Manage Target Databases
As your target databases and their environments evolve, you may need to perform various life-cycle management activities.
View Registration Details for a Target Database
You can view registration details from the Target database details page in the Oracle Data Safe service in Oracle Cloud Infrastructure.
Update Connection Details for a Target Database
From the Target database details page, you can update connection details for a target database. The connection details vary depending on the database type; for example, TCP/TLS, database service name, database port number, and so on.
For example, for some target databases you can change the Oracle Data Safe private endpoint or Oracle Data Safe on-premises connector configuration for a target database.
Update a Target Database Name and Description
You can update the name and description for your target database.
Update the Database User
You can use the Update database user feature on the Target database information page to update the user credentials on your target database that Oracle Data Safe requires.
For a non-Autonomous AI Database, you can update the credentials for the Oracle Data Safe service account. For an Autonomous AI Database, you can update the credentials
for the ADMIN account, which is required to unlock the Oracle Data
Safe user account that already exists on the database.
Manage Peer Databases Associated with a Registered Active Data Guard Primary Database
When you register a target database that is the primary database in an Active Data Guard association, you can manage the associated standby databases from the Target database information page of the primary database. Managing the standby databases can include, adding them as peer databases, refreshing their connection details, editing their connection details, or deregistering them from Oracle Data Safe.
- From the navigation menu in Oracle
Cloud Infrastructure, select Oracle AI
Database, and then select
Data Safe - Database
Security.
The Overview page for the Oracle Data Safe service is displayed.
- Under Data Safe on the left, click Target databases.
- Under List scope on the left, select the compartment that contains the target databases that you want to view.
- (Optional) To list all of the target databases in the child compartments too, select the Include child compartments check box.
- Click the name of the target database for which you want to add peer
databases to or refresh peer database connections for.
The Target database information page is displayed.
Add Peer Databases
- Click Add peer database in the Active Data Guard peer databases section.
- For a cloud target database and Cloud@Customer database:
- In the side pane you will see a list of standby database that are associated with the selected primary database. Select from the list which of the standby databases you would like to register as peers.
- (Optional) Click + on a standby database to see the details for and edit any of the following if necessary:
- Peer Display Name
- Database Service Name
- Database Port Number
- TCP/TLS
- Click Add peer database
- For an on-premises target database:
- In the side pane enter in the information for the peer
database:
- Peer display name
- Database service name
- Database IP address
- Database port number
- TCP/TLS
- Click Add row to add an additional peer database.
- Click Add peer database
- In the side pane enter in the information for the peer
database:
Manually Refresh Peer Database Connections
Click Refresh.
Note:
Oracle Data Safe automatically checks and refreshes the peer database connection details every hour.Edit Connection Details
- Click on the name of the peer database from the Active
Data Guard peer databases section.
This will bring you to the Peer database information page.
- To edit connection details, click Edit connection
details, edit the information as necessary, and click
Save changes.
Note:
If the peer database is the root database, the connection details can't be edited. The Secondary key value for a root database is 0.
Deregister a Peer Database
- Click on the name of the peer database from the Active
Data Guard peer databases section.
This will bring you to the Peer database information page.
- Click Deregister.
Actions to Take After Performing a Manual Switch Over of Active Data Guard Associated Target Databases
If you have registered Active Data Guard associated target databases in Oracle Data Safe, you are able to see the role (primary or standby) of the databases. If you perform a manual switchover of the databases, you may not see the changes in the roles reflected immediately in Oracle Data Safe.
As a result of this, it's possible that a data masking job will fail because the proper read and write permissions are not associated with the database.
To prevent this from occurring, after performing a manual switchover, refresh the database connections. See Manage Peer Databases Associated with a Registered Active Data Guard Primary Database for more information.
Deregister a Target Database
When you deregister a target database, the target database is no longer available in Oracle Data Safe. If your target database is connected via a private endpoint, the private endpoint is not automatically deleted during deregistration. You can still view collected audit data in the audit reports for a deregistered target database as long as the audit data retention period is not expired.
Resources that are Automatically Deleted When a Target Database is De-registered
When you de-register a target database there are a number of resources that are automatically deleted. However, there are also some resources that can't be deleted. See the below list to learn what happens to certain resources when a target database is de-registered.
Table 3-3 Resources that are automatically deleted when a target database is de-registered
| Functional Area | Oracle Data Safe Resource | Oracle Data Safe Resource Name in OCI IAM | Comments |
|---|---|---|---|
| Activity Auditing | Audit Profile* | data-safe-audit-profiles | In a cleanup job once there are no more audit events for the target |
| Activity Auditing | Audit Trail | data-safe-audit-trails | |
| Activity Auditing | Audit Event | data-safe-audit-events | Once the retention policy is over |
| Activity Auditing | Audit Policy* | data-safe-audit-policies | |
| Activity Auditing/Alerts | Target Alert Policy Associations | data-safe-target-alert-policy-associations | |
| Activity Auditing/Alerts | Report | data-safe-reports | Reports that are older than 90 days will be deleted in a routine cleanup job |
| Activity Auditing | Archive Retrievals | data-safe-archive-retrievals | Yes - After the retrieved data has been online for 30 days |
| User Assessment | User Assessment | user-assessments | In a routine cleanup job |
| Security Assessment | Security Assessment | security-assessments | In a routine cleanup job |
| SQL Firewall | Database Security Config | data-safe-database-security-configs | In a routine cleanup job |
| SQL Firewall | Security Policy | data-safe-security-policies | In a routine cleanup job |
| SQL Firewall | Security Policy Deployment | data-safe-security-policy-deployments | In a routine cleanup job |
| SQL Firewall | Firewall Policy | data-safe-sql-firewall-policies | In a routine cleanup job |
| SQL Firewall | SQL Collection | data-safe-sql-collections | In a routine cleanup job |
| SQL Firewall | Violation Logs | data-safe-sql-firewall-violations | Yes-After the 12 month retention period has passed |
| SQL Firewall | SQL Firewall Allowed SQL | data-safe-sql-firewall-allowed-sqls | In a routine cleanup job |
Note:
A maximum of 100 policies are cleaned up per day. So, in cases where more than 100 policies need to be cleaned up, the remaining policies are queued up for the next day's cleanup job.The routine cleanup job runs frequently and deletes a number of resources whenever it runs. If you have many resources in the queue to be deleted, it may take several runs of the cleanup job to empty the queue.
Resources associated with or used by the target database (for example, sensitive data models, masking policies, and reports) are not deleted when the target database is de-registered. You need to manually delete these items. See What Resources Can Be Deleted While a Target Database is Active for more information.
Manage Network Access Changes for Oracle Autonomous AI Database Serverless
You can change the network access type for Oracle Autonomous AI Database Serverless from Secure access from everywhere to Secure access from allowed IPs and VCNs only, and vice versa. When making a network access change, you may need to perform tasks to maintain the database's registration with Oracle Data Safe.
Overview
If you plan to switch the network access for your Oracle Autonomous AI Database Serverless from Secure access from everywhere (public endpoint) to Private endpoint access only, prior to making the network access change, you need to create an Oracle Data Safe private endpoint on the same virtual cloud network (VCN) and subnet as your database. If you plan to switch from a private endpoint to a public endpoint, you do not need to do anything other than make the network switch. You do not need to deregister your Autonomous AI Database with Oracle Data Safe beforehand. Your database will have a public IP address after you make the change and you can view that IP address from the database's Console. You may want to delete the Oracle Data Safe private endpoint previously used because it is no longer needed.
Note:
If your database is not yet registered with Oracle Data Safe, first make the network access change and then register it.
When you switch the network access type to Private endpoint access only, the database's private endpoint communicates with Oracle Data Safe's private endpoint. The two private endpoints allow Oracle Data Safe to communicate with your database. This scenario is illustrated in the diagram below.
Workflow
If your Oracle Autonomous AI Database Serverless is already registered with Oracle Data Safe and you want to switch the database's network access type from Secure access from everywhere to Private endpoint access only, then follow the general steps listed in the table below.
| Step | Description | Reference |
|---|---|---|
|
1 |
Create an Oracle Data Safe private endpoint. |
|
|
2 |
Switch the network access type to Private endpoint access only for your Oracle Autonomous AI Database Serverless. |
Change from Public to Private Endpoints with Autonomous AI Database |
|
3 |
Update the security rules to allow communication between Oracle Data Safe and your database. |
Update the Security Rules to Allow Communication Between Oracle Data Safe and Your Database |
Update the Security Rules to Allow Communication Between Oracle Data Safe and Your Database
Update the ingress and egress security rules for the Network Security Groups (NSGs) on your private VCN in Oracle Cloud Infrastructure to allow traffic from Oracle Data Safe's private endpoint to your Autonomous AI Database's private endpoint. While both an NSG and a security list act as virtual firewalls for your database, Oracle recommends that you use NSGs. For more information, see Network Security Groups.
Example 3-4 Configure security rules for Oracle Autonomous AI Database Serverless with private VCN access
Suppose you provision an Oracle Autonomous AI Database Serverless with private VCN access in Oracle Cloud Infrastructure. During provisioning, Oracle Cloud Infrastructure automatically creates a private endpoint for your database and you associate an NSG with your database.
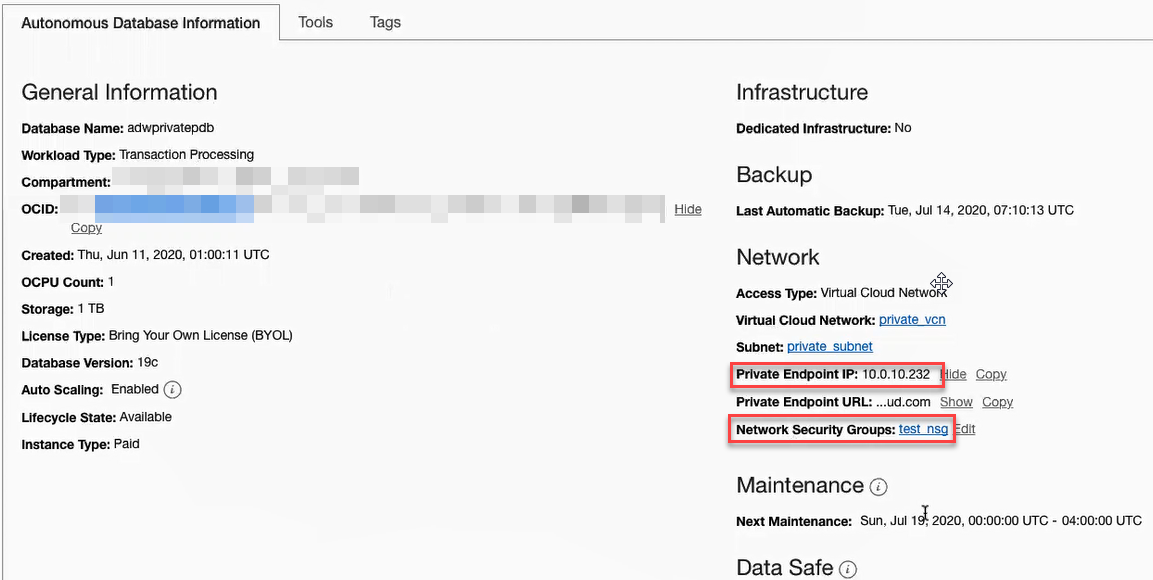
To obtain the private IP address for your database's private endpoint and view the NSG name, you access the Autonomous AI Database information tab in your database's Console in Oracle Cloud Infrastructure. As shown in the following screenshot, under Network, the private endpoint's IP address is 10.0.10.232 and the NSG name is test_nsg.
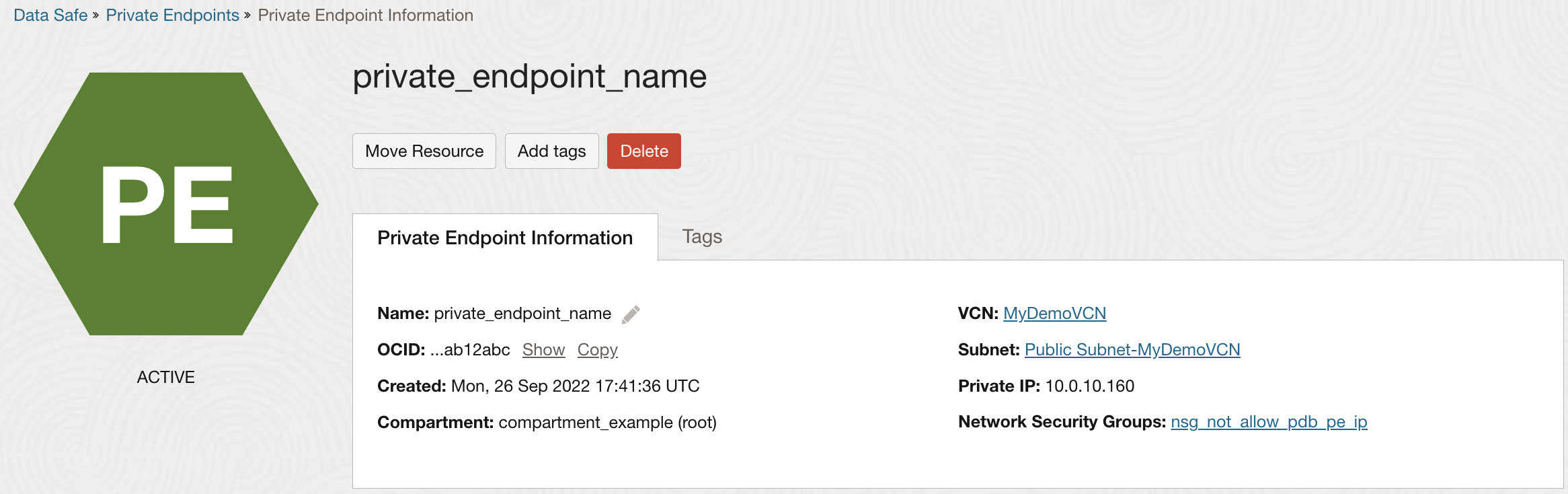
To obtain the private IP address and NSG for Oracle Data Safe's private endpoint, you access the Private endpoint information tab on the Data Safe page in Oracle Cloud Infrastructure. As shown in the following screenshot, the IP address is 10.0.10.160 and the NSG name is nsg_not_allow_pdb_pe_ip.
Next, you create a security rule for each of the NSGs the following way:
- Ingress rule for the database private endpoint NSG: The database's private endpoint IP address, 10.0.10.232 (on port 1522), can receive incoming traffic from Oracle Data Safe's private endpoint IP address, 10.0.0.6 (from any port).
- Egress rule for the Oracle Data Safe private endpoint NSG: Oracle Data Safe's private endpoint IP address, 10.0.0.6 (from any port), can send requests to the database's private endpoint IP address, 10.0.10.232 (on port 1522).
The following diagram illustrates the security rules.
What to Do if an Autonomous AI Database Name Changes
If you rename your Autonomous AI Database from the database's Console in Oracle Cloud Infrastructure, the change is automatically propagated to Oracle Data Safe. Oracle recommends that you update the target database name in Oracle Data Safe to best match your database name.
Each target database name must be unique in Oracle Data Safe. By updating your target database name, you can avoid name conflicts in the future.