2.17.1 Webhook Definition
In a Webhook definition, you can create a Channel with specific third party authentication mode, provide test and service url and generate secret key.
- Select Setup > Administration > System > Webhook.
- In the Webhook section, perform any of the Basic Operations mentioned in Navigation chapter.
A brief description of the fields are given below:
Table 2-77 Webhook Definition
Field Do this Channel Specify the channel name of interfaced third-party application for identification. The same will be added into weblogic Key Store. Client Secret Key The client secret key is auto generated by the system on clicking Generate button after defining the details. If already generated, the same can be used to regenerate Service URL Specify the context path of third-party application’s Webhook Service URL used for communication where POST request is to be provided. You can define multiple service end-point URLs for the same channel. Test Service URL Specify the GET web service Webhook URL of third-party application to check service availability.
Click Test button to generate sample test call. The status, either success or error of the test call is displayed on the screen as SERVICE URL TEST SUCCESFUL/FAILED. Refer step 4 below for more information.
Enabled Check this box to enable the Webhook definition. Authentication mode Select the authentication mode of third-party application from the drop-down list. The list is displayed based on lookup code WHK_AUTH_MODE_CD. System supports the following options:
BASIC - On selecting this option, you need to define User Name and Password to authenticate.
OAUTH2.0 - On selecting this option, you need to define additional enabled fields such as Grant Type, Client Id, Client Secret, Identity Domain, Token and Header Key.
ORACLE BANKING ROUTING HUB - On selecting this option, you need to define User Name, Password, Token Header Key, Response Token Key, and Request Authorization Header Prefix to authenticate.
Note: Based on the above selection, additional Webhook definition fields are enabled and need to be populated accordingly.
The following additional fields are available for BASIC type of Authentication mode: User Name Specify the Basic Authentication User Name. Password Specify the Basic Authentication User Password. The following additional fields are enabled for OAUTH2.0 type of Authentication mode: Token URL Specify the third-party OAUTH 2.0 token generation URL. Grant Type Select the OAUTH 2.0 grant type from the drop-down list. The list is populated based on lookup code WHK_GRANT_TYPE_CD. Client Id Specify the identification name of third-party OAUTH 2.0 client. Client Secret Specify the secret code of third-party OAUTH 2.0 client. Identity Domain Specify the domain name of the third-party OAUTH 2.0 client. Token Header Key Specify the token header key of third-party OAUTH 2.0 client. Response Token Key Specify the Response Token Key of third-party OAUTH 2.0 client which is the key name of Authentication Response Header. The same is used to identify token value used as input for subsequent calls.
Note: If value is not provided, system defaults to access_token.
Request Authorization Header Prefix Specify the Request Authorization Header Prefix of third-party OAUTH 2.0 client This is the prefix used to Request Authorization Header based on token generation mechanism like Basic, Bearer, JWT and so on.
Note: If value is not provided, system defaults to Bearer.
User Name If Authentication mode is selected as OAUTH2.0 and Grant Type as Resource Owner Password, specify the third-party OAUTH 2.0 Resource Owner User Name. Password If Authentication mode is selected as OAUTH2.0 and Grant Type as Resource Owner Password, specify the third-party OAUTH 2.0 Resource Owner User Password. The following additional fields are enabled for ORACLE BANKING ROUTING HUB (OBRH) type of Authentication mode: User Name Specify the third-party OBRH Resource Owner User Name. Password Specify the third-party OBRH Resource Owner Password. Token Header Key Specify the token header key of third-party OBRH client. Response Token Key Specify the Response Token Key of third-party OBRH client which is the key name of Authentication Response Header. The same is used to identify token value used as input for subsequent calls.
Note: If value is not provided, system defaults to access_token. An example is indicated below where token element is the key name:
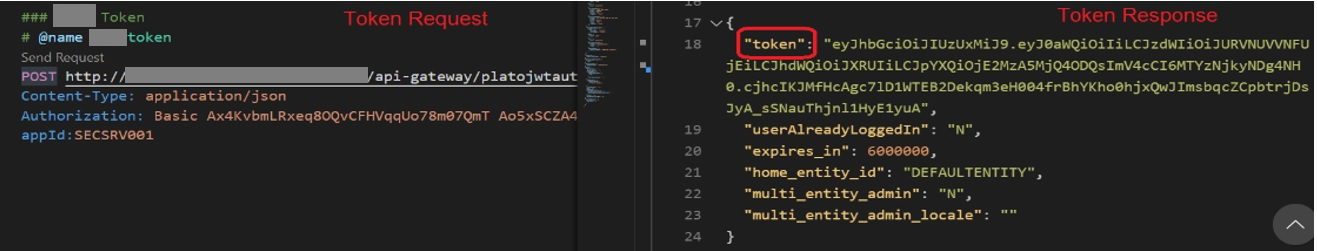
Description of the illustration response-token-key.pngRequest Authorization Header Prefix Specify the Request Authorization Header Prefix of third-party OBRH client This is the prefix used to Request Authorization Header based on token generation mechanism like Basic, Bearer, JWT and so on.
Note: If value is not provided, system defaults to Bearer. An example is indicated below:
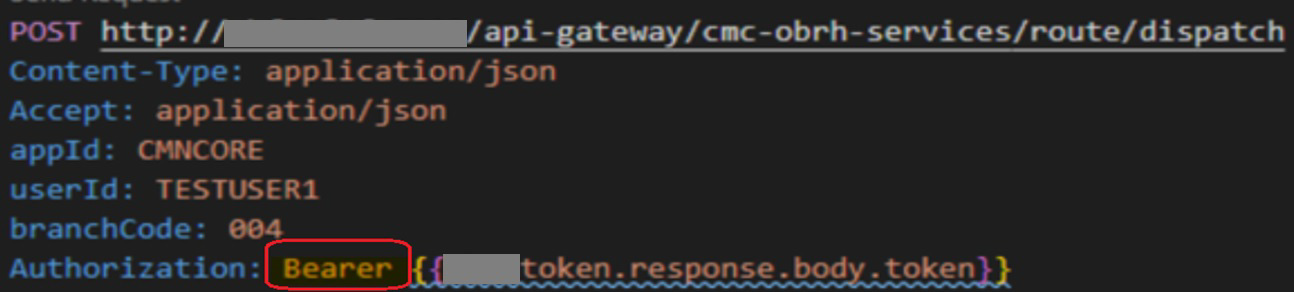
Description of the illustration request-authorization-header-prefix.pngBureau <Check if required> Select the Credit Bureau from the drop-down list. This is required if the Credit Bureau report format is to be processed externally as defined in Setup > Administration > User > Credit Bureau screen.
The list is populated with credit bureau details maintained in CRB_SOURCE_CD lookup. This field is enabled only during ADD process and is Read-Only during EDIT.
Ensure that the selected Bureau is not already selected for the enabled record. Else, system displays an error indicating Record already exist with same bureau and need to disable the existing record and enable the new record with the new Bureau.
Note: The Event Details section is not displayed if the Credit Bureau report format is to be processed externally.
Verified This check box is auto selected on verifying the channel data by clicking TEST button and if the test server connection is successful. - Perform any of the Basic Actions mentioned in Navigation chapter.
- Click Test button to verify the configuration details of third-party application.
- Th external system generates base 64 X-Hmac header using HMAC SHA 256 and propagate this as part of response header to OFSLL.
- Channel name is used in HMAC digest as given below. This will be passed to the external interface using HTTP Header Key ChannelName. This value will be in base 64 encoded format.
- System will validate this response and update the Verified indicator. Only HTTP status code 200 is considered as success.
Format: "OFSLL": Base64 Encoded [HMAC SHA 256 of ["Http Method Types":"Base64 Encoded Channel Name": "Service URL"] with Client Secret Key]
For example:
Client Secret KeyZXlKMGVYQWlPaUpLVjFRaUxDSmhiR2NpT2lKSVV6VXhNaUo5LmV5SnpkV0lp T2lKWFJVSklUMDlMSWl3aVEwaEJUazVGVENJNklrVllWRVZTVGtGTVNVNVVS VkpHUVVORkxVOUJWVlJJTWpBaUxDSnBjM01pT2lKUFJsTk1URjlYUlVKSVQw OUxJaXdpWlhod0lqb3hOVFUxTmpnMU1qSXpMQ0pwWVhRaU9qRTFOVFUyT0 RRNU1qTjkuemxMb0lzdWduek1FRnhyblcxYXJIeXNMSFliSmVQd0R5SUxvdDdU aXZDMEFVUktEbm5WcDJpWmRiT1pJald5aHNfSWxNaG1lV1dWZUF0YmZRUnl 1X2c=Cipher Text for HMAC SHA 256GET:RVhURVJOQUxJTlRFUkZBQ0UtT0FVVEgyMA==:application/json:https:// Hostname:Port/webhook_oauthqa/service/api/resources/webhook/testGenerated Sample X-Hmac headerOFSLL:F/jj07qhgM3g5z91EHU/rdxYbaJ266SRnXsBRoUxgUc=Note:
Configuration details for OBRH application cannot be verified using Test option since OBRH currently does not support return of customizing HTTP header [X-Hmac]. - Clicking Generate button OFSLL generates Client Secret Key. This key is used in generation of X-HMAC header that is sent to the third-party channel to validate origination of the request.
System generated X-HMAC header uses base 64 encoded HMAC SHA 256 algorithm. This algorithm uses below logic:
Format: "OFSLL": Base64 Encoded [HMAC SHA 256 of ["Http Method Types":"Base64 Encoded Payload":" Http Content Types": "Service URL"] with Client Secret Key]
For example.
Client Secret KeyT0ZTTExfQjJCX1RFU1RfQ0xJRU5UOndlbGNvbWUxCipher Text for HMAC SHA 256POST:ewogICAgIlJlcXVlc3RUeXBlIjogIk9VVEJPVU5EIgp9:application/json:http:// Hostname:Port/webhook/service/api/resources/webhook/basicGenerated Sample X-Hmac headerOFSLL:q6xCpZrnudfB8owvYEi2+Aac4clM3b/XFVTVrChdQKA=
Parent topic: Webhook