Prerequisites for Creating a Connection
Satisfy the following prerequisites specific to your environment to create a connection with the Oracle HCM Cloud Adapter.
- Subscribe to Oracle HCM Cloud
- Assign Required Roles to an Integration User
- Request Access to Atom Feeds and REST APIs Capabilities on Your Oracle HCM Cloud Instances
- Create an HCM-compliant .dat File to Use the HCM Data Loader
- Upload Files to Oracle WebCenter Content
- Perform Prerequisites to Set Up the OAuth Authorization Code Credentials Security Policy
- Verify the Status of Location-Based Access Control (LBAC)
- Perform Prerequisites to Use the JWT User Assertion Security Policy
- Specifying the Oracle HCM Cloud Service Catalog Service WSDL or Event Catalog URL
Subscribe to Oracle HCM Cloud
Subscribe to Oracle HCM Cloud. This action enables you to create an Oracle HCM Cloud user account with the correct privileges. You specify this user account when creating an Oracle HCM Cloud Adapter connection on the Connections page.
For information about specifying these credentials on the Connections page, see Configure Connection Security. For information about subscribing, see Oracle HCM Cloud.
Request Access to Atom Feeds and REST APIs Capabilities on Your Oracle HCM Cloud Instances
Oracle HCM Cloud Atom feeds and Oracle HCM Cloud REST APIs support is available by default in the Oracle HCM Cloud Adapter in Oracle Integration. However, for the Oracle HCM Cloud application, you must first request access to Atom feeds and REST APIs capabilities on your Oracle HCM Cloud instance(s).
See the steps described in My Oracle Support Note 2060899.1. Once these are enabled in your Oracle HCM Cloud application, Atom feeds and REST APIs appear in the Oracle HCM Cloud Adapter in Oracle Integration.
Assign Required Roles to an Integration User
To use the Oracle HCM Cloud Adapter in an integration, you must assign specific roles to an integration user.
Associating the Integration User with the Following Roles and Privileges
| Role | Description |
|---|---|
|
ALL_INTEGRATION_POINTS_ALL_DATA |
Starting with release 12, this role is no longer supported. When existing customers upgrade to release 12, users with this role continue using it, although it is hidden from the Security Console. If you create a new integration user in release 12 or later, you cannot assign this role. |
|
ORA_HRC_HUMAN_CAPITAL_MANAGEMENT_INTEGRATION_SPECIALIST_JOB |
Human Capital Management Integration Specialist. The role applies to Releases 12 and 13. |
|
AttachmentsUser |
Provides access to the Attachments security group to download the log file or the output file with the HCM Integration Service. Starting with Release 12, this role is automatically shipped. You must verify that this role is automatically assigned to the user. |
|
SOAOperator |
The SOA Operator role. |
|
FND_MANAGE_CATALOG_SERVICE_PRIV |
Role for managing the web services catalog. |
|
For Oracle CRM Cloud implementations, you can also assign the Customer Relationship Management Application Administrator role. |
See Customer Relationship Management Application Administrator (Job Role) of Security Reference for CX Sales and B2B Service. |
Additional roles may be required as per each interface requirements.
Using the Security Console
Use the Security Console to manage application security such as roles, users, certificates, and administration tasks. Access to the Security Console is provided by the predefined Security Manager role. Access the Security Console in the following ways:
-
Use the Manage Job Roles or Manage Duties tasks in the Setup and Maintenance work area.
-
Select Navigator > Tools > Security Console.
Description of the illustration sales_cloud_security.png
Create an HCM-compliant .dat File to Use the HCM Data Loader
If you want to use the HCM Data Loader for bulk-loading and maintaining
data, you must create a .dat file that is HCM-compliant. See your
Oracle HCM Cloud documentation for instructions.
Upload Files to Oracle WebCenter Content
You must satisfy the following prerequisites if you want to upload a file to Oracle WebCenter Content (Universal Content Manager) with the Oracle HCM Cloud Adapter.
-
Create a PGP Public Key for Encrypted File Upload:
To upload encrypted files, a PGP public key is required. You must generate the PGP public key and save it for upload. The supported algorithm for the public key is RSA for encryption and the key size must be 1024 bits in length.
The process for uploading files into Oracle HCM Cloud is:
-
You encrypt files using the Oracle HCM Cloud public key.
-
The data-loading process decrypts files using the Oracle HCM Cloud private key.
See Set up Encryption for File Transfer in HCM Data Loader.
-
-
Configure Security and User Access
Once you have configured security groups and doc accounts for the file to upload, you can configure the Oracle HCM Cloud Adapter to upload the file to Oracle WebCenter Content.
Perform Prerequisites to Set Up the OAuth Authorization Code Credentials Security Policy
Perform the following prerequisites to set up the OAuth Authorization Code Credentials security policy with an Oracle Fusion Applications identity domain or a non-Oracle Fusion Applications identity domain (for example, the Oracle Integration identity domain).
Set Up the OAuth Authorization Code Credentials Security Policy with the Oracle Fusion Applications Identity Domain
You must create a resource application to represent the Oracle Fusion Applications resource and a client application for Oracle Integration to use the OAuth Authorization Code Credentials security policy. Once these tasks are completed, you can successfully configure a connection on the Connections page. You do not need to create any JWT signing certificates for upload into Oracle Fusion Applications.
Create an Identity Domain Resource Application to Represent the Oracle Fusion Applications Resource
- Create an identity domain resource application to represent the
Oracle Fusion Applications resource.
- Log in to the identity domain as the domain administrator.
- In the menu bar, click Identity & Security.
- Click Domains.
- Select your compartment.
- Click the identity domain.
- In the menu bar, click Integrated
applications.
This is the location at which you create the client application for your grant type.
- Click Add application.
- Select Confidential Application, then click Launch workflow.
-
- Provide a name (for example,
FA Resource), and click Submit. - Click the OAuth configuration tab, then the Edit OAuth configuration subtab.
- In the Resource server configuration section, select Configure this application as a resource server now.
- (Optional) In the Configure application APIs that need to be OAuth protected section, select a value from the Access token expiration (seconds) list.
- Click the Allow token refresh toggle.
- In the Refresh token expiration (seconds) list, select a value.
- In the Primary audience field, add
the Oracle Fusion Applications URL and port. This is the primary
recipient where the token is
processed.
https://FA_URL:443 - Click the Add scope toggle, then click Add.
- In the Scope field, enter
/. - In the Description field, enter All.
- Select Requires user consent.
- Click Add, then click Submit.
- From the Actions menu at the top, select Activate, and then Activate application to activate the application for use. The resource server representing the resource is now active.
- Provide a name (for example,
Create the Confidential Client Application for Oracle Integration
- Sign in as the identity domain administrator to the Oracle Cloud Console.
- In the menu bar, click Identity & Security.
- Click Domains.
- Select your compartment.
- Click the identity domain.
- In the menu bar, click Integrated applications.
- Click Add application.
- Select Confidential Application, then click Launch workflow.
- Enter a name. The remaining fields on this page are optional and can be ignored.
- Click Submit.
- Click the OAuth configuration tab, then the Edit OAuth configuration subtab.
- In the Client configuration panel, select Configure this application as a client now.
- For the authorization code, select Refresh token and Authorization code in the Allowed grant types section.
- In the Redirect URL field, enter the
redirect URL of the client application. After user login, this URL is redirected
to with the authorization code. You can specify multiple redirect URLs. This is
useful for development environments in which you have multiple instances, but
only one client application due to licensing issues. For example:
Note:
If you don't know the following information, check with your administrator:
- If your instance is new or upgraded from Oracle Integration Generation 2 to Oracle Integration 3.
- The complete instance URL with the region included (required for new instances).
For Connections… Include the Region as Part of the Redirect URL? Example of Redirect URL to Specify… Created on new Oracle Integration 3 instances Yes. https://OIC_instance_URL.region.ocp.oraclecloud.com/icsapis/agent/oauth/callbackCreated on instances upgraded from Oracle Integration Generation 2 to Oracle Integration 3
No. This applies to both:
- New connections created after the upgrade
- Existing connections that were part of the upgrade
https://OIC_instance_URL.ocp.oraclecloud.com/icsapis/agent/oauth/callbackFor the OAuth authorization code to work, the redirect URI must be set properly.
- Click the Add Resources toggle.
- Click Add scope to add appropriate scopes.
If the Oracle Fusion Applications instance is federated with the identity domain, the Oracle Integration cloud service application is listed among the resources for selection. This enables the client application to access Oracle Integration.
- Search for the Oracle Fusion Applications resource application created in Create an Identity Domain Resource Application to Represent the Oracle Fusion Applications Resource.
- Find and expand the resource.
- Select the scope, then click Add.
- Click Submit.
The Details page shows the client ID and client secret values in the General Information section.
- Copy and save these values. You need this information when creating
a connection for the OAuth Authorization Code Credentials security policy on the
Connections page.
Note the following details for successfully authenticating your account on the Connections page.
If The... Then... Identity domain safeguarding Oracle Integration and the Oracle Fusion Applications resource application are the same. Log in to Oracle Integration using the local Oracle Fusion Applications user created earlier. You must create a connection and click Provide Consent on the Connections page for authentication to succeed. Identity domain safeguarding Oracle Integration and the Oracle Fusion Applications resource application are different. Log in to Oracle Integration using a general Oracle Integration developer account, create a connection, and click Provide Consent on the Connections page. You need to log in to the Oracle Fusion Applications resource identity domain application using the local Oracle Fusion Applications user account created earlier. - From the Actions menu at the top, select Activate, and then Activate application to activate the client application for use.
Resolve Errors That Occur When Clicking Provide Consent
After you configure the OAuth Authorization Code Credentials security policy on the Connections page, you must test your connection.
If you are logged in to Oracle Integration with an Oracle Integration
user account and click Provide Consent to test the OAuth
flow, consent is successful. However, when you test the connection, it fails with an
Unauthorized 401 error.
- Log out of Oracle Integration and log back in with a user account that exists in Oracle Fusion Applications.
- Return to the Connections page and retest the connection.
The connection is successful this time.
Set Up the OAuth Authorization Code Credentials Security Policy with a Non-Oracle Fusion Applications Identity Domain
You must set up trust between Oracle Fusion Applications and an identity domain and create a client application for Oracle Integration to use the OAuth Authorization Code Credentials security policy. Once these tasks are completed, you can successfully configure a connection on the Connections page. Use this option when you are integrating with a non-Oracle Fusion Applications identity domain, such as the Oracle Integration identity domain.
Set Up Trust Between Oracle Fusion Applications and an Identity Domain
- Get the JWK signing certificates from the identity domain of Oracle Integration.
- Get the REST API of the identity domain endpoint that gives
you the signing certificate endpoint. For
example:
/admin/v1/SigningCert/jwk - Copy the endpoint.
- Get the identity domain URL from the Oracle Cloud Console or from the Oracle Integration About menu.
- Add that URL to the front of the signing certificate and use
a tool (for example,
postman) to invoke the REST APIs. For example:https://identity_domain_URL.identity.oraclecloud.com/admin/v1/SigningCert/jwk - Perform a GET call to retrieve the payload of
the signing keys. There are two sections in the payload:
- Identity domain signing key
- Certificate authority (CA) signing key
Examples of the type of response you receive are provided. See Retrieve the Tenant's Signing Certificate in JWK Format.
- Copy both signing key sections into separate
files. Note that the headers and footers in the files must be in the
following exact format to be successfully uploaded to Oracle Fusion
Applications:
-----BEGIN CERTIFICATE----- content_of_signing_key . . . . . . -----END CERTIFICATE-----You can validate the content. For example:openssl x509 -in identity.cert -noout -text
- Get the REST API of the identity domain endpoint that gives
you the signing certificate endpoint. For
example:
- File a service request (SR) with Oracle Fusion Applications Support
that includes the following details:
- SR Summary: Set Up Trust Between Oracle Fusion Applications and OCI Identity Domain
- Category: Login, Logout and SSO
Attach your certificates for upload. You cannot upload the certificates yourself.
- Create a resource application in an Oracle Integration identity domain to represent the Oracle Fusion Applications
resource.
- Log in to the identity domain as the domain administrator.
- In the navigation pane, click Identity & Security.
- Click Domains.
- Select your compartment.
- Click the identity domain.
- In the navigation pane, click Integrated applications.
- Click Add application.
- Select Confidential Application, then click Launch workflow.
- Provide a name (for example,
FA Resource), and click Submit. - Click the OAuth configuration tab, then the Edit OAuth configuration subtab.
- In the Resource server configuration section, click Configure this application as a resource server now.
- (Optional) In the Configure application APIs that need to be OAuth protected section, select a value from the Access token expiration (seconds) list.
- Click the Allow token refresh toggle.
- In the Refresh token expiration (seconds) list, select a value.
- In the Primary Audience field, add
the Oracle Fusion Applications URL and port. This is the primary
recipient where the token is
processed.
https://FA_URL:443 - Click the Add scope toggle, then click Add.
- In the Scope field, enter
/. - In the Description field, enter All.
- Select Requires user consent.
- Click Add, then click Submit.
- From the Actions menu at the top, select Activate, and then Activate application to activate the client application for use.
(Optional) Create a Local User
Note:
The following step is required if the Oracle Fusion Applications user is not federated with an identity domain or whichever identity provider you are using.- Create an identity domain local user. Carefully review the
following table to see if you already have a local user.
Scenario Do I Need to Create a Local User? You have an Oracle Fusion Applications user federated with the identity domain that is protecting Oracle Integration. No. You do not need to create the local identity domain Oracle Fusion Applications user. This is because identity domain already has Oracle Fusion Applications users in its repository.
You do not have federation between Oracle Fusion Applications and the identity domain that is protecting Oracle Integration. Yes. You must create the local identity domain Oracle Fusion Applications user that you plan to use with the OAuth setup in Oracle Integration.
The identity domain administrator must create a nonfederated local username in the identity domain that matches the user in Oracle Fusion Applications. If you have already used and invoked Oracle Fusion Applications REST endpoints, you likely already created a user with the necessary roles and accesses to invoke the REST endpoints of Oracle Fusion Applications. This user must be created in the identity domain and have a local user password.
Create the Confidential Client Application for Oracle Integration
- Sign in as the identity domain administrator to the Oracle Cloud Console.
- In the navigation pane, click Identity & Security.
- Click Domains.
- Select your compartment.
- Click the identity domain.
- In the navigation pane, click Integrated applications.
- Click Add application.
- Select Confidential Application, then click Launch workflow.
- Enter a name. The remaining fields on this page are optional and can be ignored.
- Click Submit.
- Click the OAuth configuration tab, then the Edit OAuth configuration subtab.
- In the Client configuration box, select Configure this application as a client now.
- For the authorization code, select Refresh token and Authorization code in the Allowed grant types section.
- In the Redirect URL field, enter the
redirect URL of the client application. After user login, this URL is redirected
to with the authorization code. You can specify multiple redirect URLs. This is
useful for development environments in which you have multiple instances, but
only one client application due to licensing issues. For example:
Note:
If you don't know the following information, check with your administrator:
- If your instance is new or upgraded from Oracle Integration Generation 2 to Oracle Integration 3.
- The complete instance URL with the region included (required for new instances).
For Connections… Include the Region as Part of the Redirect URL? Example of Redirect URL to Specify… Created on new Oracle Integration 3 instances Yes. https://OIC_instance_URL.region.ocp.oraclecloud.com/icsapis/agent/oauth/callbackCreated on instances upgraded from Oracle Integration Generation 2 to Oracle Integration 3
No. This applies to both:
- New connections created after the upgrade
- Existing connections that were part of the upgrade
https://OIC_instance_URL.ocp.oraclecloud.com/icsapis/agent/oauth/callbackFor the OAuth authorization code to work, the redirect URI must be set properly.
- Click the Add scope toggle, then click
Add.
If the Oracle Fusion Applications instance is federated with the identity domain, the Oracle Integration cloud service application is listed among the resources for selection. This enables the client application to access Oracle Integration.
- Search for the Oracle Fusion Applications resource application created in Set Up Trust Between Oracle Fusion Applications and an Identity Domain.
- Find and expand the resource.
- Select the scope, then click Add.
- Click Submit.
The details page shows the client ID and client secret values.
- Copy and save these values. You need this information when creating
a connection for the OAuth Authorization Code Credentials security policy on the
Connections page.
Note the following details for successfully authenticating your account on the Connections page.
If The... Then... Identity domain safeguarding Oracle Integration and the Oracle Fusion Applications resource application are the same. Log in to Oracle Integration using the local Oracle Fusion Applications user created earlier. You must create a connection and click Provide Consent on the Connections page for authentication to succeed. Identity domain safeguarding Oracle Integration and the Oracle Fusion Applications resource application are different. Log in to Oracle Integration using a general Oracle Integration developer account, create a connection, and click Provide Consent on the Connections page. You need to log in to the Oracle Fusion Applications resource identity domain application using the local Oracle Fusion Applications user account created earlier. - From the Actions menu at the top, select Activate, and then Activate application to activate the client application for use.
Avoid Potential Errors When Testing Your Connection with a Nonfederated User Account
After you configure the OAuth Authorization Code Credentials security policy on the Connections page, you must test your connection.
If you are logged in to Oracle Integration with an Oracle Integration
user account and click Provide Consent to test the OAuth
flow, consent is successful. However, when you test the connection, it fails with an
Unauthorized 401 error.
- Log out of Oracle Integration and log back in with a user account that exists in Oracle Fusion Applications.
- Return to the Connections page and retest the connection.
The connection is successful this time.
Verify the Status of Location-Based Access Control (LBAC)
Check if you have enabled Location-Based Access Control (LBAC) for Fusion Applications (for Oracle HCM Cloud).
If LBAC is enabled, you must allowlist (explicitly allow identified
entities access) the Oracle Integration NAT Gateway IP address in your LBAC. If you
do not perform this task, you can receive a 401 Access Denied error
or 403 Forbidden error from Oracle Fusion Applications.
See How Location-Based Access Works in Securing SCM and Doc ID 2615294.1 at Oracle Support Services.
Perform Prerequisites to Use the JWT User Assertion Security Policy
You must perform prerequisites to use the JWT User Assertion security policy.
Configure a Confidential Application to Use the JWT User Assertion Security Policy
You must generate a private key and configure a confidential application to use the JWT User Assertion security policy.
See Prerequisites for JWT User Assertion in Using the REST Adapter with Oracle Integration 3.
Configure JWT Assertions for Outbound Use
Perform the following prerequisites to use JWT assertions.
- Take the private key you generated in Configure a Confidential Application to Use the JWT User Assertion Security Policy and upload it on the Certificates page. See Upload a Certificate to Connect with External Services.
The service provider typically provides instructions on how to generate the signing keys and the format. For an example, see Required Keys and OCIDs.
- Create the JWT header and JWT payload JSON files. You upload
both files on the Connections page when configuring the adapter to support
JWT assertions.
Note the following details about the JWT payload JSON file:
- The
iss,exp,sub, andaudclaims are mandatory. Oracle Integration validates that these claims are present. Anything else you upload depends on the provider you are trying to call. For example, NHS may require additional claims. - The
iat(issued at),exp(expiry),nbf(not before), andjti(JWT ID) claims are dynamically calculated if present in the JWT payload JSON file. If you manually provide values for these claims, they are replaced with dynamically-calculated values. - Any remaining claims are optional and depend upon the provider you are calling.
For example:
JWT Header JSON File Example JWT Payload JSON File Example { "alg" : "RS256", "typ": "JWT", "kid": "fajwt2" }Where:
alg: The algorithm to use.typ: A JWT assertion typically set toJWT.kid: A key identifier that is uniquely-generated and associated with the uploaded signing key.
{ "iss": "f6c9d437eed64e2a8f2b045e39e2e03f", "sub": "admin.user", "aud": "https://identity.oraclecloud.com/", "exp": "1739412427" "iat": "1727372629" "jti": "12345" }Where:
- JWT issuer (
iss): A unique identifier for the entity that issued the assertion. This is typically the entity that holds the key material used to sign or integrity-protect the assertion. Examples of issuers are OAuth clients (when assertions are self-issued) and third-party security token services. If the assertion is self-issued, the issuer value is the client identifier (client_id). If the assertion was issued by a security token service (STS), the issuer must identify the STS in a manner recognized by the authorization server. The assertion must contain an issuer. - JWT subject (
sub): The subject typically identifies an authorized accessor for which the access token is being requested (that is, the resource owner or an authorized delegate). In some cases, this may be a pseudo anonymous identifier or other value denoting an anonymous user. When the client is acting on behalf of itself, the subject must be the value of the client'sclient_id. The assertion must contain a subject. - JWT audience
(
aud): A value that identifies the party or parties to process the assertion. The assertion must contain an audience that identifies the authorization server as the intended audience. The authorization server must reject any assertion that does not contain its own identity as the intended audience (in this case, for an Oracle Cloud Infrastructure Identity and Access Management identity domain,https://identity.oraclecloud.com/). - Expires at (
exp): The time at which the assertion expires. While the serialization may differ by assertion format, the time must be expressed in UTC format with no time zone component. The assertion must contain an expires-at entity that limits the window during which the assertion can be used. The authorization server must reject expired assertions (subject to allowable clock skew between systems). The authorization server may reject assertions with an expires-at attribute value that is unreasonably far in the future. - Issued at (
iat): The time at which the JWT was issued. - JWT identifier
(
jti): A unique identifier for the JWT. This helps to prevent replay attacks and ensures the token is only used once.
- The
Specifying the Oracle HCM Cloud Service Catalog Service WSDL or Event Catalog URL
You must specify a mandatory Oracle HCM Cloud service catalog service WSDL (for accessing business objects) and optionally an event catalog URL (for accessing event subscriptions).
Obtaining the Oracle HCM Cloud Catalog Service WSDL
| WSDL Requirements | Where Do You Get the WSDL |
|---|---|
|
The URL must be that of a service catalog service WSDL. The service catalog service enables clients to retrieve information about all public Oracle Fusion Application service endpoints available for that instance. The information it returns is specific to the particular cloud instance and also reflects the new services that may have been introduced in patches applied to the instance. This service is used to programmatically discover the SOAP services available on the cloud instance and retrieve the necessary metadata to invoke the SOAP services to manage business objects. |
The developer creating an Oracle HCM Cloud connection must work with the Oracle HCM Cloud service administrator to get the concrete WSDL URL for the service catalog service provisioned for the specific SaaS application. The concrete WSDL URL must be supplied while creating the connection. |
Prerequisites
This section describes how to derive the external virtual host and port for a tokenized service WSDL. The topology information in the Topology Registration setup task contains the external virtual host and port for the domains and applications. The following instructions describe the steps for deriving the values using the service catalog service WSDL URL as an example: https://atf_server:port/fndAppCoreServices/ServiceCatalogService.
To access the Review Topology page, the ASM_REVIEW_TOPOLOGY_HIERARCHY_PRIV entitlement must be granted to the user's job role. The entitlement is granted to the ASM_APPLICATION_DEPLOYER_DUTY duty role, which is inherited by the duty roles ASM_APPLICATION_DEVELOPER_DUTY and ASM_APPLICATION_ADMIN_DUTY.
If the menu items and tasks described in the following procedure are not available in your cloud instance, your user account is missing the required role. Contact your cloud instance security administrator for assistance.
-
Log in to the cloud instance.
-
Click the Navigator icon in the global area in the top part of the window, then chose Setup and Maintenance under the Tools heading.
-
Select Review Topology under the Topology Registration section in the Tasks regional area on the left side of the window.
-
Click the Detailed tab in the middle of the window.
The tab shows the list of domains configured in the cloud instance.
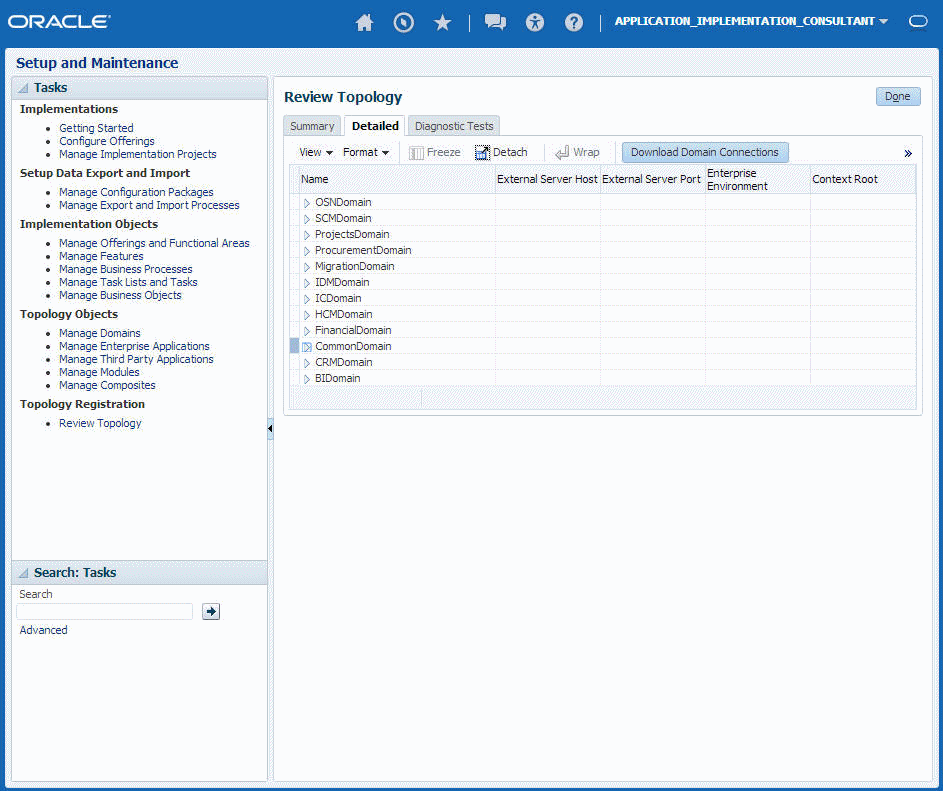
Description of the illustration osc_get_wsdl_detals.png -
Map the token name for the service path value to the domain name in the Topology Manager:
Token Name in Service Path Domain Name atf_server CommonDomain crm_server CRMDomain fin_server FinancialDomain hcm_server HCMDomain ic_server ICDomain prc_server ProcurementDomain prj_server ProjectsDomain scm_server SCMDomain -
Expand the domain name and select any external virtual host and port for the J2EE applications that are deployed on the domain. In the sample window, the values for this particular instance are fs-your-cloud-hostname and 443, respectively.
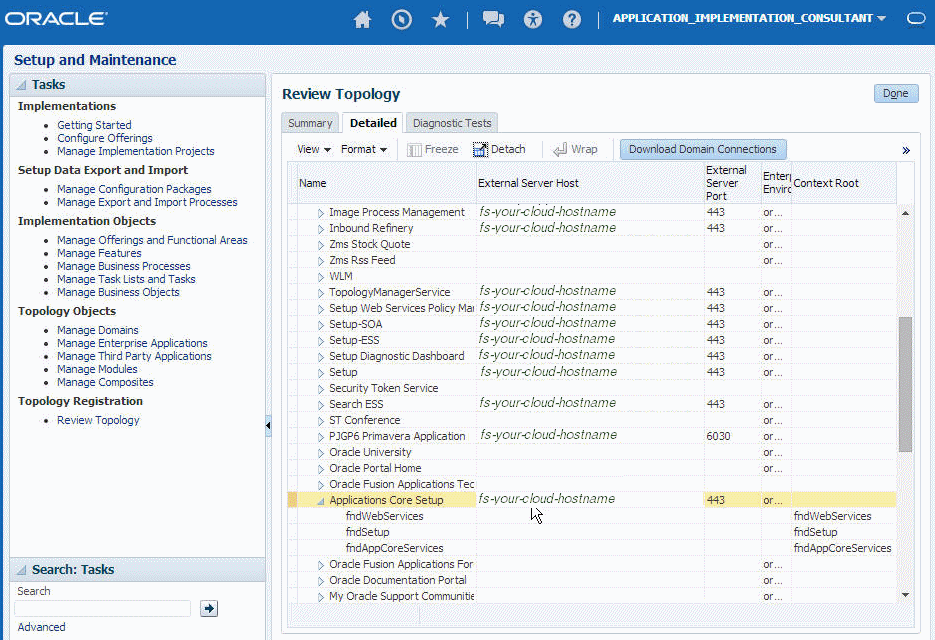
Description of the illustration osc_get_wsdl_detals2.png -
Replace the
domainName_server:PortNumberwith the external virtual host and port identified in the previous step. For example:https://fs-your-cloud-hostname:port/fndAppCoreServices/ServiceCatalogService?wsdl
Obtaining the Event Catalog URL
You must know the CRM URL format to access the CRM application user interface. Follow the URL format to determine the event catalog URL. For example, if the CRM URL format is:
https://fusxxxx-crm-ext.us.oracle.com/customer/faces/CrmFusionHomeThen the event catalog URL is:
https://fusxxxx-crm-ext.us.oracle.com/soa-infraFor Fusion Applications Releases 10 Through 12
Obtain the Oracle Fusion Applications Releases 10 through 12 service catalog service WSDLs and interface catalog URLs through the following methods.
Obtain the Service Catalog Service WSDL for Releases 10 Through 11
| WSDL Requirements | Where Do You Get the WSDL? |
|---|---|
|
The URL must be that of a service catalog service WSDL. The service catalog service is a Fusion Application service that returns a list of external services available for integration. It allows clients to retrieve information about all public Fusion Application service endpoints available for that instance. The service catalog service enables clients to retrieve information about all public Oracle Fusion Application service endpoints available for that instance. The information it returns is specific to the particular cloud instance and also reflects the new services that may have been introduced in patches applied to the instance. This service is used to programmatically discover the SOAP services available on the cloud instance and retrieve the necessary metadata to invoke the SOAP services to manage business objects. |
The developer creating an Oracle HCM Cloud connection must work with the Oracle HCM Cloud service administrator to get the concrete WSDL URL for the service catalog service provisioned for the specific SaaS application. |
This section describes how to derive the external virtual host and port for a tokenized service catalog service WSDL. The topology information in the Topology Registration setup task contains the external virtual host and port for the domains and applications. The following instructions describe the steps for deriving the values using the service catalog service WSDL URL as an example: https://atf_server:port/fndAppCoreServices/ServiceCatalogService.
To access the Review Topology page, the ASM_REVIEW_TOPOLOGY_HIERARCHY_PRIV entitlement must be granted to the user’s job role. The entitlement is granted to the ASM_APPLICATION_DEPLOYER_DUTY duty role, which is inherited by the duty roles ASM_APPLICATION_DEVELOPER_DUTY and ASM_APPLICATION_ADMIN_DUTY.
If the menu items and tasks described in the following procedure are not available in your cloud instance, your user account is missing the required role. Contact your cloud instance security administrator for assistance.
-
Log in to the cloud instance.
-
Click the Navigator icon in the global area in the top part of the window, then chose Setup and Maintenance under the Tools heading.
-
Select Review Topology under the Topology Registration section in the Tasks regional area on the left side of the window.
-
Click the Detailed tab in the middle of the window.
The tab shows the list of domains configured in the cloud instance.

Description of the illustration osc_get_wsdl_detals.png -
Map the token name for the service path value to the domain name in the Topology Manager:
Token Name in Service Path Domain Name atf_server CommonDomain crm_server CRMDomain fin_server FinancialDomain hcm_server HCMDomain ic_server ICDomain prc_server ProcurementDomain prj_server ProjectsDomain scm_server SCMDomain -
Expand the domain name and select any external virtual host and port for the J2EE applications that are deployed on the domain. In the sample window, the values for this particular instance are fs-your-cloud-hostname and 443, respectively.

Description of the illustration osc_get_wsdl_detals2.png -
Replace the
domainName_server:PortNumberwith the external virtual host and port identified in the previous step. For example:https://fs-your-cloud-hostname:port/fndAppCoreServices/ServiceCatalogService?wsdl
Obtain the Service Catalog Service WSDL For Release 12
-
Log in to the Fusion Applications home page. For example:
https://acme.fs.us2.oraclecloud.com/homePage/faces/FuseWelcomeWhere
acmeis the system name andfsis a Fusion Applications domain. -
Copy
https://acme.fs.us2.oraclecloud.com/and appendfndAppCoreServices/ServiceCatalogService?WSDL. For example:https://acme.fs.us2.oraclecloud.com/fndAppCoreServices/ServiceCatalogService?WSDL
Obtain the Interface Catalog URL
The interface catalog URL takes the following format:
https://fusxxxx-fs-ext.us.oracle.com/helpPortalApi/otherResources/latest/interfaceCatalogsFor Fusion Applications Releases 13 and Later
Obtain the Oracle Fusion Applications Release 13 and later service catalog service WSDLs and interface catalog URLs through the following methods.
Obtain the Service Catalog Service WSDL
-
Log in to the Fusion Applications home page. For example:
https://acme.fa.us6.oraclecloud.com/fscmUI/faces/FuseWelcomeWhere
acmeis the system name andus6is the data center. -
Copy
https://acme.fa.us6.oraclecloud.com/and append it withfscmService/ServiceCatalogService?WSDL. For example:https://acme.fs.us2.oraclecloud.com/fscmService/ServiceCatalogService?WSDL
Obtain the Interface Catalog URL
The interface catalog URL takes the following format:
https://fusxxxx-fa-ext.us.oracle.com/fscmRestApi/otherResources/latest/interfaceCatalogs