16 Managing Certificates
In addition to Oracle Key Vault-generated certificates, you can manage third-party certificates.
- Rotating Certificates
You can rotate both Oracle Key Vault-generated certificates or third-party certificates. - Managing Console Certificates
You can use the Oracle Key Vault management console to manage console certificates.
16.1 Rotating Certificates
You can rotate both Oracle Key Vault-generated certificates or third-party certificates.
- About Rotating Certificates
The certificate rotation process captures all certificates in the Oracle Key Vault server. This operation does not rotate the console certificates. - Advice for Managing Certificate Rotations
Oracle Key Vault provides advice on the best ways to rotate certificates. - Factors That May Affect the Certificate Rotation Process
- Rotating All Certificates
You can use the Oracle Key Vault management console to rotate certificates. - Checking the Certificate Rotation Status
You can use the Oracle Key Vault management console to check the status of a certificate rotation.
Parent topic: Managing Certificates
16.1.1 About Rotating Certificates
The certificate rotation process captures all certificates in the Oracle Key Vault server. This operation does not rotate the console certificates.
A certificate in Oracle Key Vault lasts 730 days. If you do not rotate the certificate (both server and endpoint certificates), then the endpoints that use the certificate cannot connect to the Oracle Key Vault server. When this happens, you must re-enroll the endpoint. To avoid this scenario, you can configure an alert to remind you to rotate the certificate before the 730-day limit is up. The rotation process handles the rotation for all certificates in one operation. You can find how much time the Oracle Key Vault server certificate has before it expires by checking the OKV Server Certificate Expiration setting on the Configure Alerts page in the Oracle Key Vault management console. To find the expiry time of the endpoints' certificates, you must to navigate to the Endpoints page and check the Certificate Expires field.
In addition to standalone environments, you can rotate certificates in primary-standby and multi-master cluster environments. In both, Oracle Key Vault automatically synchronizes the certificates in both systems in a primary-standby configuration, and in all nodes in a multi-master cluster configuration. You do not have to perform any extra configuration.
Related Topics
Parent topic: Rotating Certificates
16.1.2 Advice for Managing Certificate Rotations
Oracle Key Vault provides advice on the best ways to rotate certificates.
- Do not initiate a certificate rotation while a node addition is in progress.
- Do not try node operations (such as adding or disabling nodes) while a certificate rotation is in process.
- You cannot initiate certificate rotation unless all nodes in the cluster are active. You can check if a node is active by checking the Cluster Monitoring page. (Click the Cluster tab, and then select Monitoring from the left navigation bar.)
- In a primary-standby configuration, do not perform certificate rotation if the primary database is in read-only restricted mode. Only initiate a certificate rotation when both servers in the configuration are active and synchronized with each other.
- If you are performing certificate rotation on a system that was upgraded from a previous release, ensure that you upgrade the endpoints as well. Endpoints whose software has not been upgraded will not receive updated credentials.
- You cannot perform a certificate rotation while a backup operation or a restore operation is in progress.
- Before performing a certificate rotation, back up the Oracle Key Vault system.
- In order for the certificate rotation process to fully complete, you must delete and re-enroll all endpoints that are not in the Enrolled state. If you no longer need the endpoint, then you only need to delete it.
Parent topic: Rotating Certificates
16.1.3 Factors That May Affect the Certificate Rotation Process
- Each cluster node only generates certificates for a small set of endpoints. These endpoints are those whose creator node (the node on which the certificates are generated) it is. (You can find an endpoint's creator node in the Oracle Key Vault management console by going to the Endpoints page, and then looking for the creator node for each endpoint.) If all endpoints were created before an upgrade from Oracle Key Vault release 12.2, then it is possible that they may all be associated with one single cluster node. This can make the rotation process slower than if the endpoints had been created on different cluster nodes.
- During the rotation process, Oracle Key Vault rotates endpoints in batches on each node of the cluster, with a maximum number of endpoints that are allowed to be in the rotated state at any one time. At least one of those rotated endpoints must receive its new certificates and acknowledge receipt (involving at least two communications with the server) before the server moves on to processing another endpoint. If all endpoints are considered to have been created on a single Oracle Key Vault cluster node, then the rotation process may degenerate to rotating a few endpoints at a time across the cluster.
- In order to receive the new certificates, the endpoint must reach out to the node on which its certificates have been generated (that is, the creator node). In a multi-master cluster configuration, whenever the endpoint attempts to make a connection to Oracle Key Vault, it performs the following actions:
- First, it obtains the list of server IPs from its configuration file (
okvclient.ora). - Next, it picks one at random from those in the cluster subgroup to which the endpoint’s creator node belongs.
The endpoint reaches out to a random Oracle Key Vault cluster node, and not necessarily to its creator node. This means that even if the Oracle Key Vault management console shows that the endpoint has had its certificates rotated, the endpoint may not receive the new certificates for some considerable period of time, despite making repeated attempts to reach out to the Oracle Key Vault cluster. An endpoint can only successfully receive an update if it has at least one object uploaded to the Oracle Key Vault server. You can check if the endpoint has objects by executing the
okvutil listcommand.
- First, it obtains the list of server IPs from its configuration file (
- If a given endpoint does not receive its rotated certificates due to network or other issues, or is in the "Suspended" state, Oracle recommends that you re-enenroll the endpoint, or even delete it. This will allow the certificate rotation process to continue on to completion. You can find the current certificate rotation status by going to the Endpoints page and looking for Common Name of Certificate Issuer.
Related Topics
Parent topic: Rotating Certificates
16.1.4 Rotating All Certificates
You can use the Oracle Key Vault management console to rotate certificates.
Related Topics
Parent topic: Rotating Certificates
16.1.5 Checking the Certificate Rotation Status
You can use the Oracle Key Vault management console to check the status of a certificate rotation.
Parent topic: Rotating Certificates
16.2 Managing Console Certificates
You can use the Oracle Key Vault management console to manage console certificates.
- About Managing Console Certificates
Oracle Key Vault enables you to install a certificate signed by a Certificate Authority (CA) for more secure connections. - Step 1: Download the Certificate Request
When you request the console certificate, you can suppress warning messages. - Step 2: Have the Certificate Signed
After you download the Oracle Key Vaultcertificate.csrfile, you can have it signed. - Step 3: Upload the Signed Certificate to Oracle Key Vault
In addition to uploading the signed certificate, you can optionally choose to deactivate and re-activate the certificate. - Console Certificates in Special Use Case Scenarios
Depending on the situation, you must perform additional steps when you use console certificates.
Parent topic: Managing Certificates
16.2.1 About Managing Console Certificates
Oracle Key Vault enables you to install a certificate signed by a Certificate Authority (CA) for more secure connections.
You can upload upload a certificate that was signed by a third-party CA to Oracle Key Vault to prove its identity, encrypt the communication channel, and protect the data that is exchanged throughout the Oracle Key Vault system.
To install a console certificate, you must generate a certificate request, get it signed by a CA, and then upload the signed certificate back to Oracle Key Vault.
Parent topic: Managing Console Certificates
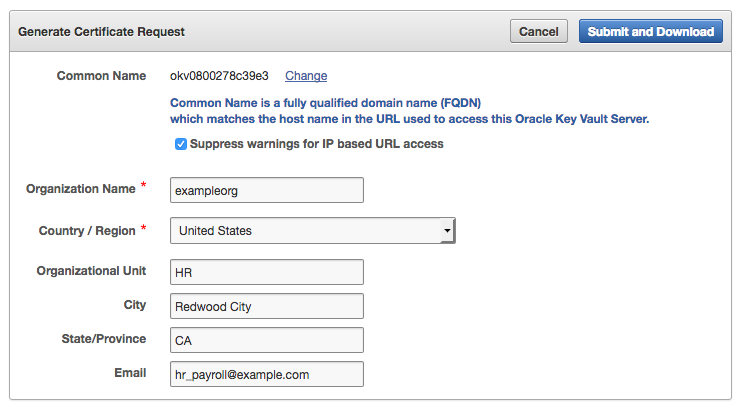
16.2.2 Step 1: Download the Certificate Request
When you request the console certificate, you can suppress warning messages.
Parent topic: Managing Console Certificates
16.2.3 Step 2: Have the Certificate Signed
After you download the Oracle Key Vault certificate.csr file, you can have it signed.
To have the certificate signed, you can use any out-of-band method to have it signed by a CA of your choice.
Afterward, you can then upload the signed certificate back to Oracle Key Vault using the management console.
Parent topic: Managing Console Certificates
16.2.4 Step 3: Upload the Signed Certificate to Oracle Key Vault
In addition to uploading the signed certificate, you can optionally choose to deactivate and re-activate the certificate.
Parent topic: Managing Console Certificates
16.2.5 Console Certificates in Special Use Case Scenarios
Depending on the situation, you must perform additional steps when you use console certificates.
-
Primary-standby environments: If you want to use a console certificate in a primary-standby configuration, then you must install it on the primary and standby servers first, and then pair them.
-
RESTful services: When you install a console certificate, you must download the RESTful software utility again before you can use the new certificate.
-
Restored data from a backup: If you install a console certificate, perform a backup, and then restore another Oracle Key Vault appliance from that backup, you must re-install the console certificate on the new server before you can use it. The restore process does not copy the console certificate.
Parent topic: Managing Console Certificates