Introduction
Tunnel Session Management (TSM) improves firewall traversal for real time communications for OTT VoIP applications and reduces the dependency on SIP/TLS and SRTP by encrypting access-side VoIP within standardized VPN tunnels. As calls or sessions traverse a TSM tunnel, the Oracle Communications Session Border Controller (OCSBC) will route all SIP and RTP traffic from within the TSM tunnel to the core (or appropriate destination).
Oracle Communications is working with other telecom providers and vendors to standardize TSM. Within the 3GPP, TSM is called a Tunneled Services Control Function (TSCF). Currently the 3GPP Technical Requirement draft is TR 33.8de V0.1.3 (2012-05) as a standardized approach for overcoming non-IMS aware firewall issues with supporting companies including China Mobile, Ericsson, Huawei, Intel, RIM, Vodafone, and ZTE. Beyond the standard, we provide exceptional tunnel performance & capacity within the OCSBC as well as high availability, DDoS protection and our patented TSM Tunnel Redundancy to improve audio quality in lossy networks such as the Internet.
Figure 1-1 Basic TSM Setup
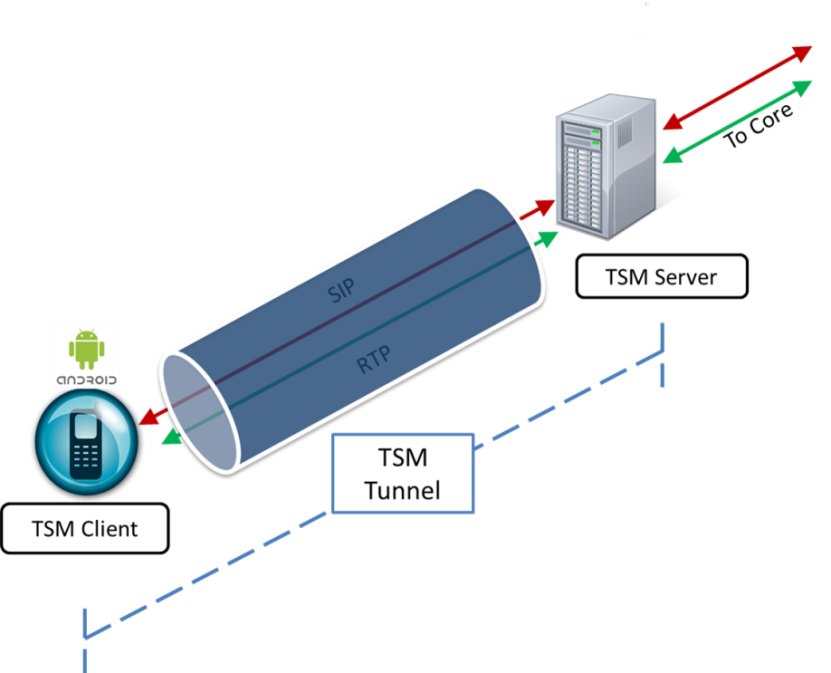
- the TSM server (often referred to as a TSCF or Tunneled Services Control Function)
- the TSM client
To deploy TSM-enabled clients such as softphones, SIP-enabled applications or contact center agent applications, customers and 3rd party ISVs will need to incorporate the open source TSM software libraries into their applications which will establish tunnels to the TSM server.
TSM Tunnel
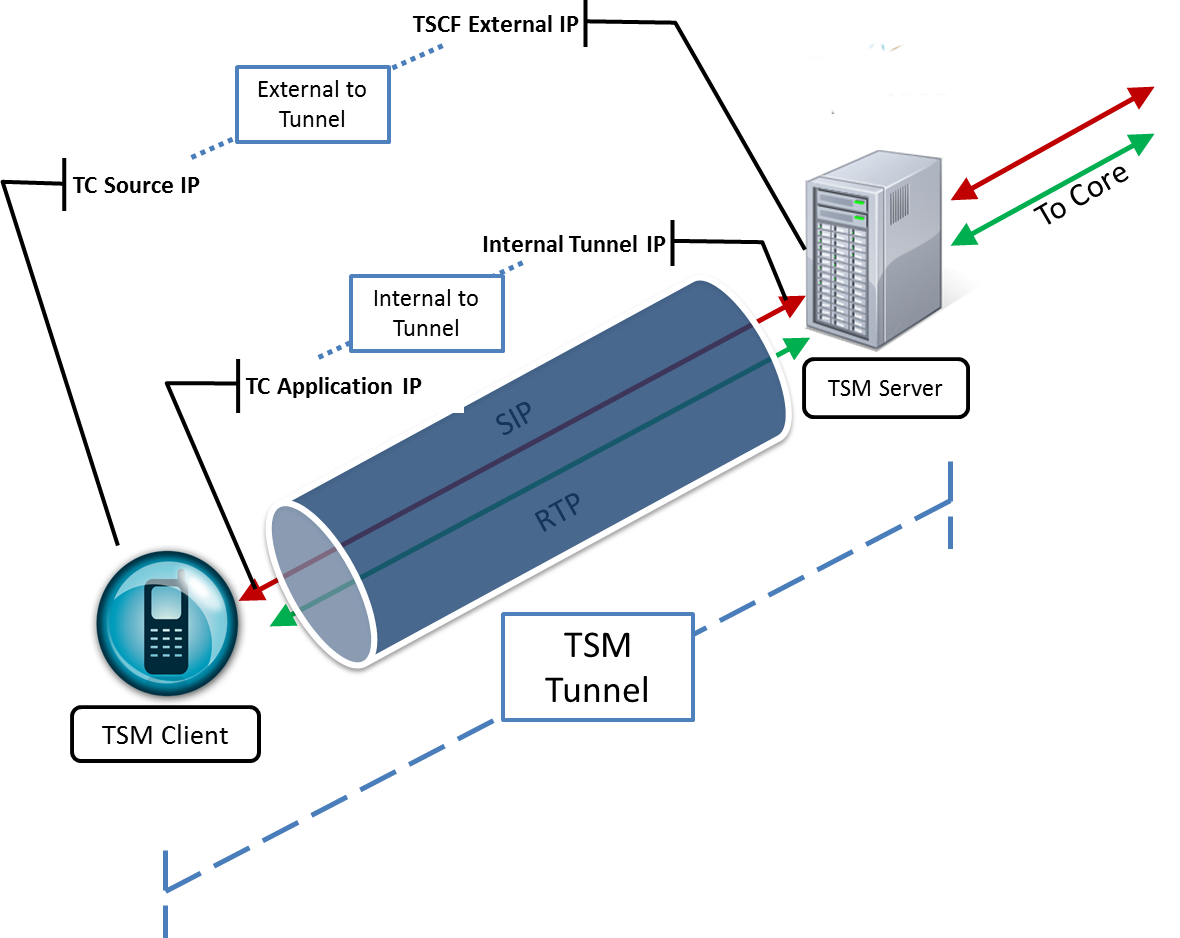
The following diagram briefly explains the various IP addresses utilized during the TSM session.
- TSCF External IP—This IP address is visible to any endpoint on the Internet and is used to initiate the TSM session between the TC and the TSCF. This may be configured under . See the TSCF chapter in the ACLI Configuration Guide to configure the TSCF function on the server.
- TC Source IP—This IP address corresponds to the source address of the TC in its respective access network or it could be the IP of the Proxy behind which it is located.
- Internal Tunnel IP—This IP address will be assigned to the TC (once TLS authentication is successful) from a configured pool of IP addresses on the TSCF. It will be used to facilitate communication with the core (P-CSCF). The address pool can be configured under .
- TC Application IP—This is the IP address associated with the respective application (SIP / RTP / other) at the TC. This is the same as the Internal Tunnel IP.
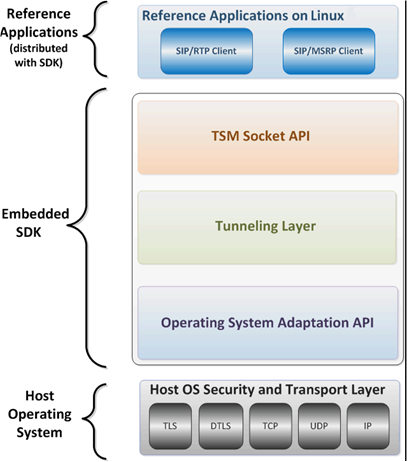
SDK Host Operating System Relationship
The following illustrations depict the relationship between the SDK and the host operating system:
Figure 1-2 SDK/Host OS Relationship (Simplified View)
Provided Functionality
Operating Systems Support
This SDK release supports the following operating systems:
- Linux flavors (using GCC version 4.4.7 or 4.8.5)
- Android 9 Pie (64-bit)
- iOS 12
Platform Support
This SDK supports any platform running S-CZ8.3.0.
Proxy Support
This SDK release supports the following proxy authentication types:
- Basic
- Digest
- NTLMv2
- SPNEGO
If proxy authentication is enabled, the SDK will try to use SPNEGO authentication. If that fails, the SDK tries to use NTLMv2.
Additional Features
- On-the-fly integration of downloaded OpenSSL with TSCF libraries.
- Server Assigned Configuration mode
- Security Traversing Gateway (STG)
- Payload multiplexing within a tunnel
- Each SDK
instance can support:
- Up to 3 concurrent voice calls
- Up to 10 MSRP chat sessions
- 1 MSRP file transfer session
- Tunnel Transport
- TCP
- UDP
- TLS
- DTLS
- IP version
- IPv4
- IPv6
Note:
When used in Decoupled Mode, the TSCF also supports mixing IPv4 and IPv6. For example, you can use an IPv6 external address outside the tunnel and an IPv4 address inside the tunnel, or vice versa.