Task 2: Configure the Oracle GoldenGate Environment
Perform the following steps to complete this task:
- Step 2.1 - Access the GoldenGate deployment
- Step 2.2 - Change the default Oracle GoldenGate administrator password
- Step 2.3 - Create the Database Credentials
- Step 2.4 - Create Autostart profiles
- Step 2.5 - Configure Oracle GoldenGate processes
Step 2.1: Access the deployment
To access the deployment:
- If the client subnet is public, you can access the nodes using the VIP
address and SSH tunnel. You must create an SSH tunnel with the VIP
DNS Name on both the primary and standby clusters using the
following command on all
nodes:
Thessh -N -L <local_port>:<vip-dns-name>:443 -p 22 <gghub-node>local_portcan be any available port on the local system. Thegghub-nodeis the name of the cluster to which the tunnel is configured.Oracle recommends that you manage GoldenGate using the primary and standby VIP DNS names as follows:
- Primary VIP DNS Name:
prim.<cluster-prefix>.goldengate.com - Standby VIP DNS Name:
stby.<cluster-prefix>.goldengate.com
You can then access the deployment with your web browser using
https://localhost:<local_port> - Primary VIP DNS Name:
- If the client subnet is private,
- You must create a Bastion to the client subnet with the following values:
- Target VCN: Select your VCN
- Target subnet: Client subnet name
- CIDR block allowlist: Enter or select the IP addresses or address ranges to allow connections to target resources using SSH sessions.
- Create an SSH Port Forwarding session using the primary VIP address and standby VIP address with port 443. Learn more about creating Port Forwarding sessions.
- From the session's Actions menu (three dots), select View SSH command and click Copy.
- Run the SSH command, ensuring that you replace
<privateKey>with the local private key path and443for<localPort>. Learn more about connecting to a Port Forwarding session - You can then access the deployment with your web browser using
https://localhost.
- You must create a Bastion to the client subnet with the following values:
Step 2.2: Change the default password
Log in to Oracle GoldenGate 21c Service Manager as the Administrator for the deployment, to change the password for the Security Role user.
- In your web browser, use the localhost address and local port used when
you set up the SSH tunnel using the VIP DNS name to the instances.
For example,
https://localhost:<local-port>. - Log in as
oggadmin, and use the password found in the/mnt/acfs_gg/deployments/ogg_credentials.jsonfile. - After you log in, open the navigation menu, and then select Administrator.
- On the Users page, click Edit (pencil icon) for the oggadmin user.
- Update the password, and then click Submit.
Note:
The password must be between 8 and 30 alphanumeric upper and lowercase characters, and contain at least one of the following special characters: dash (-), exclamation point (!), percent (%), amperstand (&), asterisk (*), comma (,), pound or hastag (#), and underscore (_).
Upon resetting the oggadmin password, your session ends. Log
back in to Service Manager using the new password. You must now update the
password for oggadmin for each of the other
deployments.
- On the Service Manager Home page, select the port number for the Administration Server for a deployment.
- Log in to the Administration Service as
oggadmin, and enter the password found inthe /mnt/acfs_gg/deployments/ogg_credentials.json. - On the Administration Service Home page, open the navigation menu, and then select Administrator.
- On the Users page, click Edit (pencil icon) for the oggadmin user.
- Update the password, and then cilck Submit. The same password rules as above apply.
Next, change the AGCTL password.
- On any node of primary cluster, as the
opcuser, runsudo su -to switch torootuser. - Run the following commands, and enter the new password when
prompted:
/u01/app/grid/xag/bin/agctl stop goldengate <deployment_name> /u01/app/grid/xag/bin/agctl modify goldengate <deployment_name> --adminuser oggadmin /u01/app/grid/xag/bin/agctl start goldengate <deployment_name> - On any node of Standby Cluster, as
opcuser, runsudo su -to switch torootuser. - Run the following
command:
/u01/app/grid/xag/bin/agctl modify goldengate <deployment_name> --adminuser oggadmin
Step 2.3: Create database credentials
Use the Oracle GoldenGate Microservices UI to create the database
credentials using the above TNS alias names. As the oggadmin user, add
the database credentials:
- Log in into the Oracle GoldenGate Administration Service:
https://localhost:<localPort>/<instance_name>/adminsrvr. - In the left navigation menu, click Configuration.
- In the Database tab, click Add Credentials (plus icon).
- Add the required information for each source and target CDB and
PDB:
Region Container Domain Alias User ID Region 1 CDB GoldenGate Reg1_CDB c##ggadmin@<tns_alias> Region 1 PDB GoldenGate Reg1_PDB ggadmin@<tns_alias> Region 2 CDB GoldenGate Reg2_CDB c##ggadmin@<tns_alias> Region 2 PDB GoldenGate Reg2_PDB ggadmin@<tns_alias>
Step 2.4: Create Autostart profiles
Create a profile that automatically starts the Extract and Replicat processes when the Oracle GoldenGate Administration Server starts, and restarts if any Extract or Replicat processes are abandoned. In GoldenGate Microservices, profiles manage auto start and restart.
Using the Oracle GoldenGate Administration Server UI, create a profile to assign to each Oracle GoldenGate process:
- Log in to the Administration Service on the Source GoldenGate.
- Click on Profile under Administration Service.
- Click the plus (+) sign next to Profiles on the Managed Process Settings home page.
- Enter the details as follows:
- Profile Name: Start_Default
- Description: Default auto-start/resteart profile
- Default Profile: Yes
- Auto Start: Yes
- Auto Start Options
- Startup Delay: 1 min
- Auto Restart: Yes
- Auto Restart Options
- Max Retries: 5
- Retry Delay: 30 sec
- Retries Window: 30 min
- Restart on Failure only: Yes
- Disable Task After Retries Exhausted: Yes
- Click Submit
- Repeat these steps on the Target GoldenGate.
Step 2.5: Configure Oracle GoldenGate processes
When creating Extract, Distribution Paths, and Replicat processes with Oracle GoldenGate Microservices Architecture, all files that need to be shared between the GGHub nodes are already shared with the deployment files stored on a shared file system.
Below, are the essential configuration details recommended for running Oracle GoldenGate Microservices on GGhub for Extract, Distribution Paths, and Replicat processes.
Perform the following sub-steps to complete this step:
- Step 2.5.1 - Extract configuration
- Step 2.5.2 - Replicat configuration
- Step 2.5.3 - Distribution Path configuration
Step 2.5.1: Extract configuration
When creating an Extract using the Oracle GoldenGate Administration
Service interface, leave the Trail Subdirectory parameter blank so that the trail
files are automatically created in the deployment directories stored on the shared
file system. The default location for trail files is the /<deployment
directory>/var/lib/data directory.
Note:
To capture from a multitenant database, you must use an Extract configured at the root level using a c## account. To apply data into a multitenant database, a separate Replicat is needed for each PDB because a Replicat connects at the PDB level and doesn't have access to objects outside of that PDB.
For GoldenGate Extract processes using Data Guard configurations that are using redo transport Maximum Performance or Maximum Availability modes, the following parameter must be added to the Extract process parameter file on the primary system to avoid losing transactions and resulting in logical data inconsistencies:
TRANLOGOPTIONS HANDLEDLFAILOVERThis parameter prevents Extract from extracting transaction data from redo that has not yet been applied to the Data Guard standby database. This is crucial to preventing Oracle GoldenGate from replicating data to a target database that does not exist in the source standby database.
If this parameter is not specified, after a data loss failover of the source database it is possible to have data in the target database that is not present in the source database, leading to logical data inconsistencies.
By default, after 60 seconds, a warning message will be written to the Extract report file when the Extract is stalled due to not being able to query the standby database applied SCN information. For example:
WARNING OGG-02721 Extract has been waiting for the standby database for 60 seconds.The amount of time before the warning message is written to Extract report file can be adjusted using the Extract parameter "TRANLOGOPTIONS HANDLEDLFAILOVER STANDBY_WARNING".
If the Extract is still not able to query the standby database applied SCN information after 30 minutes (default), the Extract process will abend, logging the following message in the Extract report file:
ERROR OGG-02722 Extract abended waiting for 1,800 seconds for the
standby database to be accessible or caught up with the primary database.If the standby database becomes available before the default 30 timeout expires, Extract continues mining data from the source database and reports the following message to the report file:
INFO OGG-02723 Extract resumed from stalled state and started
processing LCRs.The timeout value of 30 minutes can be adjusted using the Extract parameter "TRANLOGOPTIONS HANDLEDLFAILOVER STANDBY_ABEND <value>", where value is the number of seconds the standby is unavailable before abending.
If the standby database will be unavailable for a prolonged duration, such as during a planned maintenance outage, and you wish Extract to continue extracting data from the primary database, remove the "TRANLOGOPTIONS HANDLEDLFAILOVER" parameter from the Extract parameter file and restart Extract (see example below in Figures 4 to 6). Remember to set the parameter after the standby becomes available.
Note:
If extracting from a primary database continues while the standby is unavailable, a data loss failover could result after the standby becomes available, and not all the primary redo was applied before a failover. The GoldenGate target database will contain data that does not exist in the source database.If the Extract process has been assigned an auto restart profile, after a Data Guard role transition, the Extract process will automatically restart. Extract will continue to mine redo data from the new primary database, ignoring the current state of the new standby database, until a default 5-minute timeout period expires. After this time, if the standby is not available Extract will abend with the following errors:
INFO OGG-25053 Timeout waiting for 300 seconds for standby database
reinstatement. Now enforcing HANDLEDLFAILOVER.
ERROR OGG-06219 Unable to extract data from the Logmining server OGG$CAP_XXXXX.
ERROR OGG-02078 Extract encountered a fatal error in a processing thread and is
abending.Extract will continue to automatically restart, based on the GoldenGate
Microservices auto restart profile, and failing due to reaching the
HANDLEDLFAILOVER timeout, until the number retries is reached
or the new standby database becomes available.
During the timeout period following a database role transition, the
HANDLEDLFAILOVER parameter is automatically suspended, so data
will be replicated to the Oracle GoldenGate replica database without consideration
of the source standby database not being kept up to date. The timeout period for the
standby database to start up before Extract abends can be adjusted using the Extract
parameter TRANLOGOPTIONS DLFAILOVER_TIMEOUT.
It is recommended that you leave DLFAILOVER_TIMEOUT at
the default of 5 minutes, to allow the old primary to convert to a standby. If the
new standby database will be unavailable for an extended period of time or
completely gone, then in order for Extract to start and remain running, you must
remove the HANDLEDLFAILOVER parameter from the Extract parameter
file. After removing the parameter, Extract no longer waits until redo has been
applied to the standby database before extracting the data.
During the time it takes for the standby database to come back online and
apply all the redo from the primary database, there will be data divergence between
it and the Oracle GoldenGate replica database. This will be resolved once the
standby database is up to date. At which point, add the
HANDLEDLFAILOVER parameter back into the integrated Extract
process parameter file, and then stop and restart the Extract.
When Oracle Data Guard Fast-Start Failover is disabled, such that the broker can automatically fail over to a standby database in the event of loss of the primary database, you must specify an additional integrated Extract parameter shown below.
TRANLOGOPTIONS FAILOVERTARGETDESTID nThis parameter identifies which standby database the Oracle GoldenGate Extract process must remain behind, with regards to not extracting redo data that has not yet been applied to the standby database.
If Oracle Data Guard Fast-Start Failover is disabled, and you don’t
specify the additional integrated Extract parameter
FAILOVERTARGETDESTID, the extract will abend with the following
errors:
ERROR OGG-06219 Unable to extract data from the Logmining server OGG$CAP_XXXXX.
ERROR OGG-02078 Extract encountered a fatal error in a processing thread and is
abending.To determine the correct value for FAILOVERTARGETDESTID,
use the LOG_ARCHIVE_DEST_N parameter from the GoldenGate source
database which is used for sending redo to the source standby database. For example,
if LOG_ARCHIVE_DEST_2 points to the standby database, then use a
value of 2.
As the oracle user on the primary database system,
execute the following command:
[opc@exapri-node1 ~]$ sudo su - oracle
[oracle@exapri-node1 ~]$ source <db_name>.env
[oracle@exapri-node1 ~]$ sqlplus / as sysdba
SQL> show parameters log_archive_dest
NAME TYPE VALUE
--------------------- ----------- ---------------------------------------------------
log_archive_dest_1 string location=USE_DB_RECOVERY_FILE_DEST,
valid_for=(ALL_LOGFILES, ALL_ROLES)
log_archive_dest_2 string service="<db_name>", SYNC AFFIRM delay=0
optional compression=disable max_failure=0 reopen=300
db_unique_name="<db_name>" net_timeout=30,
valid_for=(online_logfile,all_roles)In this example, the Extract parameter would be set to the following:
TRANLOGOPTIONS FAILOVERTARGETDESTID 2Create the Extract:
- Log in to the Oracle GoldenGate Administration Server
- Click in Overview under Administration Service
- Click the plus button to Add Extract
- Select Integrated Extract
- Add the required information as follows:
- Process Name: EXT_1
- Description: Extract for Region 1 CDB
- Intent: Unidirection
- Begin: Now
- Trail Name: aa
- Credential Domain: GoldenGate
- Credential Alias: Reg1_CDB
- Register to PDBs: PDB Name
- Click Next
- If using CDB Root Capture from PDB, add the
SOURCECATALOGparameter with the PDB Name - Click Create and Run
Step 2.5.2 - Replicat configuration
Oracle generally recommends using integrated parallel Replicat which offers better apply performance for most workloads when the GGHUB is in the same region as the target Oracle GoldenGate database.
The best apply performance can be achieved when the network latency between the GGHUB and the target database is as low as possible. The following configuration is recommended for the remote Replicat running on the Oracle GGHUB.
APPLY_PARALLELISM– Disables automatic parallelism, instead of usingMAX_APPLY_PARALLELISMandMIN_APPLY_PARALLELISM, and allows the highest amount of concurrency to the target database. It is recommended to set this as high as possible based on available CPU of the hub and the target database server.MAP_PARALLELISM– Should be set with a value of 2 to 5. With a larger number of appliers, increasing the Mappers increases the ability to hand work to the appliers.BATCHSQL– applies DML using array processing which reduces the amount network overheads with a higher latency network. Be aware that if there are many data conflicts,BATCHSQLresults in reduced performance, as rollback of the batch operations followed by a re-read from trail file to apply in non-batch mode.
Step 2.5.2.1 - Create the Checkpoint Table
The checkpoint table is a required component for Oracle GoldenGate Replicat processes. After connecting to the database from the Credentials page of the Administration Service, you can create the checkpoint table.
Create the checkpoint table in the target deployment:
- Log in to the Oracle GoldenGate Administration Server
- Click in Configuration under Administration Service.
- Click on Database and Connect to the target database or PDB:
- Click the plus (+) sign next to Checkpoint. The Add Checkpoint page is displayed.
- Enter the details as follows:
- Checkpoint Table: ggadmin.chkp_table
- Click Submit
Refer to Oracle GoldenGate with Oracle Database Guide for more information on the checkpoint table.
Step 2.5.2.2 - Add a Replicat
After you’ve set up your database connections and verified them, you can add a Replicat for the deployment by following these steps:
- Log in to the Oracle GoldenGate Administration Server
- Click theplus (+) sign next to Replicats on the Administration Service home page. The Add Replicat page is displayed.
- Select a Replicat type and click Next.
- Enter the details as follows:
- Process Name: REP_1
- Description: Replicat for Region 2 PDB
- Intent: Unidirectional
- Credential Domain: GoldenGate
- Credential Alias: Reg2_PDB
- Source: Trail
- Trail Name: aa
- Begin: Position in Log
- Checkpoint Table: "GGADMIN"."CHKP_TABLE"
- Click Next
- From the Action Menu, click Start.
Step 2.5.3 - Distribution Path configuration
Distribution paths are only necessary when trail files need to be sent to an additional Oracle GoldenGate Hub in a different, or even the same, region as described in the following figure.
Figure 3-1 Oracle GoldenGate Distribution Path
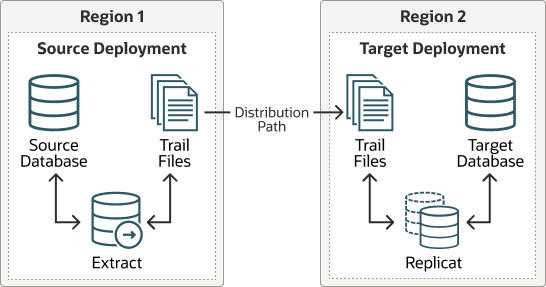
When using Oracle GoldenGate Distribution paths with the NGINX Reverse Proxy, additional steps must be carried out to ensure the path client and server certificates are configured.
More instructions about creating distribution paths are available in Using Oracle GoldenGate Microservices Architecture. A step-by-step example is in the following video, “Connect an on-premises Oracle GoldenGate to OCI GoldenGate using NGINX,” to correctly configure the certificates.
Here are the steps performed in this sub-step:
- Step 2.5.3.1 - Download the Target Server’s Root Certificate, and then upload it to the source Oracle GoldenGate
- Step 2.5.3.2 - Create a user in the Target Deployment for the Source Oracle GoldenGate to use
- Step 2.5.3.3 - Create a Credential in the Source Oracle GoldenGate
- Step 2.5.3.4 - Create a Distribution Path on the Source Oracle GoldenGate to the Target Deployment
- Step 2.5.3.5 - Verify the Connection in the Target Deployment Console Receiver Service
Step 2.5.3.1 - Download the Target Server’s Root Certificate, and then upload it to the source Oracle GoldenGate
Download the target deployment server’s root certificate and add the CA certificate to the source deployment Service Manager.
- Log in to the Administration Service on the Target GoldenGate.
- Follow “Step 2 - Download the target server’s root certificate” in the video “Connect an on-premises Oracle GoldenGate to OCI GoldenGate using NGINX.”
Step 2.5.3.2 - Create a user in the Target Deployment for the Source Oracle GoldenGate to use
Create a user in the target deployment for the distribution path to connect to:
- Log in to the Administration Service on the Target GoldenGate.
- Click on Administrator under Administration Service.
- Click the plus (+) sign next to Users.
- Enter the details as follows:
- Username: ggnet
- Role: Operator
- Type: Password
- Click Submit
Step 2.5.3.3 - Create a Credential in the Source Oracle GoldenGate
Create a credential in the source deployment connecting the target deployment with the user created in the previous step. For example, a domain of OP2C and an alias of WSSNET.
- Log in to the Administration Service on the Source Oracle GoldenGate.
- Click in Configuration under Administration Service.
- Click the plus (+) sign next to Credentials on the Database home page.
- Enter the details as follows:
- Credential Domain: OP2C
- Credential Alias: wssnet
- User ID: ggnet
- Click Submit
Step 2.5.3.4 - Create a Distribution Path on the Source Oracle GoldenGate to the Target Deployment
A path is created to send trail files from the Distribution Server to the Receiver Server. You can create a path from the Distribution Service. To add a path for the source deployment:
- Log in to the Distribution Service on the Source Oracle Goldengate.
- Click the plus (+) sign next to Path on the Distribution Service home page. The Add Path page is displayed.
- Enter the details as follows:
Option Description Path Name Select a name for the path. Source: Trail Name Select the Extract name from the drop-down list, which populates the trail name automatically. If it doesn’t, enter the trail name you provided while adding the Extract. Generated Source URI Specify localhost for the server’s name; this allows the distribution path to be started on any of the Oracle RAC nodes. Target Authentication Method Use ‘UserID Alias’ Target Set the Target transfer protocol to wss (secure web socket). Set the Target Host to the target hostname/VIP that will be used for connecting to the target system along with the Port Number that NGINX was configured with (default is 443). Domain Set the Domain to the credential domain created above in Step 2.3.3.3, for example, OP2C. Alias The Alias is set to the credential alias wssnet, also created in Step 2.3.3.3. Auto Restart Options Set the distribution path to restart when the Distribution Server starts automatically. This is required, so that manual intervention is not required after a RAC node relocation of the Distribution Server. It is recommended to set the number of Retries to 10. Set the Delay, which is the time in minutes to pause between restart attempts, to 1. - Click Create Path.
- From the Action Menu, click Start.