced password complexity, password life time, and number of failed attempts allowed. During the password grace period, the administrator is prompted to change the password but when the password has expired, it must be changed. For more details, refer to Creating a New Administrator.
-
Enterprise User Security Based Authentication: The Enterprise User Security (EUS) option enables you to create and store enterprise users and roles for the Oracle database in an LDAP-compliant directory server. After the Enterprise Manager repository is configured with EUS, you can configure Enterprise Manager to use EUS as its authentication mechanism as described in Enterprise User Security Based Authentication. You can register any EUS user as an Enterprise Manager administrator.
In addition to using EUS to authenticate Enterprise Manager administrators, it can also be used to simplify management of database target credentials. EUS helps centralize the administration of users and roles across multiple databases. If the managed databases are configured with EUS, the process of logging into these databases is simplified. When you drill down to a managed database, Enterprise Manager will attempt to connect to the database using Enterprise Manager credentials. If successful, Enterprise Manager will directly connect you to the database without displaying a logon page.
-
LDAP Authentication Options: Oracle Internet Directory and Microsoft Active Directory
-
Oracle Internet Directory (OID) Based Authentication - Oracle Internet Directory is a LDAP v3 compliant directory built on the Oracle database and is fully integrated into Oracle Fusion Middleware and Oracle Applications. Therefore, it is ideally suited for Oracle environments or enterprises with Oracle database expertise. When using an authentication scheme based on OID as the identity store, you can have your applications authenticate users against the OID.
-
Microsoft Active Directory Based Authentication - Microsoft Active Directory is a directory service that provides authentication and authorization functionality in a Windows network. When using a Microsoft Active Directory as an identity store, you can plug in this scheme to have your applications authenticate users against the Microsoft Active Directory.
Note:
Enterprise Manager will support external authentication as long as the specific authentication scheme is supported and integrated with the WebLogic Server.
-
-
RADIUS Synchronous Authentication: This scheme can be enabled by setting a property value using either the command line or the UI:
- Open a terminal window and execute the following command:
$ORACLE_HOME/bin/emctl set property -name oracle.sysman.db.enable_radius_auth -value true - When creating a new credential or editing an existing named credential, click the RADIUS Authentication checkbox.
- Open a terminal window and execute the following command:
-
Security Assertion Markup Language (SAML): SAML is a standard that enables seamless, single sign-on (SSO) login into applications. It works by transferring the user’s identity from one place (the identity provider) to another (the service provider) through an exchange of digitally signed XML documents. Oracle Enterprise Manager supports SAML version 2.0.
To configure Enterprise Manager with SAML-based login, follow these steps:
-
The Service Provider Configuration requires ldap parameters. Run the command in the primary OMS and additional OMS(s). Command format:
<OMS Home>/bin/emctl config auth saml_service_provider -ldap_type <LDAP type> -ldap_host <LDAP host> -ldap_port <LDAP port> -ldap_principal "cn=<LDAP principal>" -user_base_dn cn=<user base> -group_base_dn cn=<group base> -ldap_credential <LDAP password> -enable_auto_provisioning -use_ssl -cert_file <full path to the cert file>- The supported values for
ldap_typeare AD and OID. enable_auto_provisioningis an optional parameter with the default value false. If true, external user is created in EM Repository if the user did not exist earlier.use_sslis an optional parameter with the default value false. If true, the ldap provider generated is SSL enabled.
The following example configures SSL enabled ldap provider of type OID running on server with host myhost.example.com, port 3131, auto-provisioning enabled,
OMS Homeat /u01/app/oracle/middleware, and configures saml service provider:/u01/app/oracle/middleware/bin/emctl config auth saml_service_provider -ldap_type oid -ldap_host myhost.example.com -ldap_port 3131 -ldap_principal "cn=orcladmin" -user_base_dn cn=Users -group_base_dn cn=Groups -ldap_credential password -enable_auto_provisioning -use_ssl -cert_file /tmp/certSample output:
Oracle Enterprise Manager 24ai Release 1 Copyright (c) 1996, 2024 Oracle Corporation. All rights reserved. Configuring SAML Authentication ... StartedSAML Service Provider configured Weblogic configuration file modified Configuring SAML Authentication ... Successful Configuring LDAP Authentication ... Started Successfully validated connection to LDAP server Configuring LDAP Authentication ... Successful Run 'emctl config auth saml_service_provider' in other OMS(s) and restart all OMS(s) using 'emctl stop oms -all' and 'emctl start oms' - The supported values for
-
Restart the primary and additional OMS(s):
emctl stop oms -all emctl start oms -
Run the following command in the primary OMS:
emctl config auth export_saml_metadataSample output:
Oracle Enterprise Manager 24ai Release 1 Copyright (c) 1996, 2024 Oracle Corporation. All rights reserved. Exporting SAML Metadata ... Started SAML Service Provider metadata is exported to file /u01/oracle/work/user_projects/domains/Ext/saml_sp_metadata.xml -
Import the Service Provider metadata into your Identity Provider. This varies depending on your provider. For example, if using Configure Oracle Access Management (OAM), login to OAM → Federation → Identity Provider Management → Create Service Provider Partner → Browse and choose the metadata file. Enter the values as shown in the image and then save.
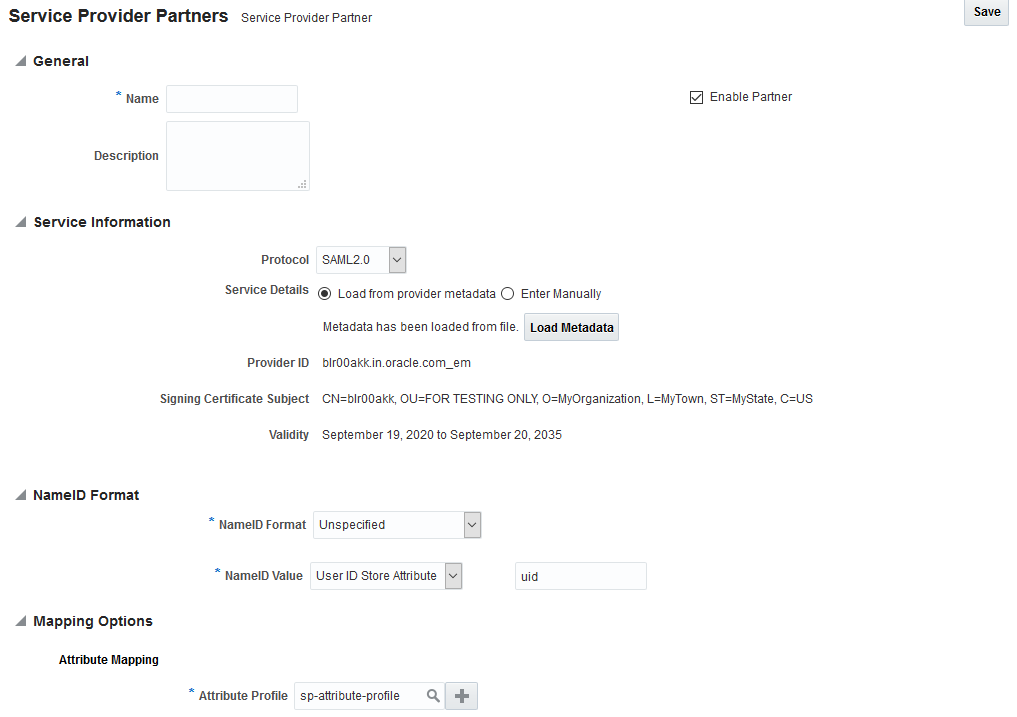
-
Get SAML metadata xml file from Identity Provider and run the following command in the primary OMS and additional OMS(s):
emctl config auth import_saml_identity_provider -idp_metadata /tmp/dev_oam_saml_metadata.xmlSample output:
Oracle Enterprise Manager 24ai Release 1 Copyright (c) 1996, 2024 Oracle Corporation. All rights reserved. Configuring SAML Authentication ... Started SAML Identity Provider configured Configuring SAML Authentication ... Successful Restart all OMS(s) using 'emctl stop oms -all' and 'emctl start oms' -
Restart the primary and additional OMS(s):
emctl stop oms -allemctl start oms
-
These authentication schemes have been tested in house and some of the external authentication schemes mentioned below can be configured using the emctl config auth utility command, which configures the required WebLogic providers as well as set the required OMS properties.
Authenticating schemes where the emctl utility command configures the WebLogic authentication providers, the command sets the required configuration parameters and leaves most of the other parameters to the default values. Administrators should ensure the configuration parameters of the WebLogic providers are tuned for performance suited to their environment before going into production. This can be done through the WebLogic Administration Console.
For more information regarding configuring SAML for different identity providers, such as Azure Ad, PingID and IDCS, see EM 13.5: Primary Note on SAML 2.0 Configuration and Issues for SSO login (Doc ID 2976397.2).
Creating a New Administrator
Enterprise Manager allows you to create and manage new administrator accounts. Each administrator account includes its own logon credentials as well as a set of roles and privileges that are assigned to the account. You can also assign a password profile to the administrator. You will need to have Enterprise Manager Super Administrator privileges to create and manage new administrator accounts.
To create, edit, or view an administrator account:
Repository Based Authentication
Repository Based Authentication is the default method of Enterprise Manager Authentication. With this authentication method, a new administrator is created in the repository.
Note:
Repository-based authentication is the default authentication method.
On this page, you can specify the type of administrator account being created and select the password profile. The password cannot be changed by the administrator if the Prevent Password Change toggle is on.
If the Expire Password Now toggle is on, the password for the new administrator account will be set to an expired state. If the password has expired, when the new administrator logs in, the Change Password page is displayed and the administrator is prompted to change the password.
The administrator should enter his current password and the new password and click Apply. He can now start using Enterprise Manager.
Creating a New User (Command Line)
The following examples make User1 an Enterprise Manager user, provide a description for the user, and prevent the password from being changed. Only another Super Administrator can change the password. The profile is set as MGMT_ADMIN_USER_PROFILE.
Example 2-1 Command Line
emcli create_user
-name="User1"
-desc="This is temp hire."
-prevent_change_password="true"
-profile="MGMT_ADMIN_USER_PROFILE"Example 2-2 Scripting and Interactive
create_user
(name="User1"
,desc="This is temp hire."
,prevent_change_password="true"
,profile="MGMT_ADMIN_USER_PROFILE")Restoring to the Default Authentication Method
The following sections detail how to restore the default Enterprise Manager authentication methods.
Bypassing the Single Sign-On Logon Page
If the OMS is configured with SSO or OAM or some other authentication method, you may want to by-pass the Single Sign-On or OAM authentication under certain circumstances.To bypass the SSO logon page, connect to the following URL:
Deleting an Administrator
To delete an administrator account:
- From the Setup menu, select Security, then select Administrators. The Administrators page is displayed.
- Select the administrator that you want to delete, then click Delete.
- On the confirmation page, click Yes.
If the administrator has resources assigned the Delete Administrator page appears. Use the Delete Administrator page to specify what happens to administrator-owned objects when removing an administrator from Enterprise Manager. On this page, you can:
-
Delete all administrator-owned objects along with the Enterprise Manager administrator. This will delete the administrator and associated job types, jobs, corrective actions, report definitions, reports, and templates. Blackouts will not be deleted.
-
Reassign objects to another Enterprise Manager administrator. This will assign the administrator's objects to another administrator. The credentials belonging to the administrator will be deleted from the repository before any reassignment takes place.
Usage Tips
Click View Objects to see all objects currently owned by the Enterprise Manager administrator to be deleted.
To reassign the objects to another administrator, enter the name of the new administrator in the New Owner text box, or click the flashlight icon to view a list of available administrators.
Only a super administrator can delete other Enterprise Manager administrators. Enterprise Manager will not allow administrators to:
-
Delete themselves.
-
Delete the management repository owner.
Administrator object reassignments can be handled as follows:
-
Blackouts can be reassigned to any user who has OPERATOR privileges on all targets affected by the blackout.
-
Jobs can be reassigned to any administrator. However, ALL credentials associated with the job will be removed, leaving the job in a Suspended state. This requires the new job owner to explicitly set new credentials. Currently running jobs are allowed to continue running. Once the new job owner sets the credentials, the job will revert to a SCHEDULED state.
-
Corrective Actions can be reassigned to any administrator who has OPERATOR privileges for targets on which the corrective action can operate.
-
Report Definitions can be reassigned to any administrator.
-
Reports can be reassigned to any administrator.
-
Monitoring Templates can be reassigned to any administrator.
Enterprise User Security Based Authentication
Enterprise User Security enables you to create and store Oracle database information as directory objects in an LDAP-compliant directory server such as Oracle Internet Directory (OID) or Microsoft Active Directory. For example, an administrator can create and store enterprise users and roles for the Oracle database in the directory, which helps centralize the administration of users and roles across multiple databases. See Database Enterprise User Security Administrator's Guide.
If you currently use Enterprise User Security to mange Oracle users and roles for all your Oracle databases, you can also extend this feature to manage Enterprise Manager administrator accounts. Configuring Enterprise Manager for use with Enterprise User Security simplifies the process of logging in to database targets you are managing with the Oracle Enterprise Manager console.
To configure Enterprise Manager for use with Enterprise User Security:
The next time you use the Oracle Enterprise Manager console to drill down to a managed database, Enterprise Manager will attempt to connect to the database using Enterprise User Security. If successful, Enterprise Manager will connect you to the database without displaying a logon page. If the attempt to use Enterprise User Security fails, Enterprise Manager will prompt you for the database credentials.
Registering Enterprise Users (EUS Users) as Enterprise Manager Users
After you have configured Enterprise Manager to use Enterprise Users (EUS), you can register existing enterprise users as Enterprise Manager Users and grant them the necessary privileges so that they can manage Enterprise Manager effectively.
You can register existing enterprise users by using:
-
Enterprise Manager Console
-
Enterprise Manager Command Line Interface (EM CLI)
Registering Enterprise Users Using the Enterprise Manager Console
You can use the Enterprise Manager console to register enterprise users by following these steps:
Registering Enterprise Users Using the Command Line Interface
To register Enterprise Users as Enterprise Manager users using EM CLI, enter the following command:
emcli create_user -name=eususer -type=DB_EXTERNAL_USER
This command registers the eususer as an Enterprise Manager user where eususer is an existing Enterprise User.
Oracle Internet Directory (OID)
You can implement an OID-based authentication scheme to have Enterprise Manager authenticate users against the OID.
Running the emctl config auth oid command on the OMS creates a WebLogic authentication provider of type OracleInternetDirectoryAuthenticator that uses the configuration parameter values specified by the command. Any configuration values not specified retain the default values. Tuning and modification of advanced OID configuration parameters is carried out through the WebLogic Server Administration Console and not the emctl config auth oid command.
Note:
In the event that you need to perform LDAP troubleshooting, enable LDAP tracing log file (ldap_trace.logATN) generation from the WebLogic Server Console. See Troubleshooting Authentication Issues in Enterprise Manager.
Prerequisites
Oracle Internet Directory LDAP server is set up and running.
WebLogic Administration Server is up and running.
Testing the OID Configuration
Use the WebLogic Server Administration Console (Users and Groups tab) to check whether the OID configuration has been successful. To navigate to this tab, select Home/Summary of Security Realms/myrealm/Users and Groups. From the Users and Groups tab, you should see users and groups showing up from the OID.
Microsoft Active Directory Based Authentication
You can implement Microsoft AD-based authentication scheme to have Enterprise Manager authenticate users against the Active Directory.
Running the emctl config auth ad command on the OMS creates a WebLogic authentication provider of type ActiveDirectoryAuthenticator that uses the configuration parameter values specified by the command. Any configuration values not specified retain the default values. Tuning and modification of advanced AD configuration parameters is carried out through the WebLogic Server Administration Console and not the emctl config auth ad command.
Before running the following procedure, ensure the Active Directory LDAP server is up and running.
Testing the Microsoft Active Directory Configuration
Use the WebLogic Server Administration Console (Users and Groups tab) to check whether the Microsoft Active Directory configuration has been successful. To navigate to this tab, select Home/Summary of Security Realms/myrealm/Users and Groups. From the Users and Groups tab, you should see users and groups showing up from the Microsoft Active Directory.
External Authorization using External Roles
When configuring Enterprise Manager for external authentication of users, you can also configure it to work with the external authentication provider to manage authorization as well. This is done using external roles. This is useful in many scenarios including, but not limited to, auto-provisioned users where the auto-provisioned user will not have any Enterprise Manager roles granted to them. The idea behind external roles is to create a role in Enterprise Manager with the relevant privileges and have the name of the role match the name of a LDAP group. Users who are part of the LDAP group will automatically be granted privileges in the role once they log on to Enterprise Manager.
To set up external roles, create a role in Enterprise Manager and mark it as external. The name of this role should be the same as an external LDAP group. Set up this role with the necessarily roles and privileges. For example, in Enterprise Manager you can create a role called EM_ADMIN that is marked external. The EM_ADMIN name matches an LDAP group called EM_ADMIN. Assume JohnDoe is a member of the EM_ADMIN LDAP group and is also an Enterprise Manager user. When JohnDoe logs on to Enterprise Manager, he will be granted all the privileges defined in the Enterprise Manager role EM_ADMIN.
Auto Provisioning
Typically the external LDAP users must be created in Enterprise Manager before they can log in to the Enterprise Manager console. Auto provisioning removes that requirement by automatically creating the Enterprise Manager user account upon successful authentication of the user the first time he logs on to Enterprise Manager.
To enable auto provisioning, set the OMS property oracle.sysman.core.security.auth.autoprovisioning to true.
This parameter can be set using emctl or the console.
This allows the external users to login without being first created as an Enterprise Manager user in the Enterprise Manager repository. Their user account gets created automatically upon the first login. Once this property is set, all external LDAP users will be able to login to Enterprise Manager console. If you want to further restrict the auto provisioning feature to a subset of users, such as only to members of certain LDAP groups, then set another OMS property "oracle.sysman.core.security.auth.autoprovisioning_minimum_role". This property should be set to the LDAP group name whose members should be auto-provisioned For example, if set to "EM_ADMIN", only members of that LDAP group called EM_ADMIN will be able to login to Enterprise Manager and have user accounts automatically created in Enterprise Manager.
Using a Different Name to the External Users Display Name
By default, you must log in to Oracle Enterprise Manager with the user name that is displayed in the Weblogic Console >Security Realms >myrealms >Users and Groups >Users list. After authenticating Oracle Enterprise Manager with external providers, the cn values of the external users are listed in Weblogic Console Users list.
In some environments, the cn value is in the form 'FIRST NAME LAST NAME'. If you prefer to use the sAMAccountName or user ID (UID) to login to Oracle Enterprise Manager you must update the provider configurations.
For example, there is a user with the user name 'TEST USER' displayed in the Weblogic Console, but the user wants to login to Oracle Enterprise Manager as 'tuser' which is the sAMAccountName of that user.
Note:
The sAMAccountName is used in this example. To use a UID, replace sAMAccountName with uid in the steps that follow.
-
In the external provider, check the parameter/properties configured for the external user.
-
The value of parameter 'cn' is 'TEST USER'.
-
In the same file, find the parameter that has the value for user as 'tuser' . That parameter may be 'sAMAccountName'.
To use the sAMAccountName of the external users (tuser) to log in to Oracle Enterprise Manager:
-
Back up the
<GCDOMAIN>/config/config.xmlfile. -
On the Weblogic Console, navigate to Security Realms>myrealms>Providers>External Authenticator.
-
Click Lock and Edit to edit this page.
-
Click the Provider Specific tab.
-
Look for the User From Name filter.
-
Change the value of User From Name from
(&(cn=%u)(objectclass=person))to(&(sAMAccountName=%u)(objectclass=person)). -
Look for User Name Attribute.
-
Change the value of User Name Attribute from cn to sAMAccountName.
-
Click Save then click Activate Changes.
-
Restart Oracle Management Server with the
-alloption:<OMS_HOME>/bin/emctl stop oms -all -force
<OMS_HOME>/bin/emctl start oms
-
Log in to the Weblogic Console >Security Realms >myrealms >Users and Groups >Users list and confirm that the user 'tuser' exist in Users list. Now you can user the user name 'tuser' to log in to Oracle Enterprise Manager.
Note:
Follow the above steps for Extended Domain also.
Backup the Extended Domain configuration file <GC_INST>/user_projects/domains/EMExtDomain1/config/config.xml.
Collect the Extended Domain port Extended Admin Server HTTPS Port by running the following command:
emctl status oms -detailsUse the above port value and open the Extended Domain Weblogic console with the following URL:
https://<OMS.HOSTNAME>:<Extended Admin Server HTTPS Port>/consoleFor example:
https://<OMS.HOSTNAME>:7016/consoleIn multi-node OMS, implement these steps in every Extended Domain.
For more information about logging in to Oracle Enterprise Manager with sAMAccountName or a name other than the display name of External Users, see Doc ID. 1637959.1.
Mapping LDAP User Attributes to Enterprise Manager User Attributes
When external authentication is enabled, a flashlight icon appears next to the name field in the Create User flow.
Note:
External authentication is enabled when an administrator is first created in Enterprise Manager.
Clicking on the flashlight displays a popup window, giving Enterprise Manager administrators the ability to search for enterprise users in the external LDAP server (for example AD/OID) that have been configured. The user's LDAP attributes are shown as well. This helps the Enterprise Manager administrator to verify external user's attributes before creating them in Enterprise Manager.
When external authentication has been configured, it is often desirable to automatically propagate user information such as email address, department, that is defined for the user in LDAP to the corresponding Enterprise Manager user account. This can be done by setting the OMS property oracle.sysman.core.security.auth.ldapuserattributes_emuserattributes_mappings. This property will contain the mapping between the Enterprise Manager user properties and the corresponding LDAP user attributes that will be used to populate the user properties. The mapping between an Enterprise Manager property and an LDAP attribute is expressed in the format <key>={%attribute%}where:
-
key - An Enterprise Manager user property. Values for user properties are:
USERNAME
EMAIL
CONTACT
LOCATION
DEPARTMENT
COSTCENTER
LINEOFBUSINESS
DESCRIPTION
Any other values specified for keys will be ignored.
-
attribute - A user attribute that needs to be fetched from LDAP and is used to set the properties of the user in Enterprise Manager. The attribute should be specified using the following format
{%attribute%}, for example{%mail%}The value between % should be a valid attribute in the LDAP server. You can also specify literal strings when specifying attribute values, for example:
DESCRIPTION={%firstname% %lastname% employee}In this example, only firstname and lastname will be fetched from LDAP but the description for the user will be "firstname lastname employee". For example, "John Doe employee".
Another example is
CONTACT={telephone number %phone%}. If a comma needs to be specified in the literal string value, it needs to be escaped with "\" For example,DESCRIPTION={%lastname% \, %firstname% \, %phone%}This will result in a user with description "Doe, John, 212-454-0000". The other characters that need to be escaped with backslash (\), if specified in the literal string, are ':' and '=', so they should be entered as
\:or\=.
The OMS property oracle.sysman.core.security.auth.ldapuserattributes_emuserattributes_mappings should thus be set to a set of comma separated key-attribute pairs.
As an example, let us assume user JOHNDOE exists in LDAP and has the following attributes:
uid=johndoe,mail=johndoe@example.com,description=EM LDAP Admin,postalcode=90210,department=EnterpriseAdmin,telephone=2124540000,displayname=JohnDoe
If you set OMS property:
oracle.sysman.core.security.auth.ldapuserattributes_emuserattributes_mappings to "USERNAME={%uid%},EMAIL={%mail%},CONTACT={%telephone%},DEPARTMENT={%department%},DESCRIPTION={%description%},LOCATION={%postalcode%}"
then when you select the user from the popup window and hit Ok, the user's attributes are automatically populated in the appropriate fields of the 'Create User' page.
Changing User Display Names in Enterprise Manager
In some LDAP environments, users may have numeric login IDs. Enterprise Manager has the ability to display user-friendly username in when a user logs in using a numeric ID. When they log on to the Enterprise Manager console, the numeric ID is displayed and used everywhere the user's name is shown including audit records. In order to show a more user-friendly name, you can use the OMS property oracle.sysman.core.security.auth.enable_username_mapping to enable the mapping of a an external, more intuitive name than the name shown in Enterprise Manager. You can use emctl to change this property.
emctl set property –name “oracle.sysman.core.security.auth.enable_username_mapping" –value “true"
You can also set this using the Enterprise Manager console as well. These are dynamic properties and do not require bouncing the Management Service.
Once enabled, an External User ID field will be added that will contain the name or ID used by the user to log on to Enterprise Manager (this name/ID exists as a valid user in LDAP). The Create Administrator page appears.
For example, if external user 123456 wants to log in and johndoe needs to be shown as logged in user, specify 'johndoe' in the Name field.
User 123456 will still log in as that ID as that user exists in the LDAP server as 123456 but the name 'johndoe' will be shown as his user name in the Enterprise Manager console.
The OMS property oracle.sysman.core.security.auth.ldapuserattributes_emuserattributes_mappings can also be used in this environment to automatically populate the user's name and external ID. An extra field called EXTERNALUSERID needs to be set. Using the example above, set the OMS property to the following:
"USERNAME={%displayname%},EXTERNALUSERID={%uid%},EMAIL={%mail%},CONTACT="{%telephone%},DEPARTMENT={%department%},DESCRIPTION={%description%},LOCATION={%postalcode%}"
The features described above are available in EM CLI as well. With the OMS properties set, the EM CLI create_user verb can be used to create users with their LDAP attributes automatically populated.
Configuring Other LDAP/SSO Providers
Oracle Enterprise Manager currently offers native support for Oracle Internet Directory, Oracle Access Manager, Active Directory and Single Sign-On. Native support allows WebLogic Server and Enterprise Manager to be configured for external authentication using the EMCTL command.
Configuring Enterprise with:
- Oracle Internet Directory: Oracle Internet Directory (OID)
- Active Directory: Microsoft Active Directory Based Authentication
LDAP providers need to be marked SUFFICIENT and should be ahead of
the Enterprise Manager Repository authenticator in the list of providers.
For SSO providers, please refer to the requirements of the specific SSO provider configuration. Along with configuring the appropriate authentication providers, certain OMS properties have to be set as well in order for Enterprise Manager to work.
For configuring Enterprise Manager with any other type of LDAP server, the following OMS properties need to be set. You can use emctl or the console to set these properties. The properties need to be set for each OMS.
emctl set property -name "oracle.sysman.core.security.auth.is_external_authentication_enabled" -value "true"
-
oracle.sysman.core.security.auth.is_external_authentication_enabled=true.
-
oracle.sysman.emSDK.sec.DirectoryAuthenticationType to LDAP
For configuring Enterprise Manager with any other type of SSO solution, along with configuring the weblogic authentication/identity assertion providers, the following OMS properties need to be set.
-
oracle.sysman.core.security.auth.is_external_authentication_enabled=true
-
oracle.sysman.core.security.sso.type=OTHERSSO
-
oracle.sysman.core.security.sso.logout_url=<whatever value was provided for configuring logout on SSO server>
-
oracle.sysman.emSDK.sec.DirectoryAuthenticationType=SSO
Configuring Single Sign-on based Authentication
This section covers the following topics:
Configuring Single-Sign-on with Oracle AS SSO 10g
If you are currently using Oracle Application Server Single Sign-On to control access and authorization for your enterprise, you can extend those capabilities to the Enterprise Manager console.
By default, Enterprise Manager displays the main logon page. However, you can configure Enterprise Manager so it uses Oracle Application Server Single Sign-On to authenticate your Enterprise Manager users. Instead of seeing the Enterprise Manager logon page, users will see the standard Oracle Application Server Single Sign-On logon page. From the logon page, administrators can use their Oracle Application Server Single Sign-On credentials to access the Oracle Enterprise Manager console.
Note:
-
You can configure Enterprise Manager to use one of the default Oracle Application Server Single Sign-On or Enterprise User Security features, but not both.
-
When Enterprise Manager is configured to use Single Sign-On with Server Load Balancer (SLB), make sure that the correct monitoring settings have been defined.
Partner applications are applications that are designed to delegate authentication to the OracleAS Single Sign-On server. The following sections describe how to configure Enterprise Manager as an OracleAS Single Sign-On Partner Application:
Registering Enterprise Manager as a Partner Application
To register Enterprise Manager as a partner application manually, follow these steps:
Removing Single Sign-On Configuration
To remove the single sign-on configuration, perform the following:
Registering Single Sign-On Users as Enterprise Manager Administrators
After you have configured Enterprise Manager to use the Single Sign-On logon page, you can register any Single Sign-On user as an Enterprise Manager administrator. You can register single sign-on users using:
-
Enterprise Manager Graphical User Interface
-
Enterprise Manager Command Line Interface
Registering Single Sign-On Users Using the Graphical User Interface
You can use the graphical user interface to register single sign-on users by following these steps:
Registering Single Sign-On Users Using EM CLI
You can use the following EM CLI command to create Single Sign-On users:
emcli create_user -name=ssouser -type=EXTERNAL_USER
This command creates a user with the name ssouser who is authenticated against the single sign-on user.
| Argument | Description |
|---|---|
|
-name |
Name of the administrator. |
|
-type |
The type of user. The default value for this parameter is EM_USER. The other possible values are:
|
|
-password |
The password for the newly created administrator. |
|
-roles |
The list of roles that can be granted to this administrator. |
|
|
The list of email addresses for this administrator. |
|
-privilege |
The system privileges that can be granted to the administrator. This option can be specified more than once. |
|
-profile |
The name of the database profile. This is an optional parameter. The default profile used is DEFAULT. |
|
-desc |
The description of the user being added. |
|
-expired |
This parameter is used to set the password to "expired" status. This is an optional parameter and is set to False by default. |
|
-prevent_change_password |
When this parameter is set to True, the user cannot change the password. This is an optional parameter and is set to False by default. |
|
-input_file |
This parameter allows the administrator to provide the values for any of these arguments in an input file. The format of value is |
Example 1
emcli create_user
-name="new_admin"
-email="john.doe@example.com;jane.doe@example.com"
-roles="public"
-privilege="view_job;923470234ABCDFE23018494753091111"
-privilege="view_target;<host>.com:host"
This example creates an Enterprise Manager administrator named new_admin. This administrator has two privileges: the ability to view the job with ID 923470234ABCDFE23018494753091111 and the ability to view the target <host>.com:host. The administrator new_admin is granted the PUBLIC role.
Example 2
emcli create_user
-name="User1"
-type="EXTERNAL_USER"
-input_file="privilege:/home/user1/priv_file"
Contents of priv_file are:
view_target;<host>.com:host
This example makes user1 which has been created externally as an Enterprise Manager user. user1 will have view privileges on <host>.com:host.
Example 3
emcli create_user
-name="User1"
-desc="This is temp hire."
-prevent_change_password="true"
-profile="MGMT_ADMIN_USER_PROFILE"
This example sets user1 as an Enterprise Manager user with some description. The prevent_change_password is set to true to indicate that the password cannot be changed by user1 and the profile is set to MGMT_ADMIN_USER_PROFILE.
Example 4
emcli create_user
-name="User1"
-desc="This is temp hire."
-expire="true"
This example sets user1 as an Enterprise Manager with some description. Since the password is set to expire immediately, when the user logs in for the first time, he is prompted to change the password.
Bypassing the Single Sign-On Logon Page
If the OMS is configured with SSO or OAM or some other authentication method, you may want to by-pass the Single Sign-On or OAM authentication under certain circumstances. To bypass the SSO logon page, connect to the following URL:
Configuring Enterprise User Security based Authentication
For instructions on configuring Enterprise Manager for use with Enterprise User Security, see "Enterprise User Security Based Authentication".
Restoring to the Default Authentication Method
The following sections provide instructions on restoring the default authentication method used by Enterprise Manager.
Bypassing the Single Sign-On Logon Page
If the OMS is configured with SSO or OAM or some other authentication method, you may want to by-pass the Single Sign-On or OAM authentication under certain circumstances.To bypass the SSO logon page, connect to the following URL: