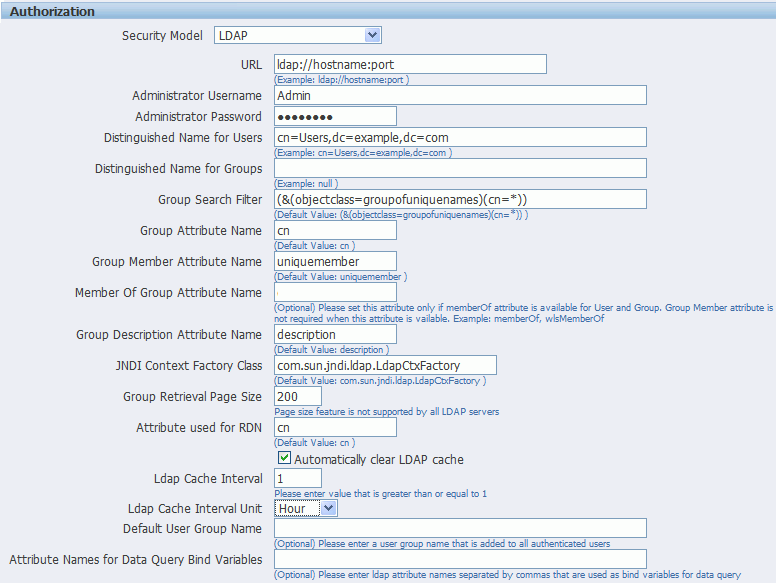
-
URL
For example: ldap://example.com:389/
If you're using LDAP over SSL, then note the following:
-
the protocol is "ldaps"
-
the default port is 636
For example: ldaps://example.com:636/
-
Administrator Username and Password for the LDAP server
The Administrator user entered here must also be a member of the XMLP_ADMIN group.
-
Distinguished Name for Users
For example: cn=Users,dc=example,dc=com
The distinguished name values are case-sensitive and must match the settings in the LDAP server.
-
Distinguished Name for Groups
For example: cn=Groups,dc=us,dc=oracle,dc=com
The default value is cn=OracleDefaultDomain,cn=OracleDBSecurity,cn=Products,cn=OracleContext,dc=example,dc=com
-
Group Search Filter
The default value is (&(objectclass=groupofuniquenames)(cn=*))
-
Group Attribute Name
The default value is cn
-
Group Member Attribute Name
The default value is uniquemember
-
Member of Group Attribute Name
(Optional) Set this attribute only if memberOf attribute is available for User and Group. Group Member Attribute is not required when this attribute is available. Example: memberOf or wlsMemberOf
-
Group Description Attribute Name
The default value is description
-
JNDI Context Factory Class
The default value is com.sun.jndi.ldap.LdapCtxFactory
-
Group Retrieval Page Size
Setting this value enables support of the LDAPv3 control extension for simple paging of search results. By default, the Publisher server doesn't use pagination. This value determines the number of results to return on a page (for example, 200). Your LDAP server must support control type 1.2.840.113556.1.4.319 to support this feature, such as Oracle Internet Directory 10.1.4. Ensure that you check your LDAP server documentation for support of this control type before entering a value.
-
Attribute used for Login Username
Enter the attribute that supplies the value for the Login user name. This is also known as the Relative Distinguished Name (RDN). This value defaults to cn.
-
Automatically clear LDAP cache - to schedule the automatic refresh of the LDAP cache the LDAP cache per a designated interval, select this box. After you select this box the following additional fields become enabled:
-
Enter an integer for Ldap Cache Interval. For example, to clear the LDAP cache once a day, enter 1.
-
Select the appropriate Ldap Cache Interval Unit: Day, Hour, or Minute.
-
Default User Group Name
(Optional) Use this option if your site has the requirement to allow all authenticated users access to a set of folders, reports, or other catalog objects. The user group name that you enter here is added to all authenticated users. Any catalog or data source permissions that you assign to this default user group are granted to all users.
-
Attribute Names for Data Query Bind Variables
(Optional) Use this property to set attribute values to be used as bind variables in a data query. Enter LDAP attribute names separated by a commas for example: memberOf, primaryGroupID,mail