Use OAuth 2.0 Grants in Oracle Identity Cloud Service Environments
To use an OAuth 2.0 grant type with the Oracle Utilities Adapter in Oracle Integration, you must perform the following prerequisites.
- Prerequisites for All Grants
- Prerequisites for Resource Owner Password Credentials
- Prerequisites for OAuth Client Credentials
- Prerequisites for JWT Assertions
Note:
The following instructions apply only to cloud tenancies that still use Oracle Identity Cloud Service. Most cloud tenancies have been migrated to identity domains, which require different configuration instructions. See Use OAuth 2.0 Grants in Identity Domain Environments. If you are unsure of your environment, check with your administrator.Note:
Understand the following restrictions before performing OAuth 2.0 grants.- Do not let external client applications use the system-created Oracle Identity Cloud Service application to authenticate against Oracle Integration endpoints.
- The scope of the client application is for accessing all deployed integrations in that service instance. There is no support for limiting access to a subset of integrations.
- To trigger the Oracle Integration flow with OAuth, the Oracle Utilities Adapter trigger connection should also use the OAuth Client Credentials security policy.
- The OUAF applications do not support the OAuth Client Credentials using JWT Client Assertion security policy or the OAuth using JWT User Assertion security policy for the message sender to trigger an integration. However, the Basic Authentication and OAuth Client Credentials security policies can still be used by the message sender to initiate a JWT-based connection on the trigger end of the integration.
Prerequisites for All Grants
Perform the following tasks for each grant type you use.
- Obtain the Oracle Identity Cloud
Service URL.
- Go to the URL for your Oracle Utilities application. You are
redirected to a URL such
as:
https://idcs-c2881.identity.myhost.example.com/ui/v1/signin - Replace
/signinwith/adminconsoleto access Oracle Identity Cloud Service.For example:https://idcs-c2881.identity.myhost.example.com/ui/v1/adminconsoleYou'll be prompted to sign in again to the Oracle Identity Cloud Service Console.
- Log in to the Oracle Identity Cloud Service Console with your identity domain administrator credentials.
- Go to the URL for your Oracle Utilities application. You are
redirected to a URL such
as:
- Check the Oracle Utilities application in Oracle Identity Cloud
Service.
When an Oracle Utilities application instance is provisioned, an Oracle Identity Cloud Service application is created for that application instance. The application name is composed as follows:
product-domaintenantsuffixsequential_numberFor example:CCS-PRODC12345CMETERDATA0CCS-PRODC12345FIELDSERVICE1- To request creation of a new OAuth client application,
create a cloud operations service request and provide the following
information:
- Environment(s) where the OAuth client application is needed (for example, PROD, TEST01, or DEV).
- Client name suffix: Use a distinct name that may suggest the functional purpose of the integration.
- Provide a meaningful description of the integration point.
- Client type (trusted or confidential) and client certificate: The integration requirements may call for a trusted client and the external application may also supply its own certificate. Otherwise, Oracle Identity Cloud Service creates a trusted client with its internal native certificate.
- OAuth flow for your intended integration: Client credentials is currently supported.
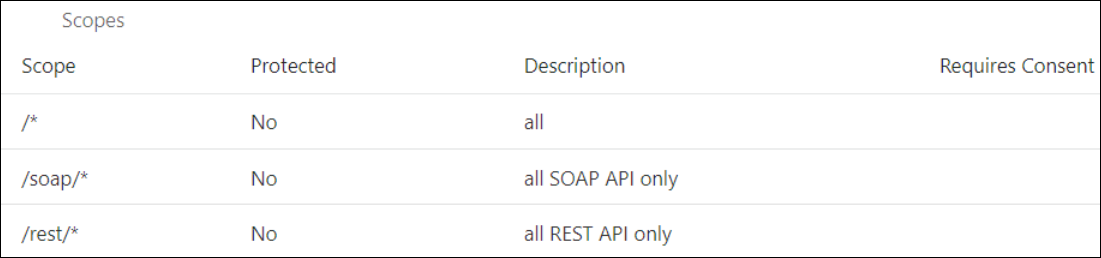
- Scope: You can define the OAuth client application with access to either REST or SOAP APIs or both REST and SOAP APIs.
The Oracle Utilities Cloud Operations team creates the OAuth client using the input provided in the service request.- Log in to Oracle Identity Cloud Service to get your application.
- Go to Oracle Cloud Services and find the application with the above name to access the application.
- To request creation of a new OAuth client application,
create a cloud operations service request and provide the following
information:
Prerequisites for Resource Owner Password Credentials
Perform the following tasks.
- Validate the Oracle Integration application and user roles:
- Go to Configuration, and then Client Configuration of the Oracle Identity Cloud Service application.
- Verify that Resource Owner and Refresh Token for Allowed Grant Types are enabled.
- Go to Configuration, and then Resources of the Oracle Identity Cloud Service application.
- Verify that the Is Refresh Token
Allowed option is enabled.
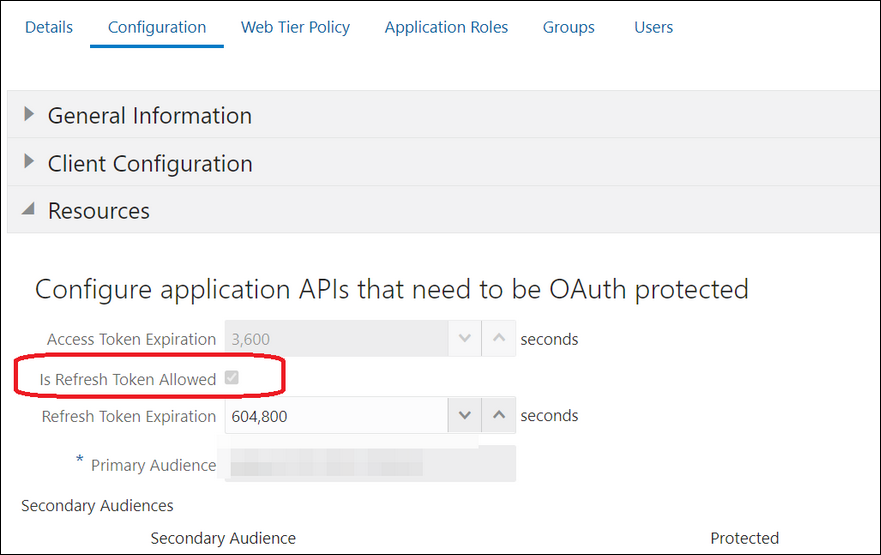
The scope with access to either REST or SOAP APIs or both REST and SOAP APIs is provided.
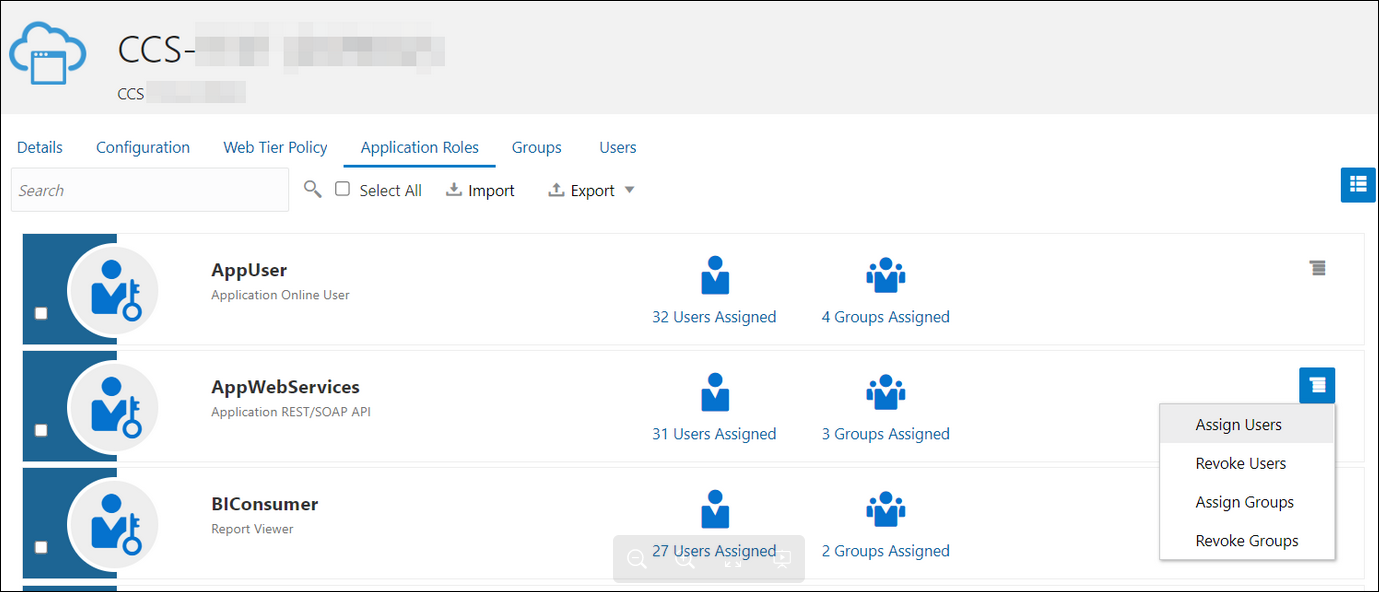
- Add the appropriate user(s) to the various Oracle Application roles. For standard/production configurations, use the ServiceUser role. (See Oracle Integration Service Roles in Provisioning and Administering Oracle Integration 3.)
- To assign the user, go to the Application
Roles section of the application and assign the user for
AppWebServices.
- Configure the client application:
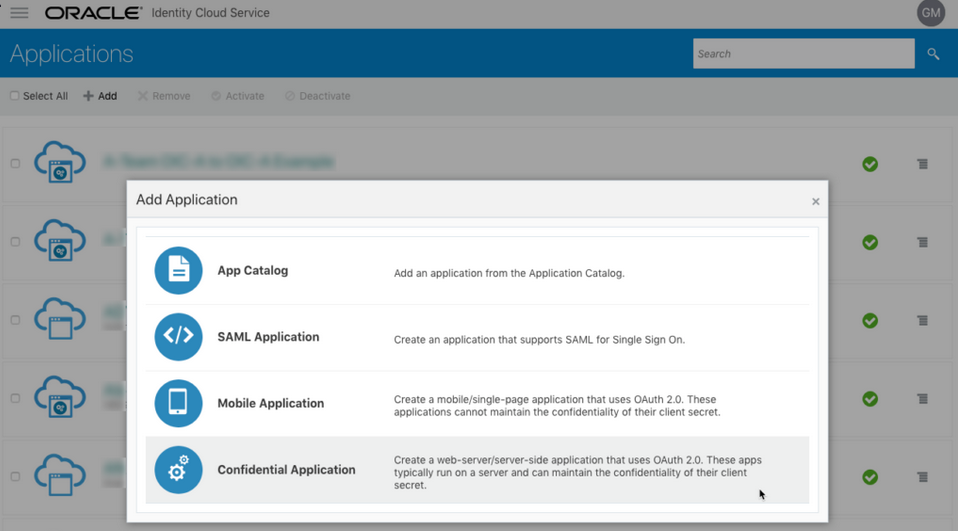
- In the Oracle Identity Cloud Service Console, go to the Applications section to create a new application that allows you to invoke an Oracle Utilities application with an OAuth Utilities Connection. Add this application as a confidential application.
- Click Add.
- Select Confidential Application.
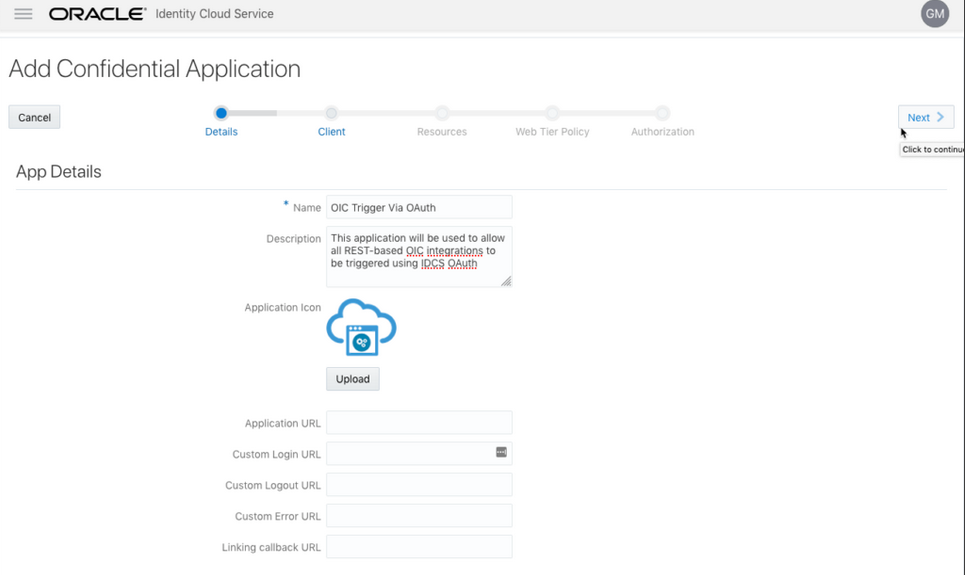
- Complete the Details page, and go to the Client page.
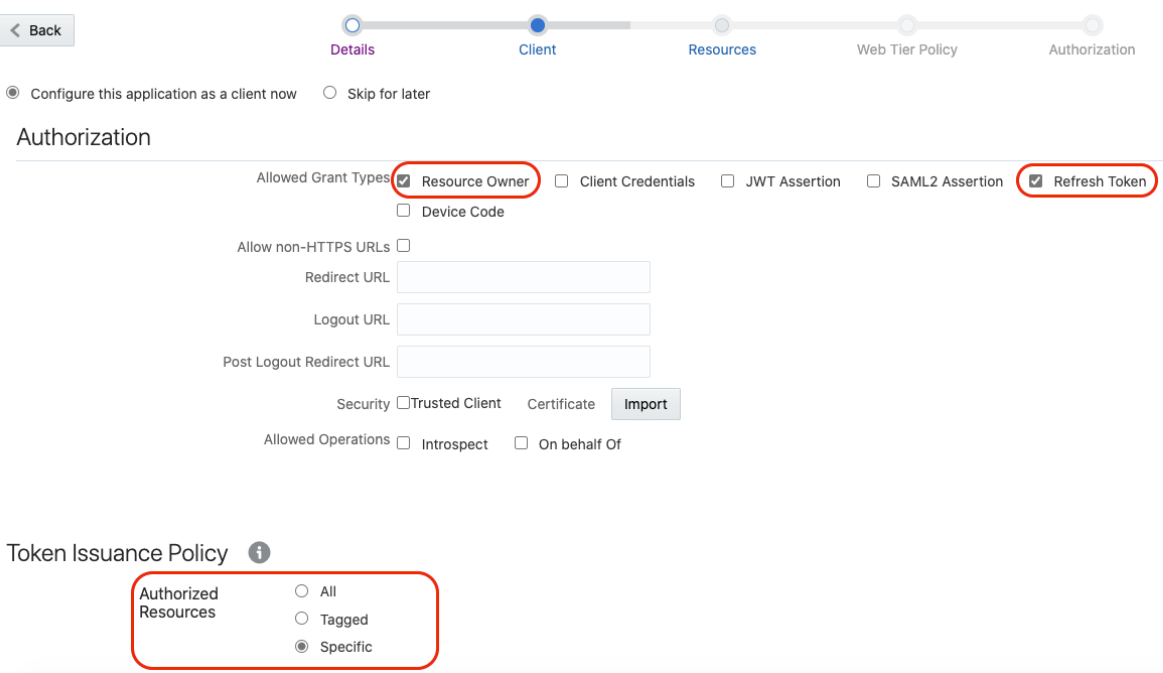
- On the Client page, select
Configure this application as a client now
and add the following.
- Select Resource Owner and Refresh Token for Allowed Grant Types.
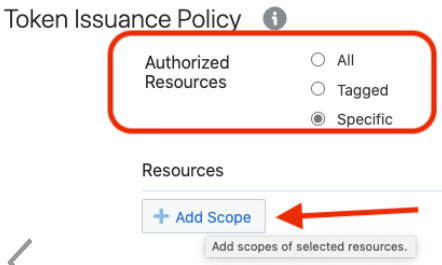
- Select Specific in the Authorized Resources section.
- Click Add Scope under the
Resources section.
- Find the Oracle Utilities application.
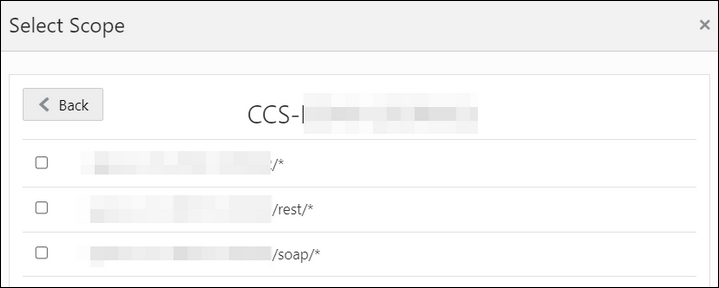
- Add the scope containing access to either REST
(/rest/*) or
SOAP(/soap/*) APIs or both REST and
SOAP APIs (/*), and click
>.
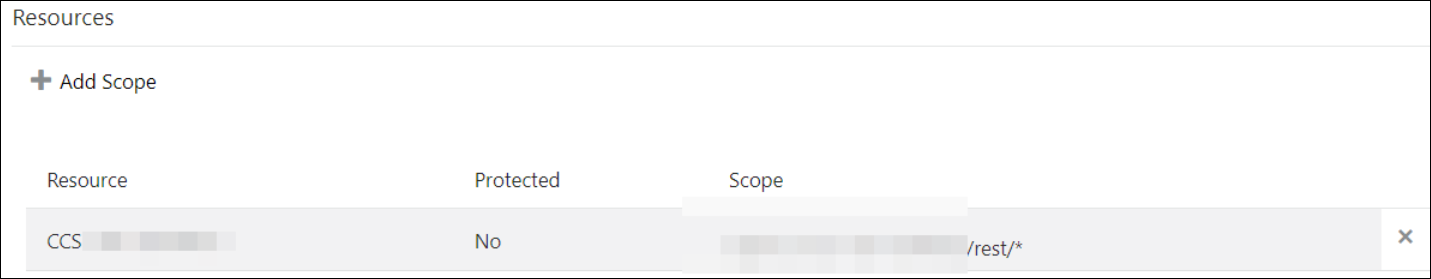
- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- Validate the client application:
- To fetch the access client, make a request to Oracle Identity Cloud
Service with the user name and password in the
payload.
Note:
Addoffline_accessin the scope to fetch the request refresh token as part of the response.##Syntax curl -i -H 'Authorization: Basic <base64Encoded_clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=password&username=<user-name>&password=<password>&scope=<App_Scope>%20offline_access' ###where #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <username> - user for token needs to be issued (must be in serviceuser role). #### <password> - password for above user #### <app_scope> - Scope added while creating application in client configuration section ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<idcs_host>/oauth2/v1/token -d 'grant_type=password&username=sampleUser&password=SamplePassword&scope=https://<Resource_APP_Audience>/rest/*%20offline_access' - Capture the
access_tokenandrefresh_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600, "refresh_token": "AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc=" } - Use the
access_tokenin the authorization header to invoke the Oracle Utilities application endpoint.curl --location --request GET 'https://<Utilities_Application_API_ENDPOINT>' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token, use the refresh token and make a request to Oracle Identity Cloud Service.
- Capture the
access_tokenandrefresh_tokenfrom the response for further use.curl -i -H 'Authorization: Basic <base64-clientid-secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=<refresh_token>' ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=refresh_token&refresh_token=AQAgY2MzNjVlOTVhOTRh...vM5S0MkrFSpzc='
- To fetch the access client, make a request to Oracle Identity Cloud
Service with the user name and password in the
payload.
Prerequisites for OAuth Client Credentials
Oracle Identity Cloud Service (IDCS) configuration requirements for OAuth Client Credential inbound and outbound requests in integrations using the Oracle Utilities Adapter are described below.
- Inbound to Oracle Integration:
For IDCS configurations to enable OAuth Client Credentials in the inbound direction to Oracle Integration, see Prerequisites for Client Credentials in Using the REST Adapter with Oracle Integration 3.
- Outbound from Oracle Integration to
Oracle Utilities Applications:
Perform the following tasks.
- Validate the Oracle Utilities application and user
roles:
- Go to Configuration, and then Client Configuration of the Oracle Identity Cloud Service application.
- Verify that Client Credentials for Allowed Grant Types is enabled.
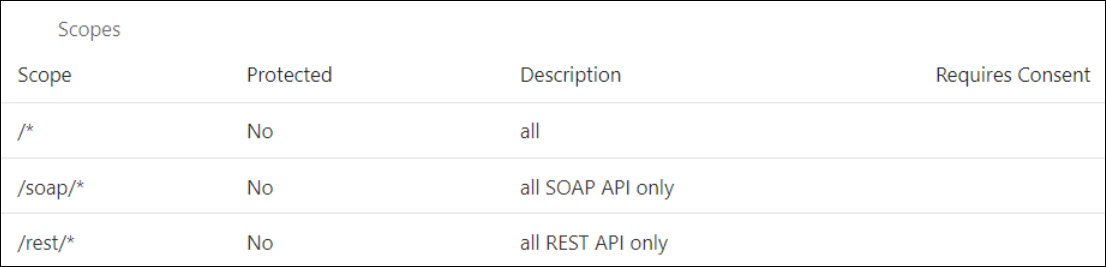
- Go to Configuration, and
then Resources of the Oracle Identity
Cloud Service application. The scope with access to either REST
or SOAP APIs or both REST and SOAP APIs is provided.
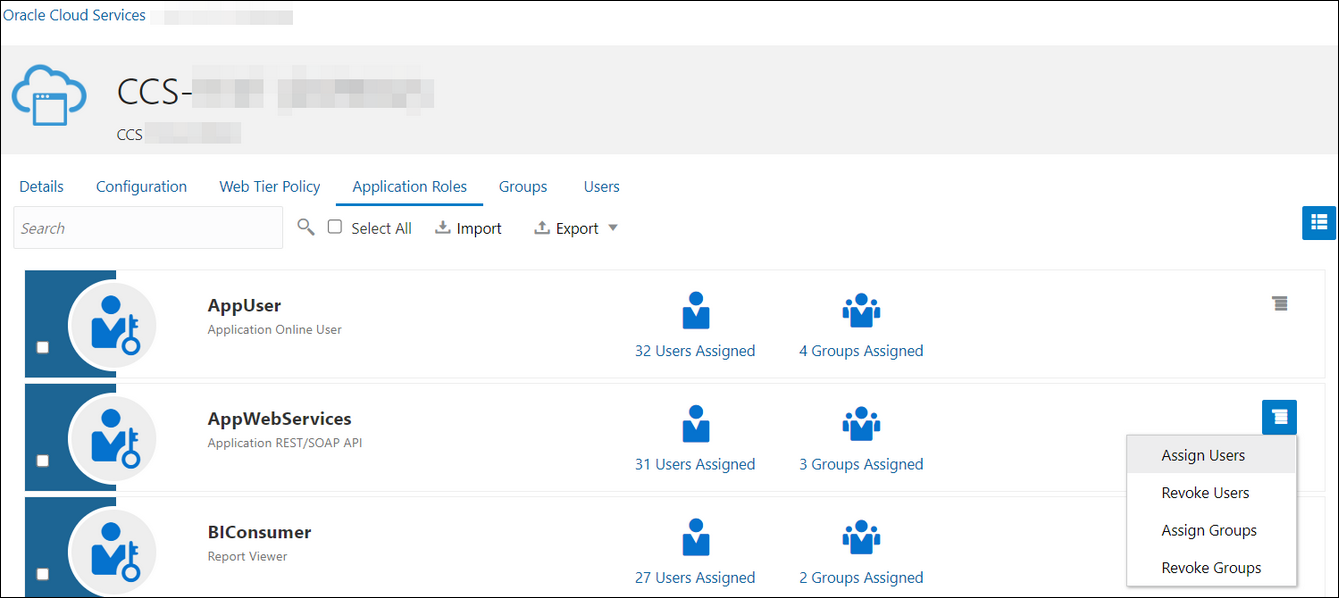
- Add the appropriate user(s) to the various Oracle Utilities application roles. For standard/production configurations, use the ServiceUser role. (See Oracle Integration Service Roles in Provisioning and Administering Oracle Integration 3.)
- To assign the user, go to the
Application Roles section of the
application under AppWebServices.
- Configure the client application:
- In the Oracle Identity Cloud Service Console, go to the Applications section to create a new application that allows you to invoke an Oracle Utilities application API with an OAuth Utilities Connection. The application is added as a confidential application.
- Complete the Details section, and go to the Client section.
- On the Client page,
select Configure this application as a client
now, and complete the following:
- Select Client Credentials from the Allowed Grant Types list.
- Select Specific in the Authorized Resources area of the Token Issuance Policy section.
- Click Add Scope under the Resources section.
- Find the Oracle Utilities application.
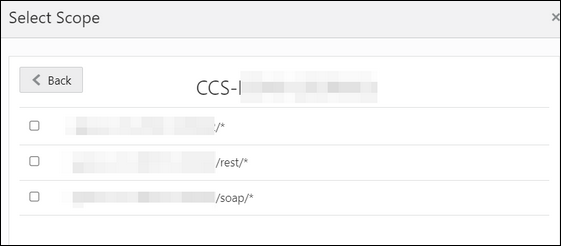
- Add the scope containing access to either
REST or SOAP APIs or both REST and SOAP APIs, and click
>.
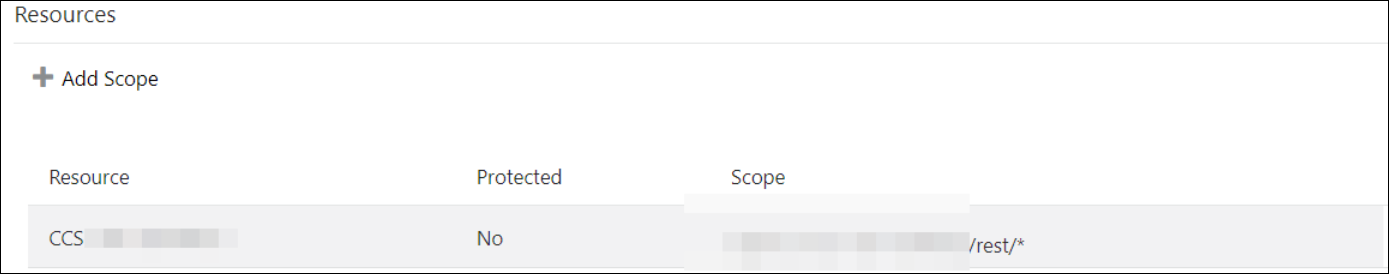
- Save your changes.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
The next step is to create an application user in the appropriate Oracle Utilities Cloud Service (such as Oracle Utilities Meter Solution Cloud Service). Access the appropriate Oracle Utilities Cloud Service application, and navigate to the User portal.- Create a new user corresponding to the OAuth
client created above:
- Search for
Add User. - Enter the OAuth client ID as the user’s login ID.
- Provide values of your choice for the mandatory fields, such as USER, LAST NAME, and FIRST NAME.
- Select USER ENBLE as Enable.
- Assign User Groups that provide the integration with access to the appropriate functionality (for example, the ALL_SERVICES user group providing a future expiration date).
- Assign To Do Roles (for example, the F1_DFLT system default role) and appropriate Access Security (for example, System Default) with an expiration date to the created user.
- Save the user.
The OAuth client credentials are now ready to use.
- Search for
- Validate the client application.
- Fetch the access client to make a request to Oracle
Identity Cloud Service with the client ID and client secret of
the client in the
payload.
##Syntax curl -i -H 'Authorization: Basic <base64Encoded_clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<IDCS-Service-Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=client_credentials&scope=<App_Scope>' ###where #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <app_scope> - Scope added while creating application in client configuration section ##Example curl -i -H 'Authorization: Basic OGQyM...ZDA0Mjcz' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<idcs_host>/oauth2/v1/token -d 'grant_type=client_credentials&scope=https://<Resource_APP_Audience>/rest/*' - Capture the
access_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600 } - Use the
access_tokenin the authorization header to invoke the Oracle Utilities Application APIs.curl --location --request GET 'https://<Utilities_Application_API_ENDPOINT>' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token when it is expired, make the same request to Oracle Identity Cloud Service.
- Fetch the access client to make a request to Oracle
Identity Cloud Service with the client ID and client secret of
the client in the
payload.
- Validate the Oracle Utilities application and user
roles:
Prerequisites for JWT Assertions
- Inbound to Oracle Integration
For IDCS configurations to enable JWT user/client assertions in the inbound direction to Oracle Integration, see Prerequisites for JWT User Assertion in Using the REST Adapter with Oracle Integration 3.
- Outbound from Oracle Integration to Oracle Utilities Applications
- Generate the key
- Configure the client application
- Add a certificate as a trusted partner
- Generate the JWT user assertion
- Generate the JWT client assertion
- Validate the client application
- Generate the key
You must first generate the key to import when you configure the client application for the JWT user assertion.
- Generate the self-signed key
pair.
keytool -genkey -keyalg RSA -alias <your_alias> -keystore <keystore_file> -storepass <password> -validity 365 -keysize 2048 ##example keytool -genkey -keyalg RSA -alias assert -keystore sampleKeystore.jks -storepass samplePasswd -validity 365 -keysize 2048 - Export the public key for signing the JWT
assertion.
keytool -exportcert -alias <your_alias> -file <filename> -keystore <keystore_file> -storepass <password> ##example keytool -exportcert -alias assert -file assert.cer -keystore sampleKeystore.jks -storepass samplePasswd ## This should show a success message e.g. Certificate stored in file <assert.cer> - Convert the keystore to P12
format.
keytool -importkeystore -srckeystore <filename> -srcstorepass <password> -srckeypass <password> -srcalias <your_alias> -destalias <your_alias> -destkeystore <destFileName> -deststoretype PKCS12 -deststorepass <password> -destkeypass <password> ##example keytool -importkeystore -srckeystore sampleKeystore.jks -srcstorepass samplePasswd -srckeypass samplePasswd -srcalias assert -destalias assert -destkeystore assert.p12 -deststoretype PKCS12 -deststorepass samplePasswd -destkeypass samplePasswd ## This should show a success message e.g. Importing keystore sampleKeystore.jks to assert.p12... - Export the private key from the P12
keystore.
openssl pkcs12 -in <destFileName> -nodes -nocerts -out <pem_file> ##example openssl pkcs12 -in assert.p12 -nodes -nocerts -out private_key.pem ## This should show a success message: MAC verified OK
- Generate the self-signed key
pair.
- Configure the client applicationIn the Oracle Cloud Console, go to the Integrated applications section to create a new application that allows you to invoke an Oracle Utilities application API with an JWT Utilities connection.
- Click Add application.
- Select Confidential Application, and click Launch workflow.
- Enter a name in the Application details section. The remaining fields on this page are optional and can be ignored.
- Click Next.
- In the Client configuration
section, select Configure this application as a client
now, and complete the following:
- For JWT assertions, select JWT assertion and Refresh token in the Allowed grant types section.
- Leave the Redirect URL, Post-logout redirect URL, and Logout URL fields blank.
- In the Client type section, select Trusted.
- Upload the public certificate created in the Generate the key section.
- Provide the alias name. Remember this alias name because it is used when creating assertions. This action adds the certificate as a trusted partner.
- Bypass several fields and scroll down to the Token issuance policy section.
- Select Specific in the Authorized resources section.
- Click the Add Resources check box.
- Click Add scope.
- Use the search facility to find the Oracle
Utilities application.
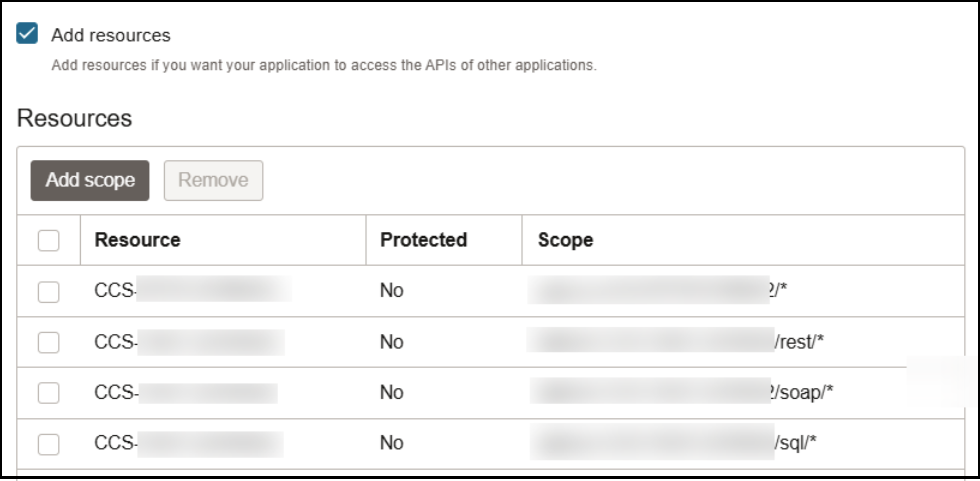
- Add the scope containing access to either REST or SOAP APIs or both REST and SOAP APIs. The scopes are displayed in the Resources section.
- Click through the remaining wizard pages without making changes and save the application.
- Activate the application for use.
- In the General Information section, note the client ID and client secret values. These values are required for the third-party application that is communicating with the identity domain.
- Add a certificate as a trusted partnerIn addition to importing the signing certificate into the client application, you are also required to include the certificate as a trusted partner certificate.
- In the navigation pane, click
Settings.
- Click Trusted partner certificates.
- Click Import certificate to upload the public certificate created in the Generate the key section.
- In the navigation pane, click
Settings.
- Generate the JWT user assertion
Generate the JWT user assertion using the generated private key and simple Java code.
Note:
You can use the https://github.com/jwtk/jjwt library to generate the user assertion. There are many libraries listed at https://jwt.io/ for multiple technologies.Sample: header: { "alg": "RS256", "typ": "JWT", "kid": "assert" } payload: { "sub": "utilitiesApplicationUser", "jti": "8c7df446-bfae-40be-be09-0ab55c655436", "iat": 1589889699, "exp": 1589909699, "iss": "d702f5b31ee645ecbc49d05983aaee54", "aud": "https://identity.oraclecloud.com/" }Where:subspecifies the user name for whom user assertion is generated.jtiis a unique identifier.iatis issued (epoch seconds).expis the token expiry (epoch seconds).issis the client ID aud must include the identity domain audiencehttps://identity.oracle.com/. The signing algorithm must be RS256.kidspecifies the key to use to verify the signature. Therefore, it must match with the uploaded certificate alias.
- Generate the JWT client assertion
Similar to JWT user assertion, you can generate the client assertion using the generated private key and simple Java code.
Note:
You can use the https://github.com/jwtk/jjwt library to generate the user assertion. There are many libraries listed at https://jwt.io/ for multiple technologies.Sample: header: { "alg": "RS256", "typ": "JWT", "kid": "assert" } payload: { "sub": "d702f5b31ee645ecbc49d05983aaee54", "jti": "8c7df446-bfae-40be-be09-0ab55c655436", "iat": 1589889699, "exp": 1589909699, "iss": "d702f5b31ee645ecbc49d05983aaee54", "aud": "https://identity.oraclecloud.com/" }Where:subspecifies the client ID of the client application.jtiis a unique identifier.iatis issued (epoch seconds).expis the token expiry (epoch seconds).issis the client ID aud must include the identity domain audience https://identity.oracle.com/. The signing algorithm must be RS256.kidspecifies the key to use to verify the signature. Therefore, it must match with the uploaded certificate alias.
Note:
In user assertions, you addsubas the user name. In client assertions, you add the client ID assub. - Validate the client application
- Once you generate the JWT user assertion, generate the access token as
follows.
##Syntax curl -i -H 'Authorization: Basic <base64Encoded clientid:secret>' -H 'Content-Type: application/x-www-form-urlencoded;charset=UTF-8' --request POST https://<Identity_Domain_Service_Instance>.identity.oraclecloud.com/oauth2/v1/token -d 'grant_type=urn%3Aietf%3Aparams%3Aoauth%3Agrant-type%3Ajwt-bearer&assertion=<user assertion>&scope=<app_scope>' ###where #### grant type - urn:ietf:params:oauth:grant-type:jwt-bearer #### <base64-clientid-secret> - Base 64 encode clientId:ClientSecret #### <user assertion> - User assertion generated #### <app scope> - Scope added while creating application in client configuration section - Capture the
access_tokenfrom the response.{ "access_token": "eyJ4NXQjG...dfsdfsFgets2ed", "token_type": "Bearer", "expires_in": 3600 } - Use the
access_tokenin the authorization header to invoke the Oracle Utilities Application APIs.curl --location --request GET 'https://<Utilities_Application_API_ENDPOINT>' \ --header 'Authorization: Bearer eyJ4NXQjG...dfsdfsFgets2ed' - To update the access token when it expires, make the same request to Oracle Identity Cloud Service.
- Once you generate the JWT user assertion, generate the access token as
follows.
- Add new security policies
- OAuth Client Credentials using JWT Client Assertion
- OAuth using JWT User Assertion