









|
During database installation or by employing the Setup tool, you may choose to use accounts from external repositories. This chapter describes how to integrate accounts from an LDAP server and from non-LDAP user stores into BEA AquaLogic Service Registry.
An LDAP server can be integrated with BEA AquaLogic Service Registry with these scenarios:
DOMAIN/USERNAME). All users must specify the domain name in the login dialog. When managing accounts or groups, we recommend using the DOMAIN/USERNAME format for performance reasons. If no domain is set, searches are performed across all domains.For information about configuring LDAP scenarios, see LDAP.
This chapter also contains the following configuration examples:
| Notes: | 1. BEA AquaLogic Service Registry treats external stores as read-only. User account properties stored in these external stores cannot be modified by BEA AquaLogic Service Registry. |
| Note: | 2. The Administrator account must not be stored in the LDAP. We strongly recommend that users stored in account_list.xml (by default, only administrator) should not be in the LDAP. If you really need to have users from LDAP in the file account_list.xml, delete password items from the file and change of all the accounts' properties according to the LDAP. The account_list.xml file contains a list of users that can be logged into a registry without connection to the database. |
To integrate external accounts from another repository, either:
bin subdirectory of your installation:
Windows: setup.bat |
UNIX: ./setup.sh |
See the command-line parameters for Setup in Command Line Scripts.
For more information on the Setup tool, please see Reconfiguration After Installation.
Select LDAP on the Account Provider panel.
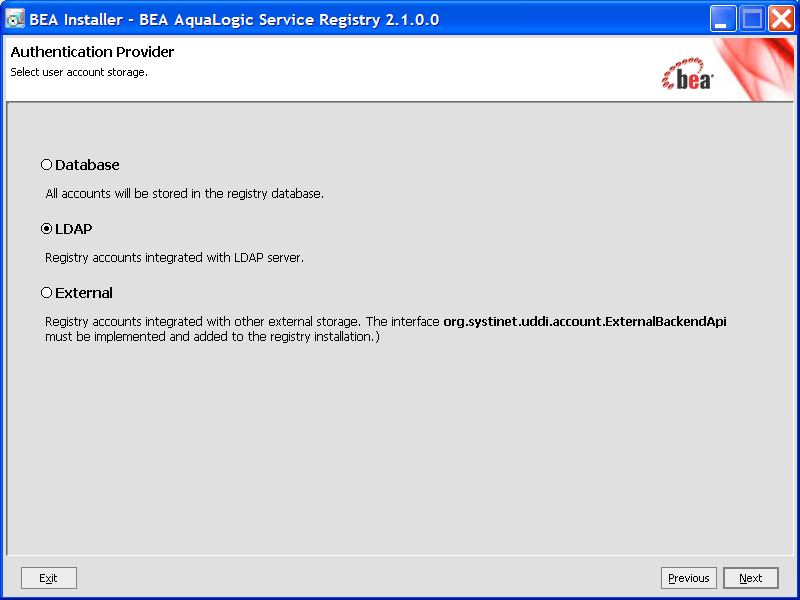
Enter the settings as described in the following figure.
BEA AquaLogic Service Registry uses a JNDI interface to connect to LDAP servers. The following JNDI properties must be known to the server. (The default properties are noted in parentheses.)
ldap://hostname:389).
You can select the following LDAP usage scenarios:
| Note: | Automatic discovery of the LDAP service using the URL's distinguished name is supported only in Java 2 SDK, versions 1.4.1 and later, so be sure of the Java version you are using. |
| Note: | The automatic discovery of LDAP servers allows you not to hardwire the URL and port of the LDAP server. For example, you can use ldap:///o=JNDITutorial,dc=example,dc=com as a URL and the real URL will be deduced from the distinguished name o=JNDITutorial,dc=example,dc=com. |
| Note: | BEA AquaLogic Service Registry integration with LDAP uses the JNDI API. For more information, see |
| Note: | http://java.sun.com/products/jndi/tutorial/ldap/connect/create.html |
| Note: | and |
| Note: | http://java.sun.com/j2se/1.4.2/docs/guide/jndi/jndi-dns.html#URL |
The installation consists of the following steps:
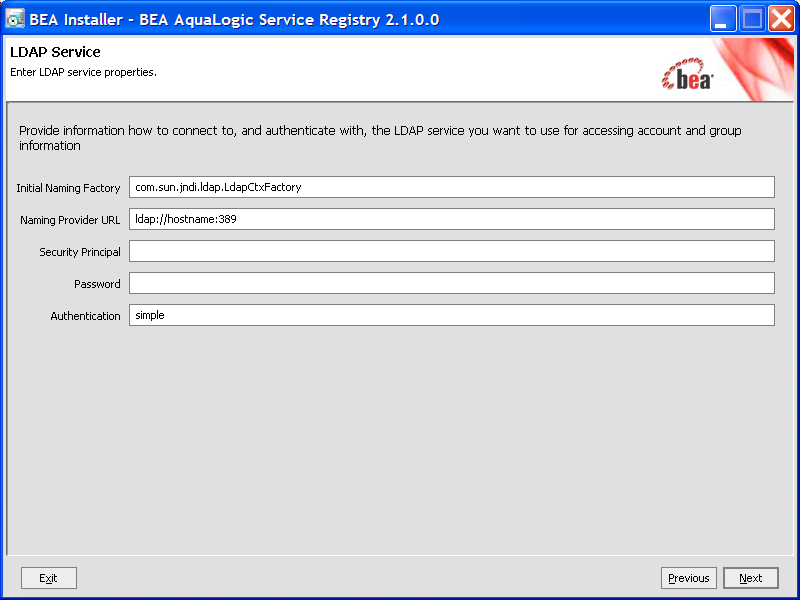
You can specify mapping between BEA AquaLogic Service Registry user account properties and LDAP properties. You can add rows by clicking Add. To edit an entry, double click on the value you wish to edit.
The following user account properties can be mapped from an LDAP server.
java.lang.String loginName
java.lang.String email
java.lang.String fullName
java.lang.String languageCode
java.lang.String password
java.lang.String description
java.lang.String businessName
java.lang.String phone
java.lang.String alternatePhone
java.lang.String address
java.lang.String city
java.lang.String stateProvince
java.lang.String country
java.lang.String zip
java.util.Date expiration
java.lang.Boolean expires
java.lang.Boolean external
java.lang.Boolean blocked
java.lang.Integer businessesLimit
java.lang.Integer servicesLimit
java.lang.Integer bindingsLimit
java.lang.Integer tModelsLimit
java.lang.Integer assertionsLimit
java.lang.Integer subscriptionsLimit
The Registry account property dn specifies the LDAP distinguished name. The value depends on the LDAP vendor.
If an optional property (such as email) does not exist in the LDAP, then the property's value is set according to the default account. The default account is specified in the configuration file whose name is account_core.xml.
| Note: | User account properties that you specify at the Figure 11-6 will be treated as read-only from Registry Console and registry APIs. |
For more information, please see "userAccount data structure" in the Developer's Guide in Using the AquaLogic Service Registry.
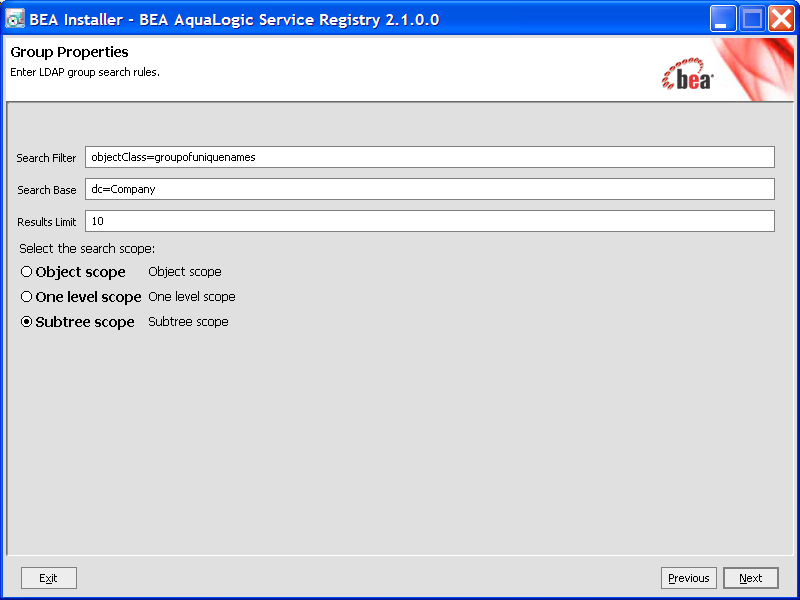
You can specify mapping between BEA AquaLogic Service Registry group properties and LDAP properties. You can add rows by clicking Add. To edit an entry, double click on the value you wish to edit.
If a property (such as description) does not exist in the LDAP then property value is set according to the default group. The default group (groupInfo) is specified in the configuration file whose name is group.xml.
For more information, please see"group data structure" in the Developer's Guide in Using the AquaLogic Service Registry.
The installation consists of the following steps:
{domain prefix}domain_name{domain postfix}{search base}
where {domain prefix} is value of property whose name is domain prefix, {domain postfix} is value of property whose name is domain postfix and {searchbase} is value of property whose name is searchbase.
The correct LDAP service is chosen via DNS. The installation consists of the following steps:
It is only a matter of configuration to setup LDAP over SSL (or TLS) with a directory server of your choice. We recommend that you first install BEA AquaLogic Service Registry with a connection to LDAP that does not use SSL. You can then verify the configuration by logging in as a user defined in this directory before configuring use of SSL.
The configuration procedure assumes that you have already installed BEA AquaLogic Service Registry with an LDAP account provider. BEA AquaLogic Service Registry must not be running.
In this case only LDAP server authentication is required. This is usually the case.
Edit the REGISTRY_HOME/app/uddi/conf/directory.xml file in one of the following ways depending on the version of Java used to run BEA AquaLogic Service Registry:
This is shown in the following example:
<config name="directory" savingPeriod="5000">
<directory>
<!-- LDAP over (SSL/TLS) unprotected connection -->
<!--
<property name="java.naming.provider.url" value="ldap://hostname:47361"/>
-->
<!-- LDAP over SSL/TLS for Java 1.4.2 and later -->
<!--
<property name="java.naming.provider.url" value="ldaps://hostname:636"/>
-->
<!-- LDAP over SSL/TLS for Java where LDAP over SSL is supported -->
<property name="java.naming.provider.url" value="ldap://hostname:636"/>
<property name="java.naming.security.protocol" value="ssl"/>
...
...
...
</directory>
</config>
In both cases, be sure that the hostname specified in the java.naming.provider.url property matches the name that is in the directory server certificate's subject common name (CN part of certificate's Subject). Otherwise you will get an exception during startup of BEA AquaLogic Service Registry. It will inform you of a hostname verification error. The stack trace contains the hostname that you must use.
BEA AquaLogic Service Registry does not support LDAP over SSL with mutual authentication.
The client that connects to the SSL/TLS server must trust the server certificate in order to establish communication with that server. The configuration of LDAPS explained above inherits the default rule for establishing trust from JSSE (the Java implementation of SSL/TLS). This is based on trust stores.
When a trust store is needed to verify a client/server certificate, it is searched for in the following locations in order:
It is recommended to use the first option to define a trust store specifically for the application you are running. In this case, you have to change the command that starts the registry (or the JVM environment of the ported registry) to define the following Java system properties:
To ensure that the server certificate is trusted, you have to:
keytool -import -trustcacerts -alias alias -file file -keystore keystore -storepass storepass |
changeit;
changeit;
changeit;
changeit;
The following configuration examples are included in this section:
In this example, we show how to configure a Sun One Directory Server 5.2 under the LDAP with a Single Search Base scenario.
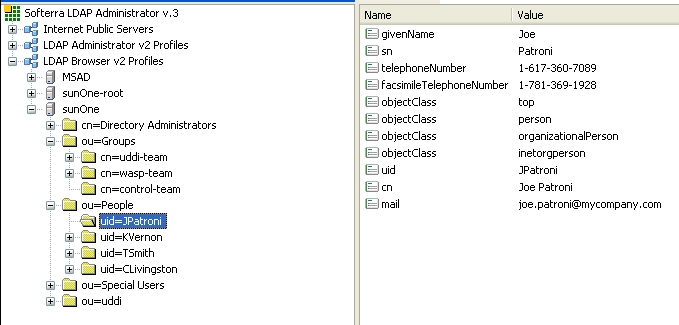
SUN One with Single Search Base shows user properties that are stored in the LDAP server.
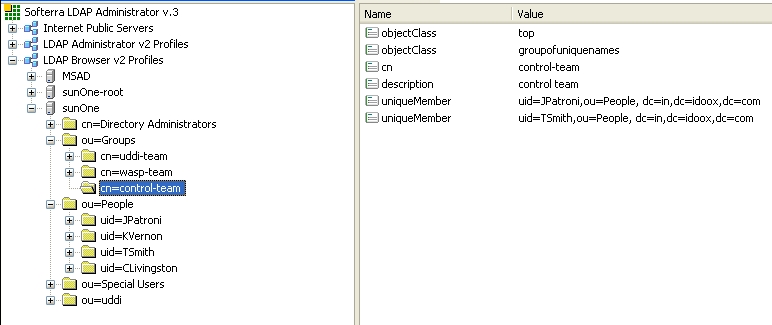
SUN One with Single Search Base shows group properties that are stored in the LDAP server.
The following table shows how to configure BEA AquaLogic Service Registry using this scenario.
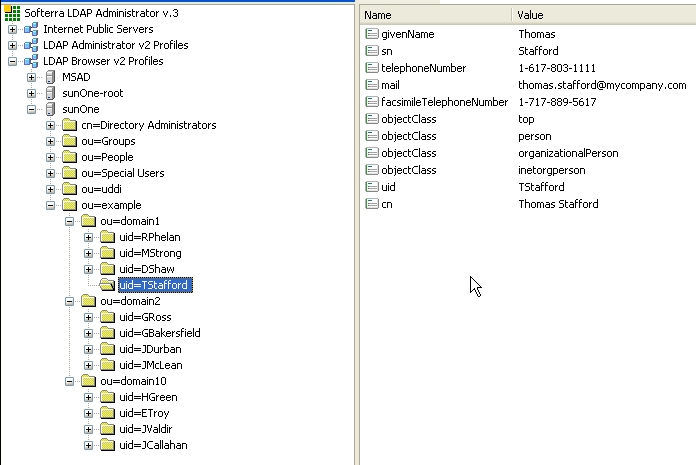
In this example, we show how to configure Sun One Directory Server 5.2 with multiple search bases. In Figure 11-14, you can see users and domains that are stored on the LDAP server. We want to configure the LDAP integration with BEA AquaLogic Service Registry in this way:
Figure 11-14 shows how users from LDAP are mapped to BEA AquaLogic Service Registry
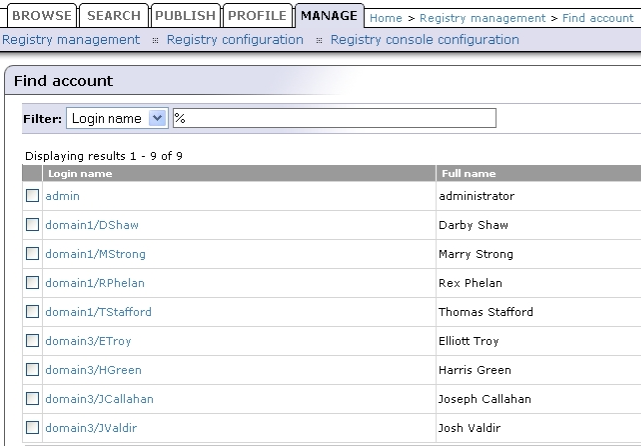
The following table shows how to configure BEA AquaLogic Service Registry using this scenario.
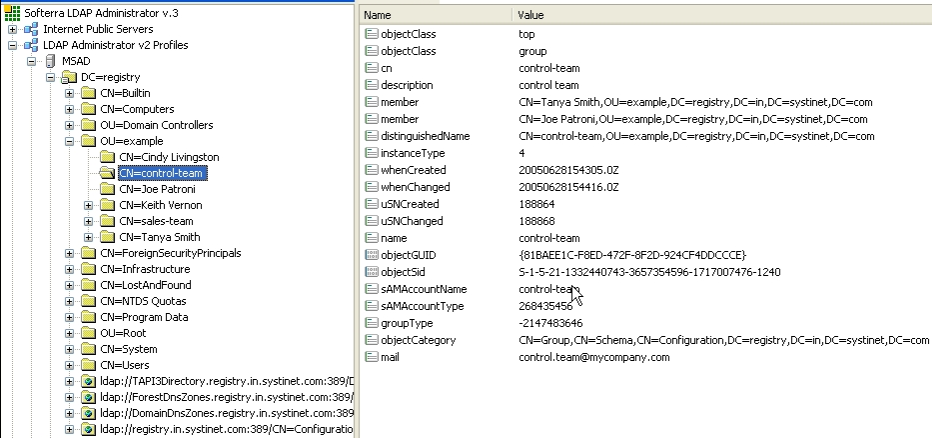
Table 11-3In this example, we show how to configure an Active Directory with a single search base. Figure 11-15 shows group properties that are stored in the Active Directory. These group properties will be mapped to BEA AquaLogic Service Registry as shown in Figure 11-16.
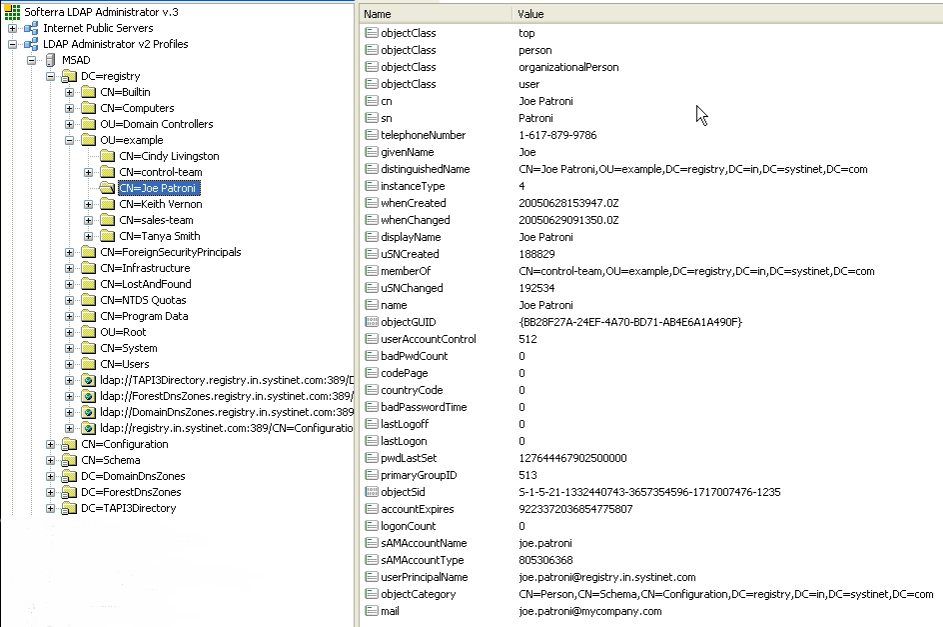
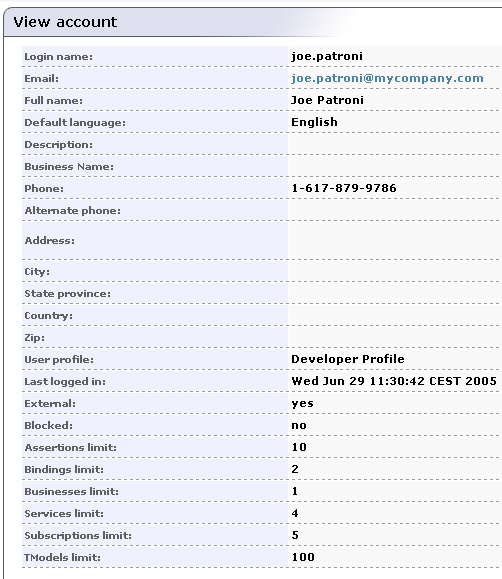
The following figure shows user properties that are stored in the Active Directory. These user properties will be mapped to BEA AquaLogic Service Registry as shown in Figure 11-16.
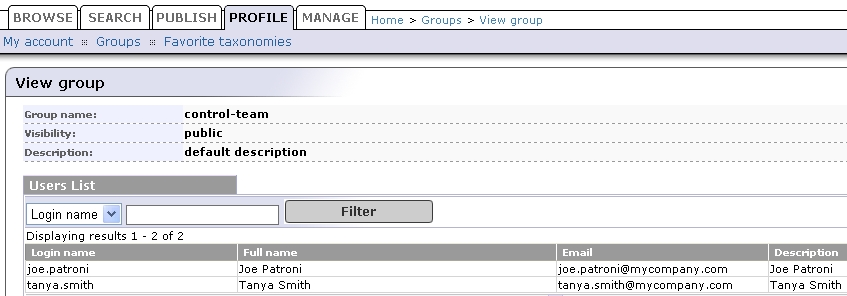
The following table shows how to configure BEA AquaLogic Service Registry using this scenario.
Table 11-4
Select External on the Advanced Account Settings panel.
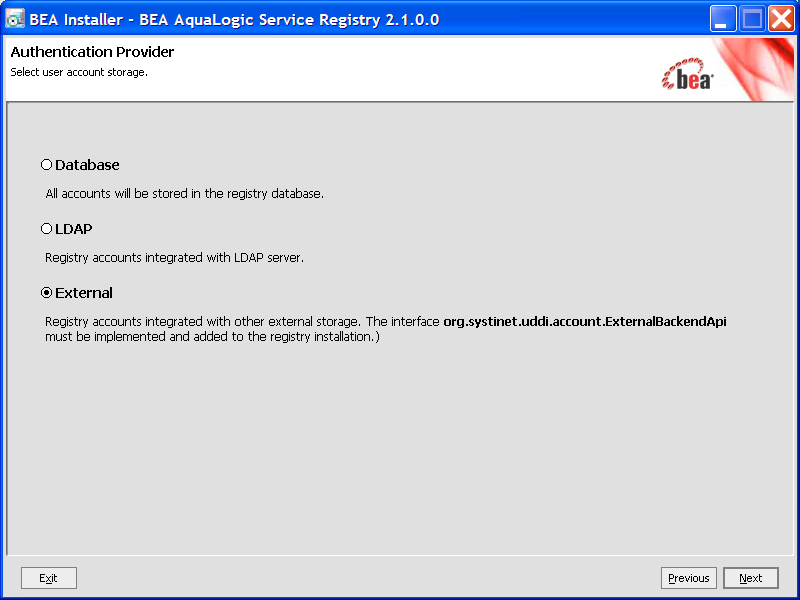
External accounts require implementation of the interface org.systinet.uddi.account.ExternalBackendApi.


|