Basic Tasks for Configuring Protected Database Access
This section explains the basic tasks involved in configuring protected database access. Figure 8-2 shows the overall workflow described in Recovery Appliance Workflow, with the configuration tasks on the Recovery Appliance highlighted.
Figure 8-2 Database Access Configuration Tasks in the Recovery Appliance Workflow
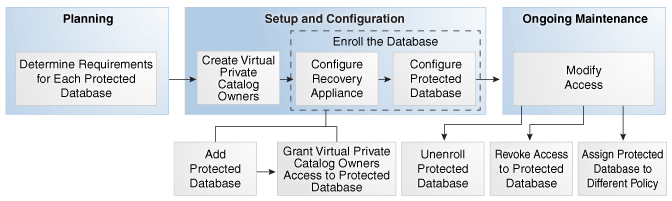
Description of "Figure 8-2 Database Access Configuration Tasks in the Recovery Appliance Workflow"
Typically, you configure protected database access in the following sequence:
-
During the planning phase, decide which databases will be protected by the Recovery Appliance.
"Task 4: Determine access requirements for Recovery Appliance" describes this task.
-
During the configuration phase (see "Setup and Configuration for Recovery Appliance"), do the following:
-
Create virtual private catalog accounts.
"Creating Virtual Private Catalog Accounts" describes this task.
-
Enroll the protected database with the Recovery Appliance.
Note:
With Cloud Control, you can perform all enrollment steps in a single page except registering the database in the recovery catalog.
"Enrolling Protected Databases" describes this task.
-
-
During the ongoing maintenance phase (see "Maintenance Tasks for Recovery Appliance"), you can do the following:
-
Update the properties of an existing protected database using
DBMS_RA.UPDATE_DB(see "Updating Protected Database Properties") -
Remove metadata for protected databases from the Recovery Appliance using
DBMS_RA.DELETE_DB -
Revoke access to a specific protected database from a specific virtual private catalog owner by using
DBMS_RA.REVOKE_DB_ACCESS
-