13 Enrolling and Upgrading Endpoints for Oracle Key Vault
After an endpoint is registered in Oracle Key Vault, an endpoint administrator enrolls and provisions the endpoint to manage security objects in Key Vault.
- About Endpoint Enrollment and Provisioning
Endpoints are Oracle Key Vault clients that use the server to store and manage security objects, share them with trusted peers, and retrieve them. - Finalizing Enrollment and Provisioning
To enroll and provision a registered endpoint an endpoint administrator must download and then install theokvclient.jarfile. - Environment Variables and Endpoint Provisioning Guidance
Environment variables such asJAVA_HOMEandOKV_HOMEmust be correctly set so that Oracle Key Vault can access its utilities. - Endpoints That Do Not Use the Oracle Key Vault Client Software
Third-party KMIP endpoints do not use the Oracle Key Vault softwareokvutilandliborapkcs.so. - Transparent Data Encryption Endpoint Management
Oracle Key Vault can manage TDE keys by using the same PKCS#11 interface that TDE uses to communicate with an external keystore. - Endpoint okvclient.ora Configuration File
Oracle Key Vault endpoint libraries and utilities use theokvclient.oraconfiguration file, which stores the configuration parameters associated with the endpoint. - okvclient.ora Parameters That Must Not Be Modified
Theokvclient.oraconfiguration file contains configuration parameters that you must not modify. - Upgrading Endpoint Software
You can upgrade the endpoint software from the Oracle Key Vault management console login window.
13.1 About Endpoint Enrollment and Provisioning
Endpoints are Oracle Key Vault clients that use the server to store and manage security objects, share them with trusted peers, and retrieve them.
These clients can be systems like Oracle database servers, Oracle middleware servers, operating systems, and other information systems.
If you plan to configure the extraction of symmetric keys from Oracle Key Vault to false (to prevent them from being extracted), it is important that you first upgrade the endpoint to Oracle Key Vault release 21.4.
An Oracle Key Vault system administrator first adds (or registers) the endpoint to Key Vault, and then sends the endpoint's enrollment token (generated during registration) to the endpoint administrator. The endpoint administrator verifies the enrollment token before enrolling and provisioning the endpoint. An enrolled endpoint can upload, download, and manage security objects using Key Vault.
Endpoint enrollment is a three-step process performed by two kinds of administrative users summarized in the following table.
Table 13-1 Summary of Endpoint Enrollment
| Step# | Task | Performed by | Endpoint Status (as seen on Oracle Key Vault Management Console) |
|---|---|---|---|
|
1. |
|
Users with the System Administrator role and Key Administrator role on Oracle Key Vault, or user with the Manage Endpoint privilege |
Registered |
|
2. |
|
Endpoint administrator using the Oracle Key Vault management console |
Enrolled |
|
3. |
Install |
Endpoint administrator on endpoint |
Enrolled |
Endpoint enrollment ensures that only authorized endpoints can communicate with Oracle Key Vault because the utilities needed to communicate are bundled with the okvclient.jar endpoint software file.
okvclient.jar contains the following:
-
A Transport Layer Security (TLS) certificate and private key that the endpoint uses to authenticate itself to Oracle Key Vault
-
A TLS certificate for Oracle Key Vault that serves as the root CA
-
Endpoint libraries and utilities
-
Additional information such as the Oracle Key Vault IP address that is used by
okvutilto create theokvclient.oraconfiguration file
In an Oracle Real Application Clusters (RAC) environment, you must enroll and provision each Oracle RAC node as an endpoint. Each Oracle RAC-enabled database corresponds to one virtual wallet in Oracle Key Vault. Each Oracle RAC instance of that database corresponds to an endpoint in Oracle Key Vault. All endpoints for each database share the same wallet as their default wallet. You must download one distinct okvclient.jar for each instance.
13.2 Finalizing Enrollment and Provisioning
To enroll and provision a registered endpoint an endpoint administrator must download and then install the okvclient.jar file.
- Step 1: Enroll the Endpoint and Download the Software
You must have the endpoint's enrollment token before you can download the endpoint softwareokvclient.jar. - Step 2: Prepare the Endpoint Environment
You must ensure that you have the right version of the Java Development Toolkit (JDK) and that the Oracle environment variables are set. - Step 3: Install the Oracle Key Vault Software onto the Endpoint
You can install the endpoint using downloadedokvclient.jarfile. - Step 4: Perform Post-Installation Tasks
The post-installation procedures include optionally configuring a TDE connection for the endpoint, checking the installation contents, and deleting theokvclient.jar file.
Parent topic: Enrolling and Upgrading Endpoints for Oracle Key Vault
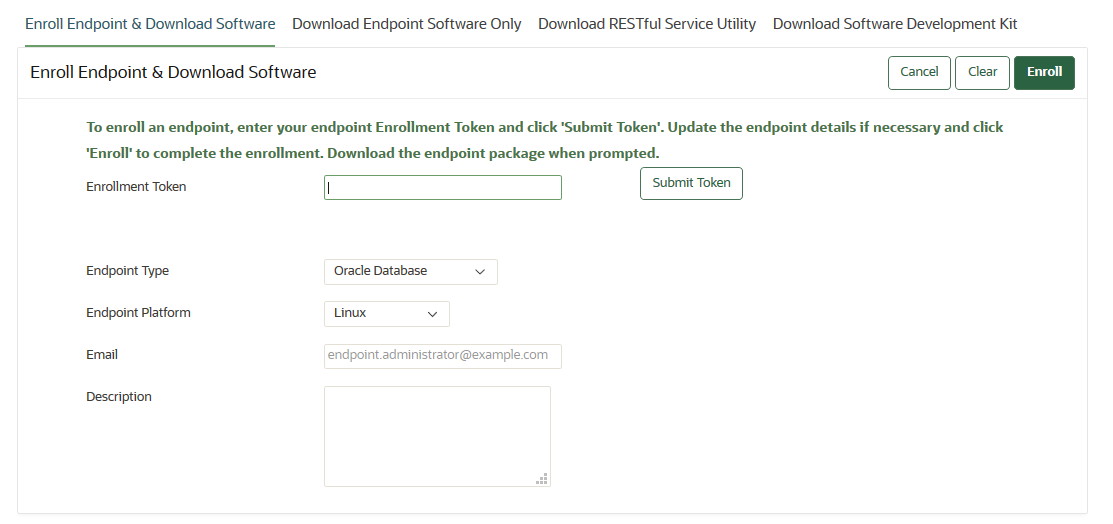
13.2.1 Step 1: Enroll the Endpoint and Download the Software
You must have the endpoint's enrollment token before you can download the endpoint software okvclient.jar.
okvclient.jar software file on the endpoint, starting with preparing the endpoint environment.
Related Topics
Parent topic: Finalizing Enrollment and Provisioning
13.2.2 Step 2: Prepare the Endpoint Environment
You must ensure that you have the right version of the Java Development Toolkit (JDK) and that the Oracle environment variables are set.
Parent topic: Finalizing Enrollment and Provisioning
13.2.3 Step 3: Install the Oracle Key Vault Software onto the Endpoint
You can install the endpoint using downloaded okvclient.jar
file.
Note:
To upgrade to the latest endpoint software for an enrolled endpoint, you can download the endpoint software without having to re-enroll the endpoint.Parent topic: Finalizing Enrollment and Provisioning
13.2.4 Step 4: Perform Post-Installation Tasks
The post-installation procedures include optionally configuring a TDE connection for the endpoint, checking the installation contents, and deleting the okvclient.jar file.
Parent topic: Finalizing Enrollment and Provisioning
13.3 Environment Variables and Endpoint Provisioning Guidance
Environment variables such as JAVA_HOME and OKV_HOME must be correctly set so that Oracle Key Vault can access its utilities.
- How the Location of JAVA_HOME Location Is Determined
The default location for theokvclient.orafile is the$OKV_HOME/confdirectory. - Location of the okvclient.ora File and Environment Variables
$OKV_HOMEis the destination directory for the endpoint software specified with the-doption during installation. - Setting OKV_HOME for Non-Database Utilities to Communicate with Oracle Key Vault
For non-database utilities, you must set the environment variableOKV_HOMEto point to the destination directory for the endpoint software. - Environment Variables in sqlnet.ora File
You must consider several points while using thesrvctlutility on Oracle Database endpoints.
Parent topic: Enrolling and Upgrading Endpoints for Oracle Key Vault
13.3.1 How the Location of JAVA_HOME Location Is Determined
The default location for the okvclient.ora file is the $OKV_HOME/conf directory.
When you provision endpoints you must know how the installation process determines the location of Java home and the okvclient.ora file.
The endpoint software installation process uses the following rules to determine the Java home location:
-
If a user-defined
JAVA_HOMEenvironment variable exists, the installation process uses this value. -
If
JAVA_HOMEis not set, then the installation process looks for it in thejava.homesystem property of the Java Virtual Machine (JVM).
After the JAVA_HOME path is determined, the installation process adds it to the okvclient.ora configuration file to be used by all okvutil commands.
You can force okvutil to use a different JAVA_HOME setting by using one of the following methods:
-
Set the
JAVA_HOMEenvironment variable in the shell where you runokvutil:setenv JAVA_HOME path_to_Java_homeOr:
export JAVA_HOME = path_to_Java_home -
Set the
JAVA_HOMEproperty directly in theokvclient.oraconfiguration file.JAVA_HOME=path_to_Java_home
Restart the endpoint database after you set the JAVA_HOME variable in okvclient.ora.
You may need to periodically manually update the value of the JAVA_HOME environment variable setting in the okvclient.ora file. This can happen when a newer version of Java is installed and the previous version of Java is removed. To do this, first shut down the endpoint database, so that okvclient.ora is not overwritten by the database processes. Then, manually update the value of JAVA_HOME in okvclient.ora.
Parent topic: Environment Variables and Endpoint Provisioning Guidance
13.3.2 Location of the okvclient.ora File and Environment Variables
$OKV_HOME is the destination directory for the endpoint software specified with the -d option during installation.
The okvclient.ora file is a configuration file in the $OKV_HOME/conf directory .
In addition to the $OKV_HOME/conf file, the installation process creates a soft link to okvclient.ora for an existing database. The location of the soft link depends on the following:
-
If the
$ORACLE_BASEenvironment variable is set, then the installation process creates a soft link to theokvclient.oraconfiguration file (in$OKV_HOME/conf) in the$ORACLE_BASE/okv/$ORACLE_SIDlocation.If a soft link to
okvclient.oraalready exists in the$ORACLE_BASE/okv/$ORACLE_SIDlocation, then the installation process accepts the existing soft link tookvclient.oraas a a valid soft link. -
If the
$ORACLE_BASE/okv/$ORACLE_SIDdirectory is not set, then the installation process tries to create it. -
If the
$ORACLE_HOMEenvironment variable is set but the$ORACLE_BASEvariable is not set, then the installation process creates a soft link for the$ORACLE_HOME/okv/$ORACLE_SIDlocation to point to the configuration file in the$OKV_HOME/confdirectory.
Parent topic: Environment Variables and Endpoint Provisioning Guidance
13.3.3 Setting OKV_HOME for Non-Database Utilities to Communicate with Oracle Key Vault
For non-database utilities, you must set the environment variable OKV_HOME to point to the destination directory for the endpoint software.
You must manually set OKV_HOME because the installation process does not set this variable automatically. Setting OKV_HOME enables utilities to communicate with Oracle Key Vault. These include utilities such as Oracle Recovery Manager (RMAN) that access Oracle Key Vault for keys.
You must set OKV_HOME in all environments where you will run utilities such as RMAN. For example, if you spawn a new xterm window, then you will need to set OKV_HOME in this environment before running RMAN.
Parent topic: Environment Variables and Endpoint Provisioning Guidance
13.3.4 Environment Variables in sqlnet.ora File
You must consider several points while using the srvctl utility on Oracle Database endpoints.
-
If you are using the
srvctlutility, and if you want to include environment variables in thesqlnet.oraconfiguration file, then you must set these environment variables in both the operating system and thesrvctlenvironment. -
For Oracle Database endpoints, if you are using the
srvctlutility and setting environment variables insqlnet.ora, then you must set them in both the operating system and thesrvctlenvironment. -
The operating system and
srvctlutility should have$ORACLE_SID,$ORACLE_HOMEand$ORACLE_BASEset to the same values.
Parent topic: Environment Variables and Endpoint Provisioning Guidance
13.4 Endpoints That Do Not Use the Oracle Key Vault Client Software
Third-party KMIP endpoints do not use the Oracle Key Vault software okvutil and liborapkcs.so.
In this case you must manually set the Transport Layer Security (TLS) authentication as follows:
-
Extract the
ssldirectory from theokvclient.jarfile.jar xvf okvclient.jar ssl
-
Use the following files to set up the TLS authentication:
-
ssl/key.pem: Endpoint private key -
ssl/cert.pem: Endpoint certificate -
ssl/cert_req.pem: Certificate request corresponding tocert.pem -
ssl/CA.pem: Trust anchor for verifying the Oracle Key Vault server certificate
-
Parent topic: Enrolling and Upgrading Endpoints for Oracle Key Vault
13.5 Transparent Data Encryption Endpoint Management
Oracle Key Vault can manage TDE keys by using the same PKCS#11 interface that TDE uses to communicate with an external keystore.
Therefore, you do not need to patch the database to use Oracle Key Vault for storing and retrieving TDE master encryption keys. Oracle Key Vault supplies the PKCS#11 library to communicate with Oracle Key Vault.
Oracle Key Vault improves upon TDE key management. For example, you can directly upload the keys in the wallet to Oracle Key Vault for long-term retention, to be shared with other database endpoints within the same endpoint group. Therefore, you do not need to store the wallet indefinitely after migration. Migration in this context means that the database is configured to use Oracle Key Vault for wallet backup, and that the administrator intends to migrate to an online master encryption key (formerly knows as TDE direct connect).
You can continue to use the wallet, and upload wallet copies to Oracle Key Vault as part of every TDE key administration SQL operation, involving a WITH BACKUP SQL clause. However, be aware that TDE ignores the WITH BACKUP clause in an Oracle Key Vault online key deployment, even if it is required for the ADMINISTER KEY MANAGEMENT statement.
Oracle Database TDE are endpoints for Oracle Key Vault. Endpoint enrollment and installation ensure that the PKCS#11 library is installed in the correct location for TDE to pick up and use. When the PKCS#11 library is installed, all other configurations and operations are in effect.
Example 13-1 shows examples of setting an encryption key.
Example 13-1 Setting an Encryption Key
ALTER SYSTEM SET ENCRYPTION KEY IDENTIFIED BY secret_passphrase -- For Oracle Database 11g Release 2 ADMINISTER KEY MANAGEMENT SET ENCRYPTION KEY IDENTIFIED BY secret_passphrase WITH BACKUP; -- For Oracle Database 12c or later
13.6 Endpoint okvclient.ora Configuration File
Oracle Key Vault endpoint libraries and utilities use the okvclient.ora configuration file, which stores the configuration parameters associated with the endpoint.
The okvclient.ora file consists of key-value pairs separated by an equal sign (=). At minimum, set the following parameters in the endpoint configuration file:
-
SERVER=node1_IP:node1_port/node1_DN,node2_IP:node2_port/node2_DN,...This parameter specifies the IP address and port number of the Oracle Key Vault server, separated by a colon and the server DN separated by a slash. If the port number is not specified, then it defaults to the standard KMIP port
5696. -
STANDBY_SERVER=standby_server_IP:standby_server portThis is the standby server. If primary-standby is configured, then this parameter shows the standby IP address.
READ_SERVER=node1_IP:node1_port/node1_DN,node2_IP:node2_port/node2_DN,...This parameter specifies the list of read-only servers.
-
SSL_WALLET_LOC=directoryThis parameter specifies the location of the wallet containing TLS credentials for the endpoint.
-
SERVER_POLL_TIMEOUT=timeout_valueYou can use the
SERVER_POLL_TIMEOUTparameter to specify a timeout for a client's attempt to connect to an Oracle Key Vault server before trying the next server in the list. The default value is 300 (milliseconds).In Oracle Key Vault clients first establish a non-blocking TCP connection to Oracle Key Vault to quickly detect unreachable servers.
After the first attempt, the client makes a second and final attempt to connect to the server but this time waits for twice as long as the duration specified by the
SERVER_POLL_TIMEOUTparameter. This is done to overcome possible network congestion or delays. PKCS11_PERSISTENT_CACHE_FIRST=valuesets the persistent master encryption key cache operation mode.
The CONF_ID value in an okvclient.ora file is a unique internal value that helps an Oracle database to find its virtual wallet in Oracle Key Vault. Do not modify any settings in the okvclient.ora file. Instead, set endpoint configuration parameters through the Oracle Key Vault management console. Depending on your privileges, you can set these for individual endpoints or globally, for all endpoints.
Several okvclient.ora parameters can be modified through the Oracle Key Vault management console. You should modify the parameters only in the Oracle Key Vault management console. Depending on your privileges, you can set these parameters for individual endpoints or globally, for all endpoints.
-
PKCS11_CACHE_TIMEOUT=valuespecifies the duration in minutes for which the master encryption key is available after it is cached in the in-memory cache. In the Oracle Key Vault management console, this setting is PKCS 11 In-Memory Cache Timeout ( in minutes ) in the Endpoint Settings page. -
PKCS11_PERSISTENT_CACHE_TIMEOUT=valuespecifies the duration in minutes for which the master encryption key is available after it is cached in the persistent master encryption key cache. In the Oracle Key Vault management console, this setting is PKCS 11 Persistent Cache Timeout ( in minutes ) in the Endpoint Settings page. -
PKCS11_PERSISTENT_CACHE_REFRESH_WINDOW=valuespecifies the duration in minutes to extend the period of time for which the master encryption key is available after it is cached in the persistent master encryption key cache. In the Oracle Key Vault management console, this setting is PKCS 11 Persistent Cache Refresh Window ( in minutes ) in the Endpoint Settings page. -
PKCS11_CONFIG_PARAM_REFRESH_INTERVAL=valuesets the frequency at which a long-running process will re-read theokvclient.oraconfiguration file. In the Oracle Key Vault management console, this setting is PKCS11 Configuration Parameter Refresh Interval ( in minutes ) in the Endpoint Settings page. -
SERVER_POLL_TIMEOUT=valuespecifies a timeout for a client's attempt to connect to an Oracle Key Vault server before trying the next server in the list. The default value is 300 (milliseconds). In the Oracle Key Vault management console, this setting is Server Poll Timeout ( in milliseconds ) in the Endpoint Settings page.
13.7 okvclient.ora Parameters That Must Not Be Modified
The okvclient.ora configuration file contains configuration parameters that you must not modify.
These parameters are automatically populated when you add the endpoint to Oracle Key Vault. Do not modify them. They are as follows:
-
SERVER=node1_IP:node1_port/node1_DN,node2_IP:node2_port/node2_DN,...This parameter specifies the IP address and port number of the Oracle Key Vault server, separated by a colon and the server DN separated by a slash. If the port number is not specified, then it defaults to the standard KMIP port
5696. -
STANDBY_SERVER=standby_server_IP:standby_server portThis is the standby server. If primary-standby is configured, then this parameter shows the standby IP address.
READ_SERVER=node1_IP:node1_port/node1_DN,node2_IP:node2_port/node2_DN,...This parameter specifies the list of read-only servers. Do not modify this parameter. Oracle Key Vault populates this setting when the endpoint node is added.
SERVER_DN=CN=server_certification,OU=product,O=company,L=city,ST=state_or_province,C=countryGEN_TIMESTAMP=timestamp_informationThis parameter shows the time and date format used in the endpoint.
-
UPDATE_TIMESTAMP=updated_timestampThis parameter shows the date, time, and timezone for when the configuration file was last updated.
-
SW_TYPE=software_typeThis parameter shows the endpoint software type, for example,
ENROLLED_ENDPOINT_SOFTWARE. -
JAVA_HOME=pathThis parameter shows the directory that is defined by the
JAVA_HOMEenvironment variable. -
OKV_JVM_LIB_PATH=pathThis parameter shows the directory that is defined by the
OKV_JVM_LIB_PATHenvironment variable. -
EP_TYPE=typeThis parameter indicates the type of the endpoint, such as
Oracle Database. -
OKV_HOSTNAME=host_nameThis parameter indicates the host server where Oracle Key Vault resides.
-
SSL_WALLET_LOC=directoryThis parameter specifies the location of the wallet containing TLS credentials for the endpoint.
-
_NOT_STRICT_PKCS11=valueThis parameter indicates the strict PKCS standard setting for use with Oracle ACFS.
-
PKCS11_NO_KMIP_OBJECT_ACCESS_CHECK=valueThis parameter indicates whether the endpoint will perform access checks.
-
_TRACE_DIR=.This parameter indicates the location where the PKCS trace files are generated. The
.character, the default, means the current directory. -
_TRACE_LEVEL=0This parameter determines the tracing level that is set for the PKCS traces.
0, the default, disables tracing. Enter a value up to16to enable full tracing. -
NUM_AFFINITY_RW_NODES=This parameter defines the number of read-write nodes that are in the cluster and have the same subgroup as the endpoint.
-
NUM_AFFINITY_RO_NODES=This parameter defines the number of read-only nodes that are in the cluster and have the same subgroup as the endpoint.
CONF_IDis a unique internal value that helps an Oracle database to find its virtual wallet in Oracle Key Vault. Do not modify this value.
Parent topic: Enrolling and Upgrading Endpoints for Oracle Key Vault
13.8 Upgrading Endpoint Software
You can upgrade the endpoint software from the Oracle Key Vault management console login window.
- Step 1: Prepare the Endpoint Environment
Ensure that you have the correct privileges and that the endpoint has the correct configuration, such as Oracle environment variables. - Step 2: Download the Oracle Key Vault Software onto the Endpoint
You download theokvclient.jarfile to local computer. - Step 3: Install the Oracle Key Vault Software onto the Endpoint
You must be the endpoint administrator to install the Oracle Key Vault software onto the endpoint. - Step 4: Perform Post-Installation Tasks
After you complete the installation, you can update the library used by TDE and then verify that the endpoint software was installed correctly. - Upgrading Endpoint Software on an Enrolled Endpoint
You should upgrade the endpoint software on an enrolled endpoint any time you upgraded to a new release of Oracle Key Vault.
Parent topic: Enrolling and Upgrading Endpoints for Oracle Key Vault
13.8.1 Step 1: Prepare the Endpoint Environment
Ensure that you have the correct privileges and that the endpoint has the correct configuration, such as Oracle environment variables.
Parent topic: Upgrading Endpoint Software
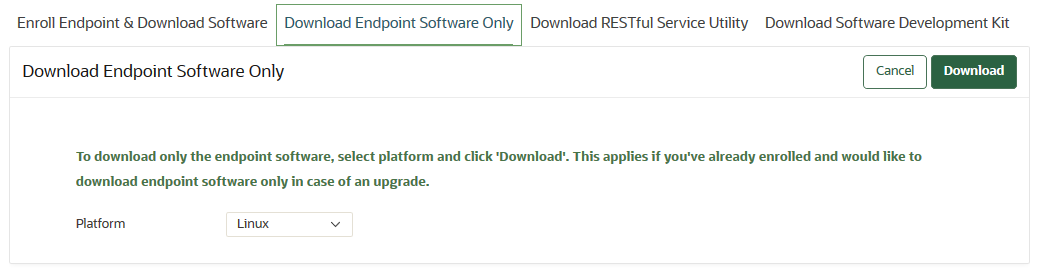
13.8.2 Step 2: Download the Oracle Key Vault Software onto the Endpoint
You download the okvclient.jar file to local computer.
13.8.3 Step 3: Install the Oracle Key Vault Software onto the Endpoint
You must be the endpoint administrator to install the Oracle Key Vault software onto the endpoint.
13.8.4 Step 4: Perform Post-Installation Tasks
After you complete the installation, you can update the library used by TDE and then verify that the endpoint software was installed correctly.
Parent topic: Upgrading Endpoint Software
13.8.5 Upgrading Endpoint Software on an Enrolled Endpoint
You should upgrade the endpoint software on an enrolled endpoint any time you upgraded to a new release of Oracle Key Vault.
okvclient.jar on the endpoint. You do not need to reenroll the endpoint.
Parent topic: Upgrading Endpoint Software