
| Download Docs | |
|
|
| bea.com | products | dev2dev | support | askBEA |
 |
 |
|
| e-docs > WebLogic Integration - Business Connect > Using WebLogic Integration - Business Connect > Keys and Certificates |
|
Using WebLogic Integration - Business Connect
|
Keys and Certificates
WebLogic Integration - Business Connect offers true security by providing authentication, confidentiality, integrity and non-repudiation of documents. WebLogic Integration - Business Connect uses state-of-the-art cryptography to ensure the security of the documents you exchange over the public Internet. The following topics are provided.
Concepts
Windows
Procedures
These topics provide the information you need to:
What Is PKI?
WebLogic Integration - Business Connect supports public key infrastructure (PKI) to securely trade business documents over the Internet. PKI is a system of components that use digital certificates and public key cryptography to secure transactions and communications.
PKI uses certificates issued by certificate authorities (CAs) to provide authentication, confidentiality, integrity and non-repudiation of data. The following defines these in more detail.
PKI Options There are two PKI options, and WebLogic Integration - Business Connect supports both. They are self-signed certificates and commercial PKIs. The option you choose can depend on a number of factors, such as cost, human and system resources and the degree or sophistication of security desired. Self-signed certificates generated by WebLogic Integration - Business Connect and certificates generated by commercial PKIs all support the X.509 standard for public key certificates. You can use any X.509 certificate, regardless of the source, in document transactions with partners. For example, you can generate a self-signed certificate for your company profile and export a public encryption key in a certificate with the profile to a partner for use in encrypting and signing documents sent to you. Meanwhile, you can engage in trading with partners who have sent you public keys in Entrust or VeriSign certificates. The following sections explain each security option in more detail. Self-Signed Certificates WebLogic Integration - Business Connect can generate root certificates in which you are, in effect, acting as your own certificate authority. WebLogic Integration - Business Connect supports single-key pair self-signed certificates for both encrypting and signing documents and dual-key pair self-signed certificates in which one certificate is used for encrypting and the other for signing. Self-signed certificates are easy to make and use. They are best suited for use within relatively small trading groups. This is because you must implicitly trust a partner's self-signed certificate; there is no chain of trust to independently vouch for the certificate. Such a trust relationship can more suitably be managed among a small number of partners. Although self-signed certificates can provide a high-degree of security, the degree is dependent on the vigilance and administrative skills of the persons managing them. Generally speaking, the use of self-signed certificates does not have the rigorous discipline and orderly structure inherent to a commercial PKI. Commercial PKIs A commercial PKI is an organization set up for the centralized creation, distribution, tracking and revocation of keys for a potentially large community of partners. A commercial PKI has a documented certificate policy (CP) that indicates the applicability of a public key certificate to a specific community or class of application with common security requirements. A commercial PKI also has a certification practice statement (CPS), which details the practices the CA follows for issuing public key certificates. There are two types of commercial PKIs:
The Role of Trust in PKI PKI establishes digital identities that can be trusted. The CA is the party in a PKI responsible for certifying identities. More than generating a certificate, this entails verifying the identity of a subscriber according to established policies and procedures. This is the case for in-house and outsourced PKIs. In an organization that generates and uses its own self-signed certificates, the trading parties must verify the certificates and establish a direct trust. Once established that an identity or issuer of an identity can be trusted, the trust anchor's certificate is stored in a local trust list. WebLogic Integration - Business Connect has a local trust list for storing and managing established trust relationships (select Tools Scalability The use of self-signed certificates relies on users to exchange certificates and establish trust in each other. This informal web of trust works for small groups, but can become unmanageable for large numbers of partners. In contrast, an in-house or outsourced PKI uses hierarchies, where a certificate authority serves as a trust anchor for many users. Once trust has been established for the certificate authority, it is unnecessary to re-establish the trust for other certificates the CA issues. Establishing hierarchies of users scales equally well for small and large groups. Certificate Revocation A certificate is expected to be usable for its entire validity period. However, there are circumstances when a certificate should no longer be considered valid even though it has not expired. Possible circumstances range from a user name change to suspected compromise of the private key. In such circumstances an in-house or outsourced CA can revoke the certificate. WebLogic Integration - Business Connect can be configured to compare your partners' certificates against lists of revoked certificates issued by CAs. However, self-signed certificates cannot be revoked. You must notify all partners using the certificate that it should no longer be trusted. Dual-Key Pairs Support for two pairs of public-private keys is a fundamental requirement for some PKIs (for example, Entrust). One key pair is for data encryption and the other key pair is for digitally signing documents. Encryption key pairs and signing key pairs are a result of conflicting requirements. One such requirement is to support different algorithms for encryption and digital signature pairs and different validity periods. Another reason is to support data recovery, which requires the private keys for decrypting to be securely backed up, but non-repudiation, which requires the private keys for signing, not to be backed up. There also might be the requirement to support updating encryption key pairs and managing decryption key histories even though this conflicts with the requirement to securely destroy the private key used for signing when updating signing key pairs. Using two key pairs, an encryption key pair and signing key pair, solves these conflicting requirements.
Why Use Encryption and Digital Signatures?
Encrypting and digitally signing documents by using certificates provides WebLogic Integration - Business Connect users with the following assurances about each of their document transmissions:
Figure 7-1 Encrypting a Document Using a Key
WebLogic Integration - Business Connect Encryption Method
WebLogic Integration - Business Connect uses a combination of public-private key encryption, which is also known as asymmetric encryption, and symmetric key encryption. This hybrid system uses the best characteristics of each method and minimizes the shortcomings of each. It follows the widely adopted S/MIME standard for securing messages.
The advantage of symmetric key encryption is that it performs the encryption task more quickly than asymmetric encryption. The advantage of asymmetric encryption is that it allows you to send an encrypted message to a partner who does not hold your secret key.
To use the best of both, WebLogic Integration - Business Connect uses the faster symmetric key to encrypt the document, such as a lengthy EDI transaction set, and the asymmetric key for the smaller task of encrypting the one-time session key. The session key can then be securely included with the message for transmission and allows your partner to decrypt the contents without sharing your secret key.
Note: As noted in Transport Selection Considerations, if you send documents using the HTTPS transport, double encrypting adds only marginally to data security. You can turn off document encryption by clearing the encrypt documents check box on the Partner Profile window Security tab.
Symmetric Key Encryption Algorithms
WebLogic Integration - Business Connect supports RC2, ARCFour, DES, and Triple DES encryption algorithms. The encryption algorithm is used in conjunction with a randomly generated session key to encrypt your document. When you set up a partner profile with WebLogic Integration - Business Connect, you must choose one of these encryption algorithms. WebLogic Integration - Business Connect provides you a full range of choices so that you are capable of trading with whatever algorithm your partner might require. However, when you choose an algorithm, you need to be careful to choose one your trading partner can support.
Symmetric Key Lengths
WebLogic Integration - Business Connect supports several key lengths for the symmetric key you choose. The choice you make depends on which encryption algorithm you choose. If you choose the RC2 or ARCFour algorithm, you can select 40-, 64-, or 128-bit key length. If you choose DES, the default key length is 56 bits. Triple DES, as the name implies, uses a 168-bit key length. As with algorithms, you need to be careful to choose a key length your trading partner can support.
Note: ARCFour is an independently developed algorithm that is interoperable with RSA RC4.
Public-Private (Asymmetric) Key Algorithms
WebLogic Integration - Business Connect uses the RSA cryptosystem for asymmetric encryption and the digital signatures provided by using certificates.
You can use two types of asymmetric RSA keys:
Public-Private (Asymmetric) Key Lengths
WebLogic Integration - Business Connect supports encryption key lengths of 512, 1024, and 2048 bits for the public-private key. You must choose one of these key lengths when you generate or obtain your certificate. You do not need to choose the same key length as your trading partner.
Summary of Algorithms and Key Lengths
To use strong encryption you must ensure that the partner's software supports such strong encryption algorithms and key lengths. The following table summarizes algorithms and key lengths for symmetric and asymmetric keys.
Support for Dual Keys WebLogic Integration - Business Connect supports single- and dual-key certificates. You do not need to do anything different to trade documents with a partner who uses dual keys. When you import the certificates from a partner who uses two keys, both are displayed in the Certificates information viewer. How certificates are used is labeled in the Certificates information viewer as follows:
Encryption and Signing Summary
Described in the simplest terms, WebLogic Integration - Business Connect exchanges encrypted and signed documents in S/MIME format.
WebLogic Integration - Business Connect is certified S/MIME-compliant by RSA Data Security, Inc.
Outbound Documents
The document contains the data that needs to be protected. The encryption and signing processes take place for every document that WebLogic Integration - Business Connect sends over the Internet.
WebLogic Integration - Business Connect encrypts and signs each document by building three parts: the encrypted document, the encrypted session key and the digital signature. The following is the process for an outbound document:
Inbound Documents
When a document is received by your trading partner, the process is reversed according to the following steps.
Certificate Basics
A certificate contains the public half of your public-private key pair along with other identifying information about your WebLogic Integration - Business Connect company profile and point of contact. WebLogic Integration - Business Connect uses certificates to distribute your public key and those of your partners. You use the public key in your partner's certificate to encrypt a document for transmission over the Internet. Your partner uses the public key in your certificate to verify the digital signature of a document received from you.
The following is some basic information about how WebLogic Integration - Business Connect uses certificates:
Where Certificates and Keys Are Stored
WebLogic Integration - Business Connect stores certificates and keys in two files: ConfigDB.db and keys.db. The ConfigDB.db file is in the root application directory. The keys.db file is in the keys subdirectory. The contents of these files are encrypted to ensure security. Do not attempt to alter these files.
The following describes the roles of these two files.
ConfigDB.db
All certificates are stored in ConfigDB.db. Certificates that you choose to trust are copied to keys.db.
keys.db
The public and private keys for your certificates are stored in keys.db. The trusted public keys of your partners and trusted anchors of certificate authorities also are stored in keys.db.
Certificate Status
WebLogic Integration - Business Connect manages certificates by using the following status categories.
Active Certificate (Yellow Bulb) 
A certificate identified with a yellow bulb is the active certificate for your company profile or for your trading partner's partner profile.
You distribute your public key to your trading partners in your certificate. Your trading partners use this key to verify the digital signature of documents they receive from you.
You receive your trading partner's public key in his or her certificate. You use your partner's public key to encrypt documents for transmission over the Internet.
There can be only one active certificate for signature and encryption or one active pair (one for signature, one for encryption) on your system. The active certificate on your system is also the active certificate on your partners' systems.
When you create or obtain a new certificate for your company profile, you can choose to activate it immediately or to save it in Pending status. If you choose to activate it immediately, WebLogic Integration - Business Connect places the active certificate for your profile in Valid status.
If you import your partner's certificate, WebLogic Integration - Business Connect activates it and places the active certificate for that profile in Valid status.
Valid or Inactive Certificate (Blue Bulb) 
A certificate identified with a blue bulb is in the Valid or Inactive state.
A valid certificate is one that was formerly active on your computer. You can have multiple valid certificates on your system.
If WebLogic Integration - Business Connect fails to verify an inbound document using the public key in the active certificate, the application tries again with each of the valid keys. If one of these succeeds, processing proceeds normally and no alert is sent.
An inactive certificate is one that is valid but is not used to verify signatures or to encrypt messages to a partner.
Pending Certificate (Red Bulb) 
A certificate identified with a red bulb is in the Pending state:
In either of the preceding cases, you must use the Certificate Profile window to activate a pending certificate. See Activating a Pending or Valid Certificate.
Retired Certificate (Clear Bulb) 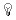
A retired certificate is one that was formerly active or valid. You can have multiple retired certificates on your system.
WebLogic Integration - Business Connect does not use the keys associated with retired certificates to sign, verify, encrypt or decrypt documents.
Exchanging Profiles and Certificates
Before you can exchange encrypted and signed documents with a trading partner, each of you must obtain the other's public key. You do this after you have created your company profile. Each of you generates a self-signed certificate or obtains one from a certificate authority (CA). Either way, the process creates a public-private key pair for your company profile. The private half of this key pair always remains on your computer. The public half is exported to a file and distributed to your trading partners on diskette by a secure means.
The following describes how to exchange profiles and certificates with your WebLogic Integration trading partners. In all cases, it is recommended that you confirm the certificate fingerprint with your trading partner before exchanging documents.
Exchanging Certificate Information with WebLogic Integration Trading Partners
If you are using the Bundled HTTPS transport to exchange messages with a WebLogic Integration trading partner, the certificate information is exchanged as follows:
When you update the certificate associated with your company profile, it is important to coordinate the update process with your trading partners. For guidelines, see Obtaining New and Replacement Certificates.
Self-Signed or CA Certificates
You and your trading partners should decide whether to use WebLogic Integration - Business Connect self-signed X.509 certificates or X.509 certificates from a third-party certificate authority (CA).
If your organization has an Entrust/PKI server and administrator and will use Entrust certificates, see Entrust Certificates.
Consider the following in deciding whether to generate a self-signed certificate or obtain one from a CA:
Entrust Certificates
WebLogic Integration - Business Connect fulfills a client role in supporting the certificate management tasks of an Entrust server. The prerequisites for this client-server relationship are your Entrust server and a person who is designated as your organization's Entrust administrator. Lacking these two requirements, your organization cannot use Entrust certificates in exchanging documents with your trading partners through WebLogic Integration - Business Connect.
WebLogic Integration - Business Connect enables an organization with an Entrust/PKI server to:
WebLogic Integration - Business Connect does not support Entrust certificate revocation or recovery.
WebLogic Integration - Business Connect supports Entrust versions 4 and 5.
The following describes the certificate-generation process involving WebLogic Integration - Business Connect and the Entrust server.
After WebLogic Integration - Business Connect creates the key pair for signing documents, the application hands the public key to the Entrust server. The Entrust server creates the signing certificate and passes the certificate to WebLogic Integration - Business Connect. The public key is within the certificate. WebLogic Integration - Business Connect retains the private signing key. The private signing key is not disclosed to the Entrust server; the private key remains secure within WebLogic Integration - Business Connect. This guarantees security integrity.
Meanwhile, the Entrust server creates the encryption key pair and creates an encryption certificate, which includes the public key. The Entrust server passes to WebLogic Integration - Business Connect the encryption key pair and the encryption certificate.
Obtaining New and Replacement Certificates
You can generate or obtain new certificates when:
Also, by using the Certificates information viewer, you can make sure you and your trading partners keep your certificates current.
Note: WebLogic Integration - Business Connect notifies you when an active certificate associated with an active company profile is about to expire. See Preferences General Tab.
The procedure used depends on whether you are generating or loading a certificate for your company profile, or importing certificate information for one of your partners. See Setting Up Certificates for Your Company Profile or Importing a Partner's Certificate.
When you generate or load a new certificate for your company profile, you must export the certificate information (your public key) to a file for distribution to your partners. See Exporting Your Certificate for Backup or Distribution.
When you generate a new certificate for your company profile because it has expired, become defective or corrupted, or cannot be used for any other reason, we recommend that you distribute it to your trading partners on diskette by a secure means. Recommended secure means include in-person, U.S. mail or private delivery service.
When you generate or load a new certificate for your company profile, you can choose to have WebLogic Integration - Business Connect activate the certificate, or save the certificate in Pending status until a later date. To avoid rejection of documents it is important that you coordinate the process of distributing and activating a replacement certificate. The following topics provide guidelines:
Replacing a Certificate for Non HTTPS Encryption
When you update a non-HTTPS certificate for your company profile (that is, one used to encrypt documents exchanged), you must carefully coordinate the timing of the update with your partners. If possible, you should perform such updates when your server is not processing outbound documents. By observing this precaution you can avoid documents being rejected by your trading partners.
If you create and activate a new certificate while WebLogic Integration - Business Connect is encrypting and signing outbound documents, documents that are signed by the private key associated with the new certificate will be rejected by your trading partners, if they have not yet received and activated the new certificate.
The update process for a non-HTTPS certificate does not affect inbound documents because your WebLogic Integration - Business Connect can decrypt and verify them with the last valid certificate.
Replacing a Certificate for Bundled HTTPS with Authentication
If you have enabled the bundled HTTPS inbound transport, with the authenticate check box selected, you should exercise care when you create and distribute a new certificate. We recommend that you:
It is important to coordinate the update with each partner ahead of time so they avoid sending you any documents until the new certificate has been activated on their system. The reason you must exercise this care is that your bundled HTTPS server can use only the active certificate to authenticate the SSL connection. Likewise, each partner must also hold your current certificate to authenticate the connection with you.
To minimize the number of errors during the process of certificate update, you and your partners should activate the new certificate nearly simultaneously, at a pre-designated time when traffic is at a minimum.
If you implement a new certificate while you are trading documents, your trading partners will not be able to establish the SSL connection required to communicate with you. During this time, your trading partners receive alerts stating that their system cannot connect with you. This situation clears itself up after your partners receive and begin using your new certificate to authenticate the SSL connection.
Certificates Information Viewer
The Certificates information viewer in Administrator enables you to manage certificates for your company and partner profiles. Open the viewer by selecting Certificates on the Administrator bar. To expand or collapse the certificate tree, click the plus or minus signs.
Using the viewer you can:
Figure 7-2 Certificates Information Viewer
Certificate Window
Use the Certificate window to view information about a certificate for a company or partner profile. You also can export a certificate to a file.
To open the window, display the Certificates information viewer. Select the certificate you want and double-click it or click Open.
When you finish viewing the certificate information, click Close. To export the certificate, click Export to display the Export Certificate window. See Exporting Your Certificate for Backup or Distribution.
Figure 7-3 Certificate Window for a Self-Signed Certificate
Field Descriptions The following describes the fields on the Certificate window The information displayed on the window is defined by the X.509 standard.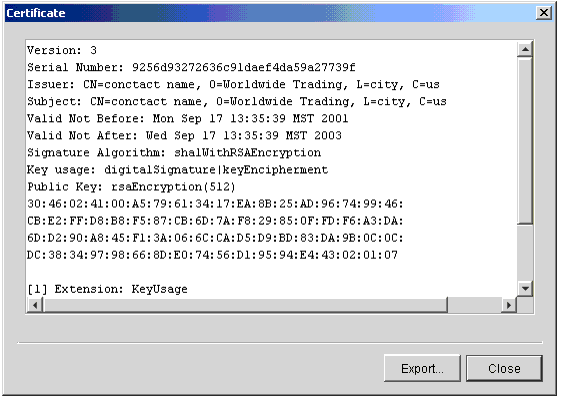
Setting Up Certificates for Your Company Profile
Use this procedure to create new, self-signed certificates for your company profile or to load a new, third-party certificate for your company profile.
If you want to use a certificate from a third-party CA such as VeriSign, you must obtain that certificate using your Internet browser and export it to a file before you begin this procedure. You must export the certificate to a file that contains the private key and the entire chain of trust. You will need the password used to export the file from your browser to load the certificate into WebLogic Integration - Business Connect.
This is not the procedure to use for importing a partner's certificate. See Importing a Partner's Certificate.
Steps
If you want to associate a certificate with an existing company profile, click Certificates on the Administrator bar to display the Certificates information viewer. Select the company you want and click New to start the New Certificate wizard.
Figure 7-4 New Certificate Wizard, Select Certificate Type Window
Generating Self-Signed Certificates
Use this procedure if you selected generate self-signed certificates in step 2 of Setting Up Certificates for Your Company Profile.
The following are the steps for generating and associating with a company profile either a single self-signed certificate for both encrypting and signing documents or two self-signed certificates, one for encrypting and one for signing.
Steps
Figure 7-5 New Certificate Wizard, Select Key Type Window
Figure 7-6 New Certificate Wizard, Summary Window
When you click Finish, a dialog box appears with a message that the certificates are being generated and might take a few minutes to complete.
If there are no other certificates for this company profile, the new certificate is placed in Active status.
If a certificate already exists for this company profile, a dialog box appears asking whether you want to activate the new certificate.
Figure 7-7 Activate Certificate Dialog Box
When this message appears, click Yes or No as follows:
After the certificate is generated, the Company Profile or Certificates information viewer reappears, depending on whether you imported a certificate for a new or existing company profile. The new certificate appears on the Certificates information viewer.
Note: Before you attempt to exchange encrypted and signed documents, you should contact each partner with whom you exchanged certificates and confirm that the fingerprints in both your certificates are identical. For more information see Certificate Window.
Importing Entrust Certificates
Use this procedure if you selected acquire Entrust certificates in step 2 of Setting Up Certificates for Your Company Profile.
The following are the steps for importing a new Entrust certificate into WebLogic Integration - Business Connect or for updating an Entrust certificate that is already associated with a company profile. Before you can use this procedure, you must consult with your organization's Entrust administrator about the information required to connect with the Entrust/PKI server and import a new or updated certificate for your company profile.
Steps
Figure 7-8 New Certificate Wizard, Entrust Server Information Window
Figure 7-9 New Certificate Wizard, Summary Window
If there are no other certificates for this company profile, the new certificate is placed in Active status.
If a certificate already exists for this company profile, a dialog box appears asking whether you want to activate the new certificate.
Figure 7-10 Activate Certificate Dialog Box
When this message appears, click Yes or No as follows:
After the certificate is generated, the Company Profile or Certificates information viewer reappears, depending on whether you imported a certificate for a new or existing company profile. The new certificate appears on the Certificates information viewer.
Note: Before you attempt to exchange encrypted and signed documents, you should contact each partner with whom you exchanged certificates and confirm that the fingerprints in both your certificates are identical. For more information see Certificate Window.
Importing a VeriSign XKMS Certificate
Use this procedure if you selected acquire a VeriSign XKMS certificate in step 2 of Setting Up Certificates for Your Company Profile.
The following are the steps for importing a new XML Key Management Specification (XKMS) certificate into WebLogic Integration - Business Connect and associating it with a company profile. Before you can use this procedure, you must register for a new XKMS certificate from VeriSign. When the new certificate is ready, you will receive an e-mail containing the information needed to connect to a server and import the certificate for your company profile.
XKMS was designed in an effort to combine the interoperability afforded by Extensible Markup Language (XML) in business-to-business electronic commerce with secure and easy to use public key infrastructure (PKI). For information about XKMS see http://xmltrustcenter.org/index.htm.
Steps
Figure 7-11 New Certificate Wizard, VeriSign XKMS Certificate Window
Figure 7-12 New Certificate Wizard, Summary Window
If there are no other certificates for this company profile, the new certificate is placed in Active status.
If a certificate already exists for this company profile, a dialog box appears asking whether you want to activate the new certificate.
Figure 7-13 Activate Certificate Dialog Box
When this message appears, click Yes or No as follows:
After the certificate is generated, the Company Profile or Certificates information viewer reappears, depending on whether you imported a certificate for a new or existing company profile. The new certificate appears on the Certificates information viewer.
Note: Before you attempt to exchange encrypted and signed documents, you should contact each partner with whom you exchanged certificates and confirm that the fingerprints in both your certificates are identical. For more information see Certificate Window.
Importing a Third-Party CA Certificate
Use this procedure if you selected to import from PKCS #12 file in step 2 of Setting Up Certificates for Your Company Profile.
The following are the steps for importing a third-party CA certificate into WebLogic Integration - Business Connect and associating it with a company profile. Such a certificate file contains both the public and private keys. Before you can use this procedure, you must perform the following tasks:
Steps
Figure 7-14 New Certificate Wizard, Third-Party Certificate Window
Figure 7-15 New Certificate Wizard, Summary Window
If there are no other certificates for this company profile, the new certificate is placed in Active status.
If a certificate already exists for this company profile, a dialog box appears asking whether you want to activate the new certificate.
Figure 7-16 Activate Certificate Dialog Box
When this message appears, click Yes or No as follows:
After the certificate is generated, the Company Profile or Certificates information viewer reappears, depending on whether you imported a certificate for a new or existing company profile. The new certificate appears on the Certificates information viewer.
Note: Before you attempt to exchange encrypted and signed documents, you should contact each partner with whom you exchanged certificates and confirm that the fingerprints in both your certificates are identical. For more information see Certificate Window.
Importing a Partner's Certificate
When your trading partner provides a new or updated certificate in a file, use this procedure to import the certificate.
Note: WebLogic Integration - Business Connect automatically places any existing partner certificate in Valid status when it imports a new one. The new certificate is automatically set to Active status.
Steps
Figure 7-17 Import Certificate Window
Figure 7-18 Browse Dialog Box
Figure 7-19 Import Certificate Summary Window
Note: Before you attempt to exchange encrypted and signed documents, you should contact the partner from whom you imported the certificate and confirm that the fingerprints in both your certificates are identical. For more information see Certificate Window.
Exporting Your Certificate for Backup or Distribution
Use this procedure to export a certificate to a file.
When exporting your certificate for distribution to your partners, only export your public key. Never give your partner a certificate that contains your private key.
When exporting your certificate for backup purposes, you can export a certificate that contains your private key. If you do so, keep this certificate in a secure place and never give it to anyone.
After you export a certificate with a public key for distribution to your trading partners, you can send the file to your trading partners by e-mail or on diskette. This is one way to save a certificate to a file. For another way to export a certificate see Viewing Certificate Information.
Steps
Figure 7-20 Export Certificate Selection Window
Figure 7-21 Export Certificate File Name and Path Window
Figure 7-22 Export Certificate Summary Window
Deleting Certificates
Use this procedure to retire certificates that you or your partners no longer use for verifying signatures or encrypting messages.
Retiring a certificate is a pseudo-deleting process that results in its removal from the Certificates information viewer. However, the certificate remains in the system as a dormant entity that can be reactivated if need be. Allowing a certificate to be retired but not deleted is a safeguard for the future in the event a signature must be re-validated or a secure message decrypted again.
This is one way to retire certificates. You also can use the Certificate Profile window for a selected company or partner profile. See Retiring a Certificate.
For the steps to reactivate a certificate, see Un-Retiring a Certificate.
You can view a details window for retired certificates after you have withdrawn them.
Steps
If you click Yes, the certificate no longer appears on the Certificates information viewer.
If you want to verify that the certificate has been retired, select the profile associated with the retired certificate and click Open to open the Certificate Profile window. Select the Retired Certificates tab. The certificate you retired appears on the tab. To view details of the retired certificate, click View Certificate.
Certificate Profile Window
The Certificate Profile window can be opened from the Certificates information viewer. You can use the Certificate Profile window to manage the certificates associated with company and partner profiles. The following topics are provided for using the window.
To open the window from the Certificates information viewer, select the name of the company or partner with the certificates you want and click Open.
The window has two tabs: Available Certificates and Retired Certificates.
Figure 7-23 Certificate Profile Window, Available Certificates Tab
Figure 7-24 Certificate Profile Window, Retired Certificates Tab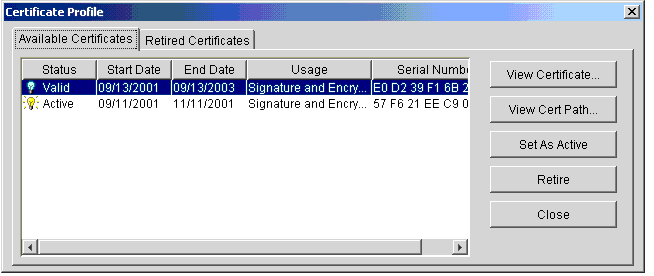
Viewing Certificate Information Use this procedure to view information about a certificate for a company or partner profile. You also can export a certificate to a file. This procedure uses the Certificate window, which is the same one described in Certificate Window, but here you access the window through the Certificate Profile window. See Certificate Profile Window for details about the window. Steps
Figure 7-25 Certificate Window for a Self-Signed Certificate
Viewing the Certificate Path
Use this procedure to view information about a certificate's chain of trust. You also can export a certificate or its trusted roots to a file.
This procedure uses the Certificate Profile window. See Certificate Profile Window for details about the window.
A chain of trust or certificate chain is an ordered list of certificates that includes the certificate of the end-user and certificates of the issuing CA. A trusted root is a public key that is verified as belonging to an issuing CA, which is called a trusted third party.
Steps
Figure 7-26 View Complete Certificate Path Window
Activating a Pending or Valid Certificate
Use this procedure to change the status of pending or valid certificates to active. A profile can have many certificates, but only one active certificate at a time. The active certificate is the one used for document trading.
This procedure uses the Certificate Profile window. See Certificate Profile Window for details about the window.
Steps
Retiring a Certificate
Use this procedure to retire a certificate. This procedure uses the Certificate Profile window and is one way to retire or delete a certificate. For details about inactivating certificates see Deleting Certificates.
For the steps to reactivate a certificate, see Un-Retiring a Certificate.
See Certificate Profile Window for details about the window.
Un-Retiring a Certificate
Use this procedure to change the status of a retired certificate to valid or active.
As explained in Deleting Certificates, certificates you have retired from use are maintained in the system in a dormant state in the event they are needed again. When you un-retire a certificate, its status changes to valid and it appears once more on the Certificates information viewer. After changing the status to valid, you can make the certificate active if you want.
This procedure uses the Certificate Profile window. See Certificate Profile Window for details about the window.
Steps
Trusted Roots
Trusted roots are the foundation upon which chains of trust are built in certificates. Underlying a certificate issued by a certificate authority is a root, self-signed certificate. In WebLogic Integration - Business Connect trusting a CA root means you trust all certificates issued by that CA. Conversely, if you elect not to trust a CA root, WebLogic Integration - Business Connect will not trust any certificates issued by that CA. Document trading fails in WebLogic Integration - Business Connect when a non-trusted certificate is used.
The self-signed certificates you can generate in WebLogic Integration - Business Connect are root certificates. This is because you are, in effect, your own CA when you generate a self-signed certificate.
WebLogic Integration - Business Connect by default trusts your and your partners' self-signed certificates that were generated by WebLogic Integration - Business Connect. WebLogic Integration - Business Connect also by default trusts the roots of many CA-issued certificates. You can, however, specify whether WebLogic Integration - Business Connect should not trust all or some certificates issued by a specific CA. You also can explicitly not trust a partner's self-signed certificate.
The Trusted Roots window displays trusted roots for various certificate authorities. It also displays the self-signed certificates of your partners and the certificates used by the WebLogic Integration - Business Connect SOAP-RPC HTTPS server and API HTTPS server (see Application Security).
Importing a trusted root is a task that rarely, if ever, must be performed. You might have to import a trusted root if, for example, your partner sends you a CA-issued certificate and your system does not have the trusted root for it. In such a case, document trading would fail. As a solution, you would need to import the root underlying the certificate and trust it.
WebLogic Integration - Business Connect can import trusted roots contained in files with the following extensions: .cer, .p7c and .p7b. There are various ways you can obtain such trusted root files:
When you import a trusted root for a certificate to WebLogic Integration - Business Connect, we recommend that you compare the MD5 fingerprints in both the trusted root and the certificate to verify that they match.
Viewing, Editing or Importing Trusted Roots
Use this procedure to specify whether to trust roots, view root details or import trusted roots. For details about trusted roots, see Trusted Roots.
Steps
Self-signed certificates that you have generated in WebLogic Integration - Business Connect for document trading do not display on the window. This is because you must trust your own self-signed certificates created for document trading; you cannot elect not to trust them. However, the self-signed certificates for the SOAP-RPC HTTPS server and API HTTPS server are listed on the window and are trusted by default. See Certificate Tool (certloader).
Figure 7-27 Trusted Roots Window
Using Certificate Revocation Lists
Use this procedure to configure WebLogic Integration - Business Connect to compare your partners' certificates against lists of invalid certificates that are maintained by the issuing certificate authorities.
A certificate revocation list (CRL) is a list of third-party certificates that are no longer valid. Certificate authorities maintain such lists of certificates they issued, but later invalidated for one reason or another. CRLs are accessible on the Internet, and you need an Internet connection for WebLogic Integration - Business Connect to use them.
WebLogic Integration - Business Connect enables you to check your partners' certificates against CRLs. When you direct WebLogic Integration - Business Connect to use CRLs, your partners' certificates are checked each time documents are exchanged. For example, when a partner sends you an encrypted document, WebLogic Integration - Business Connect checks the certificate associated with the inbound document against the CRL. If the certificate is on the CRL, WebLogic Integration - Business Connect rejects the inbound document.
Although using CRLs can enhance security, the checking process can result in longer processing times. Consequently, your decision whether to use CRLs should weigh the security advantage against the performance handicap.
You can configure WebLogic Integration - Business Connect to check certificates against the CRLs of one or more certificate authorities. However, WebLogic Integration - Business Connect checks a specific certificate only against the appropriate CRL. For example, if you configure WebLogic Integration - Business Connect to use CRLs maintained by VeriSign, Inc. and GlobalSign and an inbound document is associated with a VeriSign certificate, the system checks only against the VeriSign CRL and not the GlobalSign CRL.
You are responsible for obtaining from the certificate authority the information required for accessing the CRL. WebLogic Integration - Business Connect downloads the latest CRL in performing certificate checks. It also downloads updates of the CRL, based on the update interval in the previously downloaded CRL.
Steps
Adding CRLs
Do the following on the Certificate Revocation List window to configure WebLogic Integration - Business Connect to use one or more CRLs.
The protocols are hypertext transfer protocol (HTTP) and lightweight directory access protocol (LDAP). For example, VeriSign CRLs are accessed via HTTP and Entrust CRLs are accessed via LDAP.
You can obtain the CRL information by viewing the details of a CA-issued certificate. See Certificate Window. The information, if present, is in the extensions section and is labeled as CRL distribution point.
As an example, the following is the CRL distribution point within a VeriSign certificate. This is a URL as follows:
http://crl.verisign.com/class1.crl
This URL corresponds to the fields on the Certificate Revocation List window as described in the following table.
After you add one or more CRLs and if the Server application is running, the system downloads the CRLs into the crls directory under the WebLogic Integration - Business Connect installation directory. There might be a delay of up to one hour before Server downloads a CRL the first time. This is because the application polls for new CRLs once an hour.
Each CRL contains a refresh date that indicates when the CA updates the list. WebLogic Integration - Business Connect downloads the updated CRL after each refresh date, provided the Update check box next to the CRL is selected.
The Update check boxes next to the CRLs tell WebLogic Integration - Business Connect whether to monitor the refresh dates within the CRLs and download updated CRLs from CAs at the appropriate times. When the Update check boxes are selected, WebLogic Integration - Business Connect downloads the latest available CRLs.
Deleting CRLs
Do the following on the Certificate Revocation List window to delete CRLs.
Turning CRL Checking On and Off
Do the following on the Certificate Revocation List window to turn CRL checking on and off.
|

|

|