D Security Technical Implementation Guides Compliance Standards
- About Security Technical Implementation Guides
A Security Technical Implementation Guide (STIG) is a methodology followed by the U.S. Department of Defense (DOD). - Enabling and Disabling STIG Rules on Oracle Key Vault
You can enable STIG rules on Oracle Key Vault by enabling Strict mode. - Current Implementation of STIG Rules on Oracle Key Vault
Oracle has developed a security-hardened configuration of Oracle Key Vault that supports U.S. Department of Defense Security Technical Implementation Guide (STIG) recommendations. - Current Implementation of Database STIG Rules
The current implementation of the database STIG rules encompass a wide range of rules. - Current Implementation of Operating System STIG Rules
This topic contains information on the current implementation of operating system STIG guidelines for Oracle Key Vault.
D.1 About Security Technical Implementation Guides
A Security Technical Implementation Guide (STIG) is a methodology followed by the U.S. Department of Defense (DOD).
STIG is designed to reduce the attack surface of computer systems and networks, thereby ensuring a lockdown of highly confidential information stored within the DOD network. STIGs provide secure configuration standards for the DOD's Information Assurance (IA) and IA-enabled devices and systems. STIGs are created by the Defense Information Systems Agency (DISA).
For over a decade, Oracle has worked closely with the DOD to develop, publish, and maintain a growing list of STIGs for a variety of core Oracle products and technologies including:
-
Oracle Database
-
Oracle Solaris
-
Oracle Linux
-
Oracle WebLogic
When STIGs are updated, Oracle analyzes the latest recommendations in order to identify new ways to improve the security of its products by:
-
Implementing new and innovative security capabilities that are then added to future STIG updates
-
Delivering functionality to automate the assessment and implementation of STIG recommendations
-
Improving "out of the box" security configuration settings based upon STIG recommendations
D.2 Enabling and Disabling STIG Rules on Oracle Key Vault
You can enable STIG rules on Oracle Key Vault by enabling Strict mode.
- Enabling STIG Rules on Oracle Key Vault
You enable STIG rules (strict mode) from the command line. - Disabling STIG Rules on Oracle Key Vault
You disable STIG rules (strict mode) from the command line.
D.2.1 Enabling STIG Rules on Oracle Key Vault
You enable STIG rules (strict mode) from the command line.
Parent topic: Enabling and Disabling STIG Rules on Oracle Key Vault
D.2.2 Disabling STIG Rules on Oracle Key Vault
You disable STIG rules (strict mode) from the command line.
Parent topic: Enabling and Disabling STIG Rules on Oracle Key Vault
D.3 Current Implementation of STIG Rules on Oracle Key Vault
Oracle has developed a security-hardened configuration of Oracle Key Vault that supports U.S. Department of Defense Security Technical Implementation Guide (STIG) recommendations.
Table D-1 lists the three vulnerability categories that STIG recommendations address.
Table D-1 Vulnerability Categories
| Category | Description |
|---|---|
|
CAT I |
Any vulnerability, the exploitation of which will, directly and immediately result in loss of Confidentiality, Availability, or Integrity. |
|
CAT II |
Any vulnerability, the exploitation of which has a potential to result in loss of Confidentiality, Availability, or Integrity. |
|
CAT III |
Any vulnerability, the existence of which degrades measures to protect against loss of Confidentiality, Availability, or Integrity. |
D.4 Current Implementation of Database STIG Rules
The current implementation of the database STIG rules encompass a wide range of rules.
Table D-2 shows the current implementation of Database STIG rules on Oracle Key Vault.
Table D-2 Current Implementation of Database STIG Rules
| STIG ID | Title | Severity | Addressed by Script | Addressed by Documentation | Notes |
|---|---|---|---|---|---|
|
DG0004-ORACLE11 |
Application object owner accounts should be disabled when not performing installation or maintenance actions. |
CAT II |
No |
No |
Currently not supported |
|
DG0008-ORACLE11 |
Application objects should be owned by accounts authorized for ownership. |
CAT II |
No |
Yes |
The below list of users are either Oracle Key Vault application users or those that appear to be from the Oracle Database installation.
|
|
DG0014-ORACLE11 |
Default demonstration and sample database objects and applications should be removed. |
CAT II |
No |
No |
Implemented by default. All default demonstration and sample database objects have been removed. |
|
DG0071-ORACLE11 |
New passwords must be required to differ from old passwords by more than four characters. |
CAT II |
No |
No |
Currently not supported |
|
DG0073-ORACLE11 |
DBMS failed login account lock |
CAT II |
Yes |
No |
Implemented in strict mode.
|
|
DG0075-ORACLE11 |
DBMS links to external databases |
CAT II |
No |
No |
Implemented by default |
|
DG0077-ORACLE11 |
Production databases should be protected from unauthorized access by developers on shared production/development host systems. |
CAT II |
No |
No |
Implemented by default |
|
DG0116-ORACLE11 |
Database privileged role assignments should be restricted to IAO-authorized DBMS accounts. |
CAT II |
No |
Yes |
See DG0116-ORACLE11 STIG Guideline Guideline. |
|
DG0117-ORACLE11 |
Administrative privileges should be assigned to database accounts via database roles. |
CAT II |
No |
No |
Currently not supported |
|
DG0121-ORACLE11 |
Application users privileges should be restricted to assignment using application user roles. |
CAT II |
No |
No |
Currently not supported |
|
DG0123-ORACLE11 |
Access to DBMS system tables and other configuration or metadata should be restricted to DBAs. |
CAT II |
No |
No |
Currently not supported |
|
DG0125-ORACLE11 |
DBMS account passwords should be set to expire every 60 days or more frequently. |
CAT II |
Yes |
No |
Implemented in strict mode. the |
|
DG0126-ORACLE11 |
Password reuse should be prevented where supported by the DBMS. |
CAT II |
No |
No |
Implemented by default |
|
DG0128-ORACLE11 |
DBMS default accounts should be assigned custom passwords. |
CAT I |
Yes |
No |
Implemented in strict mode. Accounts such as
|
|
DG0133-ORACLE11 |
Unlimited account lock times should be specified for locked accounts. |
CAT II |
Yes |
No |
Implemented in strict mode. The |
|
DG0141-ORACLE11 |
Attempts to bypass access controls should be audited. |
CAT II |
Yes |
No |
Implemented in strict mode.
|
|
DG0142-ORACLE11 |
Changes to configuration options must be audited. |
CAT II |
No |
No |
Implemented by default |
|
DG0192-ORACLE11 |
Remote database or other external access should use fully-qualified names. |
CAT II |
No |
No |
Currently not supported |
|
DO0231-ORACLE11 |
Application owner accounts should have a dedicated application tablespace. |
CAT II |
No |
No |
Currently not supported |
|
DO0250-ORACLE11 |
Fixed user and public database links should be authorized for use. |
CAT II |
No |
No |
Implemented by default |
|
DO0270-ORACLE11 |
A minimum of two Oracle redo log groups/files should be defined and configured to be stored on separate, archived physical disks or archived directories on a RAID device. |
CAT II |
No |
No |
Currently not supported |
|
DO0350-ORACLE11 |
Oracle system privileges should not be directly assigned to unauthorized accounts. |
CAT II |
No |
No |
Currently not supported |
|
DO3475-ORACLE11 |
Execute permission should be revoked from
|
CAT II |
No |
No |
Currently not supported |
|
DO3536-ORACLE11 |
The |
CAT II |
Yes |
No |
Implemented in strict mode.
|
|
DO3540-ORACLE11 |
The Oracle |
CAT II |
No |
No |
Implemented by default |
|
DO3609-ORACLE11 |
System privileges granted using the |
CAT II |
No |
No |
Currently not supported |
|
DO3610-ORACLE11 |
Required object auditing should be configured. |
CAT II |
No |
No |
Currently not supported |
|
DO3689-ORACLE11 |
Object permissions granted to |
CAT II |
No |
No |
Currently not supported |
|
DO3696-ORACLE11 |
The Oracle |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-021900 |
The Oracle |
CAT I |
No |
No |
Implemented by default |
|
O121-BP-022000 |
The Oracle |
CAT I |
No |
No |
Implemented by default |
|
O121-BP-022700 |
The Oracle Listener must be configured to require administration authentication. |
CAT I |
No |
No |
Implemented by default |
|
O121-C1-004500 |
DBA OS accounts must be granted only those host system privileges necessary for the administration of the DBMS. |
CAT I |
No |
Yes |
In Oracle Key Vault, only OS user oracle can connect to the Database as SYSDBA. Oracle user is granted only necessary privileges. |
|
O121-C1-011100 |
Oracle software must be evaluated and patched against newly found vulnerabilities. |
CAT I |
No |
Yes |
Apply latest Oracle Key Vault release bundle patch which patches OS, Database, Java on the Oracle Key Vault server. |
|
O121-C1-015400 |
The DBMS, when using PKI-based authentication, must enforce authorized access to the corresponding private key. |
CAT I |
No |
No |
Implemented by default |
|
O121-C1-019700 |
The DBMS must employ cryptographic mechanisms preventing the unauthorized disclosure of information during transmission unless the transmitted data is otherwise protected by alternative physical measures. |
CAT I |
No |
No |
Implemented by default |
|
O121-N1-015601 |
Applications must obscure feedback of authentication information during the authentication process to protect the information from possible exploitation or use by unauthorized individuals. |
CAT I |
No |
Yes |
All passwords in Oracle Key Vault are either stored in Oracle Wallet or encrypted in the database. |
|
O121-N1-015602 |
When using command-line tools such as Oracle SQL*Plus, which can accept a plain-text password, users must use an alternative login method that does not expose the password. |
CAT I |
No |
No |
Cannot fully comply. However, it is highly unlikely and it is not recommended to login to the Oracle Key Vault server and run scripts that needs passwords to be passed in it. Please contact Oracle support for any such requirement. |
|
O121-OS-004600 |
Use of the DBMS software installation account must be restricted to DBMS software installation. |
CAT I |
No |
No |
Implemented by default |
|
O121-BP-021300 |
Oracle instance names must not contain Oracle version numbers. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-021400 |
Fixed user and public database links must be authorized for use. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022100 |
The Oracle |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022200 |
The Oracle |
CAT II |
No |
No |
Currently not supported |
|
O121-BP-022300 |
System privileges granted using the |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022400 |
System privileges must not be granted to
|
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022500 |
Oracle roles granted using the |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022600 |
Object permissions granted to |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-022800 |
Application role permissions must not be assigned to the
Oracle |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-023000 |
Connections by mid-tier web and application systems to the Oracle DBMS must be protected, encrypted, and authenticated according to database, web, application, enclave, and network requirements. |
CAT II |
No |
Yes |
All communications between Oracle Key Vault and endpoints is over TLS. |
|
O121-BP-023200 |
Unauthorized database links must not be defined and left active. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-023600 |
Only authorized system accounts must have the SYSTEM table space specified as the default table space. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-023900 |
The Oracle |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-025200 |
Credentials stored and used by the DBMS to access remote databases or applications must be authorized and restricted to authorized users. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-025700 |
DBMS data files must be dedicated to support individual applications. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-025800 |
Changes to configuration options must be audited. |
CAT II |
No |
No |
Implemented by default |
|
O121-BP-026600 |
Network client connections must be restricted to supported versions. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-003000 |
The DBMS must enforce Discretionary Access Control (DAC) policy allowing users to specify and control sharing by named individuals, groups of individuals, or by both, limiting propagation of access rights and including or excluding access to the granularity of a single user. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-003400 |
DBMS processes or services must run under custom and dedicated OS accounts. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-003600 |
A single database connection configuration file must not be used to configure all database clients. |
CAT II |
No |
Yes |
Clients of Oracle Key Vault cannot access its internal database. |
|
O121-C2-006700 |
A DBMS utilizing Discretionary Access Control (DAC) must enforce a policy that includes or excludes access to the granularity of a single user. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-006900 |
The DBMS must allow designated organizational personnel to select specific events that can be audited by the database. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-011500 |
Default demonstration, sample databases, database objects, and applications must be removed. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-011600 |
Unused database components, DBMS software, and database objects must be removed. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-011700 |
Unused database components that are integrated in the DBMS and cannot be uninstalled must be disabled. |
CAT II |
No |
No |
Currently not supported |
|
O121-C2-014600 |
The DBMS must support organizational requirements to enforce password encryption for storage. |
CAT II |
No |
No |
Implemented by default |
|
O121-C2-015100 |
DBMS passwords must not be stored in compiled, encoded, or encrypted batch jobs or compiled, encoded, or encrypted application source code. |
CAT II |
No |
No |
Implemented by default |
|
O121-C1-015000 |
DBMS default accounts must be assigned custom passwords. |
CAT I |
No |
No |
Implemented by default |
|
O121-C2-002100 |
The DBMS must automatically disable accounts after a period of 35 days of account inactivity. |
CAT II |
Yes |
No |
Implemented in strict mode.
|
|
O121-C2-004900 |
The DBMS must verify account lockouts and persist until reset by an administrator. |
CAT II |
Yes |
No |
None |
|
O121-C2-013800 |
The DBMS must support organizational requirements to disable user accounts after a defined time period of inactivity set by the organization. |
CAT II |
Yes |
No |
Implemented in strict mode.
|
|
O121-C2-015200 |
The DBMS must enforce password maximum lifetime restrictions. |
CAT II |
Yes |
No |
Implemented in strict mode.
|
When you apply the database STIG rules in Oracle Key Vault, the default values listed below applies to the user account profile parameters.
Table D-3 User Account Profile Parameters
| Parameter | Description | Default Value | Default Value in Strict STIG mode |
|---|---|---|---|
|
Failed Login Attempts |
Number of consecutive failed attempts to log in to the user account before the account is locked. |
3 |
3 |
|
Password Life Time (in days) |
Number of days the same password can be used for authentication. |
180 |
35 |
|
Password Grace Time (in days) |
Number of days after the grace period begins during which a warning is issued, and login is allowed. |
5 |
0 |
|
Password Reuse Max |
Number of password changes required before the current password can be reused. |
UNLIMITED |
UNLIMITED |
|
Password Reuse Time (in days) |
Number of days before which a password cannot be reused. |
365 |
365 |
|
Password Lock Time (in days) |
Number of days an account will be locked after the specified number of consecutive failed login attempts. After the time passes, then the account becomes unlocked. |
1 |
UNLIMITED |
You can configure user account profile parameters to use non-default values even when Oracle Key Vault is operating with STIG rules enabled (strict mode).
If you configure a value that is less strict than the corresponding non-STIG default value, a warning message, as shown below, is displayed indicating that the current value is not STIG compliant.
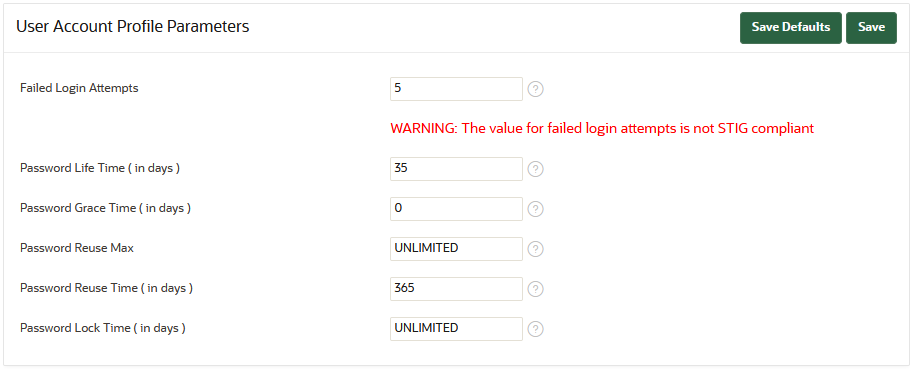
Description of the illustration 2110_user_account_profile_management.png
The above warning is displayed when the values are set to less stricter values than the STIG recommendation. In the above figure, Failed Login Attempts is set the 5 where as the STIG recommended value is 3 and hence the warning is displayed.
The Save Defaults operation resets the user account profile parameters to their default values. If STIG rules are enabled (strict mode), then profile parameters values are restored to the default values used for the strict STIG mode configuration. Otherwise, default values that apply to STIG configuration are restored.
When you enable strict STIG mode on a multi-master cluster node, user account profile parameter values are changed to the strict STIG mode default values. However, these changes are applied only to the current node. When enabling strict STIG mode, Oracle recommends that you first enable the strict STIG mode on all cluster nodes individually. Afterward, you can optionally configure the non-default values from any cluster node.
- Additional STIG Guidelines Notes
Learn about additional advice regarding STIG guidelines.
Related Topics
D.4.1 Additional STIG Guidelines Notes
Learn about additional advice regarding STIG guidelines.
- DG0116-ORACLE11 STIG Guideline
This section provides information about the STIG guideline for DG0116-ORACLE11.
Parent topic: Current Implementation of Database STIG Rules
D.4.1.1 DG0116-ORACLE11 STIG Guideline
This section provides information about the STIG guideline for DG0116-ORACLE11.
Table D-4 Accounts and Role Assignments in Oracle Key Vault
| Account | Role Assignment |
|---|---|
|
|
|
|
|
|
Parent topic: Additional STIG Guidelines Notes
D.5 Current Implementation of Operating System STIG Rules
This topic contains information on the current implementation of operating system STIG guidelines for Oracle Key Vault.
Table D-4 shows the current implementation of Operating System STIG Rules on Oracle Key Vault.
Table D-5 Operating System STIG Guideline Set Reference
| Reference | Detail |
|---|---|
| Document | Oracle Linux 8 Security Technical Implementation Guide |
| Version | 1 |
| Release | 5 |
| Release date | January 13, 2023 |
| Document link | Oracle Linux Security Technical Implementation Guide |
Table D-6 User Action - Definition and Guidelines
| User Action | Description of the Guideline |
|---|---|
| None | The guideline is implemented by default and no user action is required. |
| Enable strict mode | The guideline can be implemented by switching the
appliance to strict mode.
See Also: |
| Site policy | The guideline can be implemented depending on local policy and it requires administrator action. See the Notes column for additional information on implementation. |
| Administrative task | The guideline implementation is an administrator configuration action after installation or upgrade. It can also be a regularly used and defined administrative procedure. |
Table D-7 Current Implementation of Operating System STIG Guidelines for Oracle Key Vault
| STIG ID | Severity | User Action | Title | Notes |
|---|---|---|---|---|
| OL08-00-010000 | CAT I | - | OL 8 must be a vendor-supported release. | Implemented by default |
| OL08-00-010140 | CAT I | - | OL 8 operating systems booted with United Extensible Firmware Interface (UEFI) must require authentication upon booting into single-user mode and maintenance. | Not applicable |
| OL08-00-010150 | CAT I | - | OL 8 operating systems booted with a BIOS must require authentication upon booting into single-user and maintenance modes. | Not applicable |
| OL08-00-010370 | CAT I | - | YUM must be configured to prevent the installation of patches, service packs, device drivers, or OL 8 system components that have not been digitally signed using a certificate that is recognized and approved by the organization. | Implemented by default |
| OL08-00-010460 | CAT I | - | There must be no shosts.equiv files
on the OL 8 operating system.
|
Implemented by default |
| OL08-00-010470 | CAT I | - | There must be no .shosts files on
the OL 8 operating system.
|
Implemented by default |
| OL08-00-010820 | CAT I | - | Unattended or automatic logon via the OL 8 graphical user interface must not be allowed. | Not applicable |
| OL08-00-010830 | CAT I | - | OL 8 must not allow users to override SSH environment variables. | Implemented by default |
| OL08-00-020330 | CAT I | - | OL 8 must not allow accounts configured with blank or null passwords. | Implemented by default |
| OL08-00-020331 | CAT I | - | OL 8 must not allow blank or null passwords in the
system-auth file.
|
Implemented by default |
| OL08-00-020332 | CAT I | - | OL 8 must not allow blank or null passwords in the
password-auth file.
|
Implemented by default |
| OL08-00-040000 | CAT I | - | OL 8 must not have the telnet-server package installed. | Implemented by default |
| OL08-00-040010 | CAT I | - | OL 8 must not have the rsh-server
package installed.
|
Implemented by default |
| OL08-00-040171 | CAT I | - | The x86 Ctrl-Alt-Delete key sequence in OL 8 must be disabled if a graphical user interface is installed. | Not applicable |
| OL08-00-040190 | CAT I | - | The Trivial File Transfer Protocol (TFTP) server package must not be installed if not required for OL 8 operational support. | Implemented by default |
| OL08-00-040200 | CAT I | - | The root account must be the only account having unrestricted access to the OL 8 system. | Implemented by default |
| OL08-00-040360 | CAT I | - | A File Transfer Protocol (FTP) server package must not be installed unless mission essential on OL 8. | Implemented by default |
| OL08-00-010049 | CAT II | - | OL 8 must display a banner before granting local or remote access to the system via a graphical user logon. | Not applicable |
| OL08-00-010110 | CAT II | - | OL 8 must encrypt all stored passwords with a FIPS 140-2 approved cryptographic hashing algorithm. | Implemented by default |
| OL08-00-010120 | CAT II | - | OL 8 must employ FIPS 140-2 approved cryptographic hashing algorithms for all stored passwords. | Implemented by default |
| OL08-00-010130 | CAT II | - | The OL 8 shadow password suite must be configured to use a sufficient number of hashing rounds. | Implemented by default |
| OL08-00-010151 | CAT II | - | OL 8 operating systems must require authentication upon booting into rescue mode. | Implemented by default |
| OL08-00-010152 | CAT II | - | OL 8 operating systems must require authentication upon booting into emergency mode. | Implemented by default |
| OL08-00-010159 | CAT II | - | The OL 8 pam_unix.so module must be
configured in the system-auth file to use a FIPS
140-2 approved cryptographic hashing algorithm for system
authentication.
|
Implemented by default |
| OL08-00-010160 | CAT II | - | The OL 8 pam_unix.so module must be
configured in the password-auth file to use a FIPS
140-2 approved cryptographic hashing algorithm for system
authentication.
|
Implemented by default |
| OL08-00-010161 | CAT II | - | OL 8 must prevent system daemons from using Kerberos for authentication. | Implemented by default |
| OL08-00-010162 | CAT II | - | The krb5-workstation package must not be installed on OL 8. | Implemented by default |
| OL08-00-010163 | CAT II | - | The krb5-server package must not be installed on OL 8. | Implemented by default |
| OL08-00-010200 | CAT II | - | OL 8 must be configured so that all network connections associated with SSH traffic are terminate after a period of inactivity. | Implemented by default |
| OL08-00-010210 | CAT II | - | The OL 8 /var/log/messages file
must have mode 0640 or less permissive.
|
Implemented by default |
| OL08-00-010220 | CAT II | - | The OL 8 /var/log/messages file must
be owned by root.
|
Implemented by default |
| OL08-00-010230 | CAT II | - | The OL 8/var/log/messages file must
be group-owned by root.
|
Implemented by default |
| OL08-00-010240 | CAT II | - | The OL 8 /var/log directory must
have mode 0755 or less permissive.
|
Implemented by default |
| OL08-00-010250 | CAT II | - | The OL 8 /var/log directory must be
owned by root.
|
Implemented by default |
| OL08-00-010260 | CAT II | - | The OL 8 /var/log directory must be
group-owned by root.
|
Implemented by default |
| OL08-00-010294 | CAT II | - | The OL 8 operating system must implement DoD-approved TLS encryption in the OpenSSL package. | Implemented by default |
| OL08-00-010372 | CAT II | - | OL 8 must prevent the loading of a new kernel for later execution. | Implemented by default |
| OL08-00-010373 | CAT II | - | OL 8 must enable kernel parameters to enforce Discretionary Access Control (DAC) on symlinks. | Implemented by default |
| OL08-00-010374 | CAT II | - | OL 8 must enable kernel parameters to enforce Discretionary Access Control (DAC) on hardlinks. | Implemented by default |
| OL08-00-010381 | CAT II | - | OL 8 must require users to re-authenticate for privilege escalation and changing roles. | Implemented by default |
| OL08-00-010382 | CAT II | - | OL 8 must restrict privilege elevation to authorized personnel. | Implemented by default |
| OL08-00-010480 | CAT II | - | The OL 8 SSH public host key files must have mode 0644 or less permissive. | Implemented by default |
| OL08-00-010500 | CAT II | - | The OL 8 SSH daemon must perform strict mode checking of home directory configuration files. | Implemented by default |
| OL08-00-010520 | CAT II | - | The OL 8 SSH daemon must not allow authentication using known host's authentication. | Implemented by default |
| OL08-00-010521 | CAT II | - | The OL 8 SSH daemon must not allow Kerberos authentication, except to fulfill documented and validated mission requirements. | Implemented by default |
| OL08-00-010522 | CAT II | - | The OL 8 SSH daemon must not allow GSSAPI authentication, except to fulfill documented and validated mission requirements. | Implemented by default |
| OL08-00-010543 | CAT II | - | OL 8 must use a separate file system for
/tmp.
|
Implemented by default |
| OL08-00-010550 | CAT II | - | OL 8 must not permit direct logons to the root account using remote access via SSH. | Implemented by default |
| OL08-00-010561 | CAT II | - | OL 8 must have the rsyslog service
enabled and active.
|
Implemented by default |
| OL08-00-010571 | CAT II | OL 8 must prevent files with the setuid
and setgid bit set from being executed on the
/boot directory.
|
Implemented by default | |
| OL08-00-010630 | CAT II | - | OL 8 file systems must not execute binary files that are imported via Network File System (NFS). | Not applicable |
| OL08-00-010640 | CAT II | - | OL 8 file systems must not interpret character or block special devices that are imported via NFS. | Not applicable |
| OL08-00-010650 | CAT II | - | OL 8 must prevent files with the setuid
and setgid bit set from being executed on file systems
that are imported via Network File System (NFS).
|
Not applicable |
| OL08-00-010760 | CAT II | - | All OL 8 local interactive user accounts must be assigned a home directory upon creation. | Implemented by default |
| OL08-00-020010 | CAT II | - | OL 8 systems below version 8.2 must automatically lock an account when three unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020011 | CAT II | - | OL 8 systems, versions 8.2 and above, must automatically lock an account when three unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020012 | CAT II | - | OL 8 systems below version 8.2 must automatically lock an account when three unsuccessful logon attempts occur during a 15-minute time period. | Implemented by default |
| OL08-00-020013 | CAT II | - | OL 8 systems, versions 8.2 and above, must automatically lock an account when three unsuccessful logon attempts occur during a 15-minute time period. | Implemented by default |
| OL08-00-020014 | CAT II | OL 8 systems below version 8.2 must automatically lock an account until the locked account is released by an administrator when three unsuccessful logon attempts occur during a 15-minute time period. | Not applicable | |
| OL08-00-020018 | CAT II | - | OL 8 systems below version 8.2 must prevent system messages from being presented when three unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020019 | CAT II | - | OL 8 systems, versions 8.2 and above, must prevent system messages from being presented when three unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020020 | CAT II | - | OL 8 systems below version 8.2 must log user name information when unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020021 | CAT II | - | OL 8 systems, versions 8.2 and above, must log user name information when unsuccessful logon attempts occur. | Implemented by default |
| OL08-00-020022 | CAT II | - | OL 8 systems below version 8.2 must include root when automatically locking an account until the locked account is released by an administrator when three unsuccessful logon attempts occur during a 15-minute time period. | Implemented by default |
| OL08-00-020039 | CAT II | - | OL 8 must have the tmux package
installed.
|
Implemented by default |
| OL08-00-020100 | CAT II | - | OL 8 must ensure the password complexity module is
enabled in the password-auth file.
|
Implemented by default |
| OL08-00-020140 | CAT II | - | OL 8 must require the maximum number of repeating characters of the same character class be limited to four when passwords are changed. | Implemented by default |
| OL08-00-020150 | CAT II | - | OL 8 must require the maximum number of repeating characters be limited to three when passwords are changed. | Implemented by default |
| OL08-00-020160 | CAT II | - | OL 8 must require the change of at least four character classes when passwords are changed. | Implemented by default |
| OL08-00-020180 | CAT II | - | OL 8 passwords for new users or password changes must
have a 24 hours/1 day minimum password lifetime restriction in
/etc/shadow.
|
Implemented by default |
| OL08-00-020190 | CAT II | - | OL 8 passwords for new users or password changes must
have a 24 hours/1 day minimum password lifetime restriction in
/etc/login.defs.
|
Implemented by default |
| OL08-00-020200 | CAT II | enable strict mode | OL 8 user account passwords must have a 60-day maximum password lifetime restriction. | Implemented in strict mode |
| OL08-00-020210 | CAT II | enable strict mode | OL 8 user account passwords must be configured so that existing passwords are restricted to a 60-day maximum lifetime. | Implemented in strict mode |
| OL08-00-020230 | CAT II | - | OL 8 passwords must have a minimum of 15 characters. | Implemented by default |
| OL08-00-020231 | CAT II | enable strict mode | OL 8 passwords for new users must have a minimum of 15 characters. | Implemented in strict mode |
| OL08-00-020263 | CAT II | - | The OL 8 lastlog command must be owned by root. | Implemented by default |
| OL08-00-020264 | CAT II | - | The OL 8 lastlog command must be group-owned by root. | Implemented by default |
| OL08-00-020300 | CAT II | - | OL 8 must prevent the use of dictionary words for passwords. | Implemented by default |
| OL08-00-020310 | CAT II | - | OL 8 must enforce a delay of at least four seconds between logon prompts following a failed logon attempt. | Implemented by default |
| OL08-00-020350 | CAT II | - | OL 8 must display the date and time of the last successful account logon upon an SSH logon. | Implemented by default |
| OL08-00-020351 | CAT II | - | OL 8 default permissions must be defined in such a way that all authenticated users can read and modify only their own files. | Implemented by default |
| OL08-00-030000 | CAT II | - | The OL 8 audit system must be configured to audit the execution of privileged functions and prevent all software from executing at higher privilege levels than users executing the software. | Implemented by default |
| OL08-00-030020 | CAT II | - | The OL 8 System Administrator (SA) and Information System Security Officer (ISSO) (at a minimum) must be alerted of an audit processing failure event. | Implemented by default |
| OL08-00-030040 | CAT II | - | The OL 8 System must take appropriate action when an audit processing failure occurs. | Implemented by default |
| OL08-00-030060 | CAT II | - | The OL 8 audit system must take appropriate action when the audit storage volume is full. | Implemented by default |
| OL08-00-030061 | CAT II | - | The OL 8 audit system must audit local events. | Implemented by default |
| OL08-00-030062 | CAT II | - | OL 8 must label all offloaded audit logs before sending them to the central log server. | Implemented by default |
| OL08-00-030063 | CAT II | - | OL 8 must resolve audit information before writing to disk. | Implemented by default |
| OL08-00-030080 | CAT II | - | OL 8 audit logs must be owned by root to prevent unauthorized read access. | Implemented by default |
| OL08-00-030100 | CAT II | - | The OL 8 audit log directory must be owned by root to prevent unauthorized read access. | Implemented by default |
| OL08-00-030121 | CAT II | - | The OL 8 audit system must protect auditing rules from unauthorized change. | Implemented by default |
| OL08-00-030122 | CAT II | - | The OL 8 audit system must protect logon UIDs from unauthorized change. | Implemented by default |
| OL08-00-030130 | CAT II | - | OL 8 must generate audit records for all account
creation events that affect /etc/shadow.
|
Implemented by default |
| OL08-00-030140 | CAT II | - | OL 8 must generate audit records for all account
creation events that affect
/etc/security/opasswd.
|
Implemented by default |
| OL08-00-030150 | CAT II | - | OL 8 must generate audit records for all account
creation events that affect /etc/passwd.
|
Implemented by default |
| OL08-00-030160 | CAT II | - | OL 8 must generate audit records for all account
creation events that affect /etc/gshadow.
|
Implemented by default |
| OL08-00-030170 | CAT II | - | OL 8 must generate audit records for all account
creation events that affect /etc/group.
|
Implemented by default |
| OL08-00-030171 | CAT II | - | OL 8 must generate audit records for all account
creations, modifications, disabling, and termination events that affect
/etc/sudoers.
|
Implemented by default |
| OL08-00-030172 | CAT II | - | OL 8 must generate audit records for all account
creations, modifications, disabling, and termination events that affect
/etc/sudoers.d/.
|
Implemented by default |
| OL08-00-030180 | CAT II | - | The OL 8 audit package must be installed. | Implemented by default |
| OL08-00-030181 | CAT II | - | OL 8 audit records must contain information to establish what type of events occurred, the source of events, where events occurred, and the outcome of events. | Implemented by default |
| OL08-00-030190 | CAT II | - | OL 8 must generate audit records for any use of the
su command.
|
Implemented by default |
| OL08-00-030200 | CAT II | - | The OL 8 audit system must be configured to audit any use
of the setxattr, fsetxattr,
lsetxattr, removexattr,
fremovexattr, and lremovexattr
system calls.
|
Implemented by default |
| OL08-00-030250 | CAT II | - | OL 8 must generate audit records for any use of the
chage command.
|
Implemented by default |
| OL08-00-030260 | CAT II | - | OL 8 must generate audit records for any uses of the
chcon command.
|
Implemented by default |
| OL08-00-030280 | CAT II | - | OL 8 must generate audit records for any use of the
ssh-agent command.
|
Implemented by default |
| OL08-00-030290 | CAT II | - | OL 8 must generate audit records for any use of the
passwd command.
|
Implemented by default |
| OL08-00-030300 | CAT II | - | OL 8 must generate audit records for any use of the
mount command.
|
Implemented by default |
| OL08-00-030301 | CAT II | - | OL 8 must generate audit records for any use of the
umount command.
|
Implemented by default |
| OL08-00-030302 | CAT II | - | OL 8 must generate audit records for any use of the
mount syscall.
|
Implemented by default |
| OL08-00-030310 | CAT II | - | OL 8 must generate audit records for any use of the
unix_update command.
|
Implemented by default |
| OL08-00-030311 | CAT II | - | OL 8 must generate audit records for any use of the
postdrop command.
|
Implemented by default |
| OL08-00-030312 | CAT II | - | OL 8 must generate audit records for any use of the
postqueue command.
|
Implemented by default |
| OL08-00-030313 | CAT II | - | OL 8 must generate audit records for any use of the
semanage command.
|
Implemented by default |
| OL08-00-030314 | CAT II | - | OL 8 must generate audit records for any use of the
setfiles command.
|
Implemented by default |
| OL08-00-030315 | CAT II | - | OL 8 must generate audit records for any use of the
userhelper command.
|
Implemented by default |
| OL08-00-030316 | CAT II | - | OL 8 must generate audit records for any use of the
setsebool command.
|
Implemented by default |
| OL08-00-030317 | CAT II | - | OL 8 must generate audit records for any use of the
unix_chkpwd command.
|
Implemented by default |
| OL08-00-030320 | CAT II | - | OL 8 must generate audit records for any use of the
ssh-keysign command.
|
Implemented by default |
| OL08-00-030330 | CAT II | - | OL 8 must generate audit records for any use of the
setfacl command.
|
Implemented by default |
| OL08-00-030340 | CAT II | - | OL 8 must generate audit records for any use of the
pam_timestamp_check command.
|
Implemented by default |
| OL08-00-030350 | CAT II | - | OL 8 must generate audit records for any use of the
newgrp command.
|
Implemented by default |
| OL08-00-030360 | CAT II | - | OL 8 must generate audit records for any use of the
init_module and finit_module
system calls.
|
Implemented by default |
| OL08-00-030361 | CAT II | - | OL 8 must generate audit records for any use of the
rename, unlink,
rmdir, renameat, and
unlinkat system calls.
|
Implemented by default |
| OL08-00-030370 | CAT II | - | OL 8 must generate audit records for any use of the
gpasswd command.
|
Implemented by default |
| OL08-00-030390 | CAT II | - | OL 8 must generate audit records for any use of the
delete_module syscall.
|
Implemented by default |
| OL08-00-030400 | CAT II | - | OL 8 must generate audit records for any use of the
crontab command.
|
Implemented by default |
| OL08-00-030410 | CAT II | - | OL 8 must generate audit records for any use of the
chsh command.
|
Implemented by default |
| OL08-00-030420 | CAT II | - | OL 8 must generate audit records for any use of the
truncate, ftruncate,
creat, open,
openat, and open_by_handle_at
system calls.
|
Implemented by default |
| OL08-00-030480 | CAT II | - | OL 8 must generate audit records for any use of the
chown, fchown,
fchownat, and lchown system
calls.
|
Implemented by default |
| OL08-00-030490 | CAT II | - | OL 8 must generate audit records for any use of the
chmod, fchmod, and
fchmodat system calls.
|
Implemented by default |
| OL08-00-030550 | CAT II | - | OL 8 must generate audit records for any use of the
sudo command.
|
Implemented by default |
| OL08-00-030560 | CAT II | - | OL 8 must generate audit records for any use of the
usermod command.
|
Implemented by default |
| OL08-00-030570 | CAT II | - | OL 8 must generate audit records for any use of the
chacl command.
|
Implemented by default |
| OL08-00-030580 | CAT II | - | OL 8 must generate audit records for any use of the
kmod command.
|
Implemented by default |
| OL08-00-030600 | CAT II | - | OL 8 must generate audit records for any attempted
modifications to the lastlog file.
|
Implemented by default |
| OL08-00-030610 | CAT II | - | OL 8 must allow only the Information System Security Manager (ISSM) (or individuals or roles appointed by the ISSM) to select which auditable events are to be audited. | Implemented by default |
| OL08-00-030620 | CAT II | - | OL 8 audit tools must have a mode of 0755 or less permissive. | Implemented by default |
| OL08-00-030630 | CAT II | - | OL 8 audit tools must be owned by root. | Implemented by default |
| OL08-00-030640 | CAT II | - | OL 8 audit tools must be group-owned by root. | Implemented by default |
| OL08-00-030670 | CAT II | - | OL 8 must have the packages required for offloading audit logs installed. | Implemented by default |
| OL08-00-030700 | CAT II | - | OL 8 must take appropriate action when the internal event queue is full. | Implemented by default |
| OL08-00-040001 | CAT II | - | OL 8 must not have any automated bug reporting tools installed. | Implemented by default |
| OL08-00-040002 | CAT II | - | OL 8 must not have the sendmail package
installed.
|
Implemented by default |
|
OL08-00-040021 |
CAT II | OL 8 must not have the asynchronous transfer mode (ATM) kernel module installed if not required for operational support. | Implemented by default | |
| OL08-00-040022 | CAT II | OL 8 must not have the Controller Area Network (CAN) kernel module installed if not required for operational support. | Implemented by default | |
| OL08-00-040023 | CAT II | OL 8 must not have the stream control transmission protocol (SCTP) kernel module installed if not required for operational support. | Implemented by default | |
| OL08-00-040080 | CAT II | - | OL 8 must be configured to disable the ability to use USB mass storage devices. | Implemented by default |
| OL08-00-040111 | CAT II | - | OL 8 Bluetooth must be disabled. | Implemented by default |
| OL08-00-040129 | CAT II | - | OL 8 must mount /var/log/audit with the
nodev option.
|
Not applicable |
| OL08-00-040130 | CAT II | - | OL 8 must mount /var/log/audit with the
nosuid option.
|
Not applicable |
| OL08-00-040131 | CAT II | - | OL 8 must mount /var/log/audit with the
noexec option.
|
Not applicable |
| OL08-00-040160 | CAT II | - | All OL 8 networked systems must have and implement SSH to protect the confidentiality and integrity of transmitted and received information, as well as information during preparation for transmission. | Implemented by default |
| OL08-00-040161 | CAT II | - | OL 8 must force a frequent session key renegotiation for SSH connections to the server. | Implemented by default |
| OL08-00-040209 | CAT II | - | OL 8 must prevent IPv4 Internet Control Message Protocol (ICMP) redirect messages from being accepted. | Implemented by default |
| OL08-00-040210 | CAT II | - | OL 8 must prevent IPv6 Internet Control Message Protocol (ICMP) redirect messages from being accepted. | Not applicable |
| OL08-00-040220 | CAT II | - | OL 8 must not send Internet Control Message Protocol (ICMP) redirects. | Implemented by default |
| OL08-00-040230 | CAT II | - | OL 8 must not respond to Internet Control Message Protocol (ICMP) echoes sent to a broadcast address. | Implemented by default |
| OL08-00-040239 | CAT II | - | OL 8 must not forward IPv4 source-routed packets. | Implemented by default |
| OL08-00-040240 | CAT II | - | OL 8 must not forward IPv6 source-routed packets. | Not applicable |
| OL08-00-040249 | CAT II | - | OL 8 must not forward IPv4 source-routed packets by default. | Implemented by default |
| OL08-00-040250 | CAT II | - | OL 8 must not forward IPv6 source-routed packets by default. | Not applicable |
| OL08-00-040260 | CAT II | - | OL 8 must not enable IPv6 packet forwarding unless the system is a router. | Not applicable |
| OL08-00-040261 | CAT II | - | OL 8 must not accept router advertisements on all IPv6 interfaces. | Not applicable |
| OL08-00-040262 | CAT II | - | OL 8 must not accept router advertisements on all IPv6 interfaces by default. | Not applicable |
| OL08-00-040270 | CAT II | - | OL 8 must not allow interfaces to perform Internet Control Message Protocol (ICMP) redirects by default. | Implemented by default |
| OL08-00-040279 | CAT II | - | OL 8 must ignore IPv4 Internet Control Message Protocol (ICMP) redirect messages. | Implemented by default |
| OL08-00-040280 | CAT II | - | OL 8 must ignore IPv6 Internet Control Message Protocol (ICMP) redirect messages. | Not applicable |
| OL08-00-040281 | CAT II | - | OL 8 must disable access to the network
bpf syscall from unprivileged processes.
|
Implemented by default |
| OL08-00-040283 | CAT II | - | OL 8 must restrict exposed kernel pointer addresses access. | Implemented by default |
| OL08-00-040284 | CAT II | - | OL 8 must disable the use of user namespaces. | Implemented by default |
| OL08-00-040285 | CAT II | - | OL 8 must use reverse path filtering on all IPv4 interfaces. | Implemented by default |
| OL08-00-040286 | CAT II | - | OL 8 must enable hardening for the Berkeley Packet Filter Just-in-time compiler. | Implemented by default |
| OL08-00-040290 | CAT II | - | OL 8 must be configured to prevent unrestricted mail relaying. | Not applicable |
| OL08-00-040340 | CAT II | - | OL 8 remote X connections for interactive users must be disabled unless to fulfill documented and validated mission requirements. | Implemented by default |
| OL08-00-040341 | CAT II | - | The OL 8 SSH daemon must prevent remote hosts from connecting to the proxy display. | Implemented by default |
| OL08-00-040350 | CAT II | - | If the Trivial File Transfer Protocol (TFTP) server is required, the OL 8 TFTP daemon must be configured to operate in secure mode. | Not applicable |
| OL08-00-040390 | CAT II | - | OL 8 must not have the tuned package
installed if not required for operational support.
|
Implemented by default |
| OL08-00-010171 | CAT III | - | OL 8 must have the policycoreutils
package installed.
|
Implemented by default |
| OL08-00-010292 | CAT III | - | The OL 8 SSH server must be configured to use strong entropy. | Implemented by default |
| OL08-00-010375 | CAT III | - | OL 8 must restrict access to the kernel message buffer. | Implemented by default |
| OL08-00-010376 | CAT III | - | OL 8 must prevent kernel profiling by unprivileged users. | Implemented by default |
| OL08-00-010390 | CAT III | - | OL 8 must have the package required for multifactor authentication installed. | Implemented by default |
| OL08-00-010440 | CAT III | - | YUM must remove all software components after updated versions have been installed on OL 8. | Implemented by default |
| OL08-00-010541 | CAT III | - | OL 8 must use a separate file system for
/var/log.
|
Implemented by default |
| OL08-00-020024 | CAT III | - | OL 8 must limit the number of concurrent sessions to 10 for all accounts and/or account types. | Implemented by default |
| OL08-00-020110 | CAT III | - | OL 8 must enforce password complexity by requiring that at least one uppercase character be used. | Implemented by default |
| OL08-00-020120 | CAT III | - | OL 8 must enforce password complexity by requiring that at least one lowercase character be used. | Implemented by default |
| OL08-00-020130 | CAT III | - | OL 8 must enforce password complexity by requiring that at least one numeric character be used. | Implemented by default |
| OL08-00-020170 | CAT III | - | OL 8 must require the change of at least 8 characters when passwords are changed. | Implemented by default |
| OL08-00-020220 | CAT III | - | OL 8 must be configured in the
password-auth file to prohibit password reuse
for a minimum of five generations.
|
Implemented by default |
| OL08-00-020280 | CAT III | - | All OL 8 passwords must contain at least one special character. | Implemented by default |
| OL08-00-030741 | CAT III | - | OL 8 must disable the chrony daemon from acting as a server. | Implemented by default |
| OL08-00-030742 | CAT III | - | OL 8 must disable network management of the chrony daemon. | Implemented by default |
| OL08-00-040024 | CAT III | - | OL 8 must disable the transparent inter-process communication (TIPC) protocol. | Implemented by default |
| OL08-00-040025 | CAT III | - | OL 8 must disable mounting of cramfs. | Implemented by default |
| OL08-00-040026 | CAT III | - | OL 8 must disable IEEE 1394 (FireWire) Support. | Implemented by default |