Before You Begin: Key Prerequisites for Configuration
Oracle Access Governance REST API leverages OAuth 2.0 protocol as its authorization framework. Authentication and Authorization in Oracle Access Governance APIs is managed by OCI IAM Authorization REST APIs. Before generating an access token, you need to configure an OAuth Application in your OCI IAM for generating an Authorization token and assign an application role.
Understanding Grant Types to Invoke REST APIs
Interactive Authentication requires a user to enter credentials to authenticate and authorize before invoking a REST API, while Non-interactive logins use an automated process without a direct user input.
| Grant Type | Interactive | Comments |
|---|---|---|
| Client Credentials | No | Uses client id and client
secret to authorize and generate access token for
invoking REST APIs. Here, you would use confidential applications'
credentials assigned with an appropriate Oracle Access Governance
role.
|
| Authorization Code | Yes | Uses authorization server to authenticate and fetch authorization
code. You must configure a redirect URL for the application.
This method uses user's to access REST APIs and perform specific functions securely. In this process, the user first enters their credentials in the browser, which are validated by the authorization server. The server sends an authorization code to the configured redirect URL. The client application (Confidential Application) then exchanges this code with the authorization server by providing its client credentials. Once validated, the server issues an access token, which the client can then use to securely invoke the REST API. |
Resource Owner password |
No | Uses application username and
password to generate the access token. This
method doesn't support multi-factor authentication (MFA).
|
Step 1: Configure a Network Perimeter
Network perimeters enhance security by defining IP address boundaries and blocking suspicious IP addresses to prevent unauthorized access. This is an optional configuration but highly recommended to restrict login attempts to specific IPs or ranges, and ensure trusted access for users.
- Open your web browser and navigate to https://cloud.oracle.com.
- Enter the name of your Cloud Account Administrator in the Cloud Account Name field and click Next.
- On the Cloud Infrastructure sign-in page, enter your sign-in credentials under Oracle Cloud Infrastructure Direct Sign-In. Click Sign In.
- Complete the multi-factor authentication (MFA) verification for your cloud account.
- Navigate to Identity & Security, and click Domains.
- Choose a compartment where your Oracle Access Governance service instance is located, and then select the domain.
- On the Identity domain page, select Security→ Network Perimeters.
- Select Create network perimeter.
- Enter meaningful name. For example,
Allowed IP List for AG REST API. - In the IP addresses field, specify the range using CIDR notation or
comma-separated list. For
example
192.168.1.1-192.168.1.50, 10.0.0.1-10.0.0.100, 172.16.5.10-172.16.5.20 - Click Create.
Figure - Configuring Network Perimeter

Step 2: Add Confidential Type Application for Authorization in OCI Identity Domain
To create a new confidential application in your Identity Domain:
- Navigate to Identity & Security, and click Domains.
- Select Domains.
- Click the Integrated applications tab.
- Click Add application.
- Select Confidential Application tile, and then click Launch workflow.
- In the Details page, enter the following:
- Enter name and description for the confidential
application.
For example:
access-governance-rest-api-oauth - Click Submit.
- Enter name and description for the confidential
application.
Step 2a: Edit OAuth configurations
- Select the OAuth configuration tab.
- Select Configure this application as a client now.
- Select Edit OAuth configuration.
- Select the following grant types:
- Client credentials: Use client credentials for non-application role-specific functions, such as fetching details of a resource
- Authorization code: Use Authorization code grant type for role-specific functions that rely on user permissions, such as creating, updating, or deleting a resource. For this, you must enter a redirect URL and select Refresh token for token renewal.
- Refresh token: When an access token expires, user uses the refresh token to request a new one from the authorization server.
- Resource Owner: Not recommended and
doesn't support MFA. Uses username and password to
authenticate and generate an access token. It is meant for performing
role-specific functions that rely on user permissions, such as creating,
updating, or deleting a resource.
Note:
For more information, see Understanding Grant Types to Invoke REST APIs.
- Enter Redirect URL in the following
format:
For example, for Postman your redirect URL may be something like:https://AUTH_SERVICE/oauth2/v1/authorizehttps://oauth.pstmn.io/v1/callback - Enable the Add resources toggle button.
- Click Add scope. A list of available application, including Oracle Access Governance service instances and the scope are displayed.
- Select Oracle Access Governance application and scope, and then click
Add.
Figure - Configuring OAuth Application by setting Resource Application and Scope
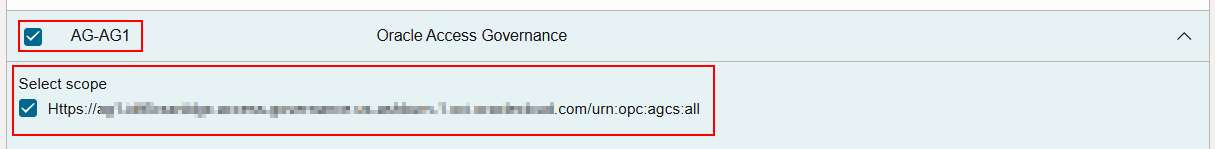
- Click Submit.
Step 3: Activate the Application
Click the Actions icon and then select Activate. The status should change from Inactive to Active.
Step 4: Assign Application Role to the OAuth Confidential Application
Note:
Perform this step only for Non-interactive authentication methods, such as client credentials and Resource Owner.- In your cloud account, go to Identity & Security → Domains.
- Choose a domain.
- Select the Oracle Cloud Services tab.
- Select the Oracle Access Governance service instance.
- Select the Application roles tab.
- Click the Actions icon, and select Manage applications.
- Select the Assign applications button.
- Select the application created in Step 2 and click
Assign.
Result: The application role is displayed under the App roles section of the OAuth configuration tab for the application created in Step 2.
Figure - Verify Application Role Assignment in the OAuth Application
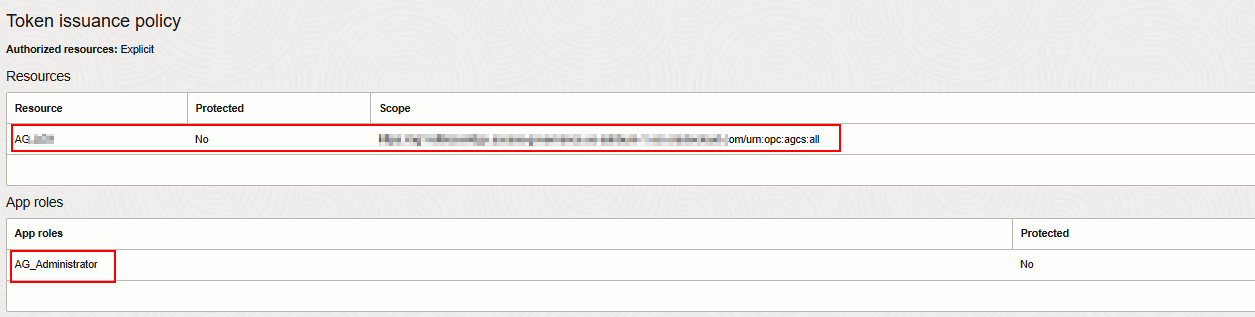
Note:
Refer to Authenticate and Authorize to generate OAuth access token using the client ID and client secret of this application.