14 Oracle Key Vault General System Administration
General system administration refers to system management tasks for the Oracle Key Vault system, such as configuring network details and services.
- Overview of Oracle Key Vault General System Administration
System administrators can perform most general administration tasks in the Oracle Key Vault management console, including finding the current status of the overall system. - Configuring Oracle Key Vault in a Non-Multi-Master Cluster Environment
On the system Settings page, you can configure the network settings. - Configuring Oracle Key Vault in a Multi-Master Cluster Environment
When you configure Oracle Key Vault in a multi-master cluster environment, you can configure either individual nodes or the entire multi-master cluster environment. - Managing System Recovery
System recovery includes tasks such as recovering lost administrative passwords. - Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a highly available configuration. - Managing Third-Party Certificates
You can use the Oracle Key Vault management console to manage third-party certificates. - Minimizing Downtime
Business-critical operations require data to be accessible and recoverable with minimum downtime.
14.1 Overview of Oracle Key Vault General System Administration
System administrators can perform most general administration tasks in the Oracle Key Vault management console, including finding the current status of the overall system.
- About Oracle Key Vault General System Administration
System administrators configure the Oracle Key Vault system settings. - Viewing the Oracle Key Vault Dashboard
The dashboard presents the current status of the Oracle Key Vault at a high level and is visible to all users. - Using the Status Panes in the Dashboard
The status panes on the dashboard provide useful high level information, such as links to alerts and an overview of current user activity.
Parent topic: Oracle Key Vault General System Administration
14.1.1 About Oracle Key Vault General System Administration
System administrators configure the Oracle Key Vault system settings.
The Oracle Key Vault system settings include administration, local and remote monitoring, email notification, backup and recovery operations, and auditing. You must have the appropriate role for performing these tasks. Users who have the System Administrator role can perform most of the administrative tasks, and users with the Audit Manager role can configure audit settings and export audit records. In most cases, you will perform these tasks in the Oracle Key Vault management console.
To quickly find information about the current status of the Oracle Key Vault system, you can view the Oracle Key Vault dashboard.
14.1.2 Viewing the Oracle Key Vault Dashboard
The dashboard presents the current status of the Oracle Key Vault at a high level and is visible to all users.
The Home tab of the management console displays the dashboard when you log into the management console.
Alerts and Managed Content are the first sections you will see on logging in.
Figure 14-1 Alerts and Managed Content Panes
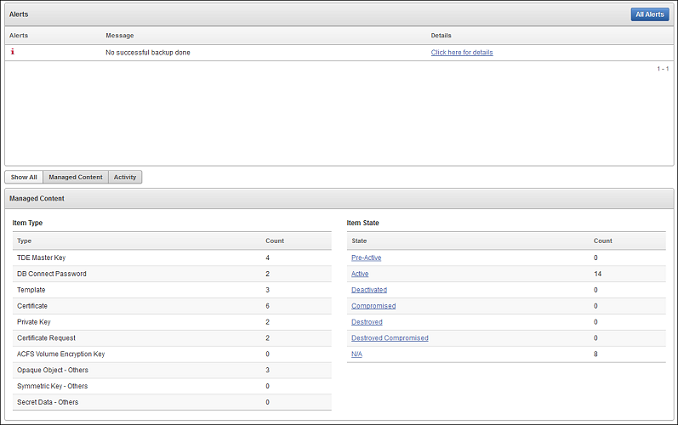
Description of "Figure 14-1 Alerts and Managed Content Panes"
The Data Interval, Operations, Endpoint Activity, and User Activity panes of the Home page follow Alerts and Managed Content.
Figure 14-2 Data Interval, Operations, Endpoint Activity, and User Activity Panes
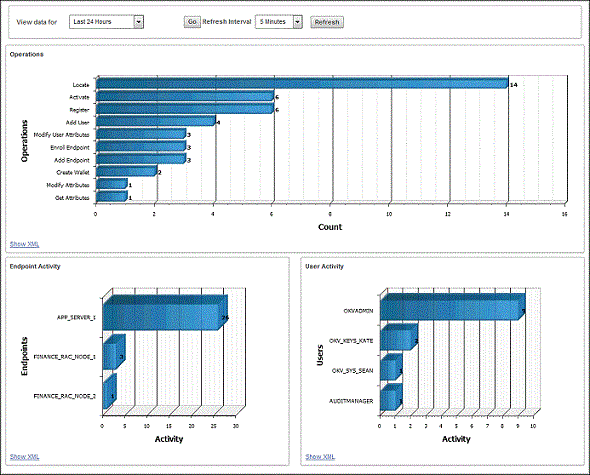
Description of "Figure 14-2 Data Interval, Operations, Endpoint Activity, and User Activity Panes"
14.2 Configuring Oracle Key Vault in a Non-Multi-Master Cluster Environment
On the system Settings page, you can configure the network settings.
Parent topic: Oracle Key Vault General System Administration
14.3 Configuring Oracle Key Vault in a Multi-Master Cluster Environment
When you configure Oracle Key Vault in a multi-master cluster environment, you can configure either individual nodes or the entire multi-master cluster environment.
- Configuring System Settings for Individual Multi-Master Cluster Nodes
You can set or change settings that apply to the cluster node. - Managing Oracle Key Vault Multi-Master Clusters
You can create, configure, manage, and administer an Oracle Key Vault multi-master cluster by using the Oracle Key Vault management console.
Parent topic: Oracle Key Vault General System Administration
14.3.1 Configuring System Settings for Individual Multi-Master Cluster Nodes
You can set or change settings that apply to the cluster node.
Examples of these settings are the network details, network services, system time, DNS, FIPS mode, syslog, and Oracle Audit Vault integration. Values set for the node override the cluster setting. However, you can clear any individual node setting to revert to the cluster setting.
- Configuring the Network Details for the Node
In a multi-master cluster, you can configure the network details from any Oracle Key Vault management console. - Configuring the Network Services for the Node
In a multi-master cluster, you can configure the network services from any Oracle Key Vault management console. - Configuring the System Time for the Node
You can set and clear the time for individual nodes. - Configuring DNS for the Node
You can set and clear the DNS for individual nodes. - Setting the FIPS Mode for the Node
All multi-master cluster nodes must use the same FIPS mode setting or you will receive an alert.
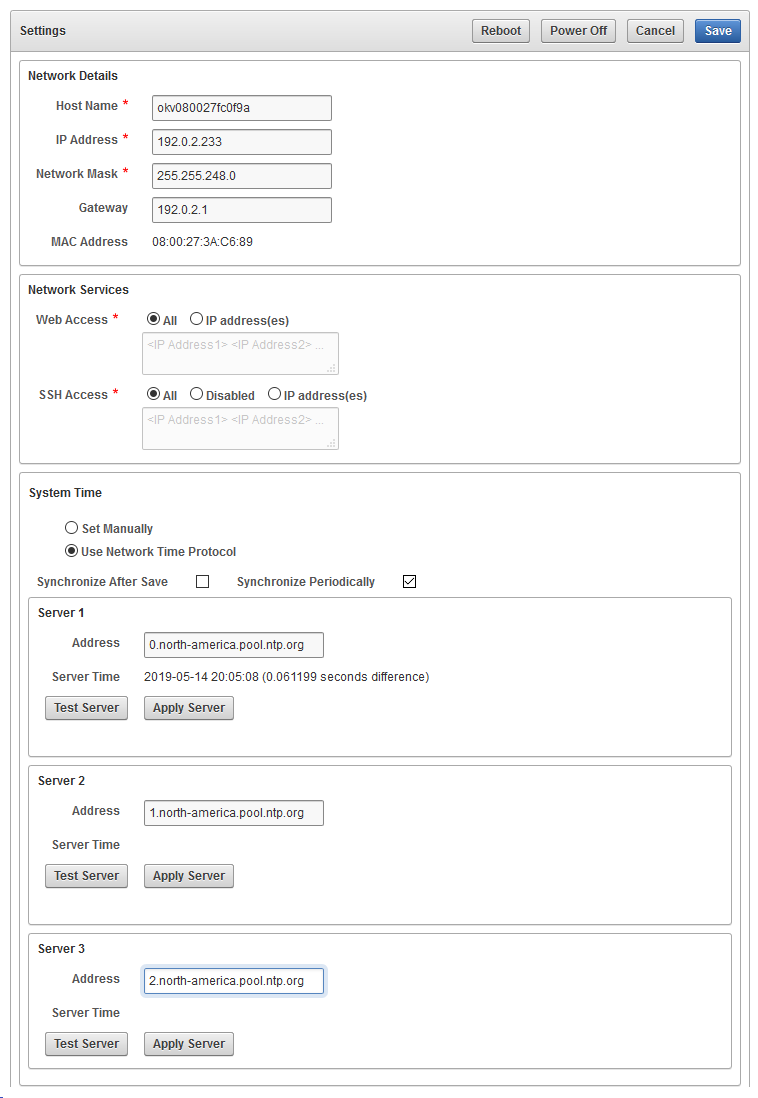
14.3.1.1 Configuring the Network Details for the Node
In a multi-master cluster, you can configure the network details from any Oracle Key Vault management console.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then System Settings from the left navigation bar.
- Update the values for the following fields:
- Host Name: Enter the name of the node.
- IP Address: Enter the IP address of the node. Note that this value cannot be changed after it is saved.
- Network Mask: Enter the network mask of the node.
- Gateway: Enter the network gateway of the node.
- Click Save.
14.3.1.2 Configuring the Network Services for the Node
In a multi-master cluster, you can configure the network services from any Oracle Key Vault management console.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then System Settings from the left navigation bar.
- For Web Access, select one of the following options:
- All: Allows all IP addresses to access the management console of this node.
- IP Address(es): Restricts management console access to the space separated list of IP addresses entered in the address box.
- Click Save.
14.3.1.3 Configuring the System Time for the Node
You can set and clear the time for individual nodes.
- Setting the System Time for the Node
In a multi-master cluster, you can set the system time for a node. - Clearing the System Time for the Node
In a multi-master cluster, you can clear the time setting for the node and reset it to use the cluster time setting.
14.3.1.3.1 Setting the System Time for the Node
In a multi-master cluster, you can set the system time for a node.
Related Topics
Parent topic: Configuring the System Time for the Node
14.3.1.3.2 Clearing the System Time for the Node
In a multi-master cluster, you can clear the time setting for the node and reset it to use the cluster time setting.
Parent topic: Configuring the System Time for the Node
14.3.1.4 Configuring DNS for the Node
You can set and clear the DNS for individual nodes.
- Setting DNS for the Node
When you configure the DNS for a multi-master cluster node, you should enter more than one DNS IP address. - Clearing DNS for the Node
In a multi-master cluster, you can clear DNS for the node, which resets it to the use the cluster DNS.
14.3.1.4.1 Setting DNS for the Node
When you configure the DNS for a multi-master cluster node, you should enter more than one DNS IP address.
Parent topic: Configuring DNS for the Node
14.3.1.4.2 Clearing DNS for the Node
In a multi-master cluster, you can clear DNS for the node, which resets it to the use the cluster DNS.
Parent topic: Configuring DNS for the Node
14.3.2 Managing Oracle Key Vault Multi-Master Clusters
You can create, configure, manage, and administer an Oracle Key Vault multi-master cluster by using the Oracle Key Vault management console.
- About Configuring Cluster System Settings
You can set or change settings that apply to an entire multi-master cluster. - Configuring the System Time for the Cluster
When you configure the system time, you can set it for multiple servers and also set the synchronization. - Configuring DNS for the Cluster
When you configure the DNS for a cluster, you can enter up to three DNS server IP addresses. - Configuring Maximum Disable Node Duration for the Cluster
You can set the Configuring Maximum Node Duration time for the cluster in hours. - Configuring RESTful Services for the Cluster
You can enable or disable RESTful Services for the cluster. - Configuring Syslog for the Cluster
You can enable syslog for either the Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) for the cluster. - Configuring SNMP Settings for the Cluster
You can enable or disable SNMP access for a multi-master cluster.
14.3.2.1 About Configuring Cluster System Settings
You can set or change settings that apply to an entire multi-master cluster.
You can set the system time, DNS, the maximum time a server can be disabled before it is evicted from the cluster, enable RESTful services, the protocol to use for syslog, the syslog destination, and monitoring settings for the cluster. Any values that are set and saved to an individual node will not be overridden by cluster settings. It may take several minutes for changes to propagate to other nodes.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.2 Configuring the System Time for the Cluster
When you configure the system time, you can set it for multiple servers and also set the synchronization.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.3 Configuring DNS for the Cluster
When you configure the DNS for a cluster, you can enter up to three DNS server IP addresses.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then Cluster System Settings from the left navigation bar.
- In the DNS section of the Cluster System Settings page, enter up to three DNS Server IP addresses.
- In the DNS section, click Save to Cluster.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.4 Configuring Maximum Disable Node Duration for the Cluster
You can set the Configuring Maximum Node Duration time for the cluster in hours.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then Cluster System Settings from the left navigation bar.
- In the Maximum Disable Node Duration section, enter a value, in hours, for the duration that a node can be disabled before it is evicted from the cluster.
- In the Maximum Disable Node Duration section, click Save to Cluster.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.5 Configuring RESTful Services for the Cluster
You can enable or disable RESTful Services for the cluster.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then Cluster System Settings from the left navigation bar.
- Select the Enable checkbox in the RESTful Services section.
- In the RESTful Services section, click Save to Cluster.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.6 Configuring Syslog for the Cluster
You can enable syslog for either the Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) for the cluster.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.3.2.7 Configuring SNMP Settings for the Cluster
You can enable or disable SNMP access for a multi-master cluster.
- Log into any Oracle Key Vault management console as a user who has the System Administrator role.
- Select the System tab, and then Monitoring Settings from the left navigation bar.
- For Scope, select Cluster.
- Select who has SNMP access to the multi-master cluster by choosing one of the options:
- All: Allows SNMP access from all IP addresses.
- Disabled: Allows no SNMP access.
- IP address(es): Allows SNMP access from the list of IP addresses supplied in the address box. Enter a space-separated list of IP addresses.
- Enter values for the following fields:
- Username: Enter the SNMP user name.
- Password: Enter the SNMP password.
- Reenter Password: Enter the SNMP password again.
- Click Save to Cluster.
Parent topic: Managing Oracle Key Vault Multi-Master Clusters
14.4 Managing System Recovery
System recovery includes tasks such as recovering lost administrative passwords.
- About Managing System Recovery
To perform system recovery, you use the recovery passphrase. - Recovering Credentials for Administrators
You can recover the system by adding credentials for administrative users. - Changing the Recovery Passphrase in a Non-Clusters Environment
Periodically changing the recovery passphrase is a good security practice. - Changing the Recovery Passphrase in a Multi-Master Cluster
Changing the recovery passphrase in a multi-master cluster is a two-step process. - Changing the Installation Passphrase
You can change the installation passphrase from the system console.
Parent topic: Oracle Key Vault General System Administration
14.4.1 About Managing System Recovery
To perform system recovery, you use the recovery passphrase.
In an emergency when no administrative users are available, or you must change the password of administrative users, you can recover the system with the recovery passphrase that was created during Oracle Key Vault installation. In addition, you can change the recovery passphrase to keep up with security best practices.
Parent topic: Managing System Recovery
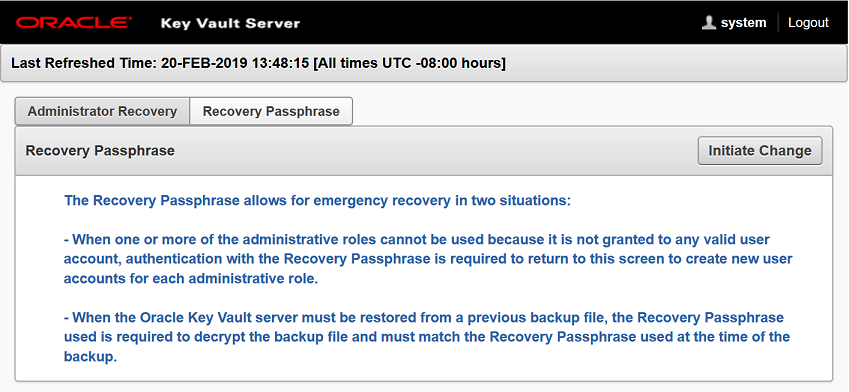
14.4.2 Recovering Credentials for Administrators
You can recover the system by adding credentials for administrative users.
Related Topics
Parent topic: Managing System Recovery
14.4.3 Changing the Recovery Passphrase in a Non-Clusters Environment
Periodically changing the recovery passphrase is a good security practice.
Related Topics
Parent topic: Managing System Recovery
14.4.4 Changing the Recovery Passphrase in a Multi-Master Cluster
Changing the recovery passphrase in a multi-master cluster is a two-step process.
To change the recovery passphrase for a multi-master cluster, you must first initiate the change throughout the nodes in the multi-master cluster environment before changing the recovery passphrase.
- Step 1: Initiate the Recovery Passphrase Change Across the Nodes
A user with the System Administrator role should perform a new backup whenever the recovery passphrase changes. - Step 2: Change the Recovery Passphrase
After the multi-master cluster nodes have been notified of the impending recovery passphrase change, you can change the recovery passphrase.
Parent topic: Managing System Recovery
14.4.4.1 Step 1: Initiate the Recovery Passphrase Change Across the Nodes
A user with the System Administrator role should perform a new backup whenever the recovery passphrase changes.
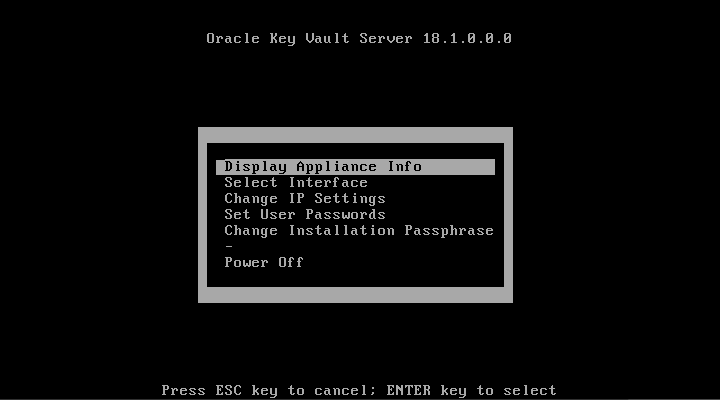
14.4.5 Changing the Installation Passphrase
You can change the installation passphrase from the system console.
- About Changing the Installation Passphrase
You can only change the installation passphrase during a specific window of time. - Changing an Installation Passphrase
You must change the installation passphrase in the system console.
Parent topic: Managing System Recovery
14.4.5.1 About Changing the Installation Passphrase
You can only change the installation passphrase during a specific window of time.
The installation passphrase is specified during installation. You must use the installation passphrase to log in to Oracle Key Vault and complete the post-installation tasks. The installation passphrase can only be changed on the console after installation but before post-installation. After the post-installation tasks are completed, this option no longer appears on the console.
If you forget the installation passphrase, then you can create a new installation passphrase. As with all Oracle Key Vault passphrases, it is important to store the installation passphrase securely.
Parent topic: Changing the Installation Passphrase
14.4.5.2 Changing an Installation Passphrase
You must change the installation passphrase in the system console.
Parent topic: Changing the Installation Passphrase
14.5 Support for a Primary-Standby Environment
To ensure that Oracle Key Vault can always access security objects, you can deploy Oracle Key Vault in a highly available configuration.
This configuration also supports disaster recovery scenarios.
You can deploy two Oracle Key Vault servers in a primary-standby configuration. The primary server services the requests that come from endpoints. If the primary server fails, then the standby server takes over after a configurable preset delay. This configurable delay ensures that the standby server does not take over prematurely in case of short communication gaps.
The primary-standby configuration was previously known as the high availability configuration. The primary-standby configuration and the multi-master cluster configuration are mutually exclusive.
Oracle Key Vault supports primary-standby read-only restricted mode. When the primary server is affected by server, hardware, or network failures, primary-standby read-only restricted mode ensures that an Oracle Key Vault server is available to service endpoints, thus ensuring operational continuity. However, key and sensitive operations, such as generation of keys are disabled, while operations such as generation of audit logs are unaffected.
When an unplanned shutdown makes the standby server unreachable, the primary server is still available to the endpoints in read-only mode.
Related Topics
Parent topic: Oracle Key Vault General System Administration
14.6 Managing Third-Party Certificates
You can use the Oracle Key Vault management console to manage third-party certificates.
- About Managing Third-Party Certificates
Oracle Key Vault enables you to install a certificate signed by a third-party Certificate Authority (CA) for more secure connections. - Step 1: Download the Certificate Request
When you request the certificate, you can suppress warning messages. - Step 2: Have the Certificate Signed
After you download the Oracle Key Vaultcertificate.csrfile, you can have it signed. - Step 3: Upload the Signed Certificate to Oracle Key Vault
In addition to uploading the signed certificate, you can optionally choose to deactivate and re-activate the certificate. - Third-Party Certificates in Special Use Case Scenarios
Depending on the situation, you must perform additional steps when you use third-party certificates.
Parent topic: Oracle Key Vault General System Administration
14.6.1 About Managing Third-Party Certificates
Oracle Key Vault enables you to install a certificate signed by a third-party Certificate Authority (CA) for more secure connections.
You can upload upload a certificate that was signed by a third-party CA to Oracle Key Vault to prove its identity, encrypt the communication channel, and protect the data that is exchanged throughout the Oracle Key Vault system.
To install a third-party certificate, you must generate a certificate request, get it signed by a CA, and then upload the signed certificate back to Oracle Key Vault.
Parent topic: Managing Third-Party Certificates
14.6.2 Step 1: Download the Certificate Request
When you request the certificate, you can suppress warning messages.
Parent topic: Managing Third-Party Certificates
14.6.3 Step 2: Have the Certificate Signed
After you download the Oracle Key Vault certificate.csr file, you can have it signed.
To have the certificate signed, you can use any out-of-band method to have it signed by a CA of your choice.
Afterward, you can then upload the signed certificate back to Oracle Key Vault using the management console.
Parent topic: Managing Third-Party Certificates
14.6.4 Step 3: Upload the Signed Certificate to Oracle Key Vault
In addition to uploading the signed certificate, you can optionally choose to deactivate and re-activate the certificate.
Parent topic: Managing Third-Party Certificates
14.6.5 Third-Party Certificates in Special Use Case Scenarios
Depending on the situation, you must perform additional steps when you use third-party certificates.
-
Primary-standby environments: If you want to use a third-party certificate in a primary-standby configuration, then you must install it on the primary and standby servers first, and then pair them.
-
RESTful services: When you install a third-party certificate, you must download the RESTful software utility again before you can use the new certificate.
-
Restored data from a backup: If you install a third-party certificate, perform a backup, and then restore another Oracle Key Vault appliance from that backup, you must re-install the third-party certificate on the new server before you can use it. The restore process does not copy the third-party certificate.
Parent topic: Managing Third-Party Certificates
14.7 Minimizing Downtime
Business-critical operations require data to be accessible and recoverable with minimum downtime.
You can configure Oracle Key Vault to ensure minimum downtime in the following ways:
-
Configuring a multi-master cluster: You can configure a multi-master cluster by adding redundancy in the form of additional nodes. The client can access any available node. In the event of a failure of any node, a client will automatically connect to another node in the endpoint node scan list. This reduces and potentially eliminates downtime.
-
Configuring a primary-standby environment: A primary-standby environment is configured by adding redundancy in the form of a standby server. The standby server takes over from the primary server in the event of a failure, thus eliminating single points of failure, and minimizing downtime.
-
Enabling read-only restricted mode: Primary-standby read-only restricted mode ensures endpoint operational continuity when primary or standby Oracle Key Vault servers are affected by server, hardware, or network failures. When an unplanned shutdown causes the standby server to become unreachable, the primary server is still available to the endpoints.
If primary-standby read-only restricted mode is disabled, then the primary server will become unavailable and stop accepting requests in the event of a standby failure. Endpoints connected to Oracle Key Vault are unable to retrieve keys until connectivity is restored between primary and standby servers.
To ensure endpoint operational continuity in the event of a primary or standby server failure, enable read-only restricted mode.
-
Enabling persistent master encryption key cache: The persistent master encryption key cache ensures that the endpoints can access keys in the event of a primary or standby server failure. While the surviving server is taking over from the failed peer, the endpoints can retrieve keys from the persistent cache and continue operations normally.
-
Apply the TDE heartbeat database patch on endpoints: Apply the database patch for Bug 22734547 to tune the Oracle Key Vault heartbeat.
Oracle strongly recommends that you back up Oracle Key Vault data regularly on a schedule. This practice ensures that backups are current and hold the most recent data. You can use this backup to restore a new or existing Oracle Key Vault server and enable it to be fully operational with minimum downtime and data loss.
If the Oracle Key Vault installation uses an online master key (formerly known as TDE direct connect), then during an upgrade, ensure that you upgrade database endpoints in parallel to reduce total downtime.
Related Topics
Parent topic: Oracle Key Vault General System Administration