4 Administering Web Services
This chapter describes how to use Oracle Enterprise Manager Fusion Middleware Control and WebLogic Scripting Tool (WLST) commands to configure and manage Oracle Fusion Middleware Web Services. It includes the following sections:
4.1 Administering Web Services Using Fusion Middleware Control
The following sections describe how to use Fusion Middleware Control to access and configure Web services on the server and client.
4.1.1 Viewing Web Services Using Fusion Middleware Control
The following sections describe how to view Web services in a domain, on a server, and in an application deployment or application.
-
Viewing the Web Services in a Domain Using Fusion Middleware Control
-
Viewing the Web Services for a Server Using Fusion Middleware Control
-
Viewing the Web Services in an Application Deployment Using Fusion Middleware Control
-
Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control
4.1.1.1 Viewing the Web Services in a Domain Using Fusion Middleware Control
Fusion Middleware Control allows you to view a summary of all currently deployed Web services for a given domain. The summary appears on the Domain home page.
To view a summary of Web services for a domain:
-
In the navigation pane, expand WebLogic Domain to show the domain in which you want to see the Web services.
-
Select the domain.
The Web Services summary appears in the lower right side of the page. For each service, the summary lists the name of the Web service, the name of server it is running on (for example, AdminServer), the name of the associated application running on the server, the name of the Web service endpoint, and a link to a test page for the service.
Note:
This Web Services summary does not include RESTful Web services.
4.1.1.2 Viewing the Web Services for a Server Using Fusion Middleware Control
Follow the procedures below to view all of the currently deployed Web services for a given server.
To view the Web services for a server:
-
In the navigation pane, expand WebLogic Domain to show the servers for which you want to see the Web services.
-
Select the server for which you want to view all current Web services.
-
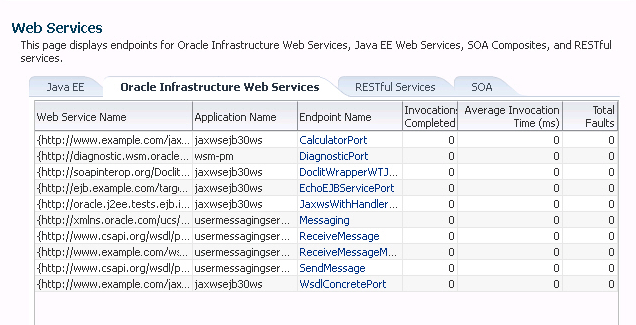
In the content pane, select WebLogic Server and then Web Services. The Web Services Server Summary page appears, as shown in Figure 4-1.
You can view tabs for Java EE Web services, Oracle Infrastructure Web services, such as ADF, and RESTful services.
The tabs that are displayed depend on the Web services deployed on that server.
Figure 4-1 Web Services Summary Page for a Server
Description of "Figure 4-1 Web Services Summary Page for a Server"
4.1.1.3 Viewing the Web Services in an Application Deployment Using Fusion Middleware Control
Fusion Middleware Control allows you to view a summary of the currently deployed Web services for a given application deployment. The summary appears on the Application Deployment home page.
To view the Web services in an application deployment:
-
In the navigation pane, expand the Application Deployments folder to view the applications in the domain.
-
Select the application.
The Web Services summary appears in the lower right side of the Domain Application Deployment page. For each service, the summary lists the name of the Web Service, the name of server it is running on, the name of the associated application running on the server, the name of the Web service endpoint, and a link to a test page for the service.
Note:
The Web Services summary does not include RESTful Web services.
4.1.1.4 Viewing the Web Services Summary Page for an Application
Follow the procedure below to navigate to the page where you can see the list of Web services for your application.
To view the Web services summary page for an application:
-
In the navigation pane, expand the Application Deployments folder to expose the applications in the domain and select the application deployment.
The Domain Application Deployment home page is displayed in the content pane.
-
In the navigation pane, expand the application deployment and select the application name.
The Application Deployment home page is displayed in the content pane.
-
In the content pane, select Application Deployment, then Web Services.
The Web Services Application Summary page is displayed.
From the Web Services Application Summary page, you can do the following:
-
View the Web services in the application.
-
View the Web service configuration, endpoint status, policy faults, and more. (ADF applications only.)
-
View and monitor Web services faults, including Security, Reliable Messaging, MTOM, Management, and Service faults. (ADF applications only.)
-
View and monitor Security violations, including authentication, authorization, message integrity, and message confidentiality violations. (ADF applications only.)
-
Navigate to pages where you can configure your Web services endpoints, including enabling and disabling the endpoint, and attaching policies to Web services.
The Web Service Details table contains tabs where you can view more information about Web services and ports, Web service endpoints, RESTful services, and Java EE Web service clients.
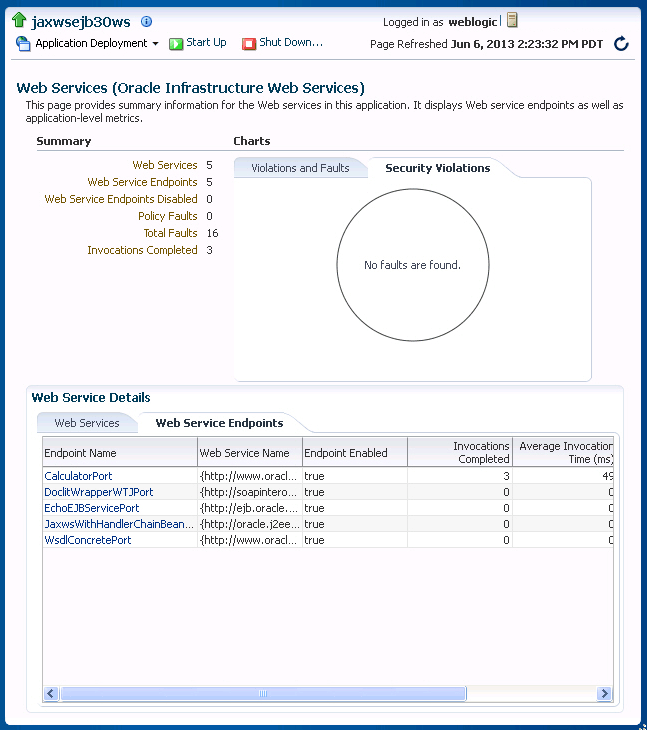
Figure 4-2 shows the Web Services Application Summary page for an ADF application.
Note:
The RESTful Services and Java EE Web Service Clients tabs are displayed only if there are RESTful services or client instances, respectively, in the application.
Figure 4-2 Web Services Home Page for ADF Applications
Description of "Figure 4-2 Web Services Home Page for ADF Applications"
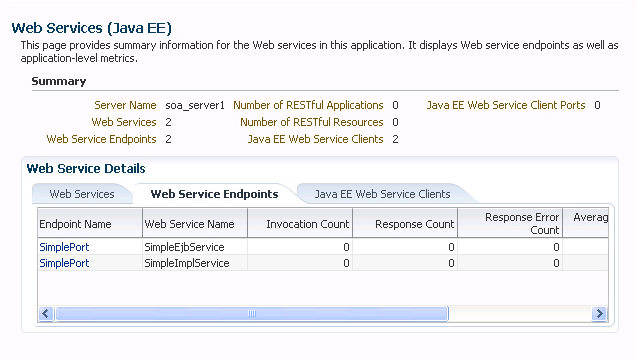
Figure 4-3 shows the Web Services summary page for a Java EE application. The Web Services (Java EE) page displays information about the Web services in this application, such as the numbers of Web services, Web service endpoints, Web service clients and client ports, and the number of RESTful applications and resources.
Figure 4-3 Web Services Home Page for Java EE Applications
Description of "Figure 4-3 Web Services Home Page for Java EE Applications"
-
4.1.1.5 Viewing the Summary Page for a Java EE Web Service
Follow this procedure to view summary information for a Java EE Web Service.
-
Navigate to the Web Services summary page for the Java EE application, as described in "Viewing the Web Services Summary Page for an Application".
-
In the Web Services tab, click the name of the Web service for which you want to view summary information.
The Java EE Web Service Summary page displays two tabs: Web Service Endpoints and Invocations. The Web Service Endpoints tab displays the endpoints associated with the Web service. Invocation statistics are aggregated data for the JEE Web service. For more information on these statistics, see "Viewing Operation Statistics for a Web Service Endpoint".
The Invocations tab provides statistics on the Web service invocations, such as the invocation and response error count. For more information on these statistics, see "Viewing Statistics for a Java EE Web Service Operation".
4.1.1.6 Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control
In Fusion Middleware Control, the following sections describe the steps you follow to view the details for a Web service endpoint:
4.1.1.6.1 Viewing the Details for an Oracle Infrastructure Web Service Endpoint
Follow this procedure to view the details for an Oracle Infrastructure Web service endpoint (such as ADF).
-
Navigate to the Web Services Application Summary page as described in "Viewing the Web Services Summary Page for an Application".
-
In the Web Service Details section of the page, click the Web Services tab and expand the Web service to display the Web service endpoints if they are not already displayed.
Alternatively, click the Web Service Endpoints tab to view a list of Web service endpoints.
-
Click the name of the endpoint to navigate to the Web Service Endpoint page.
-
From the Web Service Endpoint page, you can do the following:
-
Click the Operations tab to see the list of operations for this endpoint.
-
Click the WSM Policies tab to see the policies attached to this endpoint, if the endpoint has a valid configuration, and if it is secure.
-
Click the Charts tab to view a graphical view of the faults for this endpoint. There are two charts, one that shows the distribution of all faults, and a second that shows the distribution of only security faults. For more information, see "Viewing the Security Violations for a Web Service".
-
Click the Configuration tab to configure properties for the Web service endpoint. For more information, see "Configuring Web Services Using Fusion Middleware Control".
-
As an alternative method of viewing the details for a Web service endpoint, you can instead navigate to the Web Services Server Summary page, as described in "Viewing the Web Services for a Server Using Fusion Middleware Control", which lists all of the Web services, and click the name of the endpoint to navigate to the specific Web Service Endpoint page.
4.1.1.6.2 Viewing the Details for a Java EE Web Service Endpoint
Follow this procedure to view the details for a Java EE Web service endpoint.
-
Navigate to the Web Services Summary page as described in "Viewing the Web Services Summary Page for an Application".
-
In the Web Service Details section of the page, click the Web Services tab and expand the Web service to display the Web service endpoints if they are not already displayed.
Alternatively, click the Web Service Endpoints tab to view a list of Web service endpoints.
-
Click the name of the endpoint to navigate to the Web Service Endpoint page.
-
From the Web Service Endpoint page, you can do the following:
-
Click the Operations tab to see the list of operations for this endpoint.
-
Click the Invocations tab to see the error, invocation, and response statistics associated with invoking the endpoint.
-
Click the WSM Policies tab to see the policies attached to this endpoint, if the endpoint has a valid configuration, and if it is secure.
-
Note:
You can also view details about security violations for an endpoint. For more information, see "Viewing the Security Violations for a Web Service".
As an alternative method of viewing the details for a Web service endpoint, you can instead navigate to the server-wide Web Services Summary page, as described in "Viewing the Web Services for a Server Using Fusion Middleware Control", which lists all of the Web services, and click the name of the endpoint to navigate to the specific Web Service Endpoint page.
4.1.1.6.3 Viewing the Details for a Java EE Web Service Operation
Follow this procedure to view the operations belonging to a Java EE Web service.
-
Navigate to the summary page for the Java EE Web service as described in "Viewing the Summary Page for a Java EE Web Service".
-
In the Web Services tab, click the name of the endpoint that you are interested in.
-
Click the Operations tab of the Web Service Endpoint page to display the operations associated with the endpoint.
-
Click the name of the operation to display more detailed information.
The Web Service Operation page displays information about the operation such as the endpoint URI, the names of the application, Web service, and endpoint to which it is associated, and error, invocation, and response statistics.
For descriptions of the endpoint details and the statistics, see "Viewing Statistics for a Java EE Web Service Operation".
4.1.1.6.4 Viewing the Details for a RESTful Service Application
Follow this procedure to view the details of a RESTful service application.
-
Navigate to the Web Services Application Summary page as described in "Viewing the Web Services Summary Page for an Application".
-
In the Web Service Details section of the page, click the RESTful Services tab.
-
Click the name of the RESTful application to navigate to the RESTful Service Application page.
-
From the RESTful Service Application page, you can do the following:
-
Click the RESTful Resources tab to view the list of resources associated with the RESTful service. For each resource, you can view its name, type, path, invocation count, and average execution time in milliseconds.
-
Click the WSM Policies tab to see the policies attached to this RESTful service, if the RESTful service has a valid configuration, and if it is secure.
-
4.1.1.6.5 Viewing the Details for a RESTful Resource
Follow this procedure to view the details of a RESTful resource.
-
Navigate to the Web Services Application Summary page as described in "Viewing the Web Services Summary Page for an Application".
-
In the Web Service Details section of the page, click the RESTful Services tab.
-
Click the name of the RESTful application to navigate to the RESTful Service Application page.
-
From the RESTful Service Application page, click the RESTful Resources tab to see the list of resources associated with the RESTful service.
-
Click the name of the RESTful resource for which you want to view more information.
The RESTful Resource page displays information about the resource such as the application, module, and RESTful application name; the resource name, type, and path; the number of methods and suppressors locators; and statistics including invocation count and average execution time in milliseconds.
The RESTful Methods tab displays the information about the resource methods, including the method name, return type, path, associated HTTP method, and media type produced. Statistics including invocation count, average execution time, and execution time totals are also displayed.
4.1.2 Viewing Web Service Clients Using Fusion Middleware Control
The steps you follow to view a Web service client depend on the application type (ADF DC or asynchronous Callback client), as described in the following sections.
4.1.2.1 Viewing Connection-Based Web Service Clients
Use the following procedure to view a connection-based Web service client such as an ADF DC Web service client or ADF JAX-WS Indirection Proxy:
-
In the navigation pane, expand the Application Deployments folder to expose the applications in the farm, and select the application.
The Application Deployment home page is displayed.
-
From the Application Deployment menu, select ADF, and then Configure ADF Connections.
-
On the ADF Connections Configuration page, select a connection from the Web Service Connections section of the page, and then select the endpoint from the Configure Web Service list.
-
In the Configure Web Service page, click the tabs to view the client data.
4.1.2.2 Viewing Java EE Web Service Clients
Use the following procedure to view Java EE Web service clients:
-
In the navigation pane, expand the Application Deployments folder to expose the applications in the farm, and select the Java EE application.
The Application Deployment home page is displayed.
-
From the Application Deployment menu, select Web Services.
The Web Services (Java EE) home page is displayed.
-
Select the Java EE Web Service Clients tab to view the clients in the application.
-
Use the Monitoring tab to view the run-time client instances in the application. For more information, see "Viewing Statistics for Java EE Web Service Clients".
-
Use the Configuration tab to view the client ports and attach or detach policies. For more information, see "Attaching Policies Directly to Web Service Clients" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
4.1.2.3 Viewing Asynchronous Web Service Callback Clients
Use the following procedure to view an asynchronous Web service Callback client. Callback clients are used only by asynchronous Web services to return the response to the caller. For more information, see "Developing Asynchronous Web Services" in Developing Oracle Infrastructure Web Services.
-
Navigate to the endpoint for the asynchronous Web service, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click Callback Client in the upper right portion of the endpoint page.
4.1.3 Configuring Web Services Using Fusion Middleware Control
The following sections describe how to configure Web services using Fusion Middleware Control.
-
Configuring Asynchronous Web Services Using Fusion Middleware Control
-
Changing the JMS System User for Asynchronous Web Services Using Fusion Middleware Control
-
Configuring Reliable Messaging Using Fusion Middleware Control
-
Configuring Atomic Transactions Using Fusion Middleware Control
-
Configuring SOAP Over JMS Transport Using Fusion Middleware Control
-
Enabling or Disabling Web Services Using Fusion Middleware Control
-
Enabling or Disabling Public Access to the Web Service WSDL Document Using Fusion Middleware Control
-
Enabling or Disabling SOAP Processing Using Fusion Middleware Control
-
Enabling or Disabling Non-SOAP XML Message Processing Using Fusion Middleware Control
-
Setting the Log Level for Diagnostic Logs Using Fusion Middleware Control
-
Enabling or Disabling the Web Services Test Client Using Fusion Middleware Control
-
Enabling or Disabling the Exchange of Metadata Using Fusion Middleware Control
-
Configuring MTOM-encoded Fault Messages Using Fusion Middleware Control
-
Validating the Request Message Using Fusion Middleware Control
-
Setting the Size of the Request Message Using Fusion Middleware Control
-
Enabling or Disabling Binary Content Caching Using Fusion Middleware Control
4.1.3.1 Configuring Addressing Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable addressing using Fusion Middleware Control, attach the oracle/wsaddr_policy policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the addressing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_addressing_policyto disable an addressing policy configured at a higher scope.
For more information about the addressing policies, see "Addressing Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.2 Configuring Asynchronous Web Services Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
When you invoke a Web service synchronously, the invoking client application waits for the response to return before it can continue with its work. In cases where the response returns immediately, this method of invoking the Web service might be adequate. However, because request processing can be delayed, it is often useful for the client application to continue its work and handle the response later on. By calling a Web service asynchronously, the client can continue its processing, without interrupt, and will be notified when the asynchronous response is returned.
To configure asynchronous Web services using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/async_web_service_policyconfiguration policy to the Web service, as described in "Attaching Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the asynchronous policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_async_web_service_policyto disable an asynchronous policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
You can also configure asynchronous Callback client, as described in "Configuring Asynchronous Web Service Callback Clients".
For information about developing asynchronous Web services, see "Developing Asynchronous Web Services" in Developing Oracle Infrastructure Web Services.
To configure asynchronous Web services using the Configuration tab:
-
Navigate to the Web Services Application Summary page.
-
In the Web Service Details section of the page, expand the Web service to display the Web service endpoints if they are not already displayed.
-
Click the name of the endpoint of the asynchronous Web service to navigate to the Web Service Endpoint page.
For an asynchronous Web service, the Asynchronous flag at the top of the page is set to True. Review the following flags, which provide more information about the asynchronous Web service:
-
Transaction Enabled for Request Queue—Flag that specifies whether transactions are enabled on the request queue.
-
Using Response Queue—Flag that specifies whether a response queue is being used. If set to false, then the response is sent directly to the Web service client, without being stored.
-
Transaction Enabled for Response Queue—Flag that specifies whether transactions are enabled on the response queue.
These flags are configured at design time. For more information, see "Developing Asynchronous Web Services" in Developing Oracle Infrastructure Web Services.
-
-
From the Web Service Endpoint page, click the Configuration tab.
-
Under the Asynchronous Web Service section of the page, you can set the configuration properties defined in Table 4-1.
Note:
The configuration properties defined in Table 4-1 appear and are valid only for asynchronous Web services.
Table 4-1 Configuration Properties for Asynchronous Web Services
Configuration Property Description JMS Request Queue Connection Factory Name
Name of the connection factory for the JMS request queue. The default JMS connection factory,
weblogic.jms.XAConnectionFactory, provided with the base domain is used by default.JMS Request Queue Name
Name of the request queue. The following queue is used by default:
oracle.j2ee.ws.server.async.DefaultRequestQueue.JMS Response Queue Connection Factory Name
Name of the connection factory for the JMS response queue. The default JMS connection factory,
weblogic.jms.XAConnectionFactory, provided with the base domain is used by default.JMS Response Queue Name
Name of the request queue. The following queue is used by default: oracle.j2ee.ws.server.async.DefaultResponseQueue.
JMS System User
The user that is authorized to use the JMS queues. By default, this property is set to
OracleSystemUser.Note: For most users, the
OracleSystemUseris sufficient. However, if you need to change this user to another user in your security realm, you can do so using the instructions provided in "Changing the JMS System User for Asynchronous Web Services Using Fusion Middleware Control". -
Click Apply.
4.1.3.3 Changing the JMS System User for Asynchronous Web Services Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
By default, the JMS System User is set as OracleSystemUser. For most users, this default value is sufficient.
To configure a custom user in your security realm using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/async_web_service_policyconfiguration policy to the Web service and override thejms.access.userconfiguration property, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the asynchronous policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_async_web_service_policyto disable an asynchronous policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To change the JMS System User using the Configuration tab:
-
Access the Configuration tab on the Web Service Endpoint page for the asynchronous Web service as described in "Configuring Asynchronous Web Services Using Fusion Middleware Control".
-
Enter the name of the custom user in the JMS System User field and click Apply.
Note:
The custom user must exist in the security realm and have the permissions required to access the JMS resources.
-
Access the WebLogic Server Administration Console. To do so from Fusion Middleware Control, select the domain in the navigation pane. From the WebLogic Domain menu, select WebLogic Server Administration Console.
-
Log into the WebLogic Server Administration Console using a valid username and password with the required administrative privileges.
-
Click Deployments in the Domain Structure pane and navigate to the corresponding
service_AsynchRequestProcessorMDBorservice_AsynchResponseProcessorMDBMDBs. In these MDB names,serviceis the name of the asynchronous service for which you are changing the user name. -
In the Change Center, select Lock & Edit.
-
Select the MDB name for the request or response MDB. (You will need to update the user name for both the request and response MDBs.) In the Settings page, select the Configuration tab.
-
In the Enterprise Bean Configuration section of the page, enter the custom user name in the Run As Principal Name field and click Save.
Note that the user name you enter in this field must match the user name you entered for the JMS System User in Fusion Middleware Control.
The configuration changes need to be saved in a new deployment plan.
-
Use the Save Deployment Plan Assistant to save the new deployment plan.
-
Repeat steps 7 and 8 for the second MDB. The changes are automatically saved to the new deployment plan.
-
In the Change Center, click Activate Changes.
-
Redeploy the application. For more information, see Chapter 3, "Deploying Web Services Applications."
4.1.3.4 Configuring Reliable Messaging Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable Web services reliable messaging using Fusion Middleware Control, attach the oracle/reliable_messaging_policy policy to the Web service, as described in "Attaching Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the reliable messaging policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_reliable_messaging_policyto disable a reliable messaging configured at a higher scope.
For more information about the reliable messaging policies, see "Reliable Messaging Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.5 Configuring Atomic Transactions Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
Web services support the WS-Coordination and WS-AtomicTransaction (WS-AT) specifications. Therefore, you can configure Web services atomic transactions to enable interoperability between Oracle WebLogic Server and other vendor's transaction processing systems, such as WebSphere, Microsoft .NET, and so on.
To configure Web services atomic transactions policy using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/atomic_transaction_policypolicy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the atomic transactions policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_atomic_transaction_policyto disable an atomic transaction policy configured at a higher scope.
For more information about the atomic transaction policies, see "Atomic Transaction Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To configure atomic transactions for a Web service using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the Atomic Transaction Version field, select the version of the Web service atomic transaction coordination context that is supported. The value specified must be consistent across the entire transaction. Valid values are:
-
WSAT10
-
WSAT11
-
WSAT12
-
Default
If you select Default, all three versions are accepted.
-
-
In the Atomic Transaction Flow Option field, select whether the transaction coordination context is to be passed with the transaction flow into the Web service.
Valid values include:
-
Never—Do not export transaction coordination context. This is the default.
-
Supports—Export transaction coordination context if transaction is available.
-
Mandatory—Export transaction coordination context. An exception is thrown if there is no active transaction.
-
-
Click Apply.
4.1.3.6 Configuring MTOM Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable MTOM using Fusion Middleware Control, attach the oracle/wsmtom_policy configuration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the MTOM policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_mtom_policyto disable an MTOM policy configured at a higher scope.
For more information about the MTOM policies, see "MTOM Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.7 Configuring Fast Infoset Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable Fast Infoset using Fusion Middleware Control, attach the oracle/fast_infoset_service_policy policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the Fast Infoset policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_fast_infoset_service_policyto disable a Fast Infoset policy configured at a higher scope.
For more information about the Fast Infoset policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.8 Configuring Persistence Using Fusion Middleware Control
Note:
The procedures described in this section applies to Oracle Infrastructure Web services only.
To enable persistence using Fusion Middleware Control, attach the oracle/persistence_policy configuration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the persistence policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_persistence_policyto disable a persistence policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.9 Configuring SOAP Over JMS Transport Using Fusion Middleware Control
Note:
The procedures described in this section applies to Oracle Infrastructure Web services only.
Typically, Web services and clients communicate using SOAP over HTTP/S as the connection protocol. You can, however, configure a Web service so that client applications use JMS as the transport.
Using SOAP over JMS transport, Web services and clients communicate using JMS destinations instead of HTTP connections, offering the following benefits:
-
Reliability
-
Scalability
-
Quality of service
As with Web service reliable messaging, if WebLogic Server goes down while the method invocation is still in the queue, it will be handled as soon as WebLogic Server is restarted. When a client invokes a Web service, the client does not wait for a response, and the execution of the client can continue. Using SOAP over JMS transport does require slightly more overhead and programming complexity than HTTP/S.
You can enable and configure SOAP over JMS transport at design time using the @JMSTransportService annotation, as described in "Security and Policy Annotation Reference" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To configure SOAP over JMS transport policy using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/jms_transport_service_policypolicy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the atomic transactions policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_jms_transport_service_policyto disable a SOAP over JMS transport policy configured at a higher scope.
For more information about the SOAP over JMS transport policies, see "SOAP Over JMS Transport Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To configure SOAP over JMS transport using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
When SOAP over JMS transport is enabled, the SOAP over JMS transport configuration properties are displayed in the summary area. The configuration properties are read-only.
-
Click the Configuration tab.
-
In the SOAP Over JMS Enable HTTP WSDL Access field, select True from the menu to enable WSDL access or select False to disable WSDL access.
-
Click Apply.
4.1.3.10 Enabling or Disabling Web Services Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable or disable Web services using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/request_processing_service_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the Web service request processing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_request_processing_policyto disable a Web service request processing policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable or disable a Web service endpoint using the Configuration tab:
-
Navigate to the Web Services Application Summary page.
-
In the Web Service Details section of the page, expand the Web service to display the Web service endpoints if they are not already displayed.
-
Click the name of the endpoint to navigate to the Web Service Endpoint page.
-
From the Web Service Endpoint page, click the Configuration tab.
-
In the Endpoint Enabled field, select Enabled or Disabled from the menu to enable or disable the Web service, respectively.
-
Click Apply.
4.1.3.11 Enabling or Disabling Public Access to the Web Service WSDL Document Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable public access to the Web service WSDL document using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/wsdl_request_processing_service_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the WSDL access policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_wsdl_request_processing_service_policyto disable a WSDL access policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable or disable the display of the Web service WSDL document using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
From the WSDL Enabled field, select True from the menu to enable the display of the WSDL or False to disable the display of the WSDL.
-
Click Apply.
4.1.3.12 Enabling or Disabling SOAP Processing Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable the processing of SOAP requests on the Web service endpoint using Fusion Middleware Control, attach the oracle/soap_request_processing_service_policy configuration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the SOAP processing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_request_processing_service_policyto disable a SOAP processing policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.13 Enabling or Disabling Non-SOAP XML Message Processing Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable an endpoint to receive non-SOAP XML messages that are processed by a user-defined javax.xml.ws.Provider<T>.invoke method using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/pox_http_binding_service_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the non-SOAP XML message processing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_pox_http_binding_service_policyto disable a a non-SOAP XML message processing policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable non-SOAP XML message processing using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the RESTful Enabled field, select True from the menu to enable the feature, or select False to disable the feature.
-
Click Apply.
4.1.3.14 Setting the Log Level for Diagnostic Logs Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
You can set the log level for diagnostic logs at the domain level, as well, as described in "Setting the Log Level for Diagnostic Logs".
To set the log level for diagnostic logs using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/ws_logging_level_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the logging level policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_ws_logging_level_service_policyto disable a logging level policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To set the logging level for diagnostic logs using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the Logging Level field, select the logging level.
-
Click Apply.
4.1.3.15 Enabling or Disabling the Web Services Test Client Using Fusion Middleware Control
You can enable or disable the Web Service Test Client at the domain or Web service endpoint level using Fusion Middleware Control, as described in the following sections:
For more information about the Web Services Test Client, see "Using the Web Services Test Client".
Note:
The procedures described in this section do not impact the availability of the Web Services Test link on the Web Service Endpoint page, which enables you to access the Fusion Middleware Control Test Web Service page. For more information, see "Using the Test Web Service Page in Fusion Middleware Control".
4.1.3.15.1 Enabling or Disabling the Web Services Test Client at the Domain Level Using Fusion Middleware Control
To enable or disable the Web Services Test Client at the domain level using Fusion Middleware Control:
-
Select WebLogic Domain > Administration > General Settings.
-
Click Advanced to display the advanced settings.
-
Toggle the Enable Web Service Test Page flag to enable or disable the Web Services Test Client at the domain level.
-
Click Save.
-
Restart the WebLogic domain.
4.1.3.15.2 Enabling or Disabling the Web Service Test Client at the Web Service Endpoint Level Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable the Web Services Test Client using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/test_page_processing_service_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the Web Services Test Client policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_ws_logging_level_service_policyto disable a Web Services Test Client policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable the Web Service Test Client using the Configuration tab:
-
Navigate to the Web Service Endpoint page as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the Endpoint Test Enabled field, select True from the menu to enable the test endpoint or False to disable the test endpoint.
-
Click Apply.
4.1.3.16 Enabling or Disabling the Exchange of Metadata Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable the exchange of metadata using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/mex_request_processing_service_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the metadata exchange policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_mex_request_processing_service_policyto disable a metadata exchange policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable or disable the exchange of metadata:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the Metadata Exchange Enabled field, select True from the menu to enable the exchange of metadata or False to disable the exchange of metadata.
-
Click Apply.
4.1.3.17 Configuring MTOM-encoded Fault Messages Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable MTOM-encoded fault messages when MTOM is enabled using Fusion Middleware Control, attach the oracle/mtom_encode_fault_service_policy configuration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the MTOM-encoded fault processing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_mtom_encode_fault_service_policyto disable an MTOM-encoded fault processing policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.3.18 Validating the Request Message Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To validate the request message against the schema using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/schema_validation_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the schema validation policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_schema_validation_policyto disable a schema validation policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To enable or disable schema validation using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
In the Schema validation field, select True from the menu to enable schema validation or False to disable schema validation.
-
Click Apply.
4.1.3.19 Setting the Size of the Request Message Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To set the maximum size of the request message using Fusion Middleware Control, use one of the following methods:
-
Attach the
oracle/max_request_size_policyconfiguration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.To disable the maximum request size policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_max_request_size_policyto disable a maximum request size policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
-
Use the Configuration tab, as described below.
To size of the request message using the Configuration tab:
-
Navigate to the Web Service Endpoint page, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click the Configuration tab.
-
Set the Maximum Request Size and the Unit of Maximum Request Size.
-1 sets no limit to the size of the message. Or, you can set a maximum limit to the message by entering a number in the text box and selecting the unit of measurement.
Note:
If you set the Maximum Request Size to -1, indicating that there is no maximum request size, then the Unit of Maximum Request Size setting is irrelevant and defaults to bytes.
-
Click Apply.
4.1.3.20 Enabling or Disabling Binary Content Caching Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
To enable binary content caching using Fusion Middleware Control, attach the oracle/cache_binary_content_policy configuration policy to the Web service, as described in "Attaching Policies to Web Services and Clients Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the binary caching content policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using Fusion Middleware Control" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Attach the
oracle/no_cache_binary_content_policyto disable a binary caching content policy configured at a higher scope.
For more information about the configuration policies, see "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
4.1.4 Configuring Web Service Clients Using Fusion Middleware Control
Note:
The procedures described in this section apply to Oracle Infrastructure Web services only.
For the Web service clients in your application, including ADF data control, and asynchronous Web service Callback clients, you can set the configuration properties defined in Table 4-2.
Table 4-2 Configuration Properties for Web Service Clients
| Configuration Property | Property Name | Description |
|---|---|---|
|
General |
||
|
Endpoint Address |
|
Endpoint URL to which the client will send the request. Note: This property is not available for asynchronous Web service Callback clients. |
|
WS Addressing Reply To |
|
Specifies a callback URL for the ADF Web Services Data Control/Web Services Connection client. The value is used in the WS-addressing |
|
Maintain Session |
|
Flag that specifies whether the session should be maintained. Note: This property is not available for asynchronous Web service Callback clients. |
|
HTTP Chunking |
||
|
Stop Chunking |
|
Flag that specifies whether chunking is enabled for client requests. |
|
Chunking Size (bytes) |
|
Size of the request chunk in bytes. |
|
HTTP Timeout |
||
|
HTTP Read Timeout (ms) |
|
Length of the request read timeout in milliseconds. |
|
HTTP Connection Timeout (ms) |
|
Length of the request connection timeout in milliseconds. |
|
HTTP Basic Authentication |
||
|
HTTP User Name |
(
|
Authenticated HTTP user name. |
|
HTTP User Password |
(
|
Authenticated HTTP user password. |
|
Preemptive |
|
Flag that specifies whether security will be sent with the request without being challenged. |
|
HTTP Proxy |
||
|
Proxy Host |
|
URL of proxy to which client will send the request. |
|
Proxy Port |
|
Port number of the proxy. |
|
Proxy User Name |
|
Valid user name to access the proxy. |
|
Proxy User Password |
|
Valid password to access the proxy. |
|
Proxy Realm |
|
Realm used by the proxy. |
|
Proxy Authentication Type |
|
Authentication type used by the proxy. |
The following procedures describe how to configure ADF DC and asynchronous Web service Callback clients using Fusion Middleware Control.
4.1.4.1 Configuring Connection-based Web Service Clients
The following procedure describes how to configure an ADF DC Web service client.
-
View the ADF DC Web service client, as described in "Viewing Connection-Based Web Service Clients".
-
Click the Configuration tab.
-
Set the configuration values as required. Refer to Table 4-2.
-
Click Apply.
4.1.4.2 Configuring Asynchronous Web Service Callback Clients
The following procedure describes how to configure an asynchronous Web service Callback client. Callback clients are used only by asynchronous Web services to return the response to the caller. For more information, see "Developing Asynchronous Web Services" in Developing Oracle Infrastructure Web Services.
To configure an asynchronous Web service Callback client:
-
Navigate to the endpoint for the asynchronous Web service, as described in "Viewing the Details for a Web Service Endpoint Using Fusion Middleware Control".
-
Click Callback Client in the upper right portion of the endpoint page.
-
Click the Configuration tab.
-
Set the configuration values as required. Refer to Table 4-2.
-
Click Apply.
4.1.5 Managing the WSDL Using Fusion Middleware Control
In some cases, you might not want the Web service WSDL to be accessible to the public. You can enable or disable public access to the WSDL from the Web Service Endpoint page.
Note:
In some cases, a Web service client needs to access a WSDL during invocation. If public access to the WSDL is disabled, the client will need to have a local copy of the WSDL.
4.1.5.1 Viewing the Web Service WSDL Document
Follow the procedure below to display the WSDL document for a Web service.
To display the WSDL document for a Web service:
-
Navigate to the Web Services Application Summary page.
-
In the Web Service Details section of the page, expand the Web service to display the Web service endpoints if they are not already displayed.
-
Click the name of the endpoint to navigate to the Web Service Endpoint page.
-
In the WSDL Document field, click the endpoint name to display the WSDL for the Web service.
4.1.5.2 Enabling or Disabling Public Access to the Web Service WSDL Document
To enable or disable the display of the Web service WSDL document:
-
Using Fusion Middleware Control, see "Enabling or Disabling Public Access to the Web Service WSDL Document Using Fusion Middleware Control".
-
Using WLST, see "Enabling or Disabling Public Access to the Web Service WSDL Document Using WLST".
4.2 Administering Web Services Using WLST
The following sections describe how to perform common Web services administration tasks using WLST.
4.2.1 Viewing the Web Services in a Domain Using WLST
To view all the current Web services in a domain:
-
Connect to the running instance of WebLogic Server for which you want to view the Web services as described in "Accessing the Web Services Custom WLST Commands".
-
Use either the
listWebServices()or thelistWSMPolicySubjects()WLST command to display a list of the Web services. If you don't specify a Web service application, the command lists all services in all applications for every server instance in the domain.This is an example of the
listWebServices()command:wls:/base_domain/serverConfig> listWebServices() /base_domain/AdminServer/jaxwsejb30ws : moduleName=jaxwsejb, moduleType=web, serviceName=JaxwsWithHandlerChainBeanService moduleName=jaxwsejb, moduleType=web, serviceName=WsdlConcreteService moduleName=jaxwsejb, moduleType=web, serviceName=EchoEJBService moduleName=jaxwsejb, moduleType=web, serviceName=CalculatorService moduleName=jaxwsejb, moduleType=web, serviceName=DoclitWrapperWTJService /base_domain/AdminServer/webservicesJwsSimple : moduleName=webservicesJwsSimple!SimpleImplService, moduleType=wls, serviceName=examples.webservices.jws_basic.simple.SimpleImpl /base_domain/AdminServer/CalWSBA : moduleName=CalWSBA#1!CalculatorService, moduleType=wls, serviceName=CalculatorService /base_domain/AdminServer/SimpleRestApp : moduleName=SimpleRestApp, moduleType=web, serviceName=SimpleRestServiceService /base_domain/AdminServer/SimpleJAXWS : moduleName=SimpleJAXWS#1!SimpleImplService, moduleType=wls, serviceName=SimpleImplService moduleName=SimpleJAXWS#1!SimpleEjbService, moduleType=wls, serviceName=SimpleEjbServiceThis is an example of the
listWSMPolicySubjects()command:wls:/base_domain/serverConfig> listWSMPolicySubjects() Application: /weblogic/base_domain/SimpleRestApp Assembly: #SimpleRestApp Subject: WS-Service({http://rest.jaxws.ws.j2ee.oracle/}SimpleRestServiceService#SimpleRestServicePort) Application: /weblogic/base_domain/jaxwsejb30ws Assembly: #jaxwsejb Subject: WS-Service({http://host.example.com/targetNamespace}EchoEJBService#EchoEJBServicePort) Subject: WS-Service({http://host.examplecom/jaxws/tests/concrete}WsdlConcreteService#WsdlConcretePort) Subject: WS-Service({http://host.example.com/jaxws/tests}CalculatorService#CalculatorPort) Subject: WS-Service({http://soapinterop.org/DoclitWrapperWTJ}DoclitWrapperWTJService#DoclitWrapperWTJPort) Subject: WS-Service({http://j2ee.tests.ejb.impl/}JaxwsWithHandlerChainBeanService#JaxwsWithHandlerChainBeanPort) Application: /weblogic/base_domain/em Assembly: #default Subject: WS-Client({http://host.example.com/jaxws/tests}CalculatorService#CalculatorPort) -
Set the
detailargument of thelistWSMPolicySubjectsorlistWebServicescommand totrueto view the endpoint (port) and policy details for all applications and composites in the domain, the secure status of the endpoints, any configuration overrides and constraints, and if the endpoints have a valid configuration. Because you can specify the priority of a global or directly attached policy (using thereference.priorityconfiguration override), theeffectivefield indicates if directly attached policies are in effect for the endpoint.Note:
To simplify endpoint management, all directly attached policies are shown in the output regardless of whether they are in effect for the endpoint. In contrast, only globally attached policies that are in effect for the endpoint are displayed.
An endpoint is considered secure if the policies attached to it (either directly or externally) enforce authentication, authorization, or message protection behaviors.
wls:/base_domain/serverConfig> listWebServices(detail='true') /weblogic/base_domain/jaxwsejb30ws : moduleName=jaxwsejb, moduleType=web, serviceName=JaxwsWithHandlerChainBeanService JaxwsWithHandlerChainBeanPort http://host.example.com:17001/jaxwsejb/JaxwsWithHandlerChainIntf URI="oracle/mex_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/mtom_encode_fault_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/max_request_size_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="max.request.size", value="-1" URI="oracle/request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/soap_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/ws_logging_level_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="logging.level", value="" URI="oracle/test_page_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wsdl_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wss_saml_or_username_token_over_ssl_service_ policy", category=security, policy-status=enabled; source=global policy set "test", scope="DOMAIN('*')"; reference-status=enabled; effective=true The policy subject is secure in this context. moduleName=jaxwsejb, moduleType=web, serviceName=WsdlConcreteService WsdlConcretePort http://host.example.com:17001/jaxwsejb/WsdlAbstract URI="oracle/mex_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/mtom_encode_fault_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/max_request_size_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="max.request.size", value="-1" URI="oracle/request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/soap_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/ws_logging_level_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="logging.level", value="" URI="oracle/test_page_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wsdl_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wss_saml_or_username_token_over_ssl_service_ policy", category=security, policy-status=enabled; source=global policy set "test", scope="DOMAIN('*')"; reference-status=enabled; effective=true The policy subject is secure in this context.This is an example for the
listWSMPolicySubjectscommand. It lists the detail output for theWsdlConcretePortsubject.wls:/base_domain/serverConfig> listWSMPolicySubjects ('jaxwsejb30ws', '#jaxwsejb', None, detail='true') Application: /WLS/rc6_domain/jaxwsejb30ws Assembly: #jaxwsejb Subject: WS-Service({http://www.oracle.com/jaxws/tests/concrete}WsdlConcreteService#WsdlConcretePort) URI=/"oracle/mex_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/mtom_encode_fault_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/max_request_size_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="max.request.size", value="-1" URI="oracle/request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/soap_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/ws_logging_level_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="logging.level", value="" URI="oracle/test_page_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wsdl_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true The policy subject is not secure in this context. Subject: WS-Service({http://oracle.j2ee.tests.ejb.impl/}JaxwsWithHandlerChainBeanService#JaxwsWithHandlerChainBeanPort) URI="oracle/mex_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/mtom_encode_fault_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/max_request_size_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="max.request.size", value="-1" URI="oracle/request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/soap_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/ws_logging_level_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="logging.level", value="" URI="oracle/test_page_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wsdl_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true The policy subject is not secure in this context. ...
For more information about the listWSMPolicySubjects and listWebServices commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.2 Viewing the Web Services in Your Application Using WLST
To view the Web services in your application:
-
Connect to the running instance of WebLogic Server to which the application is deployed as described in "Accessing the Web Services Custom WLST Commands".
-
Use the
listWebServicesWLST command to display a list of the Web services in your application. You must specify the complete application path name to identify the application and the server instance to which it is deployed.listWebServices (application,composite,[detail]
For example:
wls:/wls-domain/serverConfig>listWebServices("wls-domain/AdminServer/jaxwsejb30ws") /wls-domain/AdminServer/jaxwsejb30ws: moduleName=jaxwsejb,moduleType=web,serviceName={http://namespace/}JaxwsWithHandlerChainBeanService moduleName=jaxwsejb, moduleType=web, serviceName={http://namespace/}WsdlConcreteService moduleName=jaxwsejb, moduleType=web, serviceName={http://namespace/}EchoEJBService moduleName=jaxwsejb, moduleType=web, serviceName={http://namespace/}CalculatorService moduleName=jaxwsejb, moduleType=web, serviceName={http://namespace/}DoclitWrapperWTJService
For details about the listWebServices command, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.3 Viewing the Details for a Web Service Endpoint Using WLST
To view the details for a Web service endpoint (port):
-
Connect to the running instance of WebLogic Server to which the application is deployed as described in "Accessing the Web Services Custom WLST Commands".
-
Use the
listWebServicesWLST command to display a list of the Web services in your application as described in "Viewing the Web Services in Your Application Using WLST". -
Use the
listWebServicePortscommand to display the endpoint name and endpoint URL for a Web service.listWebServicePorts(application,moduleOrCompName,moduleType,serviceName)
For example, to display the endpoint for the
WsdlConcreteService:wls:/wls-domain/serverConfig> listWebServicePorts ('jaxwsejb30ws','jaxwsejb','web','WsdlConcreteService') WsdlConcretePort http://host.example.com:7001/jaxwsejb/WsdlAbstract -
Use the
listWebServicePoliciescommand to view the policies that are attached to a Web service endpoint.listWebServicePolicies(application,moduleOrCompName,moduleType,serviceName,subjectName)
For example, to view the policies attached to the
WsdlConcretePortendpoint and any policy override settings:wls:/wls_domain/serverConfig> listWebServicePolicies ("jaxwsejb30ws", "jaxwsejb","web","WsdlConcreteService","WsdlConcretePort") WsdlConcretePort : URI="oracle/mex_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/mtom_encode_fault_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/max_request_size_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="max.request.size", value="-1" URI="oracle/request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/soap_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/ws_logging_level_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true Property name="logging.level", value="" URI="oracle/test_page_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wsdl_request_processing_service_policy", category=wsconfig, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true URI="oracle/wss_saml_or_username_token_over_ssl_service_policy", category=security, policy-status=enabled; source=global policy set "test_PS", scope="DOMAIN('*')"; reference-status=enabled; effective=true The policy subject is secure in this context.
For more information about these WLST commands and their arguments, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.4 Viewing Web Service Clients Using WLST
Use the following procedure to view the Web service clients using WLST commands:
-
Connect to the running instance of WebLogic Server to which the application is deployed as described in "Accessing the Web Services Custom WLST Commands".
-
Use the
listWebServiceClientsWLST command to display a list of the Web service clients.listWebServiceClients(application,[detail])
This command enables you to list the clients for an application or a domain. If you do not specify an application, the command outputs information, including the module for all the Web service clients in all applications in every server instance in the domain. To view details about each client, including the endpoint and policies, set the
detailargument totrue.For example:
wls:/infra/serverConfig> listWebServiceClients(detail='true') /infra/AdminServer/ADFDCDecoupling_Project1_ADFDCDecoupling-1 : moduleName=testadfbc, moduleType=wsconn, serviceRefName=AppModuleService AppModuleServiceSoapHttpPort serviceWSDLURI=http://adc1140275.example.com:7001/ADFBCDecoupling-ADFBCDecoupling-context-root/AppModuleService?wsdl URI="oracle/wss10_saml_token_with_message_protection_client_ policy", category=security, policy-status=enabled; source=local policy set; reference-status=enabled; effective=true The policy subject is secure in this context.ADF clients are specified by the
moduleType=wsconnargument in the output.For more information about the WLST commands and their arguments, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5 Configuring Web Services Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
Oracle Infrastructure Web service providers implement the java.xml.ws.Provider interface. On the Web Service Endpoint page, they display the Implementation Class and provide a subset of configuration properties.
You configure the Web service endpoint using WLST by attaching one of the configuration policies defined in "Configuration Policies" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
The following sections describe how to perform common Web services configuration tasks using WLST.
-
Configuring the JMS System User for Asynchronous Web Services Using WLST
-
Enabling or Disabling Public Access to the Web Service WSDL Document Using WLST
-
Enabling or Disabling the Processing of SOAP Requests Using WLST
-
Enabling or Disabling Non-SOAP XML Message Processing Using WLST
-
Enabling or Disabling the Web Services Test Client Using WLST
-
Enabling or Disabling MTOM-encoded SOAP Fault Messages Using WLST
4.2.5.1 Configuring Addressing Using WLST
To configure Web services addressing using WLST:
-
Attach the
oracle/wsaddr_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/wsaddr_policy") Policy reference "oracle/wsaddr_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/wsaddr_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/wsaddr_policy','reference.priority','10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/wsaddr_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the addressing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an addressing policy configured at a higher scope, attach the
oracle/no_addressing_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_addressing_policy") Policy reference "oracle/no_addressing_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.2 Configuring Asynchronous Web Services Using WLST
To configure asynchronous Web services:
-
Attach the
oracle/async_web_service_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/async_web_service_policy") Policy reference "oracle/async_web_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/async_web_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/async_web_service_policy','jms.queue','myDefaultRequestQueue') The configuration override property "jms.queue" having value "myDefaultRequestQueue" has been added to the reference to policy with URI "oracle/async_web_service_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the asynchronous policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an asynchronous policy configured at a higher scope, attach the
oracle/no_async_web_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_async_web_service_policy") Policy reference "oracle/no_async_web_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.3 Configuring the JMS System User for Asynchronous Web Services Using WLST
To configure the JMS system user for asynchronous Web services:
-
Attach the
oracle/async_web_service_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/async_web_service_policy") Policy reference "oracle/async_web_service_policy" added. -
Configure the
jms.access.userpolicy configuration property using thesetWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/async_web_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/async_web_service_policy','jms.access.user','OracleSystemUser') The configuration override property "jms.access.user" having value "OracleSystemUser" has been added to the reference to policy with URI "oracle/async_web_service_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the asynchronous policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an asynchronous policy configured at a higher scope, attach the
oracle/no_async_web_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_async_web_service_policy") Policy reference "oracle/no_async_web_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.4 Configuring Reliable Messaging Using WLST
To configure Web services reliable messaging using WLST:
-
Attach the
oracle/reliable_messaging_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/reliable_messaging_policy") Policy reference "oracle/reliable_messaging_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/reliable_messaging_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/reliable_messaging_policy','acknowledgement.interval','P0DT01S') The configuration override property "acknowledgement.interval" having value "P0DT01S" has been added to the reference to policy with URI "oracle/reliable_messaging_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the Web service reliable messaging policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a reliable messaging policy configured at a higher scope, attach the
oracle/no_reliable_messaging_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_reliable_messaging_policy") Policy reference "oracle/no_reliable_messaging_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.5 Configuring Atomic Transactions Using WLST
To configure Web services atomic transactions:
-
Attach the
oracle/atomic_transaction_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/atomic_transaction_policy") Policy reference "oracle/atomic_transaction_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/atomic_transaction_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/atomic_transaction_policy','version','WSAT11') The configuration override property "version" having value "WSAT11" has been added to the reference to policy with URI "oracle/atomic_transaction_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the Web service atomic transaction policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an atomic transaction policy configured at a higher scope, attach the
oracle/no_atomic_transaction_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_atomic_transaction_policy") Policy reference "oracle/no_atomic_transaction_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.6 Configuring MTOM Using WLST
To configure MTOM on the Web service using WLST:
-
Attach the
oracle/wsmtom_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/wsmtom_policy") Policy reference "oracle/wsmtom_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/wsmtom_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/wsmtom_policy','reference.priority','10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/wsmtom_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the Web service atomic transaction policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an MTOM policy configured at a higher scope, attach the
oracle/no_mtom_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_mtom_policy") Policy reference "oracle/no_mtom_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.7 Configuring Fast Infoset Using WLST
To configure Fast Infoset on the Web service or client using WLST:
-
Attach the
oracle/fastinfoset_service_policyororacle/fastinfoset_client_policypolicy to the Web service or client, respectively, using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/fast_infoset_service_policy") Policy reference "oracle/fast_infoset_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/fast_infoset_service_policy" and "oracle/fast_infoset_client_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/fast_infoset_client_policy','fast.infoset.content.negotiation','OPTIMISTIC') The configuration override property "fast.infoset.content.negotiation" having value "OPTIMISTIC" has been added to the reference to policy with URI "oracle/fast_infoset_client_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the Web service Fast Infoset policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a Fast Infoset policy configured at a higher scope, attach the
oracle/no_fast_infoset_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_fast_infoset_service_policy") Policy reference "oracle/no_fast_infoset_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.8 Configuring SOAP Over JMS Transport Using WLST
To configure SOAP over JMS transport on the Web service or client using WLST:
-
Attach the
oracle/jms_transport_service_policyororacle/jms_transport_client_policypolicy to the Web service or client, respectively, using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/jms_transport_service_policy") Policy reference "oracle/jms_transport_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/jms_transport_service_policy" and "oracle/jms_transport_client_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/jms_transport_service_policy','jndi.connection.factory.name','com.oracle.webservices.jms.ConnectionFactory') The configuration override property "jndi.connection.factory.name" having value "com.oracle.webservices.jms.ConnectionFactory" has been added to the reference to policy with URI "oracle/jms_transport_service_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the SOAP over JMS transport policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a SOAP over JMS transport policy configured at a higher scope, attach the
oracle/no_jms_transport_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_jms_transport_service_policy") Policy reference "oracle/no_jms_transport_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.9 Configuring Persistence Using WLST
To configure the persistence using WLST:
-
Attach the
oracle/persistence_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/persistence_policy") Policy reference "oracle/persistence_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/persistence_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.Note:
For Java SE clients, you can configure
oracle:jrf:Coherenceonly.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/persistence_policy','providerName', 'oracle:jrf:Coherence') The configuration override property "peristence_policy" having value "oracle:jrf:Coherence" has been added to the reference to policy with URI "oracle/persistence_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the persistence policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a persistence policy configured at a higher scope, attach the
oracle/no_persistent_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_persistent_policy") Policy reference "oracle/no_persistent_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.10 Enabling or Disabling Web Services Using WLST
When a Web service application is deployed, the Web service endpoint is enabled by default if no errors are encountered. If there are errors, the Web service application is deployed, but the Web service endpoint is not enabled.
You may need to temporarily make a Web service unavailable by disabling the Web service. For example, you may need to correct an invalid policy reference. When you disable a Web service, requests to the Web service will fail. To disable a Web service, you must make the endpoint on which the Web service receives requests unavailable.
To enable a Web service endpoint using WLST:
-
Attach the
oracle/request_processing_service_policypolicy using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/request_processing_service_policy") Policy reference "oracle/request_processing_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/request_processing_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride("oracle/request_processing_service_policy", "reference.priority", "10")For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
To disable the Web service access policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a Web service access policy configured at a higher scope, attach the
oracle/no_pox_http_binding_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_request_processing_service_policy") Policy reference "oracle/no_request_processing_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.11 Enabling or Disabling Public Access to the Web Service WSDL Document Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable public access to the Web service WSDL document using WLST:
-
Attach the
oracle/wsdl_request_processing_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/wsdl_request_processing_service_policy") Policy reference "oracle/wsdl_request_processing_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/wsdl_request_processing_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/wsdl_request_processing_service_policy','reference.priority,'10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/wsdl_request_processing_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the WSDL access policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a WSDL access policy configured at a higher scope, attach the
oracle/no_wsdl_request_processing_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_wsdl_request_processing_service_policy") Policy reference "oracle/no_wsdl_request_processing_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.12 Enabling or Disabling the Processing of SOAP Requests Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable the processing of SOAP requests using WLST:
-
Attach the
oracle/soap_request_processing_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/soap_request_processing_service_policy") Policy reference "oracle/soap_request_processing_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/soap_request_processing_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/soap_request_processing_service_policy','reference.priority', '10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/soap_request_processing_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the SOAP request processing policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a SOAP request processing policy configured at a higher scope, attach the
oracle/no_wsdl_request_processing_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_soap_request_processing_service_policy") Policy reference "oracle/no_soap_request_processing_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.13 Enabling or Disabling Non-SOAP XML Message Processing Using WLST
To enable an endpoint to receive non-SOAP XML messages that are processed by a user defined javax.xml.ws.Provider<T>.invoke method using WLST:
-
Attach the
oracle/pox_http_binding_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/pox_http_binding_service_policy") Policy reference "oracle/pox_http_binding_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/pox_http_binding_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/pox_http_binding_service_policy','reference.priority,'10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/pox_http_binding_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the non-SOAP XML message policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a non-SOAP XML message policy configured at a higher scope, attach the
oracle/no_pox_http_binding_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_pox_http_binding_service_policy") Policy reference "oracle/no_pox_http_binding_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.14 Setting the Log Level for Diagnostic Logs Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To set the logging level for diagnostic logs for the Web service endpoint using WLST:
-
Attach the
oracle/ws_logging_level_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/ws_logging_level_policy") Policy reference "oracle/ws_logging_level_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/ws_logging_level_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/ws_logging_level_policy','logging.level', 'INFO') The configuration override property "loggging.level" having value "INFO" has been added to the reference to policy with URI "oracle/ws_logging_level_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the log level policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a log level policy configured at a higher scope, attach the
oracle/no_ws_logging_level_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_ws_logging_level_policy") Policy reference "oracle/no_ws_logging_level_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.15 Enabling or Disabling the Web Services Test Client Using WLST
You can enable or disable the Web Services Test Client, as described in "Using the Web Services Test Client", at the domain or Web service endpoint level:
-
"Enabling or Disabling the Web Services Test Client at the Domain Level Using WLST"
-
"Enabling or Disabling the Web Services Test Client at the Web Service Endpoint Level Using WLST"
Note:
The procedures described in this section do not impact the availability of the Web Services Test link on the Web Service Endpoint page, which enables you to access the Fusion Middleware Control Test Web Service page. For more information, see "Using the Test Web Service Page in Fusion Middleware Control".
4.2.5.15.1 Enabling or Disabling the Web Services Test Client at the Domain Level Using WLST
To enable or disable the Web services Test Client at the domain level, use set the WebServiceTestEnable property for the domain to true to enable the test client and to false to disable it.
For example, to enable the Web Services Test Client at the domain level using WLST:
wls:/wls-domain/serverConfig> edit() Location changed to edit tree. This is a writable tree with DomainMBean as the root. To make changes you will need to start an edit session via StartEdit(). For more help, use help('edit') wls:/mydomain/edit> startEdit() Starting an edit session ... Started edit session, please be sure to save and activate your changes once you are done. wls:/mydomain/edit> cd('WebserviceTestpage') wls:/mydomain/edit/WebserviceTestpage !> cd('new_domain') wls:/mydomain/edit/WebserviceTestpage/new_domain !> set('Enabled','true') wls:/mydomain/edit/WebserviceTestpage/new_domain !> save() Saving all your changes ... Saved all your changes successfully. wls:/mydomain/edit/WebserviceTestpage/new_domain !> activate() Activating all your changes, this may take awhile ... The edit lock associated with the edit session is released once the activation is complete. Activation completed wls:/mydomain/edit/WebserviceTestpage/new_domain !>
For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.15.2 Enabling or Disabling the Web Services Test Client at the Web Service Endpoint Level Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable the Web services test client at the Web service endpoint level using WLST:
-
Attach the
oracle/test_page_processing_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/test_page_processing_service_policy") Policy reference "oracle/test_page_processing_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/test_page_processing_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/test_page_processing_service_policy','reference.priority,'10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/test_page_processing_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the Web Services Test Client policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a Web Services Test Client policy configured at a higher scope, attach the
oracle/no_ws_logging_level_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_test_page_processing_service_policy") Policy reference "oracle/no_test_page_processing_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.16 Enabling or Disabling the Exchange of Metadata Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable the exchange of Web service metadata using WLST:
-
Attach the
oracle/mex_request_processing_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/mex_request_processing_service_policy") Policy reference "oracle/mex_request_processing_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/mex_request_processing_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/mex_request_processing_service_policy','reference.priority,'10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/mex_request_processing_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the metadata exchange policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a metadata exchange policy configured at a higher scope, attach the
oracle/no_mex_request_processing_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_mex_request_processing_service_policy") Policy reference "oracle/no_mex_request_processing_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.17 Enabling or Disabling MTOM-encoded SOAP Fault Messages Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable the creation of MTOM-encoded SOAP fault messages when MTOM is enabled using WLST:
-
Attach the
oracle/mtom_encode_fault_service_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/mtom_encode_fault_service_policy") Policy reference "oracle/mtom_encode_fault_service_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/mtom_encode_fault_service_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/mtom_encode_fault_service_policy','reference.priority,'10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/mtom_encode_fault_service_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the MTOM-encoded fault message policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable an MTOM-encoded fault message policy configured at a higher scope, attach the
oracle/no_mtom_encode_fault_service_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_mtom_encode_fault_service_policy") Policy reference "oracle/no_mtom_encode)fault_service_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.18 Validating the Request Message Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable the validation of request messages using WLST:
-
Attach the
oracle/schema_validation_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/schema_validation_policy") Policy reference "oracle/schema_validation_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/schema_validation_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/schema_validation_policy','reference.priority', '10') The configuration override property "reference.priority" having value "10" has been added to the reference to policy with URI "oracle/schema_validation_policy".For more information about overriding the
reference.priorityconfiguration property, see "Specifying the Priority of a Policy Attachment" in Securing Web Services and Managing Policies with Oracle Web Services Manager. -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the schema validation policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a schema validation policy configured at a higher scope, attach the
oracle/no_schema_validation_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_schema_validation_policy") Policy reference "oracle/no_schema_validation_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.19 Setting the Maximum Size of the Request Message Using WLST
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To set the maximum size of the request message using WLST:
-
Attach the
oracle/max_request_size_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/max_request_size_policy") Policy reference "oracle/max_request_size_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/max_request_size_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/max_request_size_policy','max.request.size', '-1') The configuration override property "max.request.size" having value "-1" has been added to the reference to policy with URI "oracle/max_request_size_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the maximum request size policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a maximum request size policy configured at a higher scope, attach the
oracle/no_max_request_size_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_max_request_size_policy") Policy reference "oracle/no_max_request_size_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.5.20 Configuring Binary Caching of Content
Note:
The procedures described in this section apply to Oracle Infrastructure Web services and providers only.
To enable and configure the binary caching of content using WLST:
-
Attach the
oracle/cache_binary_content_policyto the Web service using theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/cache_binary_content_policy") Policy reference "oracle/cache_binary_content_policy" added. -
Configure the policy using the
setWSMPolicyOverridecommand. For a list of configuration properties that you can override, see "oracle/cache_binary_content_policy" in Securing Web Services and Managing Policies with Oracle Web Services Manager.wls:/wls_domain/serverConfig> setWSMPolicyOverride('oracle/cache_binary_content_policy','mode', 'com.oracle.webservices.api.CacheBinaryContentMode.BINARY') The configuration override property "mode" having value "com.oracle.webservices.api.CacheBinaryContentMode.BINARY" has been added to the reference to policy with URI "oracle/cache_binary_content_policy". -
Commit the session using the
commitWSMSessioncommand, for example:wls:/wls_domain/serverConfig> commitWSMSession() The policy set for subject "/weblogic/base_domain/jaxwsejb30ws|#jaxwsejb|WS-Service({http://ejb.oracle.com/targetNamespace}EchoEJBService#EchoEJBServicePort)" was saved successfully.
To disable the binary content caching policy, perform one of the following steps:
-
Detach the policy. For more information, see "Detaching Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
Disable the policy. For more information, see "Enabling and Disabling Directly Attached Policies Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
To disable a binary content caching policy configured at a higher scope, attach the
oracle/no_cache_binary_content_policyusing theattachWSMPolicycommand. For complete details, see "Attaching Policies Directly Using WLST" in Securing Web Services and Managing Policies with Oracle Web Services Manager.For example:
wls:/wls_domain/serverConfig> attachWSMPolicy("oracle/no_cache_binary_content_policy") Policy reference "oracle/no_cache_binary_content_policy" added.For more information about the WLST commands, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.
4.2.6 Configuring Web Service Clients Using WLST
Use the following procedure to configure the Web service client endpoint (port) using WLST:
-
Connect to the running instance of WebLogic Server to which the application is deployed as described in "Accessing the Web Services Custom WLST Commands".
-
Use the
listWebServiceClientsWLST command to display a list of the Web service clients in your application as described in "Viewing Web Service Clients Using WLST". -
Use the
listWebServiceClientPortscommand to display the endpoint name and endpoint URL for a Web service client.listWebServiceClientPorts(application,moduleOrCompName,moduleType,serviceRefName)
For example, to display the endpoint for the service reference
client:wls:/wls-domain/serverConfig> listWebServiceClientPorts('/base_domain/AdminServer/application1#V2.0', 'test1', 'wsconn', 'client') HelloWorld_pt serviceWSDLURI=http://namespace/infra/services/default/HelloWorld/client?wsdl
-
Use the
listWebServiceClientStubPropertiescommand to view the configuration details for a Web service client endpoint.listWebServiceClientStubProperties(application, moduleOrCompName, moduleType, serviceRefName,portInfoName)
For example, to view the configuration details for the
HelloWorld_pt:wls:/wls-domain/serverConfig> listWebServiceClientStubProperties('/base_domain/AdminServer/application1#V2.0', 'test1','wsconn','client','HelloWorld_pt') keystore.recipient.alias=A1 saml.issuer.name=B1 user.roles.include=C1
Alternatively, you can set the
detailargument totruein thelistWebServiceClientscommand to view the configuration details for the endpoint as shown in "Viewing Web Service Clients Using WLST". -
Do one of the following:
-
Use the
setWebServiceClientStubPropertycommand to set or change a single stub property of a Web service client endpoint. Specify the property to be set or changed using thepropNameandpropValuearguments. To remove a property, specify a blank value for thepropValueargument.setWebServiceClientStubProperty(application,moduleOrCompName,moduleType, serviceRefName,portInfoName,propName,[propValue])
For example, to change the
keystore.recipient.alias tooraclefor theHelloWorld_pt, use the following command:wls:/wls-domain/serverConfig> setWebServiceClientStubProperty('/base_domain/AdminServer/application1#V2.0', 'test1', 'wsconn', 'client', 'HelloWorld_pt', 'keystore.recipient.alias', 'oracle')
-
Use the
setWebServiceClientStubPropertiescommand to configure the set of properties of a Web service client endpoint. Specify the properties to be set or changed using thepropertiesargument.setWebServiceClientStubProperties(application, moduleOrCompName, moduleType, serviceRefName, portInfoName, properties)
This command configures or resets all of the stub properties for the OWSM client security policy attached to the client. Each property that you list in the command is set to the value you specify. If a property that was previously set is not explicitly specified in this command, it is reset to the default for the property. If no default exists, the property is removed.
For more information about the client properties that you can set, see Table 4-2, "Configuration Properties for Web Service Clients". When specifying these properties, use the format shown in the Property Name column.
You can also set the properties described in "Overview of Policy Configuration Overrides" in Securing Web Services and Managing Policies with Oracle Web Services Manager.
-
For more information about these WLST commands and their arguments, see "Web Services Custom WLST Commands" in WLST Command Reference for Infrastructure Components.