









|
The following sections provide the information you need to install the ALES Security Service Modules:
Before you begin this installation procedure, make sure you do the following:
| Note: | If you start the installation process from the command line or from a script, you can specify the -log option to generate a verbose installation log. For instructions on how to generate a verbose log file during installation, see Generating a Verbose Installation Log. |
If you start the installation process from the command line or from a script, you can specify the -log option to generate a verbose installation log. The installation log lists messages about events during the installation process, including informational, warning, error, and fatal messages. This can be especially useful for silent installations.
| Note: | You may see some warning messages during in the installation log. However, unless there is a fatal error, the installation program will complete the installation successfully. The installation user interface will indicate the success or failure of the installation, and the installation log file will include an entry indicating that the installation was successful. |
To generate a verbose log file during installation, include the -log=/full_path_to_log_file option in the command line or script. For example:
ales250ssm_win32.exe -log=D:\logs\ales_install.log -log_priority=debugales250ssm_solaris32.bin -log=/opt/logs/ales_install.log -log_priority=debugales250ssm_rhas_IA32.bin -log=/opt/logs/ales_install.log -log_priority=debugjava -jar ales250ssm_aix32.jar -log=/opt/logs/ales_install.log -log_priority=debugThe path must be the full path to a file name. If the file does not exist, all folders in the path must exist before you execute the command or the installation program will not create the log file.
The procedure for starting the installation program varies depending the platform on which you install BEA AquaLogic Enterprise Security. Therefore, separate instructions are provide for each supported platform.
| Note: | In a production environment, BEA recommends that you install the Security Service Modules on machines other than the machine on which the Administration Server is installed. |
To start the installation program, refer to the appropriate section listed below:
| Note: | Do not install the software from a network drive. Download the software distribution to a local drive on your machine and install it from there. Also, on a Windows platform, the file system used must be NTFS, not FAT. To check the file system format, open Windows Explorer and right-click the hard drive on which you intend to do the installation and select Properties. |
To install the application in a Microsoft Windows environment:
ales250ssm_win32.exe.The BEA Installer - Security Service Module window appears (see Figure 4-1).
If the installation program does not start automatically, open Windows Explorer and double-click the CD-ROM icon.
ales250ssm_win32.exe.The BEA Installer - Security Service Module window appears (see Figure 4-1).
To run graphical-mode installation, your console must support a Java-based GUI. If the installation program determines that your system cannot support a Java-based GUI, the installation program automatically starts console-mode installation.
chmod u+x ales250ssm_solaris32.bin: ales250ssm_solaris32.binThe BEA Installer - Security Service Module window appears (see Figure 4-1).
chmod a+x ales250ssm_solaris32.bin
ales250ssm_solaris32.binThe BEA Installer - Security Service Module window appears (see Figure 4-1).
To run graphical-mode installation, your console must support a Java-based GUI. If the installation program determines that your system cannot support a Java-based GUI, the installation program automatically starts console-mode installation.
DISPLAY variable if needed.
For Red Hat 3.0: chmod u+x ales250ssm_rhas_IA32.bin
:
For Red Hat 3.0: ales250ssm_rhas_IA32.bin
The BEA Installer - Security Service Module window appears (see Figure 4-1).
For Red Hat 3.0: chmod u+x ales250ssm_rhas_IA32.bin
For Red Hat 3.0: ales250ssm_rhas_IA32.bin
The BEA Installer window appears (see Figure 4-1).
To run graphical-mode installation, your console must support a Java-based GUI. If the installation program determines that your system cannot support a Java-based GUI, the installation program automatically starts console-mode installation.
ales250ssm_aix32.jar, from the BEA web site. Contact BEA Sales at
http://www.bea.com/framework.jsp?CNT=sales1.htm&FP=/content/about/contact/ to request a download.java -jar ales250ssm_aix32.jar
The installation program prompts you to enter specific information about your system and configuration as described in Table 4-1. To complete this procedure you need the following information:
| Note: | If this is the first AquaLogic Enterprise Security product you have installed on this machine, the Service Control Manager is also included as part of the installation (which requires additional inputs, such as the Service Control Manager directory). This condition does not apply if you choose not to install the Service Control Manager, as described in Installing an SSM Without an Associated SCM. |
Specify the BEA Home directory that serves as the central support directory for all BEA products installed on the target system. If you already have a BEA Home directory on your system, you can select that directory (recommended) or create a new BEA Home directory. If you choose to create a new directory, the installer program automatically creates the directory for you. For details about the BEA Home directory, see BEA Home Directory.
|
|||||
Specify the directory in which you want to install the product software, and then click Next. You can accept the default product directory (for example,
C:\bea\ales25-ssm\wls-ssm) or you can create a new product directory.
For additional information and a description of the resulting directory structure, see Product Installation Directory.
|
|||||
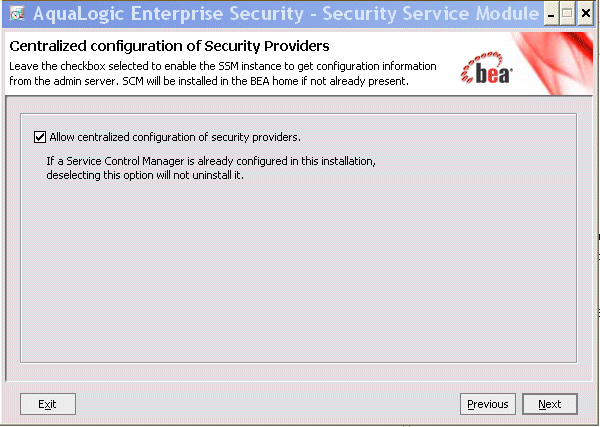
If you are not installing on the Administration Server, and you are not installing only the WLS 9.x SSM, the installer asks whether to allow centralized (automatic) configuration of security providers. Leave the box selected to enable the SSM instance to get configuration information from the Administration Server. Uncheck the box if you do not want to associate the SSM with an SCM. If you uncheck this box, the SSM installer does not ask for an SCM installation directory and does not launch the SCM installer.
Later in this section, Figure 4-2 shows the Centralized Configuration of Security Providers screen.
|
|||||
Select the network interfaces to which to bind the Service Control Manager. This is the IP Address used to listen for requests to provision policy and configuration data.
|
|||||
Enterprise Domain Name—The enterprise domain name is used to link all of the AquaLogic Enterprise Security components.
SCM Port—Port used by the Service Control Manager to receive configuration and policy data from the Administration Server; may not be used by any other server.
|
|||||
ALES 2.5 includes a utility to help you upgrade from AquaLogic Enterprise Security 2.1 and 2.2. Note that no upgrade is available for Apache and Microsoft IIS Web Server SSM instances. If you have an existing installation of ALES 2.1 or 2.2, follow this upgrade procedure. For information about upgrading the Administration Server, see Upgrading from ALES 2.1and 2.2 in Installing the Administration Server.
You can run the SSM installation in silent mode. Silent installation mode allows you to run the installer once on one machine and then use the configuration of that machine to duplicate SSM installation on multiple machines. When you run the installation program in silent mode, the installation program reads the configuration information it needs from an XML file that you specify in the command that launches the installation program.
When you run the installation program not in silent mode, it creates an XML file, located at BEA_HOME/ales25-ssm/<ssm>/adm/silent_install_ssm.xml . You can edit this XML file and use it when you run the installation program in silent mode. You need to edit the silent_install_ssm.xml file to set the values described in Table 4-2. Each installation parameter is specified in the XML file as the value of a <data-value> element, as in the following example:
<data-value name="USER_INSTALL_DIR" value="C:\bea\ales25-admin" />
The values you set in the <data-value> elements correspond generally to the responses you enter when you run the installation program not in silent mode, which are described in Table 4-1.
| Note: | If you choose to not to install the Service Control Manager, as described in Installing an SSM Without an Associated SCM, do not fill in values for SCM_INSTALL_DIR, SCM_NAME, and SCM_PORT. |
To run the SSM installation in silent mode, use one of the following commands:
ales250ssm_win32.exe -mode=silent -silent_xml=<path_to_silent.xml>
ales250ssm_solaris32.bin -mode=silent -silent_xml=<path_to_silent.xml>
ales250ssm_rhas_IA32.bin -mode=silent -silent_xml=<path_to_silent.xml>
AquaLogic Enterprise Security version 2.5 removes the requirement that a Service Control Module (SCM) be installed on each system where one or more Security Service Modules (SSMs) are installed.
This section describes how to install and configure an SSM without an associated SCM.
This section describes the current architecture of the SCM and details why it is no longer required in this release.
The SCM is responsible for storing and maintaining the configuration data for all SSMs running on the system. Once started, an SSM receives its configuration data from the local SCM. When a change is made and distributed from the Administration Server, the SCM receives the change and updates the cached copy of the configuration. On restart, the SSM receives updated configuration data from the SCM.
Although the SCM performs this configuration process efficiently, it represents an additional process that has to be installed and maintained. Because the configuration of security providers might not change after the initial system setup, you might determine that maintaining the SCM is needlessly cumbersome.
In this release of AquaLogic Enterprise Security it is possible to deploy an SSM without the SCM. You can use the PolicyIX tool, described in
PolicyIX in the Administration Reference, to communicate directly with the BLM and retrieve configuration data. The PolicyIX tool allows you to export configuration data (configured either through the ALES Administration Console or directly via the BLM API) for a given SSM to an XML file, and use it with the configured SSMs when the SCM is not available.
After you export the configuration data you must manually copy the XML configuration file and the associated signature file to the appropriate SSM configuration directory.
| Note: | The SCM is always installed on the ALES Administration server. |
For the WLS 9.x SSM, you use the WebLogic Server console, and not the SCM, to make configuration changes, as described in Configuring the WebLogic Server 9.x SSM. The WLS 9.x SSM cannot read the configuration file exported by the PolicyIX tool.
PolicyIX uses the existing settings for the SSL infrastructure, specified during the administration server installation, to sign the exported configuration files. In particular, the following Java properties are used to retrieve the signing key:
For example, consider the following use:
-Dwles.ssl.passwordFile="D:/beas/ales25-admin/ssl/password.xml"
-Dwles.ssl.passwordKeyFile="D:/beas/ales25-admin/ssl/password.key"
-Dwles.ssl.identityKeyStore="D:/beas/ales25-admin/ssl/identity.jks"
-Dwles.ssl.identityKeyAlias=wles-admin
-Dwles.ssl.identityKeyPasswordAlias=wles-admin
The PolicyIX.bat file invokes the tool with -Dales.policyTool.signer=wles-admin. The ales.policyTool.signer property is a required Java property that specifies the alias of the signing key in the identity keystore, which must be equal to the Administration server machine name.
The public key of the Administration server is then retrieved from the SSL peer keystore for the purpose of validating the configuration file's signature. This public key is available from the Administration server's certificate, which was added to the SSL peer keystore during the enrollment process.
The uuencoded signature of the XML file is stored in a corresponding signature file, whose name is derived from the full name of the signed XML file (including extension) with the added ".sig" extension. For example, myconfig.xml.sig.
If you do not configure an SCM when you install the SSM, switching back to SCM configuration for that SSM is not possible: you must uninstall the SSM and then add it back.
As described in Installing in Silent Mode, you can run the SSM installation in silent mode. Silent installation mode allows you to run the installer once on one machine and then use the configuration of that machine to duplicate an SSM installation on multiple machines.
If you do not want an SCM to be configured, do not provide values for SCM_NAME, SCM_PORT, and SCM_INSTALL_DIR when you edit the BEA_HOME/ales25-ssm/<ssm>/adm/silent_install_ssm.xml file. These data elements are described in Table 4-2.
When you run the installation program for an SSM, as described in Running the Installation Program, you can choose to not install an SCM.
If you are installing the WLS 9.x SSM, the SCM is not installed. For other types of SSMs, the installer asks whether to allow centralized (automatic) configuration of security providers. Uncheck the box if you do not want to associate the SSM with an SCM. If you uncheck this box, the SSM installer does not ask for an SCM installation directory and does not launch the SCM installer.
Figure 4-2 shows the Centralized Configuration of Security Providers screen.
When you install an SSM without an SCM, the post installation tasks differ from those described in Post Installation Tasks.
The post installation task that you do not perform is as follows:
The post installation tasks that you do perform are as follows:
| Note: | It may seem counter-intuitive to configure an SCM in the Administration Console when the SSM is not associated with an SCM. However, the Administration Console is not aware that the SCM is not configured, and makes the SSM configuration information available as if it were. The PolicyIX tool then exports this configuration information. |
After you have enrolled the instance of the SSM, as described in Enrolling the Instance of the Security Service Module, perform the following steps to export the SSM configuration data and configure the SSM:
Administration Reference.BEA_HOME/ales25-ssm/<ssm-type>/instance-name/config
If you do not use the default name (wles.securityrealm.xml) for this configuration file, set the wles.realm.filename property in the BEA_HOME/ales25-ssm/<ssm-type>/instance-name/config/security.properties file. For example, wles.realm.filename=ssmConfig.xml. See Additional Security.Properties Settings for additional information.
The ALES runtime examines the value of the wles.properties system property during initialization, and if this property is set to a valid filename, the properties contained in the specified file are used to configure the runtime. By default, the ALES runtime looks for a property file called security.properties in the working directory. For example, BEA_HOME/ales25-ssm/<ssm-type>/instance-name/config/security.properties.
In addition to the wles.realm.filename property described in Export the Configuration Data, the following properties must also be set to export the configuration file:
Now that you have installed the necessary software, you must enroll the Service Control Manager, create an instance of the Security Service Module and enroll the instance, and then start the services. For additional instructions, see Post Installation Tasks.


|