OAuth 2.0 for Integration Applications Developers
SuiteProjects Pro supports two methods to access SuiteProjects Pro data using XML API or SOAP API requests:
-
Using user credentials (Company ID, User ID, password) and, in the case of SOAP web services (SOAP API), a session ID.
-
Using OAuth 2.0 access tokens.
OAuth 2.0 bearer token authentication is the only supported method to access SuiteProjects Pro data using the REST API.
In the OAuth 2.0 scenario, client applications use one of the OAuth 2.0 grant types to get an access token after the user authorizes the application. The user's identity is verified by an authentication service, which issues the access token. The access token can then be used to gain authenticated access to SuiteProjects Pro through the XMl API, SOAP API or REST API.
This section describes how to get an access token using the OAuth 2.0 authorization code grant type in your applications, and how to use the access token in your API calls.
SuiteProjects Pro only supports the OAuth 2.0 authorization code grant type, which defines a particular workflow client applications can use to obtain the access token.
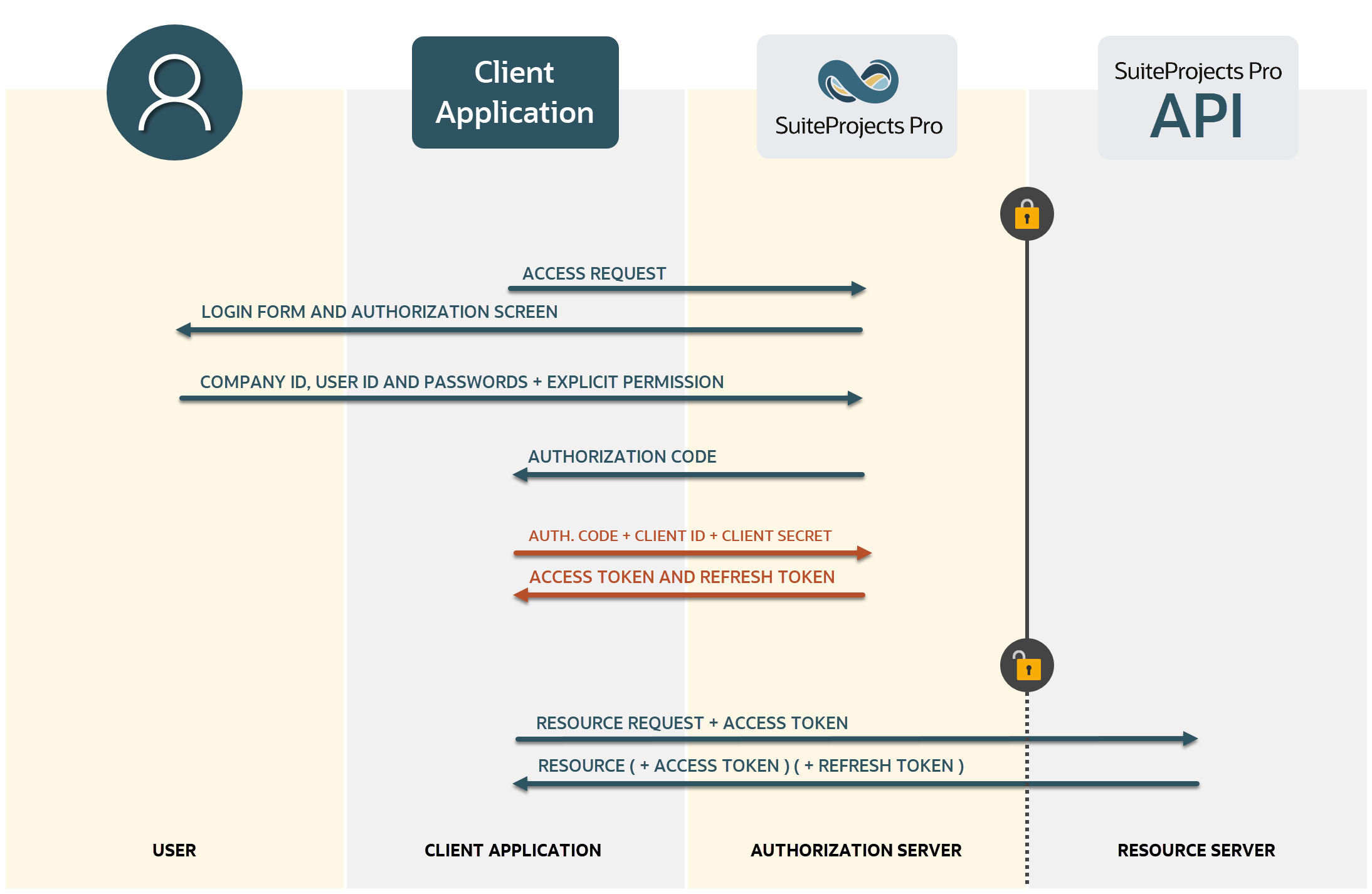
OAuth 2.0 Authorization Code Flow
Application developers can use the OAuth 2.0 redirection-based authorization code grant type to obtain an access token. This method eliminates the need for client applications to collect and store user credentials.
The authorization code flow includes the following steps:
-
Getting the user's explicit permission to access SuiteProjects Pro on their behalf. See Getting the User's Permission.
-
The client application opens a browser and directs the user to the SuiteProjects Pro identity authentication service with the necessary URL query string parameters.
-
The user enters user credentials in the SuiteProjects Pro sign-in page or in a third-party identity provider Single Sign-on form . The authenticated user is then prompted to authorize the application's access request.
-
-
Receiving the authorization code - SuiteProjects Pro issues an authorization code. The user is redirected back to the client application with the authorization code in the query string. See Receiving the Authorization Code.
-
Exchanging the authorization code for an access token - The client application must exchange the authorization code for an access token and a refresh token. See Exchanging the Authorization Code for an Access Token.
An additional step - Refreshing an access token - is required to get a new access token after the previously issued access token has expired. See Refreshing an Access Token.
You must send a request to one of the OAuth 2.0 endpoints for each of these steps. For information about OAuth 2.0 URLs, see OAuth 2.0 Endpoints URL Schema and Account-Specific URLs.
You can then use OAuth 2.0 token based authentication for your API calls. See Using OAuth 2.0 Access Tokens in Your API Requests.
OAuth 2.0 Endpoints URL Schema and Account-Specific URLs
For each step of the OAuth 2.0 authorization code flow, you must send requests to the authorization server using URLs specific to each type of request.
The following URL shows how you construct a request URL:
https://<account-domain>/login/oauth2/v1/<endpoint><query-string>
-
The first part of the URL must include your account-specific domain
<account-domain>and the service path for OAuth 2.0. For more information about your account-specific domain name, see Your Account URLs. -
The second part of the URL depends on the endpoint you want to access
<endpoint>Description
authorizeUse the authorization endpoint to get the user's explicit permission and receive an authorization code in response if the user authorizes the app to access SuiteProjects Pro on their behalf. The request URL includes a query string with request parameter.
https://<account-domain>/login/oauth2/v1/authorize?<query-string>See Getting the User's Permission and Receiving the Authorization Code.
tokenUse the token endpoint to exchange the authorization code for an access token or to refresh an access token. Request parameters are passed in the request headers and body.
https://<account-domain>/login/oauth2/v1/tokenSee Exchanging the Authorization Code for an Access Token and Refreshing an Access Token.
Getting the User's Permission
To begin the OAuth 2.0 authorization code flow, the client application must direct the user to the authorization server - SuiteProjects Pro - using a GET request.
Send a GET request to the authorization endpoint using a URL like the following example:
https://company-id.app.netsuitesuiteprojectspro.com/login/oauth2/v1/authorize?response_type=code&redirect_uri=https://example-app.com/redirect&client_id=client_application_id&scope=xml+soap+rest&state=client_generated_string
Replace the account domain and parameter values https://example-app.com/redirect, client_application_id and client_generated_string given in the example using the following guidelines.
The GET request URL includes the authorization endpoint for the SuiteProjects Pro account followed by a query string:
https://<account-domain>/login/oauth2/v1/authorize?<query-string>
where <account-domain> is your account-specific domain name. For more information, see Your Account URLs.
The request parameters are described in the following table.
|
Request parameter |
Description |
|---|---|
|
|
The value of the |
|
|
The valid redirect URI where the application will process the authorization code. The user should be redirected to this URI after allowing or denying the access request. The redirect URI must match the redirect URI specified on the application configuration form in SuiteProjects Pro. See Adding a New Application. |
|
|
The public identifier for the client application. The Client ID is generated by SuiteProjects Pro when an administrator registers the client application. See Adding a New Application. |
|
|
One or more plus-separated scope values indicating the access requested by the application. The scope determines which component API and which resources the application will be able to access.
|
|
|
A random string generated by the client application, which is used to prevent cross-site request forgery (CSRF) attacks. For more information see the OAuth 2.0 specification RFC6749 Section 10.12. |
After the application sends the GET request, SuiteProjects Pro redirects the user to the SuiteProjects Pro sign-in page. SuiteProjects Pro may redirect the user to a third-party Identity provider Single Sign-on form, if SAML SSO is enabled for the account and the user. After successful authentication, SuiteProjects Pro shows an authorization page prompting the user to approve the application's access request.
Receiving the Authorization Code
After obtaining the user's explicit permission, SuiteProjects Pro initiates a redirect to the redirect URI specified in the GET request with the authorization code and the state as query parameters.
The redirect query parameters are described in the following table.
|
Redirect parameter |
Description |
|---|---|
|
|
The client application should check that the state in the redirect matches the state set in the GET request initiating the OAuth 2.0 authorization code flow. Validating the state sent to and returned from the authorization server can be used to prevent cross-site request forgery (CSRF) attacks. |
|
|
The authorization code issued by SuiteProjects Pro.
|
The following sample redirects illustrate successful and unsuccessful authorization.
-
Application successfully authorized.
https://example-app.com/redirect?state=client_generated_string&code=OAuth2_authorization_code -
Application not authorized.
https://example-app.com/redirect?error_description=The+resource+owner+or+authorization+server+denied+the+request&error=access_denied&state=client_generated_string
where:
-
client_generated_stringis the same string that was sent in the request using thestateparameter. -
OAuth2_authorization_codeis the OAuth 2.0 authorization code obtained for a specific client application and a specific user.
Exchanging the Authorization Code for an Access Token
The application can use the authorization code to obtain an access token and a refresh token using a POST request.
Send a POST request to the token endpoint.
-
The POST request URL is
https://<account-domain>/login/oauth2/v1/token -
The request must include the client ID and the client secret in the HTTP authorization request header.
-
The client authentication method used in a header of the request follows the HTTP Basic authentication scheme. For more information, see RFC 7617.
-
The format is
client_id:clientsecret. -
The string value is Base64 encoded.
-
-
The request must include the parameters
grant_type,codeandredirect_uriin the request body. -
Request parameters must be encoded based on the HTML specification for
application/x-www-form-urlencodedmedia type. For more information, see URL Specification 5.1.
The request parameters are described in the following table.
|
Request parameter |
Description |
|---|---|
|
|
The value of the |
|
|
The authorization code issued by SuiteProjects Pro and received by the client application in the redirect. |
|
|
The valid redirect URI. The redirect URI must match the redirect URI specified on the application configuration form in SuiteProjects Pro and when requesting the authorization code. |
|
|
The public identifier for the client application. The Client ID is generated by SuiteProjects Pro when an administrator registers the client application. |
|
|
The client secret for the application. This ensures that the request to get the access token is made only from the application, and not from a potential attacker that may have intercepted the authorization code. |
Example POST request:
POST /login/oauth2/v1/token HTTP/1.1
Host: company-id.app.netsuitesuiteprojectspro.com
Authorization: Basic base_64_encoded_client_id:client_secret
Content-Type: application/x-www-form-urlencoded
code=OAuth2_authorization_code&redirect_uri=https%3A%2F%2Fexample-app.com%2Fredirect&grant_type=authorization_code
Replace the following values in the example:
-
base_64_encoded_client_id:client_secretwith the base 64 encoded string required to authenticate the request, which includes the client ID and client secret. -
OAuth2_authorization_codewith the OAuth 2.0 authorization code obtained for a specific client application and a specific user. -
https%3A%2F%2Fexample-app.com%2Fredirectwith the URL-encoded redirect URI for the client application.
The token endpoint will verify all the parameters in the request to ensure that the authorization code is valid and that the client ID and client secret match. If all the request headers and parameters are valid, the token endpoint generates an access token and refresh token and includes them in the response.
The token endpoint returns the response as a JSON object with the properties described in the following table.
|
JSON object properties |
Description |
|---|---|
|
|
The access token in JSON Web Token (JWT) format. The access token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The refresh token in JSON JWT format. The refresh token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The access token expiration time in seconds. The access token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The value of the |
Example response (successful token request):
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"refresh_token":"OAuth2_refresh_token",
"expires_in":900,
"access_token":"OAuth2_access_token",
"token_type":"bearer"
}
In the example, OAuth2_access_token is the OAuth 2.0 access token obtained for the client application that is used to authenticate API requests, and OAuth2_refresh_token is the OAuth 2.0 refresh token obtained for the client application that is used to request a new access token when it expires.
If the request fails, the token endpoint returns a JSON object with the error and error_description properties. See Token Request Errors.
The client application can now use the access token to make API requests. This completes the authorization flow.
The access token is only valid for a short period of time and within the scope it was issued for. The client application will need to refresh the access token to continue making API requests after it expires.
When using an OAuth 2.0 access token to authenticate API requests, the API uses cached filter set information -information about objects which the authenticated user can access according to the filter set assigned to that user- to optimize performance. By default, read requests using a valid access token do not include objects created after the access token was issued, even if the user can access the new objects in the UI. If new objects are expected, you can clear and regenerate the cached filter set information:
-
For XML API or SOAP API read requests, using the
clear_filter_cacheattribute. See Read Attributes. -
For REST API requests, by sending a POST request to the filter set cache refresh endpoint. Subsequent GET requests to resource endpoints return the latest available data including any objects that were created recently. See Filter Set Cache Refresh.
Refreshing an Access Token
The access token has a short expiration time (15 minutes). When the access token expires, the client application can use the refresh token to obtain a new access token using a POST request.
-
You can use the expiration time value (
expires_in) to refresh access tokens before it is due to expire. -
You can refresh access tokens if an API request returns an authentication failed error.
-
Each refresh token can be used one time only. Refresh in an access token generates a new access token and a new refresh token.
Send a POST request to the SuiteProjects Pro token endpoint. The POST request is similar to that used to exchange an authorization code for an access token except it now uses the parameters set in the following table.
|
Request parameter |
Description |
|---|---|
|
|
The value of the |
|
|
A valid refresh_token. Refresh tokens are valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
(Optional) The requested scope must be within the scope the original access token was issued for. If omitted, the new access token will be issued for the same scope as the original access token.
Note:
The |
|
|
The valid redirect URI. |
|
|
The public identifier for the client application. |
|
|
The client secret for the application. |
Example POST request:
POST /login/oauth2/v1/token HTTP/1.1
Host: company-id.app.netsuitesuiteprojectspro.com
Authorization: Basic base_64_encoded_client_id:client_secret
Content-Type: application/x-www-form-urlencoded
refresh_token=OAuth2_refresh_tokenredirect_uri=https%3A%2F%2Fexample-app.com%2Fredirect&grant_type=refresh_token
Replace the following values in the example:
-
base_64_encoded_client_id:client_secretwith the base 64 encoded string required to authenticate the request, which includes the client ID and client secret. -
OAuth2_refresh_tokenwith the OAuth 2.0 refresh token obtained for the client application. -
https%3A%2F%2Fexample-app.com%2Fredirectwith the URL-encoded redirect URI for the client application.
The token endpoint will verify all the parameters in the request to ensure that the refresh token is valid and that the client ID and client secret match. If all the request headers and parameters are valid, the token endpoint generates an access token and refresh token and includes them in the response.
The token endpoint returns the response as a JSON object with the properties described in the following table. The response includes both a new access token and a new refresh token.
|
JSON object properties |
Description |
|---|---|
|
|
The access token in JSON Web Token (JWT) format. The access token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The refresh token in JSON JWT format. The refresh token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The access token expiration time in seconds. The access token is valid for the period configured in SuiteProjects Pro for the application. See Application Configuration. |
|
|
The value of the |
Access tokens normally remain valid for their entire lifetime. However, the access token becomes invalid before it is due to expire if there are any changes in the SuiteProjects Pro configuration, or in the access privileges or role permissions of the employee who authorized the client application, and the application uses the access token is refreshed.
Example response (successful token request):
HTTP/1.1 200 OK
Content-Type: application/json
Cache-Control: no-store
Pragma: no-cache
{
"refresh_token":"OAuth2_refresh_token",
"expires_in":900,
"access_token":"OAuth2_access_token",
"token_type":"bearer"
}
In the example, OAuth2_access_token and OAuth2_refresh_token are the new OAuth 2.0 access token and the new OAuth 2.0 refresh token obtained for the client application.
If the request fails, the token endpoint returns a JSON object with the error and error_description properties. See Token Request Errors.
Token Request Errors
Your client application needs to handle the following cases when the request to exchange an authorization code for an access token or to refresh a token fails. The token endpoint may return one of the errors listed in the following table if the token request fails.
-
Errors are listed in descending priority order. Only the first error is returned if there are more than one.
-
Some of the errors are specific to one of the two possible types of request (
grant_type).
|
|
|
|
Reason |
|---|---|---|---|
|
unsupported_grant_type |
The authorization grant type is not supported by the authorization server |
- |
The |
|
invalid_request |
Authorization header not sent |
- |
Request headers must include a Basic Authorization header. |
|
invalid_request |
No credentials provided |
- |
The Client Id and Client Secret must be sent in the request Authorization header. |
|
access_denied |
Authorization code is not valid |
|
The authorization code must be valid. Possible reasons include:
|
|
invalid_request |
redirect_uri or client_id is not valid |
|
The redirect URI and Client ID must match the information specified on the application configuration form in SuiteProjects Pro. |
|
access_denied |
Refresh token is not valid |
|
The refresh token sent in the request is not valid. Possible reasons include:
|
|
invalid_scope |
Changing scopes is not supported |
|
Tokens are issued for a specific |
|
access_denied |
Authorization failed |
- |
The Client Id and Client Secret pair sent in the request is not valid. Note that account administrators may generate a new Client Secret for the application in SuiteProjects Pro. |
|
access_denied |
API access via OAuth2 is disabled |
- |
API access is not enabled for the SuiteProjects Pro account and the |
|
access_denied |
REST API access disabled |
- |
REST API is not enabled for the SuiteProjects Pro account and the |
|
access_denied |
BI Connector access disabled |
- |
The BI Connector feature is not enabled for the SuiteProjects Pro account and the |
If applicable, the client application can initiate the OAuth 2.0 authorization code flow again to obtain a new authorization code and exchange it for an access token. The user is directed to the sign-in page and required to enter valid user credentials. If the user revoked the application the authorization page will appear. If the application is still authorized, the authorization endpoint will return a new authorization code immediately after the successful user authentication.
Using OAuth 2.0 Access Tokens in Your API Requests
You can use OAuth 2.0 access token authorization instead of password authentication or Session ID in your API requests. The XML API, SOAP API and REST API support authorization using access tokens. OAuth 2.0 access token authorization is the only supported authentication method with the REST API.
-
In your XML API requests, use the
AuthXML command. See OAuth 2.0 Access Token Authentication. -
In your SOAP API requests, use the
SessionHeaderweb services method complex type to hold the access token. See Using SessionHeader for OAuth2.0 Token Based Authentication. -
In your REST API requests, send the access token as a bearer token in the HTTP authorization header. See Authentication.
Note:For REST API requests, the access token lifetime will either be the Access token lifetime set on the application configuration form in SuiteProjects Pro, or the Session timeout set in Administration > Global settings > Account > Security options, whichever is the lower.
Both the XML API and SOAP API continue to support password authentication. The SOAP API continues to support SessionID.
Authorization Errors
The relevant licensed add-on features must be enabled in your account:
-
API access must be enabled except if you are using the REST API to access supported Business Intelligence (BI) Connector resources.
-
The BI Connector feature must be enabled if you are using the REST API to access supported Business Intelligence (BI) Connector resources. The REST API returns HTTP status
404 Not foundwith error messagePage not foundorReport not foundif you attempt to access a BI Connector resource endpoint with a valid access token and the BI Connector feature is disabled.
API requests must use a valid access token with a valid scope.
-
The access token must exist.
-
The access token must not be expired.
-
The user who gave the application permission to access SuiteProjects Pro must be active. The same access token can be used if the user is set to active again.
-
The application must be enabled in the SuiteProjects Pro account. The same access token can be used if the application is disabled and then enabled again.
-
The access token must be used within the scope it was issued for. For example, if the authorization code was obtained for the scope
xml+rest, the client application cannot use the access token in a SOAP API request.
The error code and message returned depend on the API:
-
The XML API returns error code
420and messageAuthentication failed. -
The SOAP API returns error code
9and messageLogged out. -
The REST API returns HTTP status
401 Unauthorizedand the response includes aWWW-Authenticateheadererror="invalid_token", error_description="The access token is invalid".
An invalid OAuth 2.0 access token authorization has priority over a valid password authentication. You cannot use password authentication (Company ID, User ID, password) - or a valid Session ID in the SOAP session header - as a fallback for an invalid access token.