









|
This example demonstrates how to configure the security settings for ebXML message exchange between trading partners over HTTPS protocol through a proxy server. Although any proxy server can be used in this configuration, the example demonstrates how to configure the iPlanet Web Server 6.0 (Sun ONE 6.0) as the proxy server. A demonstration version of this server is available for download at http://wwws.sun.com/software/download/products/3f186391.html.
This example involves two trading partners. Trading Partner 1 is configured in WebLogic Integration and Trading Partner 2 is configured in WebLogic Integration - Business Connect as shown in the following figure:
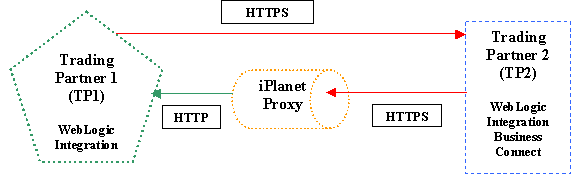
| Note: | In production scenarios, firewalls are usually configured between WebLogic Integration and the proxy server and between the proxy server and WebLogic Integration - Business Connect. To keep the IP addresses simple in this sample, the firewalls are left out of the examples. |
The following topics is discussed in this section:
Using WebLogic Integration - Business Connect
Trading Partner Integration Security
Guide to Building Business Processes
Using WebLogic Integration - Business Connect
The instructions in this sample is geared towards users that are already familiar with WebLogic Integration tasks and procedures.
Before you can configure and run this example, you need to generate a certificate which you will later on import into your WebLogic Integration keystore. Once the certificate is imported into the keystore, you can use it as an encryption, a signature, or a client certificate for WebLogic Integration and also as a WebLogic Server certificate. In a production environment, you would most likely have several certificates, but since this example is for testing only, you use one certificate for both client and server purposes.
You can generate the test certificate using any tool, however, the procedures in this section describe how to generate the certificates using OpenSSL. This is an open source tool which can be downloaded from www.openssl.org.
Before you create the certificate, you need to create the a Public/Private key pair that you then use to create the test certificate. If you are running OpenSSL in a Windows environment, you must first complete the Configuring Windows to Run OpenSSL below, before you can create the key pair.
This step includes the following procedures:
The following steps should be completed to configure your Windows environment to run OpenSSL:
OPENSSL_CONF environment variable to point to the OpenSSL configuration file:
$ set OPENSSL_CONF=c:\openssl-[X.X.X]-src\apps\gencert.conf
Where [X.X.X] is the version of your OpenSSL installation, for example 0.9.7.
| Note: | Due to the fact that Internet Explorer uses files of the type .cnf for Speed Dial configuration files, the OpenSSL configuration file might appear without the .cnf suffix and may have a shortcut icon. |
file1, file2, file3, file4, and file5. These files will be used by the OpenSSL facility to create the public/private key pair.c:\openssl\bin.You are now ready to create a public/private key pair using OpenSSL.
The following section describes how to create 1024-bit RSA public/private key pair using OpenSSL:
In a DOS command window, type the following:
$ openssl genrsa rand file1:file2:file3:file4:file5 out WLCert.key 1024
where file1:file2:file3:file4:file5 represents the five large files you created in Configuring Windows to Run OpenSSL.
You are now ready to create any type of X.509 certificate using OpenSSL.
To generate the self-signed test certificate, complete the following procedure:
Digital certificates are stored in two types of keystores in WebLogic Integration:
This example assumes that you have created your own keystores and trusts. However, you can also complete this example by using the demonstration keystore file (DemoIdentity.jks) and the demonstration trust (DemoTrust.jks) that are part of your WebLogic Server installation and therefore WebLogic Integration installation. These Java Key Store files are located in the following location:
BEA_HOME\weblogic92\server\lib\
where BEA_HOME is the directory in which you installed your product.
Since the underlying server used by WebLogic Integration is the WebLogic Server application, this section demonstrates how to use the WebLogic Server Administration Console to configure the keystores.
From WebLogic Integration, you do this by selecting Tools WebLogic Server
WebLogic Server WebLogic Console.
WebLogic Console.

server_name
Where server_name is the name of your WebLogic Server.The Configure Keystore Properties screen appears.
BEA_HOME\weblogic92\server\lib\DemoIdentity.jks
Where BEA_HOME is the directory in which you installed WebLogic Server.
JKS.Note: This attribute is optional or required depending on the type of keystore. All keystores require the passphrase in order to write to the keystore. Some keystores do not require the passphrase to read from the keystore. Whether or not you define this property depends on the requirements of the keystore. For example, WebLogic Server only reads from the keystore so a passphrase is not required, however, WebLogic Integration writes to keystores and therefore requires a passphrase.
BEA_HOME\weblogic92\server\lib\DemoTrust.jks.
Where BEA_HOME is the directory in which you installed WebLogic Server.
Note: This attribute is optional or required depending on the type of keystore. All keystores require the passphrase in order to write to the keystore. Some keystores do not require the passphrase to read from the keystore. Whether or not you define this property depends on the requirements of the keystore. For example, WebLogic Server only reads from the keystore so a passphrase is not required, however, WebLogic Integration writes to keystores and therefore requires a passphrase.
| Note: | However, since you need to load the private key you created in Creating a Public/Private Key Pair into the keystore before you can configure the SSL settings, you can minimize this window for now. Instead restart your WebLogic Server and continue to the next section, Step 3: Configuring the Local Trading Partner in WebLogic Integration, which includes loading the private key into the keystore. |
To learn more about the setting you just entered, see "Configuring Keystores" in Configuring SSL.
WebLogic Integration contains two default trading partners named Test_TradingPartner_1 and Test_TradingPartner_2. In this section, you configure Test_TradingPartner_1 to be your local trading partner in WebLogic Integration. You then export the trading partner data into a WebLogic Integration - Business Connect format file. This file, you use later to configure the remote trading partner in WebLogic Integration - Business Connect.
| Note: | Before you start any of the procedures in this section, you must have configured your keystores as described in Step 2: Configuring Keystores for WebLogic Integration and restarted your WebLogic Server after completing the keystore configuration. |
This section contains the following procedures:
The following procedure describes how to configure the default trading partner Test_TradingPartner_1 to act as the local trading partner in your WebLogic Integration application:
 Profile Management
Profile ManagementThe View and Edit Trading Partner Profiles screen appears with the two trading partners Test_TradingPartner_1 and Test_TradingPartner_2 listed, as shown in the following figure:
Since you are going to import the configuration for the remote trading partner from WebLogic Integration - Business Connect later on, you can delete Test_TradingPartner_2 from the list.
You now need to add the appropriate certificates to your local trading partner so that they will be imported into the keystore.
The following procedure describes how to add the certificate, which you created in Generating the Test Certificate, to your local trading partner configuration:
The details of your trading partner, including general information, bindings, and certificates are displayed. Note that there are no certificates configured for this trading partner.
The Add Certificate (Step 1 of 2) screen appears.
The Add Certificate (Step 2 of 2) screen appears. You use this screen to import a client certificate file to be stored in the key store and used by the local trading partner. However, before you can create the client certificate, you have to create a pass word alias.
The Add New Password Alias screen appears.
The Add Certificate (Step 2 of 2) screen appears again, with the alias values you just entered.
WLCert.crt file which you created in Generating the Test Certificate.WLCert.key file which you created in Generating the Test Certificate.By selecting CLIENT from the Type drop-down list, you specified the certificate to be a client certificate. You can add a signature certificate by using this same procedure, but instead selecting SIGNATURE from the Type drop-down list.
You can review all your configurations of the Test_TradingPartner_1 trading partner by navigating to Trading Partner Management Profile Management and clicking on the Test_TradingPartner_1 trading partner.
Profile Management and clicking on the Test_TradingPartner_1 trading partner.
The next step is to edit the protocol bindings for your trading partner.
The default trading partner you just configured to be the local trading partner for WebLogic Integration, contains two ebXML default bindings. The following steps describes how to edit the ebXML 2.0 binding with the correct transport protocol and signature settings:
The Edit Binding screen appears.
The View Binding Details screen appears
Your new binding settings are saved. To learn more about how to configure ebXML bindings including how to configure signatures and signature transforms, see "Adding Protocol Bindings to a Trading Partner" in Trading Partner Management.
Since you have completed the configuration of the local trading partner and have imported the test certificate into the keystore, you can now return to the WebLogic Server console and configure the SSL settings.
Although you specified the certificate you loaded into the keystore as a client certificate when you configured the WebLogic Integration, for testing purposes you can also use this certificate as the server certificate for WebLogic Server. You just have to configure the server with the correct alias in the SSL settings.
You configure the SSL settings on the WebLogic Server in the WebLogic Console:
From WebLogic Integration, you do this by selecting Tools WebLogic Server
WebLogic Server WebLogic Console.
WebLogic Console.
 server name
server nameTP1-clientThis is the alias you specified when loading the private key for WebLogic Server from the keystore in Adding the Test Certificate to the Keystore.
TP1ClientThis is the password specified when loading the private key for WebLogic Server into the keystore in Adding the Test Certificate to the Keystore.
An alert screen appears, which informs you that you need to restart your server. You can ignore this for now, instead restart your server after you have completed all the SSL configuration steps.
The Keystore Configuration screen appears.
To learn more about the settings you just entered, see "Configuring Two-Way SSL" in Configuring SSL.
<Feb 1, 2007 4:11:45 PM IST> <Notice> <Security> <achepuri02> <examplesServer> <[ACTIVE] ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326505038> <BEA-090082> <Security initializing using security realm myrealm.>
<Feb 1, 2007 4:11:49 PM IST> <Notice> <WebLogicServer> <achepuri02> <examplesServer> <Main Thread> <<WLS Kernel>> <> <> <1170326509604> <BEA-000365> <Server state changed to STANDBY>
<Feb 1, 2007 4:11:49 PM IST> <Notice> <WebLogicServer> <achepuri02> <examplesServer> <Main Thread> <<WLS Kernel>> <> <> <1170326509604> <BEA-000365> <Server state changed to STARTING>
<Feb 1, 2007 4:12:04 PM IST> <Warning> <HTTP> <achepuri02> <examplesServer> <[ACTIVE] ExecuteThread: '0' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326524145> <BEA-101369> <weblogic.servlet.internal.WebAppServletContext@1dab0f0 - appName: 'BEA_WLS_DBMS_ADK', name: 'BEA_WLS_DBMS_ADK_Web', context-path: '/BEA_WLS_DBMS_ADK_Web': The encoding jsp-descriptor param has been deprecated. Consider declaring the encoding in the jsp-config element (web.xml) or as a page directive (pageEncoding) instead.>
<Feb 1, 2007 4:12:18 PM IST> <Notice> <Log Management> <achepuri02> <examplesServer> <[STANDBY] ExecuteThread: '5' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326538816> <BEA-170027> <The server initialized the domain log broadcaster successfully. Log messages will now be broadcasted to the domain log.>
<Feb 1, 2007 4:12:19 PM IST> <Notice> <WebLogicServer> <achepuri02> <examplesServer> <Main Thread> <<WLS Kernel>> <> <> <1170326539377> <BEA-000365> <Server state changed to ADMIN>
<Feb 1, 2007 4:12:19 PM IST> <Notice> <WebLogicServer> <achepuri02> <examplesServer> <Main Thread> <<WLS Kernel>> <> <> <1170326539407> <BEA-000365> <Server state changed to RESUMING>
<Feb 1, 2007 4:12:21 PM IST> <Notice> <Security> <achepuri02> <examplesServer> <[ACTIVE] ExecuteThread: '2' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326541089> <BEA-090171> <Loading the identity certificate and private key stored under the alias DemoIdentity from the jks keystore file C:\bea_GA\WEBLOG~1\server\lib\DemoIdentity.jks.>
<Feb 1, 2007 4:12:21 PM IST> <Notice> <Security> <achepuri02> <examplesServer> <[ACTIVE] ExecuteThread: '2' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326541360> <BEA-090169> <Loading trusted certificates from the jks keystore file C:\bea_GA\WEBLOG~1\server\lib\DemoTrust.jks.>
<Feb 1, 2007 4:12:21 PM IST> <Notice> <Security> <achepuri02> <examplesServer> <[ACTIVE] ExecuteThread: '2' for queue: 'weblogic.kernel.Default (self-tuning)'> <<WLS Kernel>> <> <> <1170326541370> <BEA-090169> <Loading trusted certificates from the jks keystore file C:\bea_GA\JROCKI~1\jre\lib\security\cacerts.>
<Feb 1, 2007 4:12:21 PM IST> <Error> <Server> <achepuri02> <examplesServer> <DynamicListenThread[Default[2]]> <<WLS Kernel>> <> <> <1170326541620> <BEA-002606> <Unable to create a server socket for listening on channel "Default[2]". The address 127.0.0.1 might be incorrect or another process is using port 7001: java.net.BindException: Address already in use: JVM_Bind.>
.
.
.
You have now completed the WebLogic Server configuration. To learn more about WebLogic Server SSL configuration, see Configuring SSL. The next step is to export the Test_TradingPartner_1 data so that you can import this data later on when you configure the remote trading partner in WebLogic Integration-Business Connect.
Instead of configuring both the company profile and partner profile by going through the configuration screens in WebLogic Integration-Business Connect, you can import data that has been exported from WebLogic Integration directly into WebLogic Integration-Business Connect and have the partner profile automatically configured To export the WebLogic Integration trading partner data into a WebLogic Integration-Business Connect compatible format, complete the following procedure:
 Profile Management
Profile Management| Note: | Remember the navigation path to the file. You will need this when you import your trading partner information into the WebLogic Integration - Business Connect application. |
You have completed the WebLogic Integration local trading partner configuration. To learn more about creating, configuring, and managing trading partners in WebLogic Integration, see Trading Partner Management.
You can create your remote trading partner in WebLogic Integration using the procedures you just completed for Test_TradingPartner_1. However, in this example you take a short cut by importing the company profile settings from WebLogic Integration - Business Connect and use that as the remote trading partner.
The next step shows you how to configure a trading partner named Test_TradingPartner_2 as the company profile partner in the WebLogic Integration - Business Connect application and how to export the company profile information into a file that you can then import into WebLogic Integration.
In WebLogic Integration - Business Connect, creating trading partners involves setting up a company profile and then configure certificates for that profile. You can then export the profile to be used later when you configure the remote trading partner in WebLogic Integration. This section contains the following procedures:
In this section, you create and configure a company profile of in the WebLogic Integration - Business Connect:
 Programs
Programs BEA WebLogic Integration - Business Connect 8.1
BEA WebLogic Integration - Business Connect 8.1 Administrator.
Administrator.The Company Profiles information viewer opens.
The New Company Profile dialog window opens.
The Company Profile window opens with the Identity tab selected.
The Add Protocol window opens.
The HTTPS Transport Options window opens with the following values displayed:
| Note: | WebLogic Integration - Business Connect obtains the computer name in the URL from the host name field on the General tab in Tools Preferences. The host name is the computer that is running the Server application. Preferences. The host name is the computer that is running the Server application. |
The New Company Certificate dialog window opens.
The New Certificate window opens.
The New Certificate Key, Select Key Type window opens.
The New Certificate, Summary Window opens.
You have completed the company profile configuration. The next step is to export the company profile information so that you can use this to create the remote trading partner in WebLogic Integration and the server certificate in the iPlanet proxy server.
The following steps describes the exporting procedure:
The Company Profiles information viewer opens.
The Export Company Profile window opens.
You have successfully exported the company profile from WebLogic Integration - Business Connect. To learn more about WebLogic Integration - Business Connect company profiles and certificates, see Using WebLogic Integration - Business Connect.
Before you can configure the remote trading partner information in a Partner Profile for WebLogic Integration - Business Connect, you need to install and configure the iPlanet Proxy Server. This is because some of the certificates you need for the Partner Profile are created during the iPlanet configuration. So for now, you leave WebLogic Integration - Business Connect and complete the WebLogic Integration remote trading partner configuration and then proceed to the iPlanet configuration.
In this section, you create a remote trading partner in the WebLogic Integration application by importing the company profile information which you exported from WebLogic Integration - Business Connect in Exporting the Company Profile Information .
The following steps describes the importing procedure:
 Profile Management
Profile ManagementAfter successfully importing the trading partner information, remember to review the new trading partner profile and make sure that the end point URL is correct. You do this by navigating to Profile Management, clicking on Test_TradingPartner_2, and clicking on its binding. When you click on Test_TradingPartner_2, note that three certificates (client, server, signature) were automatically created in the Company Profile in WebLogic Integration - Business Connect and imported into WebLogic Integration.
Now that you have configured both the local and the remote trading partner for WebLogic Integration, the next step is to add services and service profiles to those trading partners.
Once the Test_TradingPartner_1 and Test_TradingPartner_2 configurations are completed, you have to create services and corresponding service profiles for those trading partners.
To be able to configure the services correctly, the business process which initiates the ebXML message exchange must be currently deployed. This section contains the following procedures:
Complete the following steps to add a service to your trading partner profiles.
If you are not familiar with how to build and deploy ebXML business processes, consider completing one of the exercises in Tutorials: Building ebXML Solutions.
 Service Management.
Service Management.The Add Service screen appears.
Your service is created and the View And Edit Service Details screen appears on which you add the service profile.
After you have created the trading partner service, you create a service profile which specify the protocol binding and URL endpoints for the local and remote trading partners that offer and call the service. The following procedure describes how to add a service profile:
The Add Service Profile screen is displayed.
| Note: | Make sure you change the endpoint URLs to use https, not http. If they are set to the wrong protocol, follow the directions in Editing the Trading Partner Binding to select the correct one. |
| Note: | Although it is not enforced, typically the same type of authentication is selected for both the local and remote trading partner. |
Where xxxx is a number which was randomly generated when you imported the WebLogic Integration-Business Connect self-signed certificate file.
Authentication is added and the View and Edit Service Details page is displayed.
| Note: | If there is an error, the Add Authentication page is redisplayed. A message indicating the problem is displayed above the input requiring correction. |
You have now created a service and its service profile. To learn more about services and service profiles, see "Adding Services" and "Adding Service Profiles to a Service" in Trading Partner Management. The next step is to configure the iPlanet SSL settings and then proceed to complete the configuration of WebLogic Integration - Business Connect.
This section describes how to configure your iPlanet Web Server as the proxy server for this sample.
If you do not already have iPlanet Web Server installed, you can download it from Sun's website the following location: http://wwws.sun.com/software/download/products/3f186391.html
Refer to the product documentation to install and start the iplanet admin and managed server.
This section contains the following procedures:
Before you can configure your iPlanet server certificates, you have to create a trust database in which to store the certificates. To do so, complete the following procedure:
A dialog window confirming the successful initialization appears. The next step is to request a trial digital certificate from Verisign which you use as the server certificate for iPlanet and also imported later on into the Partner Profile in WebLogic Integration - Business Connect.
You can request a trial digital certificate from Verisign to use for testing purposes. The certificate is valid for a limited number of days. To request a certificate, complete the following steps:
 Security
Security Request a Certificate.
Request a Certificate.A confirmation message is displayed in the Managed Server Console.
After you complete the request, Verisign will send you an email with the digital certificate. Copy the content and save it in a file named iPlanetServer.pem. This file is your digital certificate for the iPlanet Server.
You have completed the trial digital certificate request process. The next step is to install the digital trial certificate as the iPlanet server certificate.
You are now ready to install the server certificate for iPlanet. The following procedure describes the steps to complete:
 Security
Security Install Certificate
Install CertificateThe Install a Server Certificate screen appears.
The Add Server Certificate screen appears with the details of the certificate you are adding.
You have successfully added the server certificate. The next step is to download and convert the trusted CA server certificate.
In addition to the server certificate you just installed, you also need a trusted certificate from an Certificate Authority such as Verisign. To request a trusted certificate from Verisign, complete the following procedure:
The server certificate is in binary format. Before you can use it with iPlanet, you must convert it to PEM format. The der2pem command line utility included with WebLogic Server can be used to convert the certificate. To learn how to use the utility, see "der2pem" in
Using the WebLogic Server Java Utilities in the WebLogic Server Command Reference at the following URL:
http://download.oracle.com/docs/cd/E13222_01/wls/docs92/admin_ref/utils.html
Follow the procedure described to convert the iPlanetCA.der file to iPlanetCA.pem.
| Note: | A DER format file contains binary data and can only be used for a single certificate. A PEM format file supports multiple digital certificates. For example, a certificate chain can be included. The order of the files is important, they should be in the order of trust. The server digital certificate should be the first digital certificate in the file, the issuer of the digital certificate should be next, and so on, until you get to the self-signed root certificate authority certificate. |
After you have completed the conversion, the next step is to install the trusted CA certificate.
To install the trusted certificate you just requested, do the following:
 Security
Security Install Certificate
Install CertificateThe Add Server Certificate screen appears with the details of the certificate you are adding.
You have successfully installed the trusted CA certificate.
The next step is to install the WebLogic Integration - Business Connect certificate.
Use the procedures described in Installing the Trusted CA Certificate to import the TP2.xml file which you exported in Exporting the Company Profile Information to create WebLogic Integration - Business Connect CA certificate for your iPlanet server.
You have now successfully installed the necessary iPlanet certificates. There is just one final step required to get the iPlanet configuration to work with SSL.
 Mange Servers.
Mange Servers. Edit Listen Sockets.
Edit Listen Sockets.obj.conf file add the following lines of code:
<Object name="myProxy" ppath="*">
PathCheck fn="get-client-cert" method="(GET|POST)" dorequest="1"
Service fn=wl_proxy FileCaching="OFF" Debug="ALL" KeepAliveEnabled=false DebugConfigInfo="ON" WebLogicHost=172.16.17.183\
WebLogicPort=7001 WLLogFile="C:/depot/newlog.txt" SecureProxy="OFF" WLProxySSL="ON" RequireSSLHostMatch="False"
</Object>
magnus.conf file, add the following lines of code:
Init fn="load-modules" shlib="D:/iPlanet/Servers/bin/https/bin/proxy36.dll" funcs="wl_proxy,wl_init"
Init fn="wl_init"
This concludes the iPlanet configuration step. To learn more about the settings you just configured, see Installing and Configuring the Netscape Enterprise Server Plug-In in Using Web Server Plug-Ins With WebLogic Server at the following URL:
http://download.oracle.com/docs/cd/E13222_01/wls/docs81/plugins/nsapi.html
The next step is to configure a remote trading partner in WebLogic Integration - Business Connect by importing the trading partner information that you exported from WebLogic Integration in Step 5: Exporting the WebLogic Integration Trading Partner Data into a Partner Profile and then configure the appropriate client, server, and trusted certificates for that Partner Profile.
Instead of creating a new partner profile for Test_TradingPartner_1, you import the file you previously exported from the WebLogic Integration application into your WebLogic Integration Business Connect application. When you import the trading partner information, the company profile and the corresponding client certificate is automatically created for you.
Since you are using iPlanet as a proxy server, iPlanet takes care of the mutual authentication when WebLogic Integration - Business Connect sends a message. Therefore, you have to configure an iPlanet server certificate and also load the corresponding CA certificates.
This section contains the following procedures:
This procedure describes how to import the WebLogic Integration trading partner data directly into a partner profile:
 Programs
Programs BEA WebLogic Integration - Business Connect 8.1
BEA WebLogic Integration - Business Connect 8.1 Administrator.
Administrator.The Partner Profiles information viewer opens.
 Import.
Import.The Import Partner Profile window opens.
A message displays when the partner profile imports successfully.
You have now completed creating the remote trading partner company profile. The next step is to import a server certificate for iPlanet and load the corresponding CA certificates.
Complete the following procedure to import an iPlanet server certificate for your WebLogic Integration-Business Connect application:
 Partner Profiles
Partner Profiles Test_TradingPartner_1.
Test_TradingPartner_1.You have now installed the iPlanet server certificate. The next step is to load the CA certificates for iPlanet and for WebLogic Integration - Business Connect.
This procedure describes how to import the CA certificates into WebLogic Integration-Business Connect:
 Partner Profiles
Partner Profiles Test_TradingPartner_1.
Test_TradingPartner_1.The Trusted Roots window opens.
You have completed WebLogic Integration - Business Connect remote trading partner configuration. To learn more about configuring certificates in WebLogic Integration - Business Connect, see Keys and Certificates in Using WebLogic Integration - Business Connect.
This concludes this security example. Before you run the example, it is a good idea to restart all your servers.


|