1.16 Passkey (Passwordless login)
This topic describes the systematic instruction to Passkey (Passwordless login) option.
Passkey is passwordless login is introduced in latest IOS ecosystem (iOS devices, Safari) and Android devices and on latest browsers.which allows users to login securely without entering username and password.
IOS passkeys are shared in iCloud keychain. Hence iCloud Keychain should be enabled by the users on their apple ID on iOS device.
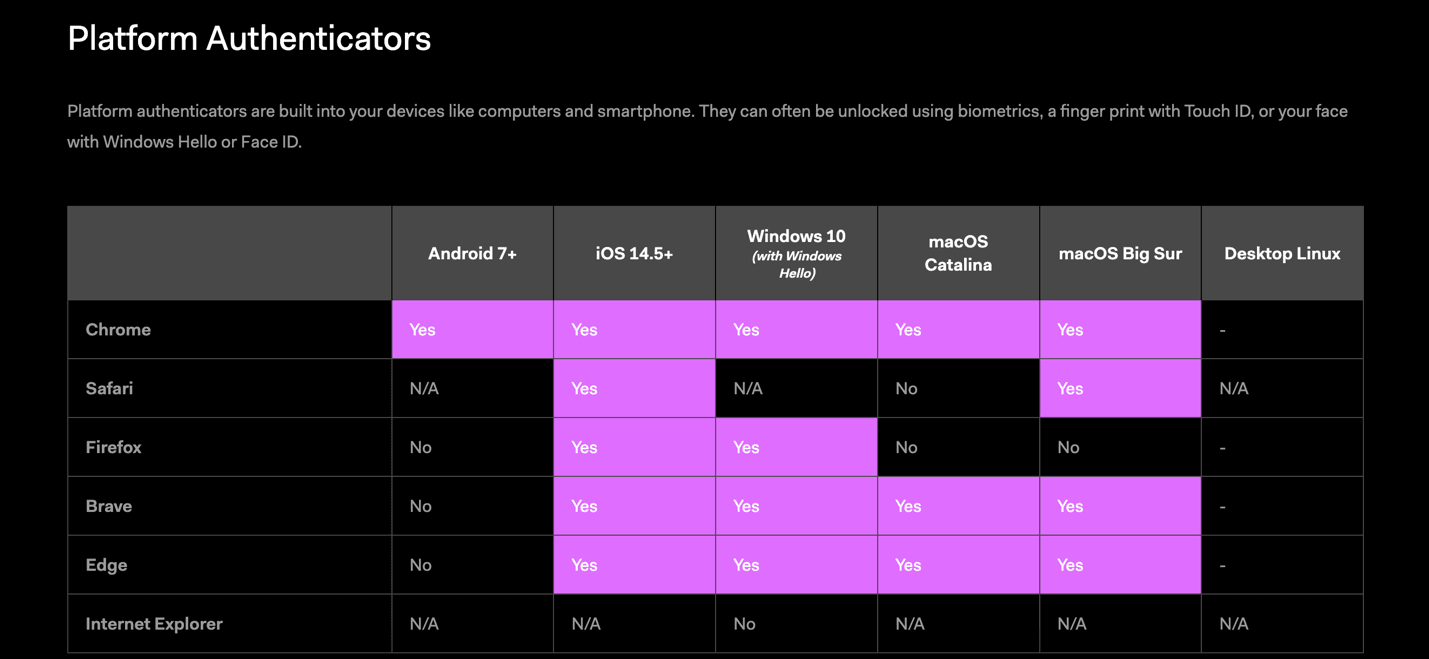
System requirements: Attached is the compatibility chart for passkeys to work:
Browsers should also be latest versions supporting WebAuthn protocols.
Note:
Only one of two login types can exist in the application, Either passkey or alternate (PIN/Pattern/FaceId/touchID). So, setup this option for brand new application update in the market. If the application is already launched and users have enabled alternate login, then enabling passkey option in later application versions will hide the alternate login options from the application and user will have an option to register passkey in his profile settings.To disable this option
By doing this, passkey option will not be available to users within the application. User will not be able to register for passkey and will not be able to login using passkey. Follow below steps:
- Remove RTM access from Client Servicing → Authentication → Passkey
Setup for Mobile Application, Mobile (Responsive) and Internet touch
points
To enable this option:
- Add RTM access from Client Servicing → Authentication → Passkey Setup for Mobile
Application,Mobile (Responsive) and Internet touch points
- Set this flag in channel-framework-js-configurations-config.js to
true
thirdPartyAPIs → passkey → required → false
- Open Zigbank project in Xcode, Select Zigbank target -> Signing Capabilities -> Delete Associated domain
TO ENABLE THIS OPTION:
- Add RTM access from Client Servicing → Authentication → Passkey Setup for Mobile
Application,Mobile (Responsive) and Internet touch points
- Set this flag in channel-framework-js-configurations-config.js to
true
thirdPartyAPIs → passkey → required → true
- Along with above, we need below server side and application side setup
Server-Side Setup:
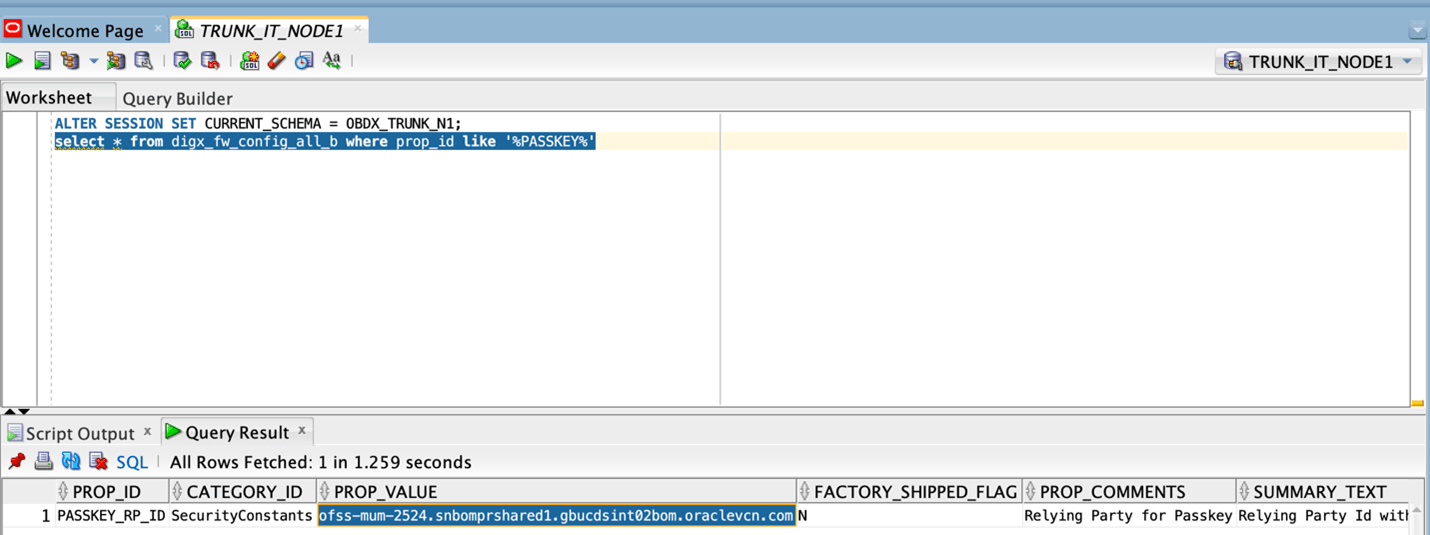
- Update the relying party in below
property
select prop_value from digx_fw_config_all_b where prop_id='PASSKEY_RP_ID'Note:
Relying partId is the domain name of the website to which credentials will be associated. (Eg google.com, example.com etc)
Hosting AASA file (Apple-app-site-association) on server.
- AASA- Apple App Site Association fille which IOS installs on the device when application is installed. This AASA file is hosted on our server for testing and then apple stores that file to its APPLE CDN when application is released on Appstore.
- This file is fetched by Apple after a duration of 5 days. So, any new update in the file takes 5 days to gets reflected in the application. In development mode though, every application installation, the AASA file is re-fetched on device.
There are two parts for the AASA file setup – Server side and application side.
Server-Side AASA Setup:
- AASA file needs to be on https server with valid SSL certificate.
- Update properties in digx-sms.war →
com.ofss.digx.app.sms.service.jar → resources/IphoneApplink.properties
Below are the sample values for a single application supporting deep link. Bank must update banks’ teamID and bundle ID.
numberofapps=1 appid0=3NXJ972C93.com.ofss.digx.obdx.zigbank <Add bank’s teamID.bundleID>paths0=* - Need to change host and port in Obdx.conf
ProxyPass "/.well-known" "http://<OHS host>/digx-sms/v1/.well-known"
ProxyPassReverse "/.well-known" "http://<OHS host>/digx-sms/v1/.well-known" - After the setup is done, this ASA file must be accessible on mobile browser with
this URL. There should not by any redirects for accessing this
file.
https://<host>/.well-known/apple-app-site-association
The output should be as below
{ "webcredentials": { "apps": [ "3NXJ972C93.com.ofss.digx.obdx.zigbank" ] } }
Application side.setup:
- Open developer portal and enable Associated domain for your appID
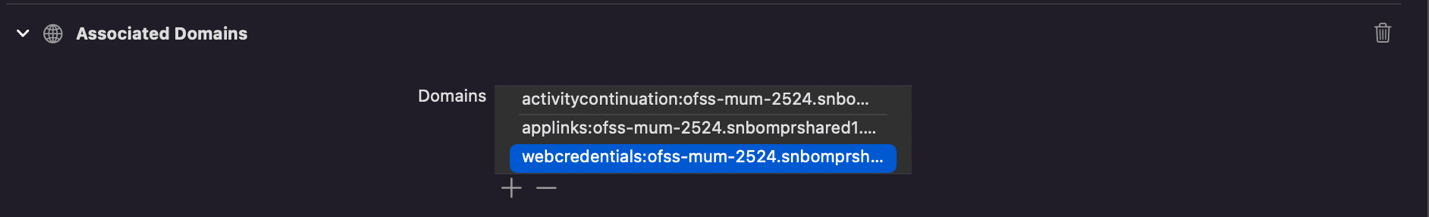
- Open Zigbank.workspace- Select Zigbank target. Go to Signing and
Capabilities – In associated domain section, update the url with bank’s host for
webcredentials key.
Example. Replace ofss-mum-2524.snbomprshared1.gbucdsint02bom.oraclevcn.com?mode=developer with banks host where the ASA file is hosted. Port and “https” should not be added here.
Note:
In webcredentials value “?mode=developer” is only for development mode and testing on TestFlight. Hence for development with this mode, we can test only with developer profile.Once app is ready for distribution to Appstore, ?mode=developer should be removed while archiving for app store release.
How to test on device in development/testing phase.
- Developer mode should be enabled on IOS device
- iCloud keychain should be enabled for AppleID configured on the device. Settings → profile → iCloud → Passwords and Keychains → Sync this iPhone
- Go to Settings → Passwords → Password Option → Check Auto ill option is enabled
Parent topic: OBDX Servicing Application