D Enable Administration Port in Oracle Identity Governance
Important pre-requisite:
It is important that the domain is configured initially with non-secure mode.
Before enabling administration port(s), ensure that OIG with SSL configuration is completed and all the use cases are working as expected. Admin port enablement should be done post enablement of SSL configuration. Also, ensure that, OIM-SOA integration is also completed as documented at Integrating Oracle Identity Governance with Oracle SOA Suite.
When you enable the administration ports in OIG weblogic domain, the following configuration must be performed for the OIG to work seamlessly.
The administration port accepts only secure and SSL traffic. WebLogic Server provides an option to enable administration ports for all the servers in the domain.
Note:
To convert the node from non-secure to secure, use the remote console.Admin port enabled at domain level.
- Enable Admin Port at Domain Level:
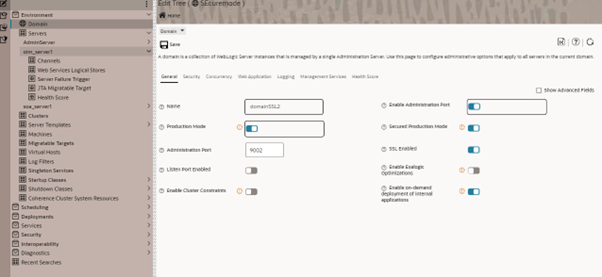
Note:
Restart the servers using administration port as shown below:
sh startManagedWebLogic_new.sh soa_server1 https://<hostname>:9002 production
sh startManagedWebLogic_new.sh oim_server1 https://<hostname>:9002 production
Administration port enabled at managed server level.
After the admin ports are enabled, the following must be followed.
- Access the WLS console using the admin port.
Note:
The WLS console cannot be accessed by using any other option.Example:
https://<host name>:9002, where 9002 is admin port (not SSL port). - Access the EM console using admin port.
Example:
https://<host name>:9002/em - OIM uses the SSL port (14001 is default port).
Example:
https://<host name>:14001/identity/ - SOA uses the SSL port (7004 is default port).
Example:
https://<host name>:7004/soa-infra - The SOA admin user allows OIM to communicate with SOA.
By default, OIM uses "weblogic" user as SOA Admin user. Once you enable the admin ports, the OIM-SOA integration stops working while handling the requests due to the following error. A "weblogic" user is an administrator and hence it forces us to use admin ports.
oracle.bpel.services.workflow.client.WorkflowServiceClientException: javax.naming.AuthenticationException: User 'principals=[weblogic, Administrators]' has administration role. All tasks by administrators must go through an Administration Port.
To resolve the above error, follow the below steps:
You must create a new user (non-admin user) synonymous with "weblogic" user with the required privileges.
- Log in to Enterprise Manager.
- Navigate to “domain XX”->Security->Security Realms->myrealms->’Users and roles tab.
- Click on Create to create a user.
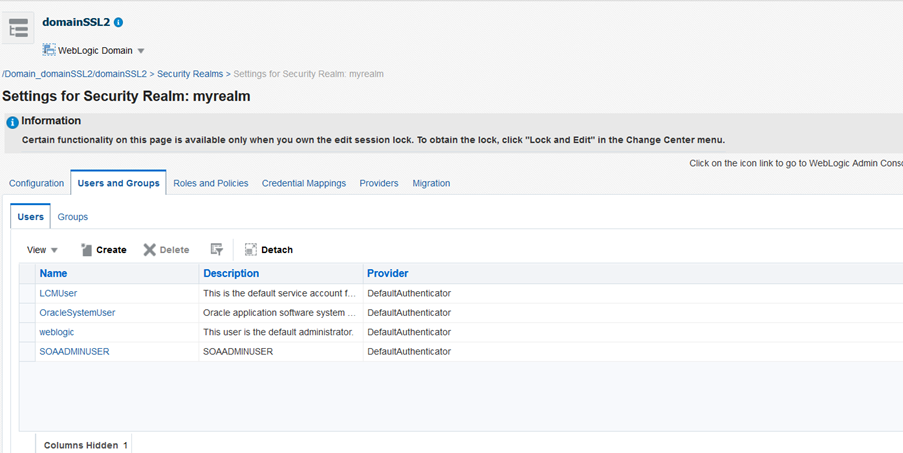
Example: SOAADMINUSER
- Log in into OIM and create the same user in OIM with the same password.(Login name: SOAADMINUSER). For more details, see Creating a User.
- Let us create an application role. To create an application role, follow the below steps.
- Navigate to Weblogic Domain ->Security->Application Roles
- Select soa-infra from the Application Stripe drop-down.
- Click Create to create a role.
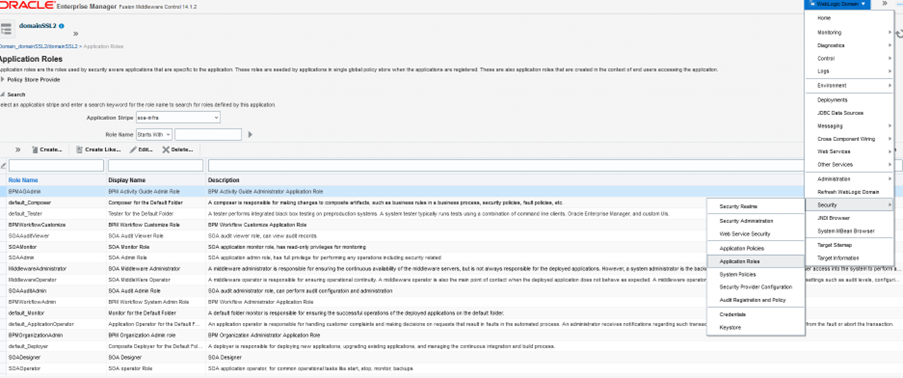
Example: OIGSOAROLE
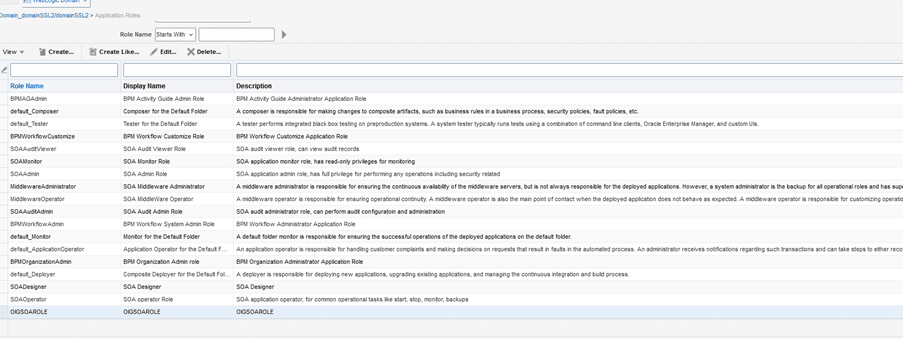
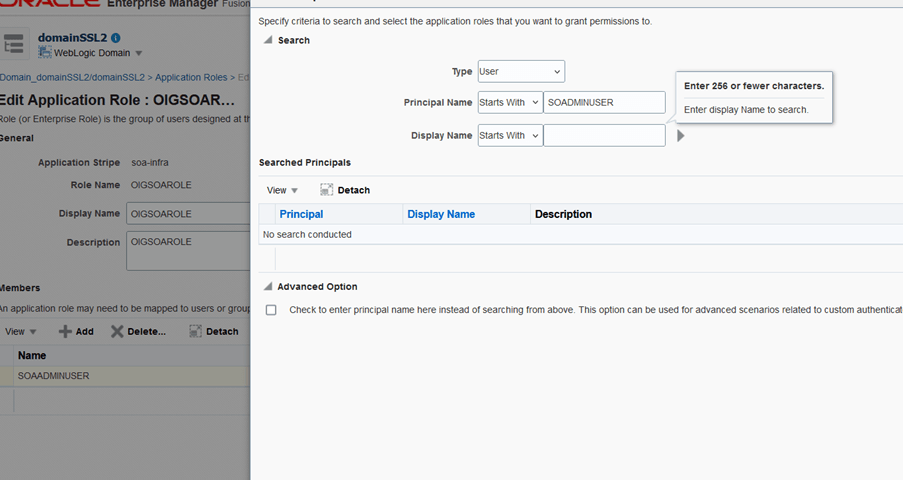
- Select the role and click Edit.
- Select User from the Type drop-down.
- Search “SOAADMINUSER”.
- Add the user (SOAADMINUSER) to this OIGSOAROLE role.
- Let us create an application policies. To create application policies, perform the following:
- Navigate to Weblogic Domain ->Security->Application Policies.
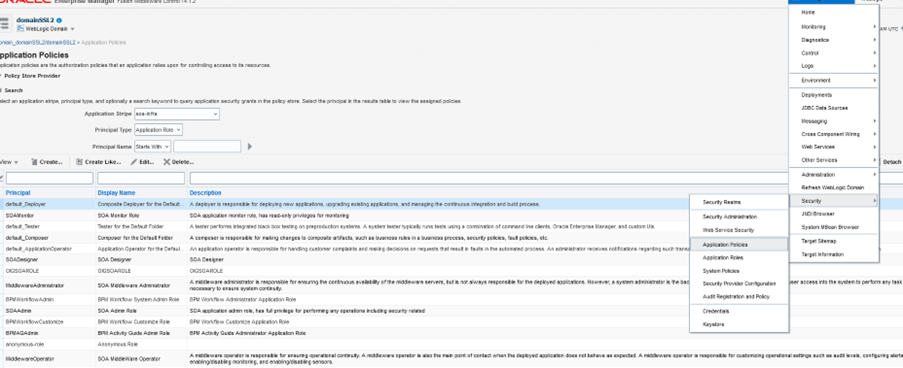
- Select soa-infra from the Application Stripe drop-down.
- Click on Create.
- Under the Grantee section, add the application role that is created in the above Step 4. Example: OIGSOAROLE
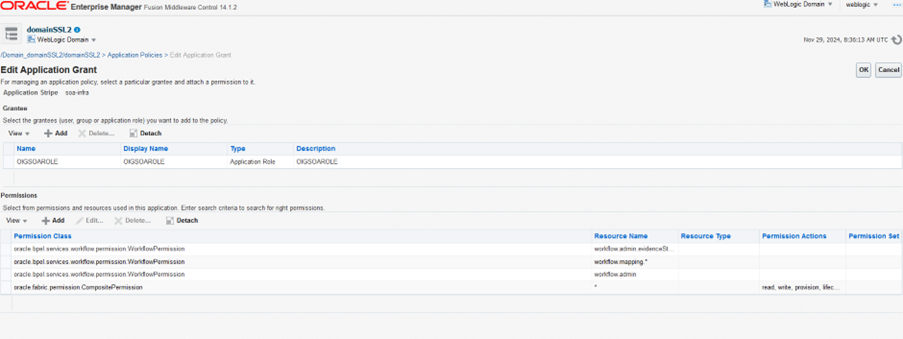
- Under Permissions tab, click Add to add the below permissions and save the changes.
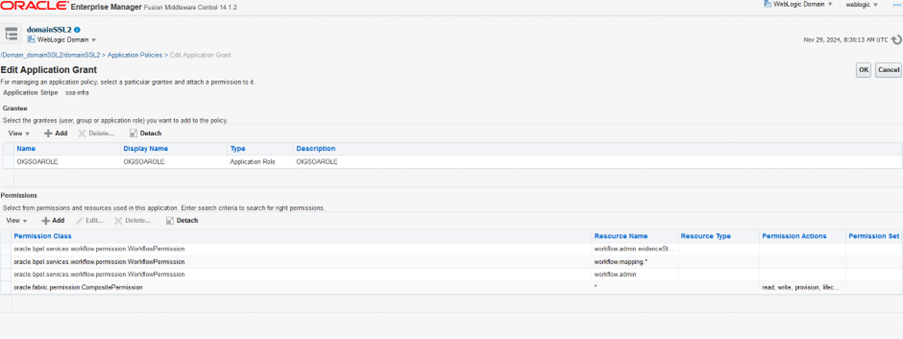
Note:
Please ensure to add the above 4 entries as shown in the screen shot.
- Navigate to Weblogic Domain ->Security->Application Policies.
- Navigate to Security ->Credentials.
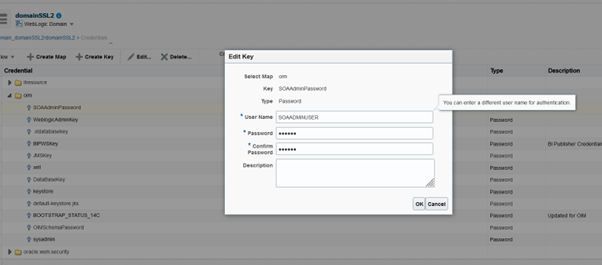
- Select OIM stripe and then select SOAAdminPassword.
- Click Edit and change the user name from weblogic to SOADMINUSER by using the same password used in the previous steps.
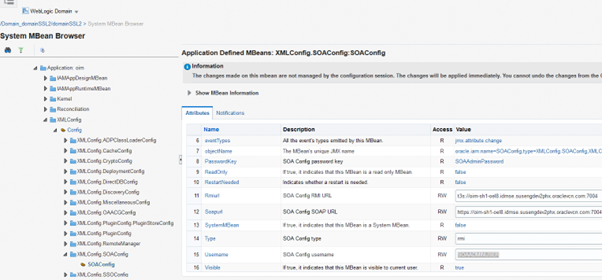
- Navigate to MBean browser and open the Mbean “XMLConfig”.
- Update the user name from “weblogic” to ‘SOAADMINUSER’ and save the changes
- Log in into WLS console and change the user name to
SOAADMINUSERin the Services > Foreign JNDI Providers > ForeignJNDIProvider-SOA section as shown below and remember to commit the changes.Note:
The SOA server’s SSL port 7004 is used. Ex: t3s://<hostname>:7004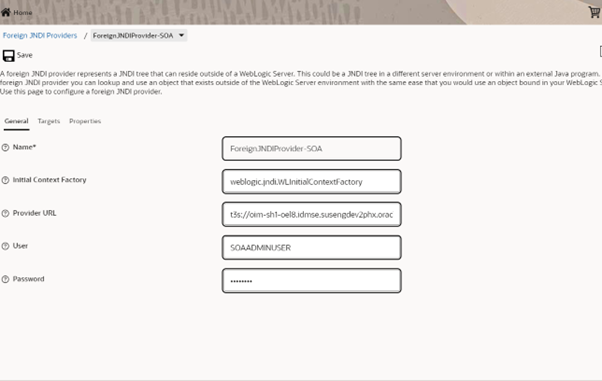
- Verification step: Log in into OIM and navigate to pending approvals page. Ensure that, you are able to see requests in the pending approvals page (provided there are some inflight requests) and request-details page opens up upon clicking the pending requests.